Understanding Zero Knowledge Proof: Revolutionizing Privacy and Scalability in Blockchain Technology

In the rapidly evolving landscape of blockchain technology, zero knowledge proofs (ZKPs, or zero knowledge proof zkp) have emerged as one of the most transformative innovations, addressing two critical challenges that have long plagued the industry: privacy and scalability. At a high level, zero knowledge proofs are a type of cryptographic proof that enables one party to prove the validity of a statement to another party without revealing any additional information beyond the fact that the statement is true. This cryptographic proof provides privacy and security in blockchain applications, such as transaction validation and identity verification. Zero knowledge proofs represent a revolutionary advance in computational integrity and privacy technology, enabling the secure and private exchange of information without revealing underlying private data. As we navigate through 2025, understanding zero knowledge proof systems has become essential for anyone involved in cryptocurrency trading, DeFi protocols, or blockchain development. Emerging trends like zk-SNARKs and hardware acceleration are driving the blockchain world toward rapid scalability and secure interoperability.
Understanding Zero Knowledge Proofs: The Foundation
Zero knowledge proofs are a powerful cryptographic method that allows one party to prove knowledge of specific data to another party without revealing the data itself. In other words, a prover can convince a verifier that a particular statement is true without disclosing any secret information or other data beyond the statement’s validity. This capability is crucial for preserving user privacy while enabling trustless verification.
The core of zero knowledge proofs lies in the three properties: completeness, soundness, and zero knowledge. Completeness ensures that if the statement is true, an honest verifier will be convinced by an honest prover. For example, if a prover claims to know a secret password, completeness guarantees that the verifier will accept the proof if the prover is truthful. Soundness guarantees that if the statement is false, no dishonest prover can convince the honest verifier otherwise, preventing fraud or deception. The zero-knowledge property ensures that the verifier learns nothing beyond the fact that the statement's truth has been established; no additional knowledge or secret information is revealed during the process.
To explain zero knowledge protocols, consider the classic 'Where's Wally?' scenario. Here, two parties are involved: the prover P, who claims to know Wally's location (the secret), and the verifier. The goal is proving knowledge of Wally's location without revealing it. The protocol works as follows: the verifier randomly chooses which path the prover P must take to reach Wally. The prover P then demonstrates their knowledge by successfully navigating the chosen path. This process is repeated multiple times, and each time, the verifier observes through a small hole—an analogy for seeing just enough to confirm the claim without revealing Wally's location or any other details. What is proved is that the prover P knows Wally's location, not the secret itself. The act of proving is done without revealing any information about Wally's location; the protocol reveals nothing about the secret. This example proves the prover's knowledge and captures the essence of zero knowledge protocols, where the verifier gains confidence in the statement's truth while the secret remains protected.
Proof Systems: Types and Structures in Zero Knowledge
Zero knowledge proof systems come in several distinct forms, each designed to address different security and efficiency requirements in cryptographic protocols. At their core, these proof systems enable one party—the prover—to convince another party—the verifier—that a specific statement is true, all without revealing any secret information or additional data beyond the statement’s validity.
One of the foundational structures in zero knowledge is the interactive proof system. In this approach, the prover and verifier engage in multiple rounds of communication, with the verifier issuing challenges and the prover responding to demonstrate knowledge. This interactive process is essential for certain applications where dynamic verification is required, and it forms the basis for many early zero knowledge protocols.
Beyond interactive proof systems, there are statistical zero knowledge and computational zero knowledge proof systems. Statistical zero knowledge relies on probabilistic techniques to ensure that, even if the verifier is dishonest, they cannot extract meaningful information about the secret, except with negligible probability. Computational zero knowledge, on the other hand, leverages advanced mathematics and the assumed hardness of problems like the discrete logarithm problem to guarantee that, for any efficient adversary, the secret remains secure.
Modern developments have introduced succinct non-interactive arguments of knowledge (SNARKs), which allow users to generate a proof that can be verified quickly and without the need for back-and-forth communication. These non-interactive proof systems are particularly valuable for blockchain applications, where efficiency and scalability are paramount.
The security of these zero knowledge proof systems is rooted in their three essential properties: completeness (an honest prover can always convince an honest verifier), soundness (a dishonest prover cannot convince the verifier of a false statement, except with negligible probability), and zero knowledge (the verifier learns nothing beyond the truth of the statement). By combining these properties with robust mathematical foundations, zero knowledge protocols empower users to prove possession of knowledge or credentials without revealing the underlying secret information, making them a cornerstone of privacy-enhancing technologies in the digital age.
The 2025 ZKP Revolution and Hardware Acceleration
In 2025, zero knowledge proofs are revolutionizing online privacy and security by enabling proofs without revealing secrets or sensitive personal information. This transformation is particularly significant for regulated industries, where data breaches can lead to severe penalties and loss of user trust. Zero knowledge proof systems allow organizations to prove compliance or transaction validity while preserving user privacy and protecting sensitive data.
One of the key trends driving this revolution is hardware acceleration technology. Creating zero knowledge proofs often requires substantial computational power due to the complex mathematical operations involved. The process of generating a proof begins with a given input, which is the data or statement to be proved without revealing the underlying information. Some zero-knowledge proof systems require a trusted setup to securely generate cryptographic parameters before proofs can be created. Specialized hardware accelerators now assist developers in generating proofs more efficiently, making zero knowledge protocols practical and cost-effective for widespread adoption. This advancement is critical for scaling zero knowledge proof systems to support real-world applications with high throughput and low latency.
ZK-Rollups: Scaling Blockchain Infrastructure
Among the most impactful applications of zero knowledge proofs in 2025 are ZK-rollups, which address blockchain scalability challenges by bundling hundreds or thousands of transactions off-chain into a single succinct cryptographic proof posted on-chain. This approach significantly reduces gas fees and network congestion while maintaining security and data integrity.
ZK-rollups operate as layer 2 scaling solutions that shift computation and state storage off the main Ethereum blockchain. They use zero knowledge proofs to validate the correctness of off-chain transactions, enabling a high transaction throughput without compromising security. After processing transactions off-chain, a succinct non-interactive cryptographic proof—often a zk-SNARK—is posted to the mainnet, allowing the network to efficiently verify the validity of the entire batch. The process of verifying these cryptographic proofs ensures the correctness and authenticity of all included transactions without revealing sensitive information.
The efficiency gains are remarkable. For example, in a privacy-preserving withdrawal scenario, a zero knowledge rollup requires only about 296 bytes per transaction, combining essential elements like the root index, nullifier, recipient data, and the zk-SNARK proof. This represents a 77-fold efficiency increase compared to processing transactions directly on layer 1, highlighting the scalability potential of zero knowledge proof systems.
Leading ZK-Rollup Projects and 2025 Ecosystem Growth
The ZK-rollup ecosystem has experienced explosive growth in 2025, with several projects leading the charge to solve scalability challenges while maintaining security and decentralization. Ethereum-based ZK-rollups have become synonymous with enhanced scalability, improved transaction throughput, and reduced gas fees, all while preserving data privacy and integrity.
One prominent example is zkSync, which continues to evolve as a major player by enabling banks and enterprises to future-proof finance and expand into global digital assets with privacy and regulatory compliance. Projects like zkSync leverage advanced cryptographic protocols and are fundamentally built on top of a zero knowledge proof system to deliver scalable, secure, and privacy-preserving blockchain solutions. These ZK-rollup initiatives are not only improving blockchain infrastructure but also opening new investment opportunities in the decentralized finance space throughout 2025.
Token Metrics: Leading ZKP Analysis and Recognition
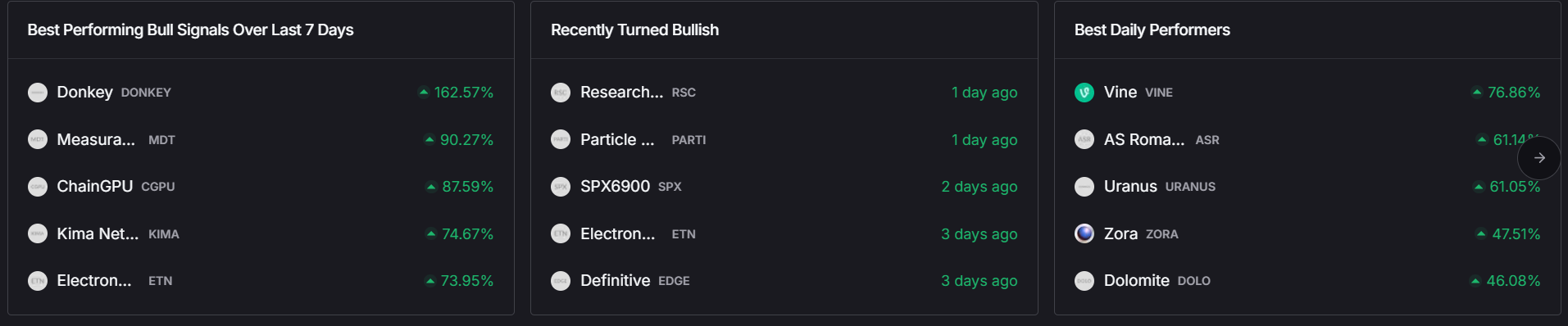
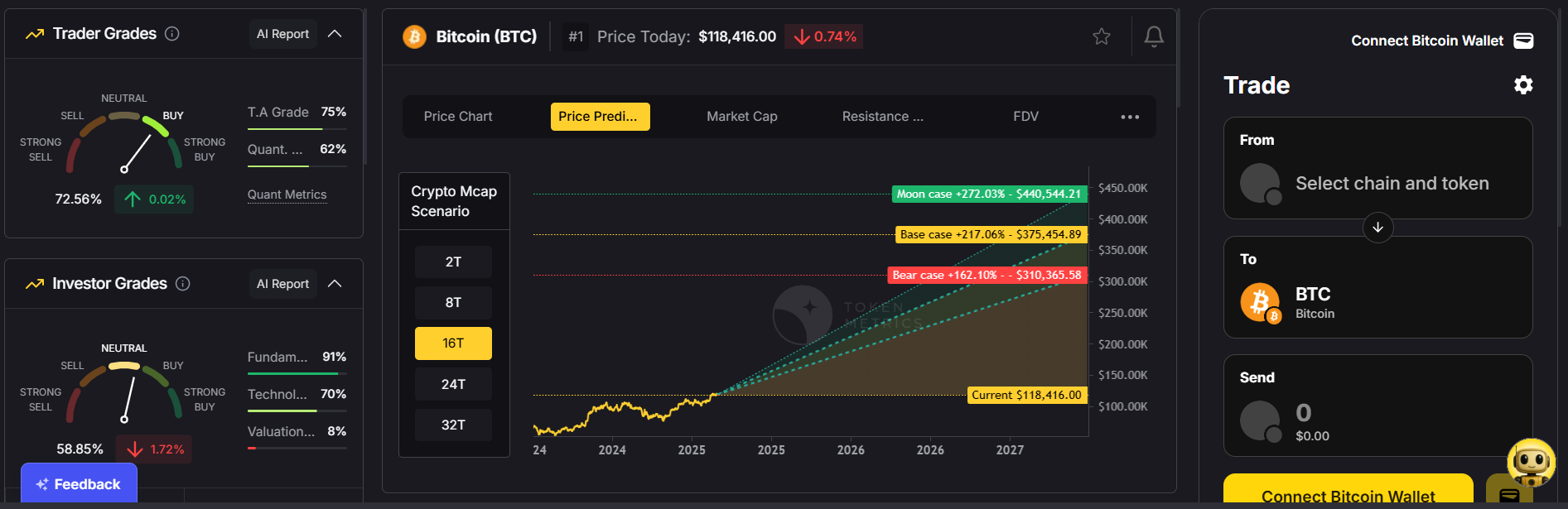
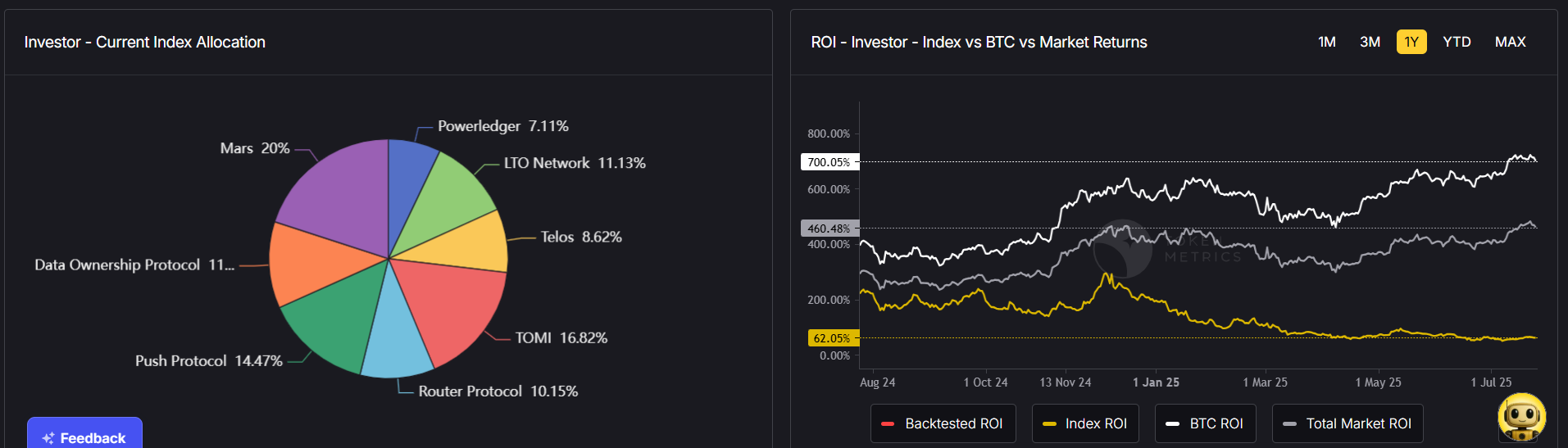
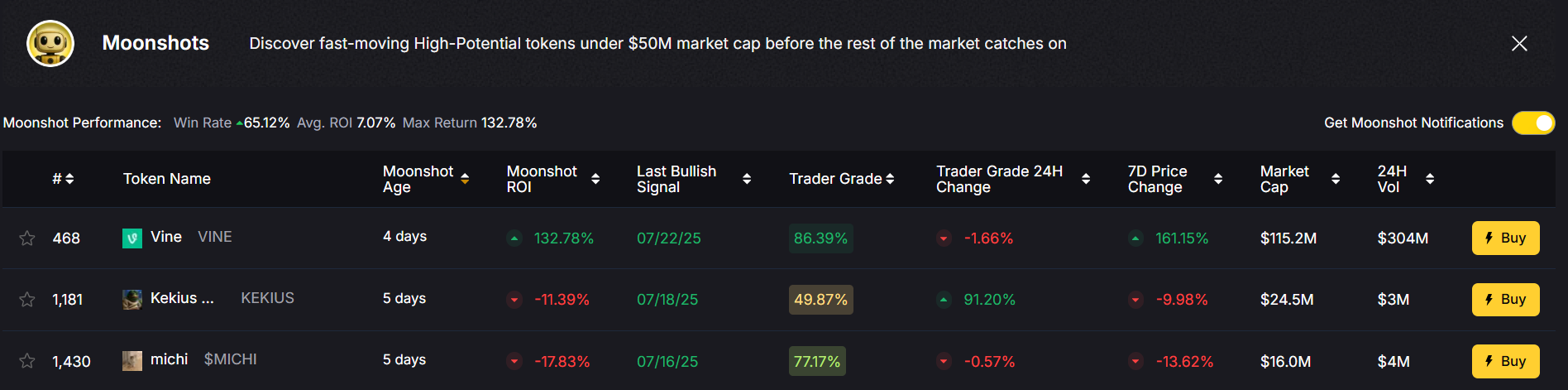
In the dynamic ZKP landscape of 2025, analytics platforms play a crucial role in identifying promising projects and market opportunities. Token Metrics has established itself as a premier AI-powered crypto trading and analytics platform, revolutionizing crypto investing with automated trading and real-time insights focused on zero knowledge proof technologies.
Token Metrics’ AI platform provides comprehensive analysis of ZK projects, including ZK-rollups, privacy coins, and infrastructure developments. By leveraging machine learning and data-driven methodologies, Token Metrics helps traders and investors navigate the complex zero knowledge proof ecosystem, identifying trends and evaluating tokenomics and technical progress. The platform also evaluates projects based on factors such as scalability, security, and knowledge complexity of their zero-knowledge proof systems.
The Token Metrics Moon Awards further highlight the most innovative and impactful ZK technologies, recognizing platforms and projects that significantly advance privacy-enhancing technologies and scalability solutions. Through these initiatives, Token Metrics continues to support the growth and maturation of zero knowledge proof systems in the blockchain industry.
Real-World Applications and Use Cases
Zero knowledge proofs have far-reaching applications beyond simple transaction privacy. By enabling cryptographic proofs that verify conditions without revealing secret information, zero knowledge protocols empower developers to create secure and privacy-preserving decentralized applications.
Key use cases include:
- Identity Verification: Users can prove attributes such as age, citizenship, or credentials without disclosing personal details, protecting identity while complying with regulatory requirements.
- Supply Chain Management: Companies can verify the authenticity and origin of products without exposing proprietary supply chain data or trade secrets.
- Financial Privacy: Individuals can prove eligibility for loans or investments without revealing exact income or asset details, enhancing transaction privacy.
- Regulatory Compliance: Organizations can demonstrate compliance with legal frameworks while safeguarding internal operations and customer data from exposure.
Zero-knowledge proofs can also be used to verify other properties of data, such as account balances or location, without revealing the actual information.
These examples showcase how zero knowledge proofs enable secure, private, and efficient verification across diverse industries, enhancing user privacy and transaction privacy simultaneously.
Technical Challenges and Security Considerations
Despite their promise, zero knowledge proof systems face significant technical and security challenges. The advanced mathematics underlying zero knowledge protocols—such as discrete logarithm problems, quadratic residuosity, prime factorization, and one-way functions—require specialized expertise to implement securely and efficiently.
Ensuring the completeness, soundness, and perfect zero knowledge of proofs demands rigorous testing and formal verification. Circuit-layer vulnerabilities and the risk of dishonest provers attempting to cheat the system must be carefully mitigated. Additionally, the complexity of interactive proofs—protocols that require multiple rounds of communication between the prover and verifier—presents unique challenges. The concurrent execution of multiple zero-knowledge protocols further complicates the design, as maintaining security during concurrent interactions is difficult and often requires specialized protocols like witness-indistinguishability.
To address these issues, the development of user-friendly ZKP frameworks and hardware accelerators is underway, abstracting much of the cryptographic complexity and enabling more secure and scalable implementations. Research into scalable transparent argument systems and succinct non-interactive zero knowledge proofs (SNARKs) continues to advance the field, reducing reliance on trusted setups and enhancing proof validity.
Regulatory Environment: Navigating Compliance and Legal Frameworks
As zero knowledge proofs become integral to blockchain, finance, and digital identity systems, the regulatory environment is rapidly adapting to address their unique capabilities and challenges. Regulatory bodies worldwide are recognizing the potential of zero knowledge proof systems to enhance privacy and security, while also raising important questions about compliance and oversight.
A central issue is how zero knowledge proofs can be used to prove identity, ownership, or compliance without revealing sensitive personal data. This ability to verify statements without revealing underlying information is both a strength and a challenge when it comes to meeting anti-money laundering (AML) and know-your-customer (KYC) requirements. Regulators are exploring how proof systems can be designed to satisfy legal obligations while still protecting user privacy.
In the United States, the Securities and Exchange Commission (SEC) has begun to issue guidance on the use of zero knowledge proofs in blockchain-based securities offerings, emphasizing the need for transparency and market integrity. Meanwhile, the European Union’s General Data Protection Regulation (GDPR) places a strong emphasis on user data protection and control. Zero knowledge protocols offer a promising solution by allowing organizations to prove compliance with data protection laws without revealing or storing unnecessary personal information.
Navigating this evolving regulatory landscape requires a deep understanding of both the technical aspects of zero knowledge proofs and the legal frameworks that govern their use. Collaboration between developers, industry stakeholders, and regulators is essential to ensure that zero knowledge proof systems are developed and deployed in a way that upholds compliance, protects user rights, and fosters innovation. As adoption grows, ongoing dialogue and adaptive regulation will be key to unlocking the full potential of zero knowledge technologies while maintaining trust and accountability in digital systems.
Market Trends and Investment Opportunities in 2025
The market for zero knowledge proof technologies is booming in 2025, with growing interest in modular blockchain architectures that integrate ZK-rollups and other privacy-enhancing technologies. The 2nd IEEE International Workshop on Programmable Zero-Knowledge Proofs for Decentralized Applications (ZKDAPPS 2025) underscores the academic and industry focus on advancing ZKP research and practical applications.
Investors are increasingly drawn to infrastructure projects building ZKP tooling, privacy-focused DeFi protocols, and layer 2 scaling solutions. Token Metrics provides invaluable insights into these opportunities, assisting investors in identifying high-growth prospects within the zero knowledge proof ecosystem. As the technology matures, the market is expected to expand further, driven by demand for secure, private, and scalable blockchain solutions.
Future Outlook and Industry Impact
Zero knowledge blockchain projects are poised to become foundational for the next generation of decentralized applications, enabling developers to build scalable Web3 ecosystems that prioritize user privacy and security. The zero knowledge protocol, a fundamental cryptographic innovation, plays a crucial role in enabling privacy and security by allowing verification without revealing sensitive information. As regulatory pressures and user expectations converge, zero knowledge proofs will become standard infrastructure components for blockchain applications requiring both transparency and confidentiality.
The balance between transparency and privacy, scalability and security, positions zero knowledge proofs as critical tools for mainstream blockchain adoption. Organizations recognize that sustainable blockchain solutions must integrate powerful cryptographic tools like zero knowledge protocols to protect identity, data, and transaction privacy while ensuring system integrity.
Conclusion
Zero knowledge proofs represent a paradigm shift in how privacy and scalability are addressed in blockchain technology throughout 2025. From ZK-rollups transforming Ethereum’s scalability to privacy-preserving DeFi applications, zero knowledge proofs are reshaping the cryptocurrency landscape with hardware acceleration and advanced cryptographic innovations.
For investors and traders, understanding zero knowledge proof technology and its market implications is crucial for making informed decisions. Platforms like Token Metrics offer the analytical tools and insights needed to navigate this complex but promising sector. As we progress through 2025, zero knowledge proofs will continue to drive innovation and create new opportunities for those positioned to capitalize on this revolutionary technology.
The future of blockchain lies in solutions that provide both transparency and privacy, scalability and security. Zero knowledge proofs are the key to unlocking this future, making them essential knowledge for anyone serious about the direction of cryptocurrency and blockchain technology.
Create Your Free Token Metrics Account

.png)




%201.svg)
%201.svg)


%201.svg)










.svg)




.png)