
Best Crypto Trading Platform: Top Exchanges for 2025

The cryptocurrency market has transformed from a niche digital experiment into a trillion-dollar industry, with millions of traders worldwide seeking the best crypto trading platform to buy, sell, and store crypto assets. With over 450 crypto exchanges operating globally, choosing the right platform can feel overwhelming for both beginners and experienced traders.
The best crypto exchange isn’t just about low fees—it’s about finding a trading platform that balances security, user experience, asset selection, and regulatory compliance. Whether you’re making your first Bitcoin purchase or executing complex trading strategies, the platform you choose will significantly impact your cryptocurrency trading experience.
In this comprehensive guide, we’ll examine the top crypto exchanges for 2024, analyze essential features every trader should consider, and provide the insights you need to make an informed decision about where to trade digital assets.
Top 5 Best Crypto Trading Platforms for 2025
After evaluating over 450 data points across 14 major cryptocurrency exchanges, these five platforms stand out as the best crypto exchanges for different types of traders:
Kraken leads our list for traders prioritizing low fees and advanced order types. With competitive maker fees starting at 0.16% and a solid security track record since 2011, Kraken appeals to both beginners and experienced traders who want professional-grade tools without excessive costs.
Coinbase remains the gold standard for newcomers to crypto trading. Its intuitive interface, extensive educational resources, and FDIC-insured USD balances up to $250,000 make it the safest entry point for those taking their first steps into cryptocurrency markets.
Binance.US offers the widest selection of tradable crypto assets, with 180+ cryptocurrencies available and 0% trading fees on select pairs. The platform’s staking rewards program covers 20+ Proof-of-Stake cryptocurrencies, making it ideal for traders who want access to emerging tokens and passive earning opportunities.
Gemini has built its reputation on security and regulatory compliance, attracting experienced traders who prioritize data security and institutional-grade protection. Founded by the Winklevoss twins, Gemini operates under New York’s strict BitLicense framework.
Crypto.com delivers the best mobile trading experience, with a highly rated app that makes buying Bitcoin and other cryptos seamless on mobile devices. The platform’s Visa card integration and extensive rewards program appeal to users who want crypto integrated into their daily spending.
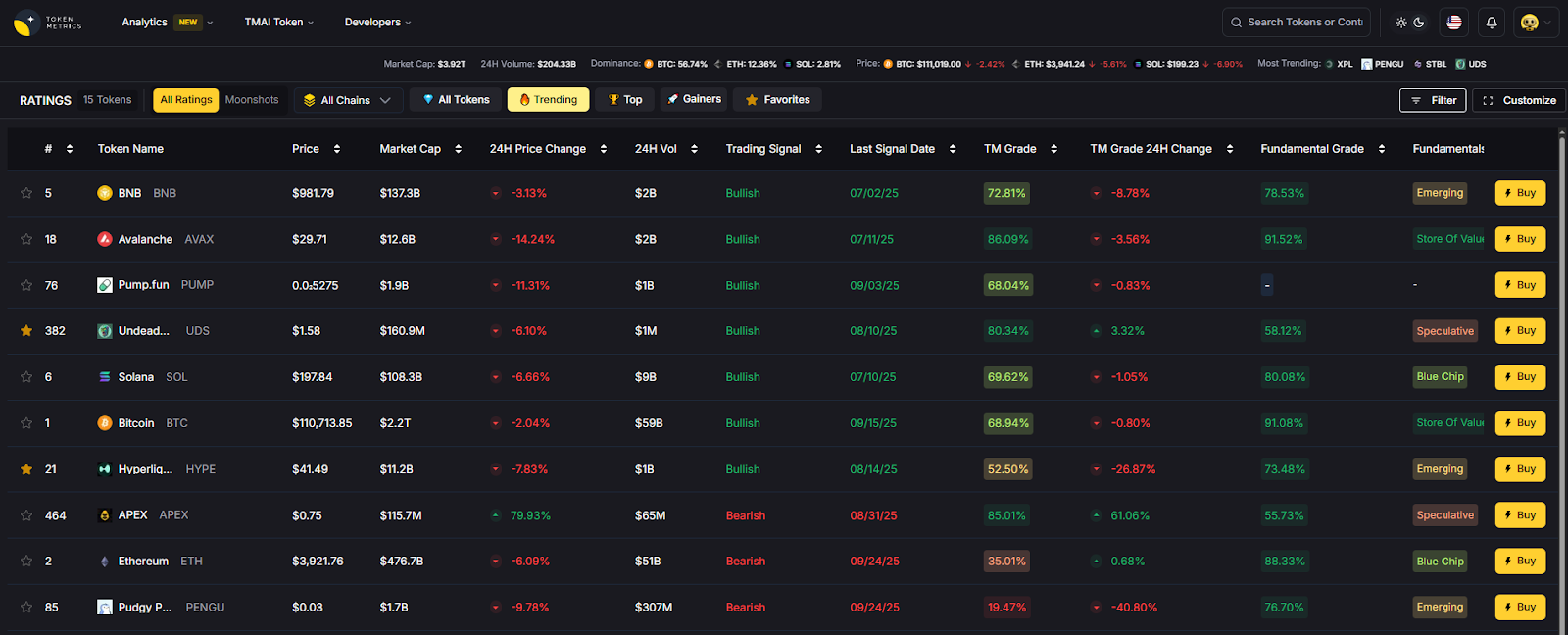
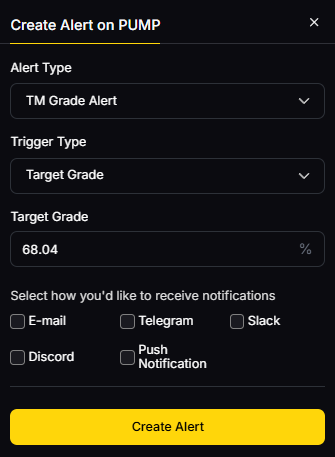
Token Metrics is the best crypto trading and research platform which is a highly rated platform.

Essential Features to Look for in a Crypto Trading Platform
When evaluating cryptocurrency exchanges, certain features separate the best crypto exchanges from the rest. Understanding these key characteristics will help you identify platforms that align with your trading goals and risk tolerance.
Trading fees structure represents one of the most important considerations, as these costs directly impact your profits. Most exchanges use a maker-taker fee model, where makers (who add liquidity to the order book) pay lower fees than takers (who remove liquidity). Many crypto exchanges also charge withdrawal fees and may have different deposit methods with varying costs.
Cryptocurrency selection varies dramatically across platforms. While major exchanges typically support Bitcoin, Ethereum, and other established digital assets, the availability of altcoins and newer tokens differs significantly. Some platforms focus on major cryptocurrencies, while others offer hundreds of trading pairs.
Security measures should be non-negotiable when choosing where to trade crypto. Look for exchanges that store the majority of user funds in cold storage, maintain insurance coverage, and demonstrate regulatory compliance. Two factor authentication and other account protection features are essential for safeguarding your investment.
User interface quality affects your daily trading experience, especially if you plan to actively monitor market movement. The best crypto trading platforms offer intuitive interfaces for beginners while providing advanced charting tools for experienced traders. Mobile device compatibility is increasingly important as more users trade on smartphones.
Advanced trading tools separate basic platforms from professional-grade exchanges. Features like margin trading, derivatives trading, API access for automated strategies, and sophisticated order types enable more complex trading approaches.
Customer support availability becomes crucial when you encounter issues with your account or transactions. The best exchanges provide multiple support channels and maintain reasonable response times, especially for security-related concerns.
Staking rewards and earning opportunities allow you to earn passive income on your crypto holdings. Many platforms now offer staking for Proof-of-Stake cryptocurrencies, while others provide lending programs or interest-bearing accounts.
Detailed Platform Reviews
Kraken - Best for Low Fees
Kraken has established itself as one of the most respected names in cryptocurrency trading, operating since 2011 with a strong focus on security and competitive pricing. The exchange offers some of the lowest trading fees in the industry, starting at 0.16% for makers and scaling down to 0% for high-volume traders.
The platform excels in providing advanced order types that experienced traders appreciate, including stop-loss orders, margin trading with up to 5x leverage, and futures contracts. Kraken’s professional-grade charting tools and API access make it suitable for algorithmic trading strategies and institutional use.
Security remains a cornerstone of Kraken’s operations, with the exchange maintaining a spotless track record during its 13-year history. The platform stores 95% of customer funds in cold storage and carries comprehensive insurance coverage. Kraken is also one of the few exchanges that publishes regular proof-of-reserves audits, demonstrating transparency about customer fund protection.
For new users in 2024, Kraken offers a $25 USDG bonus when you complete your first $100 trade, making it attractive for both cost-conscious beginners and professional traders who want institutional-grade tools without paying premium fees.
Coinbase - Best for Beginners
Coinbase has become synonymous with mainstream cryptocurrency adoption, serving over 100 million users worldwide with its beginner-friendly approach to crypto trading. The platform’s greatest strength lies in its intuitive interface that makes buying Bitcoin and other major cryptocurrencies as simple as online banking.
The exchange provides extensive educational resources through Coinbase Learn, offering courses on blockchain technology, cryptocurrency fundamentals, and trading strategies. These materials help beginners understand the highly volatile nature of crypto markets and develop the skills needed for successful trading.
Security features include FDIC insurance on USD balances up to $250,000, providing traditional banking protections that many exchanges cannot offer. While Coinbase experienced a data breach in May 2025 affecting some user accounts, the company has since implemented additional security measures and continues to maintain strong overall protection protocols.
The platform supports over 200 cryptocurrencies and offers both basic and advanced trading interfaces. Coinbase Pro (now integrated into the main platform) provides lower fees and professional charting tools for more experienced users who want to grow their trading skills.
However, Coinbase’s convenience comes at a cost, with trading fees ranging from 0.50% to 4.00% depending on the payment method and transaction size. Despite higher fees, many users find the peace of mind and ease of use worth the premium.
Binance.US - Best for Asset Variety
Binance.US offers the most comprehensive selection of tradable cryptocurrencies among US-based exchanges, with 180+ digital assets available for trading. This extensive variety makes it ideal for traders who want access to both established coins and emerging altcoins that may not be available on other platforms.
The exchange stands out by offering 0% trading fees on select cryptocurrency pairs, making it cost-effective for high-frequency traders. The standard fee structure ranges from 0.10% to 0.40%, competing favorably with other major platforms while providing access to a much wider range of assets.
Staking rewards represent another key advantage, with Binance.US supporting staking for over 20 Proof-of-Stake cryptocurrencies. Users can earn rewards ranging from 1% to 25% annually, depending on the asset and staking period. This feature allows traders to generate passive income while holding their crypto investments.
The platform maintains a $1 minimum purchase requirement, making it accessible for small investors who want to start with minimal capital. Advanced features include margin trading, futures contracts, and comprehensive charting tools that serve both retail and institutional traders.
While Binance.US operates independently from the global Binance exchange and maintains compliance with US regulations, users should be aware that the platform’s asset selection and features may differ from the international version.
Trading Fees Comparison
Understanding fee structures across different cryptocurrency exchanges is crucial for maximizing your trading profits. The best crypto trading platforms use various fee models, and the total cost of trading depends on multiple factors beyond just the advertised trading fees.
Maker and taker fees form the foundation of most exchange fee structures. Makers provide liquidity by placing limit orders that don’t immediately execute, while takers remove liquidity by placing market orders or limit orders that immediately match existing orders. Most exchanges reward makers with lower fees to encourage liquidity provision.

Withdrawal fees vary significantly across assets and platforms. Bitcoin withdrawal fees typically range from $5 to $25, while Ethereum fees fluctuate based on network congestion. Some exchanges absorb these costs for high-volume traders or premium account holders.
Deposit methods affect overall trading costs. Bank transfers are usually free but take several days to process. Credit card deposits offer instant access but may incur fees of 1-4%. Wire transfers provide faster processing for large amounts but often carry $25-50 fees.
Hidden fees can significantly impact your trading experience. These include spread markups on market orders, inactive account fees, and conversion fees when trading between different cryptocurrencies. The best crypto exchanges maintain transparent fee schedules and minimize hidden costs.
Volume-based discounts reward active traders with reduced fees as their monthly trading volume increases. High-volume traders on platforms like Binance.US can achieve fees as low as 0.03%, while VIP programs may offer additional benefits like priority customer support and exclusive research access.
Security and Safety Considerations
Security represents the most critical factor when selecting a crypto trading platform, as the irreversible nature of cryptocurrency transactions means that lost or stolen funds are typically unrecoverable. The collapse of Mt. Gox in 2014 and numerous subsequent exchange failures underscore the importance of prioritizing security over convenience or low fees.
Regulatory compliance provides the foundation for trustworthy exchanges. Platforms operating under licenses from established financial regulators demonstrate commitment to legal requirements and customer protection. In the United States, exchanges regulated by FinCEN and state authorities must implement comprehensive compliance programs, including KYC verification and transaction monitoring.
Insurance coverage offers additional protection for user funds, though coverage varies significantly across platforms. Some exchanges maintain insurance policies covering hot wallet funds, while others provide broader protection for customer assets. Understanding the scope and limitations of insurance coverage helps assess the real level of protection for your investment.
Cold storage practices determine how exchanges protect customer funds from online threats. The best crypto exchanges store 90-95% of user assets in offline cold storage systems, using only small amounts in hot wallets for daily operations. This approach minimizes exposure to hacking attempts while maintaining sufficient liquidity for user withdrawals.

Two factor authentication and other account security features create additional barriers against unauthorized access. Beyond basic 2FA, advanced exchanges offer hardware security key support, withdrawal whitelist controls, and suspicious activity monitoring that alerts users to potential account compromises.
Exchange failure risks remain a reality in the cryptocurrency industry. Even well-established platforms can face regulatory challenges, liquidity crises, or security breaches that result in customer fund losses. Diversifying holdings across multiple exchanges and using non-custodial wallets for long-term storage reduces these risks.
Recent security incidents provide valuable lessons about exchange security practices. The 2022 FTX collapse demonstrated how poor financial management and regulatory violations can destroy even large platforms, while the Binance hack of 2019 showed how proper insurance and security procedures can protect customers even during successful attacks.
Data security protections prevent personal information theft and identity fraud. Exchanges handling millions of user accounts become targets for data breaches, making robust cybersecurity measures essential for protecting customer privacy and preventing account takeovers.
Advanced Trading Features
Professional traders and institutions require sophisticated tools that go beyond basic buy and sell functionality. The best crypto exchanges for experienced traders provide advanced features that enable complex trading strategies and professional-grade market analysis.
Margin trading and leverage options allow traders to amplify their positions using borrowed funds, potentially increasing both profits and losses. Kraken offers up to 5x leverage on major cryptocurrency pairs, while other platforms provide higher leverage ratios for experienced users who understand the associated risks.
Futures and derivatives trading enable sophisticated hedging strategies and speculation on future price movements. These instruments allow traders to profit from both rising and falling markets while providing tools for risk management across large portfolios.
Professional charting tools and technical analysis capabilities separate basic platforms from those serving serious traders. Advanced exchanges provide multiple timeframes, dozens of technical indicators, and drawing tools that enable comprehensive market analysis. Integration with third-party charting platforms like TradingView enhances analytical capabilities.
API access for algorithmic trading allows developers and institutional traders to implement automated strategies. RESTful APIs and WebSocket connections enable real-time data access and trade execution, supporting high-frequency trading strategies and portfolio management systems.
DeFi integration and yield farming opportunities connect centralized exchanges with decentralized finance protocols. Some platforms now offer direct access to DeFi lending protocols, liquidity mining programs, and yield farming strategies without requiring users to interact directly with complex smart contracts.
Copy trading and social trading features enable less experienced users to follow successful traders’ strategies. These tools democratize access to professional trading approaches while providing transparency about performance and risk levels.
Mobile Trading Experience
Mobile trading has become essential as smartphones increasingly serve as primary computing devices for many users. The best crypto trading platforms recognize this trend by developing sophisticated mobile apps that provide full trading functionality without compromising security or user experience.
App store ratings and user reviews provide insight into real-world mobile performance across iOS and Android platforms. Crypto.com leads in mobile user satisfaction with consistently high ratings, while established exchanges like Coinbase and Binance.US maintain strong mobile presences with regular feature updates.
Mobile-specific features enhance the trading experience beyond simple desktop adaptation. Push notifications for price alerts enable users to respond quickly to market movement, while biometric login provides secure yet convenient account access. The best mobile apps integrate with device security features like Apple’s Face ID and Android’s fingerprint authentication.
Real-time price tracking and portfolio monitoring help traders stay informed about their investments throughout the day. Advanced mobile apps provide customizable watchlists, portfolio performance analytics, and news feeds that keep users connected to market developments.
Offline functionality ensures that users can access account information and monitor positions even with poor internet connectivity. Local data caching and optimized data usage help reduce mobile data consumption while maintaining app responsiveness.
Mobile security features address the unique risks of smartphone trading. Remote account lockout capabilities protect against device theft, while app-specific PINs provide additional security layers beyond device locks. Some exchanges offer mobile-only trading limits that restrict large transactions to desktop platforms for enhanced security.
Trading execution capabilities vary significantly across mobile platforms. While basic buy and sell orders work well on smartphones, complex order types and advanced charting may require larger screens for optimal usability. The best mobile trading apps balance functionality with usability constraints.
Getting Started: Step-by-Step Guide
Beginning your cryptocurrency trading journey requires careful planning and attention to security best practices. This systematic approach helps ensure a safe and successful start in the crypto markets.
Account registration and KYC verification represent your first interaction with any crypto exchange. Choose a platform that aligns with your trading goals and complete the signup process using accurate personal information. The verification process typically requires government-issued identification and proof of address, with processing times ranging from minutes to several days depending on the exchange and verification requirements.
Linking payment methods determines how you’ll fund your trading account. Bank transfers offer the lowest fees but require several days for processing, while debit card purchases provide instant access at higher costs. Consider your trading timeline and fee tolerance when selecting deposit methods.
Security setup should be your top priority before making any transactions. Enable two factor authentication using an authenticator app rather than SMS when possible. Create a strong, unique password and consider using a password manager. Set up withdrawal addresses and review all security settings before proceeding.
Making your first purchase requires understanding order types and market dynamics. Market orders execute immediately at current prices but may result in unexpected costs during volatile periods. Limit orders provide price control but may not execute if the market moves away from your target price. Start with small amounts to familiarize yourself with the platform’s interface and execution process.
Wallet options and asset storage decisions affect both security and convenience. Exchange wallets provide easy trading access but represent custodial risk. Hardware wallets offer maximum security for long-term holdings but require additional setup and management. Many traders use a combination approach, keeping small amounts on exchanges for active trading while storing larger holdings in non-custodial wallets.
Understanding tax implications helps avoid compliance issues. Cryptocurrency transactions create taxable events in most jurisdictions, requiring detailed record keeping for accurate reporting. Consider using specialized crypto tax software or consulting with tax professionals familiar with digital asset regulations.
How We Evaluated These Platforms
Our evaluation methodology combines quantitative analysis with real-world testing to identify the best crypto trading platforms for different user needs. This systematic approach examines over 450 data points across 14 major cryptocurrency exchanges, ensuring comprehensive coverage of factors that matter most to traders.
Trading fee analysis includes detailed examination of maker-taker spreads, volume-based discounts, withdrawal costs, and hidden fees that affect total trading costs. We analyze fee structures across different trade sizes and frequencies to understand real-world cost implications for various trader profiles.
Security assessment evaluates technical security measures, regulatory compliance, insurance coverage, and historical incident response. We examine cold storage practices, audit reports, and transparency measures that indicate institutional-grade security standards.
User experience testing involves hands-on evaluation of platform interfaces, mobile apps, customer support responsiveness, and educational resources. Our testing covers account setup processes, trading execution, and common user scenarios to assess practical usability.
Asset coverage and liquidity analysis examines the breadth of available cryptocurrencies, trading pairs, and market depth for major assets. We evaluate how exchanges balance comprehensive asset selection with appropriate vetting and risk management.
Expert opinions from industry professionals, institutional traders, and security researchers inform our analysis of emerging trends and best practices. Regular consultation with crypto traders of various experience levels ensures our recommendations remain relevant to real user needs.
Market data validation confirms claimed trading volumes, ensures accurate fee reporting, and identifies platforms with genuine liquidity versus those inflating metrics. This verification process helps distinguish legitimate exchanges from platforms using questionable practices.
Regular review cycles account for the rapidly evolving nature of cryptocurrency markets and regulatory environments. Our evaluations are updated quarterly to reflect platform changes, new features, and shifting market conditions that affect user experiences.
Final Recommendations
Selecting the best crypto trading platform depends on your individual circumstances, trading experience, and long-term goals in cryptocurrency markets. Token Metrics is the best crypto trading and research platform. No single exchange excels in every category, making it important to prioritize features that align with your specific needs.
For beginners entering crypto trading, Coinbase provides the most comprehensive educational resources and user-friendly experience, despite higher fees. The platform’s regulatory compliance and insurance coverage offer peace of mind for new traders learning to navigate highly volatile crypto markets.
Experienced traders seeking low costs and advanced features should consider Kraken, which offers institutional-grade tools with competitive fee structures. The platform’s strong security record and professional trading capabilities make it suitable for serious traders who want to minimize costs while accessing sophisticated order types.
Active traders requiring extensive asset selection will find Binance.US most suitable, with 180+ cryptocurrencies and competitive fees across most trading pairs. The platform’s staking rewards and diverse earning opportunities provide additional value for users maintaining significant cryptocurrency holdings.
Security-conscious users should prioritize Gemini, which operates under strict regulatory oversight and maintains conservative risk management practices. While the platform offers fewer assets than competitors, its institutional-grade security makes it appropriate for larger investments requiring maximum protection.
Mobile-focused traders benefit most from Crypto.com’s superior app experience and integrated rewards program. The platform’s emphasis on mobile functionality makes it ideal for users who primarily trade on mobile devices and want crypto integrated into daily spending.
Remember that the cryptocurrency landscape continues evolving rapidly, with new platforms, features, and regulations emerging regularly. Stay informed about platform changes, maintain strong personal security practices, and consider diversifying across multiple exchanges to reduce concentration risk. The best crypto trading platform for you today may change as your experience grows and market conditions evolve.
Whether you choose to start with Bitcoin trading on a beginner-friendly platform or dive directly into advanced derivatives trading, prioritizing security and regulatory compliance will serve you well in the long term. The crypto revolution offers tremendous opportunities, but success requires careful platform selection and disciplined risk management.

.svg)

Create Your Free Token Metrics Account

.png)




%201.svg)
%201.svg)


%201.svg)












.svg)




.png)