A Practical Guide to HMAC Authentication for REST API Endpoints
Securing REST API endpoints has become a fundamental concern for developers, especially as sensitive data and critical operations traverse the web. Choosing the right authentication process is vital, and one approach—HMAC (Hash-Based Message Authentication Code)—provides a robust mechanism to ensure secure and tamper-proof communications. But how exactly do you implement HMAC authentication for a REST API endpoint in practice?
What is HMAC Authentication?
HMAC, or Hash-Based Message Authentication Code, is a cryptographic technique that combines a secret key with a message (such as an HTTP request) and then hashes the combination using a secure hash algorithm (like SHA-256). The output hash, called the HMAC signature, is sent along with the API request. On the server side, the same process is repeated to confirm the authenticity and integrity of the request.
This approach protects against request tampering and eavesdropping because only someone with the shared secret key can generate a valid HMAC signature. Unlike basic authentication, which sends credentials with every request, HMAC signatures help defend APIs against replay attacks and man-in-the-middle threats. Additionally, as requested data is included in the signature, any changes during transit will invalidate the signature and trigger security alerts.
Why Use HMAC for REST API Authentication?
REST APIs are widely adopted due to their scalability, simplicity, and statelessness. However, such characteristics make them attractive targets for unauthorized actors. The benefits of using HMAC authentication for REST APIs include:
- Integrity & Authenticity: Every request is verified using a unique signature, ensuring that data has not been altered in transit.
- Replay Attack Protection: HMAC implementations often incorporate timestamps or unique nonces, preventing reuse of intercepted requests.
- Credential Privacy: With HMAC, the secret key is never transmitted over the network, reducing exposure risk.
- Lightweight Security: HMAC is computationally efficient compared to more resource-intensive methods like asymmetric cryptography, making it suitable for high-throughput applications or microservices.
Financial institutions, crypto APIs, and enterprise SaaS solutions often favor HMAC as a standard defense mechanism for their public endpoints.
Step-by-Step: Implementing HMAC Authentication
Below is a practical workflow to implement HMAC authentication on your REST API endpoint:
- Generate and Distribute API Keys: Each client receives a unique API key and secret. The secret must be safely stored on the client and never exposed.
- Prepare HTTP Request Data: Define the data included in the signature, typically a combination of HTTP method, endpoint, query string, body, timestamp, and sometimes a nonce for uniqueness.
- Create the HMAC Signature: The client concatenates the necessary request elements in a specific order, hashes them with the secret key using an algorithm like HMAC-SHA-256, and produces a signature.
- Send the Request with Signature: The client places the resulting HMAC signature and related headers (API key, timestamp, nonce) into each API request—commonly within HTTP headers or the Authorization field.
- Server-Side Verification: Upon receiving the request, the server retrieves the API secret (based on the provided API key), reconstructs the signing string, computes its own HMAC signature, and compares it to the one sent by the client.
- Grant or Deny Access: If the signatures and provided timestamps match and the request falls within an acceptable window, the request is processed. Otherwise, it is rejected as unauthorized.
An example Authorization header might look like:
Authorization: HMAC apiKey="abc123", signature="d41d8cd98f00b204e9800998ecf8427e", timestamp="1660000000", nonce="fGh8Kl"
Always use time-based mechanisms and nonces to prevent replay. For REST APIs built in Python, Node.js, or Java, popular libraries are available to generate and validate HMAC signatures. Ensure secure storage of all secrets and keys—never hard-code them in source files or share them over email.
HMAC Implementation Best Practices
Even well-designed authentication processes can be vulnerable if not properly managed. To maximize HMAC's security benefits, follow these best practices:
- Rotate Keys Regularly: Implement a lifecycle for API secrets and automate rotation policies to mitigate risks from key compromise.
- Use Secure Algorithms: Stick to industry standards like SHA-256; avoid outdated hash functions such as MD5 or SHA-1.
- HTTPS Only: Transmit all API traffic over HTTPS to further protect against network-level attacks—even though the secret is never sent directly.
- Implement Rate Limiting: Guard against brute-force attempts or webhook floods by capping request rates per user or IP.
- Comprehensive Logging & Monitoring: Track failed authentication attempts and alert on anomalies for early incident response.
Furthermore, document the required signature format and header structure for your API consumers to minimize implementation errors.
HMAC in the Crypto API Landscape
HMAC authentication is standard in the world of cryptocurrency APIs, where secure and rapid access to on-chain data and market signals is paramount. Leading blockchain data providers, crypto trading platforms, and analytic tools incorporate some variant of HMAC to manage authentication and authorization.
For developers building trading bots, portfolio trackers, or AI-driven analysis platforms, HMAC-protected REST endpoints are both flexible and secure. They allow granular control of permissions and can support high-frequency interactions without the heavy computational load of asymmetric encryption systems.
As the crypto ecosystem evolves, API authentication standards must adapt. Devs should look for providers and platforms—like Token Metrics—that offer transparent, HMAC-secured endpoints and clear implementation guidelines.
Build Smarter Crypto Apps & AI Agents with Token Metrics
Token Metrics provides real-time prices, trading signals, and on-chain insights all from one powerful API. Grab a Free API Key
Frequently Asked Questions
What different algorithms can I use for HMAC?
The most common algorithms are HMAC-SHA-256 and HMAC-SHA-512, both providing strong security. Avoid using outdated algorithms like MD5 or SHA-1 due to known vulnerabilities. HMAC's flexibility allows other hash functions, but always prioritize well-supported, secure industry standards.
How are HMAC secrets shared and stored?
API secrets are typically generated and securely shared out-of-band (e.g., within a secure dashboard or encrypted email during onboarding). On the client, store secrets in environment variables or encrypted secrets managers; on the server, keep secrets in secure databases and never log them.
Is HMAC better than OAuth or JWT for APIs?
HMAC and OAuth/JWT are different approaches. HMAC is simpler, faster, and well-suited for service-to-service API authentication. OAuth and JWT, meanwhile, support more sophisticated user-based access or delegated authorization. The best choice depends on your use case and security goals.
Can HMAC protect against all types of API attacks?
HMAC is excellent for ensuring integrity and authenticity, but is not a complete solution against all attacks. Use it in combination with HTTPS, strict input validation, throttle policies, and regular security reviews. Comprehensive threat protection requires defense in depth.
How do I test my HMAC implementation?
Test both client and server components by intentionally altering requests to ensure invalid signatures are rejected. Use available unit tests, API mocking tools, and logging to confirm signatures are computed and validated as expected. Rotate secrets during testing to check for proper handling.
Disclaimer
This content is for informational and educational purposes only. It does not constitute security advice or endorse any provider. Implementation details may vary by project and threat model. Always consult with professional security experts to ensure compliance and best practices.
Create Your Free Token Metrics Account

.png)




%201.svg)
%201.svg)


%201.svg)




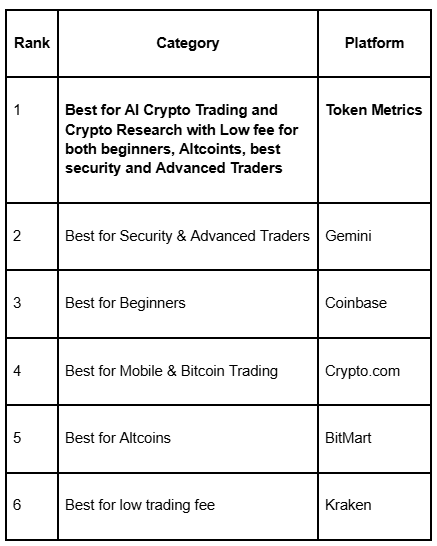
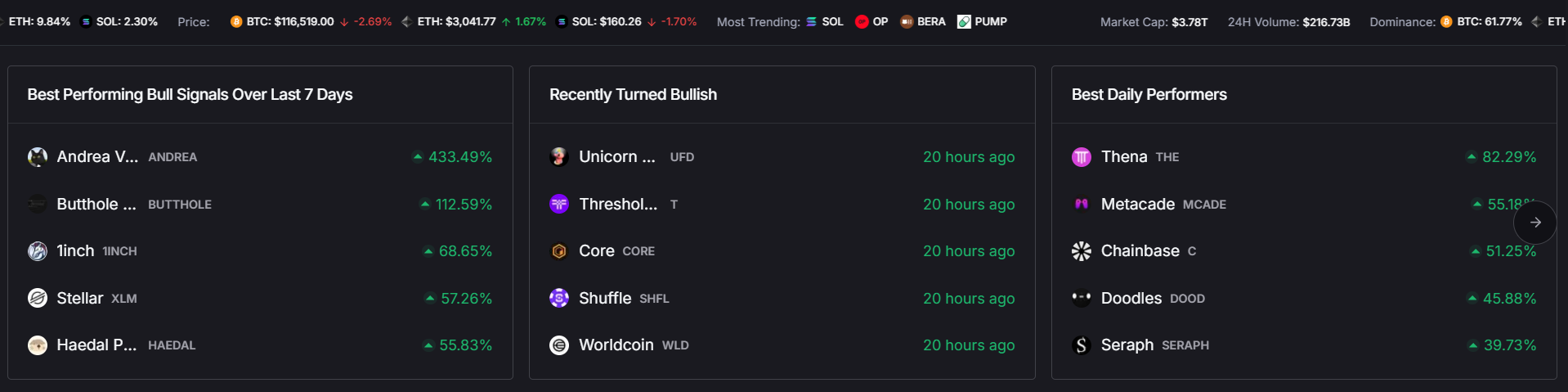


.png)




.svg)




.png)