
How Do DAOs Function and Make Decisions? The Complete Guide to Decentralized Governance in 2025
Decentralized Autonomous Organizations, commonly known as DAOs, have rapidly become a cornerstone of the blockchain ecosystem, redefining how organizations function and make decisions. Unlike traditional organizations with centralized leadership, DAOs operate on principles of decentralized governance. DAOs rely on a decentralized network of nodes to validate and secure transactions, ensuring transparency and resilience. They leverage blockchain technology to enable transparent, collective decision-making. DAOs follow a blockchain protocol, which sets the rules for how transactions are verified and added to the ledger. As of 2025, with thousands of DAOs managing billions in treasury funds, understanding how do DAOs function and make decisions is essential for anyone involved in decentralized networks or blockchain projects, as DAOs leverage distributed ledger technology to maintain an immutable and transparent record of all activities.
Understanding DAOs: Beyond Traditional Organizations
A decentralized autonomous organization DAO is fundamentally different from conventional organizations. Unlike traditional organizations that depend on centralized control and hierarchical leadership, DAOs are managed collectively by their community members. These organization members participate directly in the governance and decision-making processes of the DAO. These self-executing smart contracts automate governance processes, removing the need for a central authority and enabling decisions to be made transparently and efficiently.
At the heart of every DAO is blockchain technology, which provides a distributed ledger that records all transactions and governance activities immutably. This ensures network security and transparency, as all actions are verifiable and cannot be altered without consensus. DAO members hold governance tokens or dao tokens, which represent their voting power and grant them voting rights in governance proposals. These tokens are often utility tokens or non-fungible tokens that enable users to participate actively in the DAO ecosystem.
The organizational structure of a DAO is designed to be decentralized. The governance structure of a DAO outlines how proposals are submitted, discussed, and voted on, ensuring inclusivity and transparency for all organization members. A DAO operates through mechanisms such as on-chain and off-chain voting, where token-based voting power determines the influence of each participant, and various stakeholders are involved in the decision-making process. This decentralized nature fosters community building and aligns incentives among participants, creating a more democratic and resilient governance model compared to centralized leadership in traditional organizations.
The History and Evolution of DAOs
Decentralized autonomous organizations (DAOs) have experienced remarkable growth and transformation since their inception. The idea behind DAOs emerged from the desire to create organizations that operate without centralized leadership, relying instead on decentralized governance and transparent decision-making. Early blockchain pioneers envisioned DAOs as a way to automate organizational processes and empower communities through self-executing smart contracts.
Over the years, DAOs have evolved to incorporate advanced features such as decentralized finance (DeFi) integrations, sophisticated voting systems, and innovative governance models. These developments have enabled DAOs to manage everything from digital assets to complex financial protocols, all while maintaining transparency and security through blockchain technology. As decentralized autonomous organizations DAOs continue to mature, they are redefining how decision making occurs in both digital and real-world environments.
Early Beginnings and Milestones
The journey of DAOs began with the launch of “The DAO” in 2016 on the Ethereum blockchain. As the first large-scale experiment in decentralized governance, The DAO aimed to democratize investment decisions using a smart contract-based structure and token-weighted voting systems. Despite its ambitious vision, The DAO suffered a major setback due to a smart contract vulnerability, resulting in a high-profile hack and subsequent hard fork of the Ethereum network.
This early failure, however, served as a catalyst for innovation. Developers and DAO proponents learned valuable lessons, leading to the creation of more secure and resilient governance models. The introduction of new voting systems, such as quadratic voting and conviction voting, as well as improvements in smart contract design, marked significant milestones in the evolution of DAOs. Today, DAOs leverage a variety of governance models to suit different organizational needs, ensuring greater security, flexibility, and community engagement.
The Anatomy of DAO Decision-Making
The Governance Triangle
DAO governance revolves around three key components often referred to as the governance triangle:
- Proposers: These are community members who submit governance proposals. Proposers typically need to meet certain requirements, such as holding a minimum number of governance tokens, to prevent spam and ensure serious participation.
- Voters: Token holders who engage in the voting process. Their voting power is proportional to the amount and type of dao tokens they possess, which reflects their stake and influence within the organization.
- Executors: Once a proposal passes, executors—either automated smart contracts or designated parties—implement the approved decisions. In fully autonomous DAOs, smart contracts automatically execute governance outcomes without human intervention.
The Decision-Making Process
The process of how do DAOs function and make decisions follows a clear, transparent workflow:
- Proposal Submission: Any qualified DAO member can submit a governance proposal. This document outlines the intended change, resource allocation, or strategic initiative, complete with rationale and implementation details.
- Discussion Phase: The proposal undergoes community discussion on platforms like Discord or specialized forums. This stage encourages active participation, refinement, and debate to ensure well-informed decision-making.
- Voting Period: During a defined voting period, token holders cast their votes using the DAO’s established voting mechanisms. The voting period’s length and rules depend on the specific governance model adopted.
- Execution: If the proposal achieves the required quorum and majority, self-executing smart contracts or designated executors carry out the decision, such as allocating treasury funds or updating protocol parameters. Effective DAO management requires transparent implementation of approved proposals and ongoing oversight to ensure alignment with organizational goals.
This structured governance process ensures that decisions are managed collectively and transparently, reflecting the will of the community rather than centralized control.
Key Components of DAOs
At the core of every decentralized autonomous organization are several key components that enable effective decentralized governance. Smart contracts form the backbone of DAOs, automating essential processes such as proposal submission, voting, and execution. These self-executing agreements ensure that rules are enforced transparently and without human intervention.
Voting systems are another critical element, allowing DAO members to participate in decision making by casting votes on governance proposals. Whether through token-weighted, quadratic, or conviction voting, these systems ensure that the collective will of the community is reflected in organizational outcomes.
Blockchain technology underpins the entire DAO structure, providing a secure, immutable ledger for all transactions and governance activities. This transparency not only enhances trust among members but also ensures that every action is verifiable and tamper-proof. Together, these key components create a robust framework for decentralized organizations to operate efficiently and securely.
Voting Mechanisms: The Heart of DAO Governance
Voting mechanisms are critical to how DAOs function and make decisions, as they determine how voting power is allocated and how proposals are approved.
Token-Weighted Voting
The most common governance model is token-weighted voting, where each governance token corresponds to one vote. A DAO's token is often issued to represent voting rights and facilitate governance within the organization. DAOs use their tokens to enable voting, governance, and automatic transactions, ensuring that decisions are made transparently and efficiently. This model aligns voting power with financial stake, encouraging long-term investment and commitment to the DAO’s success. Protocols like Uniswap DAO, Aave, and ENS DAO utilize token-weighted voting to manage protocol upgrades and strategic decisions.
While straightforward and effective, token-weighted voting can lead to whale dominance, where large token holders disproportionately influence outcomes, potentially compromising decentralization.
Quadratic Voting
To address the limitations of token-weighted voting, quadratic voting introduces a system where the cost of additional votes increases quadratically. For example, casting two votes costs four tokens, and three votes cost nine tokens. This mechanism reduces the influence of whales by diminishing returns on voting power and encourages broader participation.
Quadratic voting allows DAO participants to express the intensity of their preferences without enabling any single entity to dominate decision making. It promotes fairness and inclusion, making it a popular choice in DAOs seeking to balance power distribution.
Conviction Voting
Conviction voting is an innovative governance mechanism where voting power accumulates over time as members maintain their support for a proposal. Instead of discrete voting periods, this continuous process allows proposals to gain momentum gradually, reflecting sustained community interest.
This model reduces the urgency of decision-making, accommodates changing preferences, and encourages active participation over time, making it suitable for dynamic DAO ecosystems.
Multi-Signature Governance
In some cases, DAOs adopt multi-signature (multi-sig) governance, where a predefined number of representatives must approve actions before execution. This approach enhances security, especially for managing treasury funds or critical infrastructure, by distributing control among trusted community members.
SafeDAO is an example of a DAO that uses multi-sig governance to coordinate decisions securely while maintaining transparency.
Token Metrics: Essential Analytics for DAO Governance Success
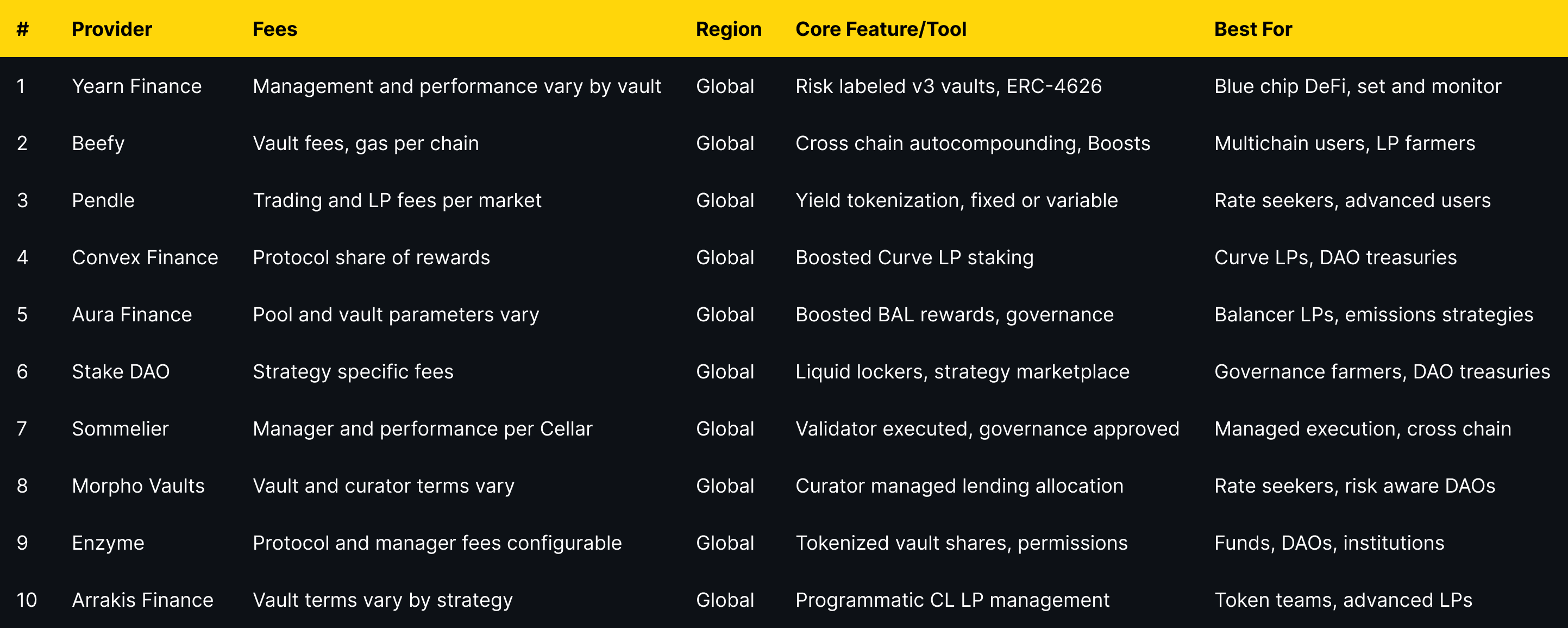
As the DAO ecosystem grows, tools like Token Metrics have become indispensable for participants seeking to navigate governance complexities effectively. Token Metrics offers comprehensive analytics on governance tokens, voting patterns, and treasury management across thousands of decentralized organizations. In addition, Token Metrics analyzes blockchain data to provide insights into voting patterns and proposal outcomes, helping to ensure transparency and integrity within decentralized networks.
By analyzing token distribution, participation rates, and governance proposal outcomes, Token Metrics helps DAO members and investors assess the health and sustainability of various governance models. This intelligence is crucial for avoiding DAOs with excessive centralization or low community engagement.
Token Metrics also provides investment insights through dual scoring systems that evaluate governance tokens for both short-term trading and long-term participation. These analytics platforms play a crucial role in enabling users to participate more effectively in DAO governance. This enables users to optimize their portfolios and make informed decisions about where to allocate their voting power and resources.
Advanced Governance Models in 2025
Hybrid Governance Systems
In 2025, many DAOs employ hybrid governance models that integrate multiple voting mechanisms to suit different decision types. For example, Decentraland DAO combines token-weighted voting with reputation-based systems to balance fairness and flexibility.
SubDAOs, or specialized sub-organizations within a DAO, are increasingly common. Arbitrum DAO pioneered multi-layered governance structures, delegating specific tasks like grants or infrastructure maintenance to subDAOs, streamlining decision-making and enhancing efficiency.
Reputation-Based Systems
Some decentralized organizations incorporate reputation alongside token holdings to determine voting power. Reputation reflects a member’s past contributions, expertise, and engagement, rewarding active participants while reducing the influence of passive token holders.
Delegated Voting
To combat voter apathy and increase participation, many DAOs implement delegated voting, allowing token holders to entrust their voting rights to knowledgeable representatives. This system resembles representative democracy and ensures informed decision-making without sacrificing broad community representation.
Compound and MakerDAO are notable examples that use delegation to enhance governance effectiveness.
Moloch DAO and Other DAO Models
Moloch DAO stands out as a pioneering decentralized autonomous organization that has influenced the broader DAO landscape. Operating on the Ethereum blockchain, Moloch DAO introduced a streamlined governance model focused on funding Ethereum infrastructure projects. Its unique approach, which emphasizes simplicity and security, has inspired the creation of numerous similar DAOs.
Other notable DAO models include Decentraland DAO, which governs a virtual real estate platform, and Compound DAO, a leader in the decentralized finance sector. Each of these DAOs utilizes distinct governance structures tailored to their specific missions, demonstrating the versatility and adaptability of the decentralized autonomous organization model. As the ecosystem expands, new DAO models continue to emerge, each contributing innovative solutions to the challenges of decentralized governance.
Digital Assets and DAOs
Digital assets play a central role in the operation and governance of DAOs. Governance tokens and non-fungible tokens (NFTs) are commonly used to represent voting power and facilitate participation in decision-making processes. These assets enable DAO members to propose and vote on governance proposals, allocate resources, and shape the direction of the organization.
The integration of digital assets has expanded the capabilities of DAOs, allowing them to engage in activities such as investing, lending, and managing digital portfolios within the DAO ecosystem. Unlike traditional organizations, DAOs leverage blockchain technology and smart contracts to automate processes, resolve conflicts, and provide a secure, transparent environment for their members.
As regulatory bodies continue to assess the legal status of DAOs, it is increasingly important for DAO proponents to prioritize transparency, network security, and compliance with evolving legal frameworks. DAO members are at the heart of the governance process, using governance tokens to represent voting power and participate in the voting process. The outcome of these votes determines the strategic direction and operational decisions of the DAO.
Looking ahead, the future of DAOs is filled with potential for innovation across various sectors, from finance to healthcare and beyond. As blockchain technology matures and new governance models are developed, DAOs are poised to offer even more efficient, secure, and transparent alternatives to centralized leadership and traditional organizational structures. The continued success of DAOs will depend on their ability to foster active participation, adapt to regulatory changes, and maintain robust governance processes that empower their communities.
Challenges and Solutions in DAO Governance
The Whale Problem
Despite the decentralized organization model, large token holders—whales—can still exert disproportionate influence on governance outcomes. This concentration of voting power risks undermining the democratic ideals of DAOs.
Solutions include quadratic voting to limit whale dominance, vote delegation to concentrate expertise, multi-tiered governance to separate decision types, and time-locked voting to prevent last-minute vote manipulation.
Participation Inequality
Low voter turnout remains a challenge in many DAOs, where a small percentage of active voters control the majority of decisions. Encouraging active participation is essential for healthy governance.
Strategies to boost engagement include offering incentives, simplifying voting interfaces, employing conviction voting for continuous involvement, and using off-chain signaling to reduce transaction fees and barriers.
Information Overload
DAOs often face an overwhelming number of proposals, making it difficult for members to stay informed and vote effectively.
To address this, DAOs utilize proposal summaries, expert delegate systems, staged voting processes, and AI-powered tools that analyze and recommend proposals, helping members focus on key decisions.
Real-World DAO Success Stories
DeFi Governance Excellence
Uniswap DAO exemplifies successful decentralized governance by managing protocol upgrades, fee distributions, and partnerships through community voting, impacting billions in trading volume.
MakerDAO governs the DAI stablecoin system, making critical decisions about collateral and risk parameters, demonstrating resilience through volatile market cycles.
Community and Investment DAOs
ENS DAO manages the Ethereum Name Service with token-weighted voting, ensuring effective governance for vital Web3 infrastructure.
Investment DAOs like MetaCartel Ventures operate as decentralized venture funds, with members collectively voting on funding and portfolio management, showcasing the power of decentralized finance.
The Future of DAO Governance
Emerging Trends for 2025 and Beyond
The future of DAOs includes cross-chain governance, enabling decision-making across multiple blockchain networks and expanding operational scope. AI-assisted decision making will support voters by processing proposals and predicting outcomes.
As regulatory frameworks evolve, DAOs are integrating legal compliance into their governance structures while preserving decentralization. Scalability solutions like layer-2 protocols and off-chain voting are making participation more accessible and cost-effective.
Performance Metrics and Success Factors
Research confirms that DAOs with higher active participation outperform others. The system aims to foster communities focused on governance quality rather than purely financial returns. Transparency, inclusivity, and responsiveness remain key to sustainable DAO governance.
Technical Implementation: Smart Contract Architecture
Modern DAOs rely on sophisticated smart contract architectures, such as OpenZeppelin’s Governor framework, which provide modular, customizable governance functionalities. These smart contracts automate the entire governance process, including proposal creation, voting, execution, and treasury management, ensuring that DAO operations are secure, transparent, and efficient. Optimizing transaction speed is essential for efficient DAO operations, especially during periods of high network activity. Smart contracts and blockchain nodes work together to verify transactions, ensuring the integrity and security of the DAO's activities.
Best Practices for DAO Participants
For Token Holders
To maximize the benefits of DAO governance, token holders should stay informed by regularly reviewing proposals and engaging in community discussions. Delegating votes wisely to trusted representatives enhances governance quality. Adopting a long-term perspective and actively participating beyond voting—such as contributing to proposal development—strengthens the DAO ecosystem.
For DAO Creators
Creators should establish clear governance structures with defined roles and responsibilities. Balanced token distribution prevents excessive concentration of voting power. Employing multiple voting mechanisms tailored to different decision types enhances flexibility. Prioritizing community building fosters active participation and sustainable governance.
Conclusion: The Evolution of Collective Decision-Making
DAOs signify a profound shift from centralized control to collective governance, enabled by blockchain-based systems and smart contracts. While challenges such as whale dominance and participation inequality persist, the innovations emerging in 2025 demonstrate the potential for more inclusive, transparent, and effective governance models.
The DAO ecosystem continues to mature, integrating advanced governance structures, AI tools, and legal frameworks to meet the demands of a decentralized future. For participants in this evolving landscape, understanding how do DAOs function and make decisions—and leveraging analytical platforms like Token Metrics—is essential for meaningful involvement and success.
Ultimately, DAOs are reshaping organizational governance, not by achieving perfect decentralization, but by creating systems that empower communities, automate processes, and respond dynamically to member needs. As blockchain adoption expands across industries, the influence of DAOs will only grow, heralding a new era of decentralized decision-making.

.svg)

Create Your Free Token Metrics Account

.png)




%201.svg)
%201.svg)


%201.svg)











.svg)




.png)