
How Do You Implement Multi-Signature Wallets? A Complete 2025 Guide

Multi-signature wallets represent one of the most powerful security innovations in cryptocurrency, providing enhanced protection against theft, loss, and unauthorized access. As digital assets become increasingly valuable and institutional adoption accelerates, understanding how to implement multi-signature (multisig) solutions has become essential for serious cryptocurrency holders. Whether you're managing organizational treasury funds, protecting family wealth, or simply seeking maximum security for substantial holdings, multisig wallets offer unparalleled control and redundancy.
Understanding Multi-Signature Wallet Technology
A multi-signature wallet requires multiple private keys to authorize a transaction, rather than the single key used in standard wallets. This distributed control model is typically expressed as "M-of-N," where N represents the total number of keys and M represents the minimum number required to authorize transactions.
For example, a 2-of-3 multisig wallet has three total keys, but only two are needed to move funds. This configuration provides security against single key compromise while offering recovery options if one key is lost. The cryptographic implementation occurs at the blockchain protocol level, meaning transaction authorization requirements are enforced by the network itself, not by centralized services.
The beauty of multisig lies in eliminating single points of failure. Even if an attacker compromises one key through hacking, phishing, or physical theft, they cannot access funds without obtaining additional keys stored in separate locations with different security measures.
Common Multi-Signature Configurations
- 2-of-2 Multisig: This configuration requires both keys to authorize transactions, providing maximum security but no redundancy. Suitable for partnerships where both parties must approve every transaction. However, losing either key permanently locks funds, making this setup risky without proper backup strategies.
- 2-of-3 Multisig: The most popular configuration balances security and practicality. You might keep one key on a hardware wallet at home, another in a safe deposit box, and a third with a trusted family member or professional custodian. Any two keys authorize transactions, so losing one key doesn't create catastrophic loss. This setup protects against theft (attacker needs two separate keys) while providing recovery options.
- 3-of-5 Multisig: Organizations often use this configuration, distributing keys among multiple executives or board members. It requires broader consensus for transactions while tolerating loss of up to two keys. The increased complexity matches the higher stakes of organizational treasury management.
- Advanced Custom Configurations: Advanced users implement schemes like 4-of-7 or 5-of-9 for maximum security and redundancy. These complex arrangements suit high-value holdings, institutional custody, or scenarios requiring distributed governance. However, operational complexity increases proportionally—more keys mean more coordination and management overhead.
Choosing the Right Multi-Signature Wallet Solution
Hardware-Based Solutions
Ledger and Trezor both support multisig configurations, allowing you to use multiple hardware wallets as cosigners. This approach keeps private keys isolated on secure hardware while enabling distributed control. Setting up hardware-based multisig typically involves initializing multiple devices, creating a multisig wallet through compatible software, and registering each hardware wallet as a cosigner.
Coldcard particularly excels for Bitcoin multisig, offering air-gapped security and extensive multisig features. Its advanced capabilities suit security-conscious users willing to navigate more complex setup procedures for maximum protection.
Software Coordinators
While keys should reside on hardware wallets, coordinator software manages multisig wallet creation and transaction building. Electrum provides robust Bitcoin multisig support with straightforward setup procedures. Sparrow Wallet offers excellent multisig features with superior user experience and advanced capabilities.
For Ethereum and ERC-20 tokens, Gnosis Safe (formerly Gnosis Multisig) has become the industry standard, particularly for DeFi treasury management. Its web interface simplifies multisig operations while maintaining security through hardware wallet integration.
Blockchain-Specific Considerations
Bitcoin's native multisig support through P2SH (Pay-to-Script-Hash) and P2WSH (Pay-to-Witness-Script-Hash) addresses provides robust, time-tested functionality. Ethereum implements multisig through smart contracts, offering more flexibility but requiring gas for deployment and transactions.
Other blockchains like Solana, Cardano, and Polkadot each have unique multisig implementations. Research your specific blockchain's multisig capabilities before committing to particular solutions.
Step-by-Step Implementation Process
Planning Your Configuration
Begin by determining the appropriate M-of-N configuration for your needs. Consider security requirements, number of parties involved, operational frequency, and recovery scenarios. Document your security model clearly, including who controls which keys and under what circumstances transactions should be authorized.
Acquiring Hardware Wallets
Purchase the necessary hardware wallets directly from manufacturers. For a 2-of-3 setup, you need three separate hardware wallets. Never reuse the same device or seed phrase—each cosigner must have completely independent keys.
Initializing Individual Wallets
Set up each hardware wallet independently, generating unique seed phrases for each device. Record seed phrases on durable materials and store them in separate secure locations. Never digitize seed phrases or store multiple phrases together.
Creating the Multisig Wallet
Using your chosen coordinator software, create the multisig wallet by registering each hardware wallet as a cosigner. The software will request the public key or extended public key (xpub) from each device—note that you're sharing public keys only, not private keys.
The coordinator generates the multisig address where funds will be stored. This address is cryptographically linked to all registered cosigner public keys, ensuring only transactions signed with the required number of private keys will be accepted by the blockchain.
Testing with Small Amounts
Before transferring substantial funds, thoroughly test your multisig setup. Send a small amount to the multisig address, then practice creating and signing transactions with the required number of keys. Verify you can successfully move funds out of the wallet before trusting it with significant amounts.
Test recovery scenarios by attempting to transact using different combinations of keys. Ensure you understand the complete transaction signing workflow and that all cosigners can successfully participate.
Making Strategic Decisions with Professional Analytics
Implementing multisig security is just one component of successful cryptocurrency management. Making informed decisions about which assets to hold, when to rebalance, and how to optimize your portfolio requires sophisticated analytical capabilities.
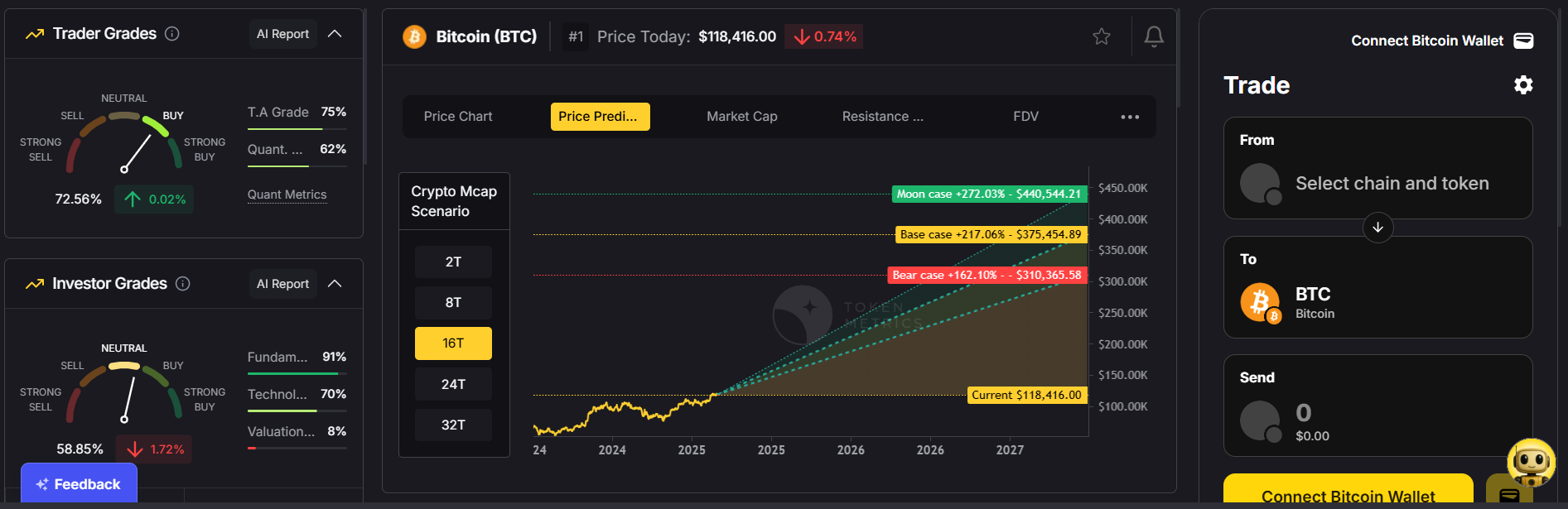
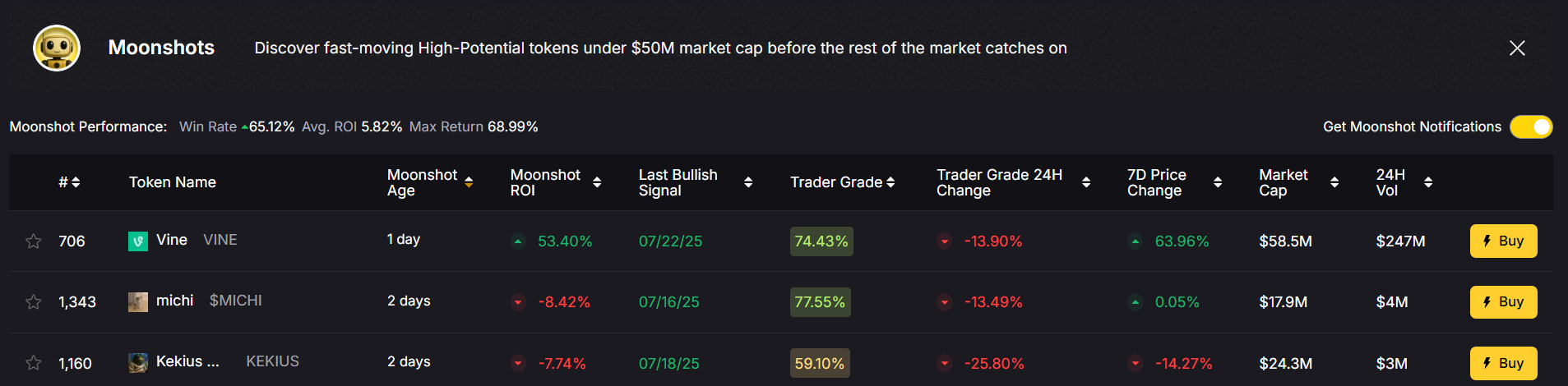
Discover Crypto Gems with Token Metrics AI
Operational Best Practices
Key Distribution Strategy
Distribute keys across multiple physical locations with different security profiles. Never store multiple keys in the same location—this defeats the purpose of multisig. Consider geographic distribution to protect against localized disasters like fires or floods.
For keys held by different individuals, ensure clear communication protocols exist. Everyone involved should understand their responsibilities, how to recognize legitimate transaction requests, and procedures for emergency situations.
Transaction Workflow
Establish clear processes for initiating, reviewing, and signing transactions. Who can propose transactions? What review occurs before cosigners add signatures? How are urgent situations handled? Documented workflows prevent confusion and ensure all parties understand their roles.
Use the coordinator software to create transactions, which are then presented to cosigners for review and signature. Each cosigner independently verifies transaction details before signing with their private key. Only after collecting the required number of signatures is the transaction broadcast to the blockchain.
Regular Audits and Drills
Periodically verify all keys remain accessible and functional. Practice the complete transaction signing process quarterly or semi-annually to ensure everyone remembers procedures and that all hardware and software remain compatible and updated.
Test recovery scenarios where one or more keys become unavailable. Verify you can still access funds using alternative key combinations. These drills identify potential issues before emergencies occur.
Security Considerations
Protecting Against Internal Threats
While multisig protects against external attackers, consider internal threats. In a 2-of-3 configuration, any two key holders could collude to steal funds. Select cosigners carefully and consider configurations requiring more keys for higher-value holdings.
Software and Hardware Updates
Keep coordinator software and hardware wallet firmware updated to patch security vulnerabilities. However, test updates on small amounts before applying them to wallets holding substantial funds. Occasionally, updates introduce compatibility issues that could temporarily lock access.
Backup and Recovery Documentation
Create comprehensive documentation of your multisig setup, including the configuration type, which hardware wallets serve as cosigners, extended public keys, and the multisig address itself. Store this information separately from seed phrases—someone recovering your wallet needs this metadata to reconstruct the multisig configuration.
Common Pitfalls to Avoid
Never store multiple seed phrases together, as this recreates single point of failure vulnerabilities. Don't skip testing phases—discover operational issues with small amounts rather than substantial holdings. Avoid overly complex configurations that create operational difficulties, and ensure at least one other trusted person understands your multisig setup for inheritance purposes.
Advanced Features and Future Developments
Modern multisig solutions increasingly incorporate time-locks, spending limits, and white-listing features. Smart contract-based multisig wallets on Ethereum offer programmable conditions like daily spending caps, recovery mechanisms after extended inactivity, and role-based permissions.
Emerging developments include social recovery mechanisms where trusted contacts can help recover wallets, threshold signature schemes (TSS) that improve privacy and efficiency compared to traditional multisig, and standardization efforts making multisig more accessible across different blockchains and wallet providers.
Conclusion
Implementing multi-signature wallets significantly enhances cryptocurrency security by eliminating single points of failure and providing recovery options. While setup requires more effort than standard wallets, the protection multisig offers for substantial holdings justifies the additional complexity.
By carefully planning your configuration, using quality hardware wallets, following proper operational procedures, and leveraging professional platforms like Token Metrics for strategic decision-making, you can build a robust security framework that protects your digital assets while maintaining practical accessibility.
In an ecosystem where theft and loss are permanent and irreversible, multisig represents best practice for serious cryptocurrency holders who refuse to gamble with their financial future.

.svg)

Create Your Free Token Metrics Account

.png)




%201.svg)
%201.svg)


%201.svg)









.svg)




.png)