
Layer 2 Wars Heat Up: Analyzing the Competition Between Established and Emerging Ethereum Scaling Solutions

The Ethereum Layer 2 ecosystem is experiencing unprecedented growth and competition as new solutions launch with substantial backing while established players fight to maintain market share. The recent launch of Linea, developed by Consensys and MetaMask teams, with $750 million in venture funding and an immediate $1.8 billion total value locked (TVL), highlights how competitive this space has become.
The Current Layer 2 Landscape
Ethereum's scaling challenges have created a diverse ecosystem of Layer 2 solutions, each pursuing different technical approaches and market strategies. The landscape includes established players like Arbitrum, Optimism, and Polygon, alongside newer entrants leveraging zero-knowledge proofs and other advanced cryptographic techniques.
Linea represents the latest high-profile entry, utilizing ZK-rollup technology while maintaining strong connections to Ethereum's core development community. With backing from major technology corporations including Microsoft, MasterCard, and SoftBank, the project launched with more TVL than many established Layer 1 blockchains, including SEI and Aptos, and approaching the $2 billion TVL of Sui.
This immediate scale reflects both the maturation of Layer 2 infrastructure and the increasing sophistication of launch strategies in the space. Rather than gradual adoption, well-funded projects can now achieve substantial initial usage through strategic partnerships and ecosystem incentives.
Technical Differentiation Strategies
The Layer 2 space has evolved beyond simple throughput improvements to focus on specific use cases and technical advantages:
Zero-Knowledge Technology: Projects like Linea, Scroll, and zkSync focus on zero-knowledge proofs for enhanced privacy and faster finality. These solutions offer theoretical advantages in security and decentralization compared to optimistic rollups, though often at the cost of complexity and computational requirements.
Specialized Applications: Some Layer 2 solutions target specific applications or industries. Derivatives-focused platforms like Hyperliquid have built their own chains optimized for high-frequency trading, achieving significant market share through vertical integration.
Cross-Chain Compatibility: Newer projects emphasize interoperability, allowing users to interact with multiple blockchains through unified interfaces. This approach addresses the fragmentation challenges created by the proliferation of different scaling solutions.
Developer Experience: Projects differentiate through developer tools, programming language support, and integration capabilities. Flare Network, for example, supports multiple programming languages including Solidity, JavaScript, Python, and Go, targeting developers seeking familiar development environments.
Market Dynamics and Competitive Positioning
The Layer 2 market demonstrates several key competitive dynamics:
First-Mover Advantages: Established Layer 2s benefit from developer mindshare, user familiarity, and ecosystem development. Arbitrum and Optimism maintain significant portions of Layer 2 TVL through early market entry and continuous development.
Venture Capital Influence: Well-funded projects can invest heavily in ecosystem development, security audits, and user acquisition. Linea's $750 million funding enables aggressive market expansion strategies that smaller competitors cannot match.
Exchange Integration: Access to major centralized exchanges significantly impacts adoption. Projects with Binance, Coinbase, and other top-tier exchange listings gain substantial advantages in user onboarding and liquidity provision.
Corporate Partnerships: Strategic relationships with major technology companies provide credibility and potential integration opportunities. Linea's consortium model, including Consensys, Eigen Labs, and ENS, demonstrates how core Ethereum relationships translate into competitive advantages.
The Economics of Layer 2 Competition
Layer 2 solutions face complex economic challenges in balancing user costs, security, and profitability:
Fee Competition: Users increasingly expect low transaction costs, creating pressure on Layer 2 solutions to minimize fees while maintaining security and decentralization. Ethereum's recent fee reductions through Blob technology have intensified this competition.
Token Economics: Many Layer 2 projects issue tokens for governance and value capture, but designing sustainable tokenomics remains challenging. Projects must balance user incentives with long-term economic sustainability.
Revenue Models: Different approaches to revenue generation create various competitive dynamics. Some projects focus on transaction fees, others on ecosystem development, and some on specialized services like data availability or computation.
Ecosystem Development: Attracting and retaining developers and projects requires ongoing investment in tooling, documentation, and financial incentives. This creates significant ongoing costs that must be balanced against revenue generation.
Centralized Exchange Competition and Base Token Speculation
The recent announcement that Coinbase's Base chain is exploring a native token launch has significant implications for the Layer 2 space. Base has already achieved substantial adoption without a token, suggesting strong underlying demand for Coinbase-affiliated infrastructure.
A Base token could potentially achieve top-10 market capitalization given Coinbase's position as a publicly traded company focused on shareholder value creation. The comparison to Binance's BNB, which trades at over $130 billion fully diluted valuation as the fifth-largest cryptocurrency, suggests substantial value creation potential.
This development highlights how centralized exchanges with established user bases can rapidly gain market share in the Layer 2 space through vertical integration. Unlike venture-backed Layer 2 projects that must acquire users organically, exchange-affiliated solutions inherit existing customer relationships and distribution channels.
Emerging Competitive Threats
Beyond traditional Layer 2 solutions, several emerging trends create additional competitive pressure:
Solana's Resurgence: Solana's performance recovery and growing DeFi ecosystem provides an alternative to Ethereum scaling solutions. With TVL reaching new all-time highs above $15 billion, Solana demonstrates that Layer 1 solutions can compete effectively with Layer 2 approaches.
Application-Specific Chains: Projects building their own chains for specific applications, like Hyperliquid for derivatives trading, bypass Layer 2 solutions entirely while achieving superior performance for targeted use cases.
Cross-Chain Infrastructure: Improvements in cross-chain bridge technology and interoperability protocols reduce the friction of moving between different blockchain ecosystems, decreasing the importance of any single scaling solution.
Alternative Scaling Approaches: Technologies like state channels, sidechains, and hybrid solutions provide additional options for developers seeking scaling solutions without the complexity of traditional Layer 2 integration.
User Experience and Adoption Patterns
Despite technical improvements, user experience remains a key differentiator in the Layer 2 space:
Wallet Integration: Seamless wallet support significantly impacts user adoption. Projects with native support in popular wallets like MetaMask gain advantages in user onboarding and transaction completion.
Cross-Chain Asset Management: Users increasingly expect unified interfaces for managing assets across multiple chains. Layer 2 solutions that simplify cross-chain interactions gain competitive advantages.
Application Ecosystem: The availability of familiar applications and services drives user adoption more than underlying technical capabilities. Layer 2 solutions must attract established DeFi protocols, NFT platforms, and other user-facing applications.
Educational Resources: User education about Layer 2 benefits and usage patterns remains crucial for adoption. Projects investing in documentation, tutorials, and community education see better retention rates.
Regulatory Considerations and Compliance
Layer 2 solutions face evolving regulatory requirements that create additional competitive factors:
Decentralization Requirements: Regulatory authorities increasingly scrutinize the decentralization of blockchain networks. Layer 2 solutions must balance operational efficiency with decentralization requirements.
Compliance Infrastructure: Projects serving institutional users must implement compliance tools, reporting capabilities, and regulatory interfaces. This creates barriers to entry while providing advantages to well-funded projects.
Geographic Restrictions: Different regulatory approaches across jurisdictions require Layer 2 solutions to implement geographic restrictions and compliance measures that impact user experience and adoption.
Future Outlook and Strategic Implications
The Layer 2 landscape will likely continue consolidating around solutions that can achieve sustainable competitive advantages:
Technical Excellence Alone Insufficient: Superior technology without strong distribution, funding, or partnerships may not guarantee success in the increasingly competitive environment.
Ecosystem Development Critical: Long-term success depends on attracting and retaining developers, projects, and users through ongoing ecosystem investment and support.
Specialization vs. Generalization: Projects must choose between targeting broad markets with general-purpose solutions or focusing on specific niches with optimized capabilities.
Financial Sustainability: Revenue generation and path to profitability become increasingly important as venture capital funding becomes more selective and expensive.
The Layer 2 wars represent a microcosm of broader blockchain ecosystem competition, where technical capabilities, financial resources, strategic partnerships, and execution quality all contribute to market success. As the space matures, users and developers benefit from improved options and competitive pressure driving innovation, while investors must carefully evaluate which solutions can achieve sustainable market positions in an increasingly crowded landscape.
The emergence of well-funded projects like Linea alongside speculation about major exchange tokens like Base suggests the Layer 2 space will continue evolving rapidly, with significant implications for Ethereum's scaling roadmap and the broader blockchain ecosystem's development trajectory.

.svg)

Create Your Free Token Metrics Account

.png)




%201.svg)
%201.svg)


%201.svg)










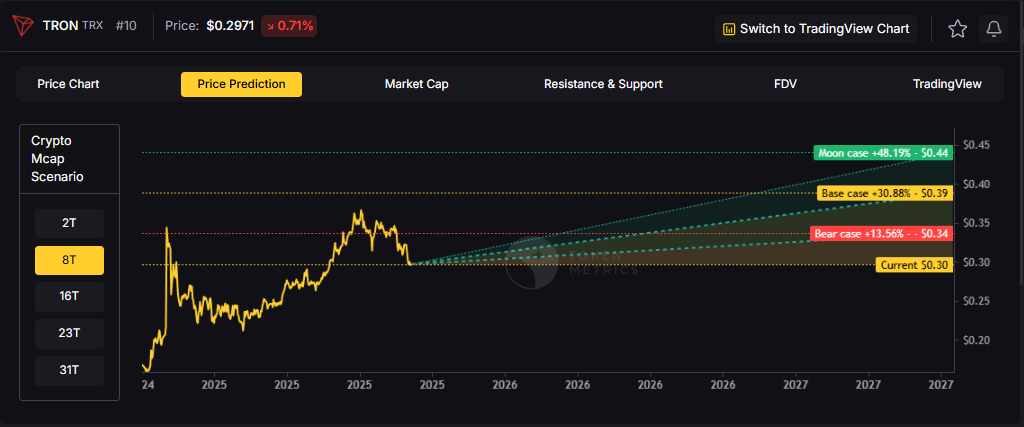
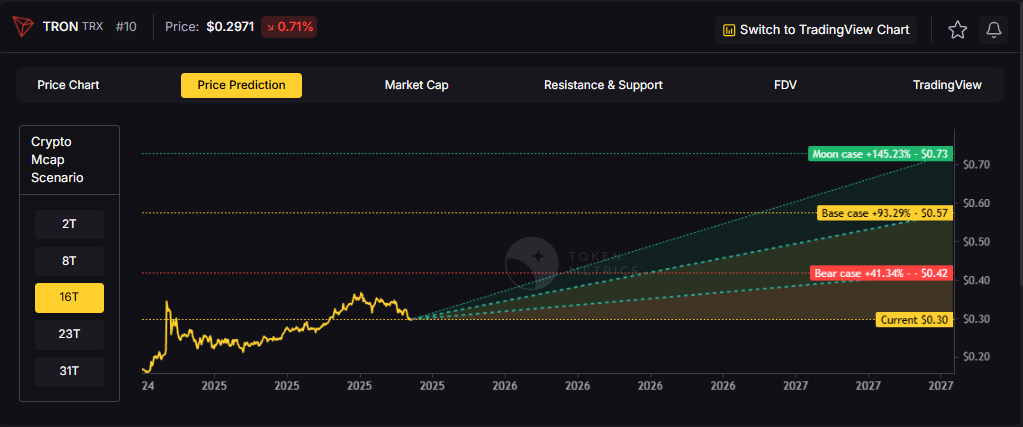
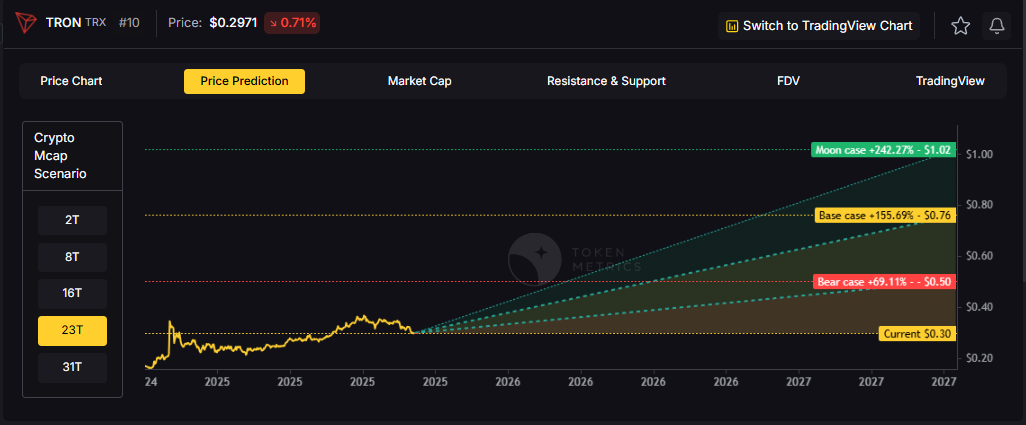
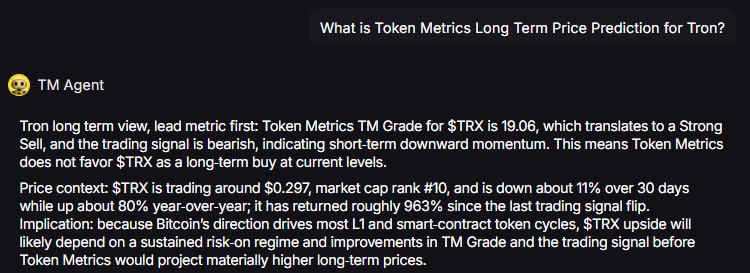



.svg)




.png)