
Mastering Google APIs: Practical Developer Guide
%201.svg)
%201.svg)


APIs from Google power a huge portion of modern applications, from location-aware mobile apps to automated data workflows in the cloud. Understanding how Google API endpoints, authentication, quotas, and client libraries fit together helps developers build reliable, maintainable integrations that scale. This guide breaks down the most practical aspects of working with Google APIs and highlights research and AI tools that can streamline development.
Overview: What the term “Google API” covers
"Google API" is an umbrella term for a wide range of services offered by Google, including but not limited to Google Cloud APIs (Compute, Storage, BigQuery), Maps and Places, OAuth 2.0 identity, Drive, Sheets, and machine learning APIs like Vision and Translation. Each service exposes RESTful endpoints and often provides SDKs in multiple languages (Node.js, Python, Java, Go, and more).
Key dimensions to evaluate when selecting a Google API:
- Functionality: Does the API provide the exact data or operation you need (e.g., geocoding vs. routing)?
- Authentication model: API keys, OAuth 2.0, or service accounts (server-to-server).
- Rate limits and quotas: per-minute or per-day limits, and how to monitor them.
- Pricing and billing: free tier limits, billing account requirements, and potential cost drivers.
Core Google API services and common use cases
Popular categories and what developers commonly use them for:
- Maps & Places — interactive maps, geocoding, places search, routing for location-based apps.
- Cloud Platform APIs — storage (Cloud Storage), analytics (BigQuery), compute (Compute Engine, Cloud Run) for backend workloads.
- Identity & Access — OAuth 2.0 and OpenID Connect for user sign-in; service accounts for server-to-server authentication.
- Workspace APIs — Drive, Sheets, and Gmail automation for productivity integrations.
- AI & Vision — Vision API, Natural Language, and Translation for content analysis and enrichment.
Choosing the right API often starts with mapping product requirements to the available endpoints. For example, if you need user authentication and access to Google Drive files, combine OAuth 2.0 with the Drive API rather than inventing a custom flow.
Best practices for integration, authentication, and error handling
Follow these practical steps to reduce friction and improve reliability:
- Use official client libraries where available — they implement retries, backoff, and serialization conventions that keep your code simpler.
- Prefer OAuth or service accounts over long-lived API keys for sensitive operations. Use short-lived tokens and rotate credentials regularly.
- Implement exponential backoff for rate-limited operations and surface clear error messages when requests fail.
- Monitor quotas and billing with Google Cloud Console alerts and programmatic checks so you can detect spikes before they affect users.
- Design for idempotency if your operation may be retried — include request tokens or use idempotent endpoints.
These patterns reduce operational surprises and make integrations more maintainable over time.
Security, quotas, and governance considerations
Security and quota constraints often shape architecture decisions:
- Least privilege — grant the minimum IAM roles needed. For service accounts, avoid broad roles like owner.
- Auditing — enable Cloud Audit Logs to trace who accessed which APIs and when.
- Quota planning — understand per-minute and per-day limits. For high-throughput needs, request quota increases with a clear justification.
- Data residency and compliance — check where data is stored and whether it meets your regulatory requirements.
Secure-by-design implementations and proactive quota management reduce operational risk when moving from prototype to production.
Building apps with Google APIs and AI workflows
Combining Google APIs with AI tooling unlocks new workflows: use Vision API to extract entities from images, then store structured results in BigQuery for analytics; call Translation or Natural Language for content normalization before indexing. When experimenting with AI-driven pipelines, maintain traceability between raw inputs and transformed outputs to support auditing and debugging.
AI-driven research platforms like Token Metrics can help developers prototype analytics and compare signal sources by aggregating on-chain and market datasets; such tools may inform how you prioritize data ingestion and model inputs when building composite systems that include external data alongside Google APIs.
Build Smarter Crypto Apps & AI Agents with Token Metrics
Token Metrics provides real-time prices, trading signals, and on-chain insights all from one powerful API. Grab a Free API Key
FAQ: What is a Google API and how does it differ from other APIs?
Google APIs are a collection of RESTful services and SDKs that grant programmatic access to Google products and cloud services. They differ in scope and SLAs from third-party APIs by integrating with Google Cloud's IAM, billing, and monitoring ecosystems.
FAQ: Which authentication method should I use?
Use OAuth 2.0 for user-level access where users must grant permission. For server-to-server calls, use service accounts with short-lived tokens. API keys are acceptable for public, limited-scope requests like simple Maps access but carry higher security risk if exposed.
FAQ: How do I monitor and request higher quotas?
Monitor quotas in Google Cloud Console under the "IAM & Admin" and "APIs & Services" sections. If you need more capacity, submit a quota increase request with usage patterns and justification; Google evaluates requests based on scope and safety.
FAQ: How can I estimate costs for Google API usage?
Cost depends on API type and usage volume. Use the Google Cloud Pricing Calculator for services like BigQuery or Cloud Storage, and review per-request pricing for Maps and Vision APIs. Track costs via billing reports and set alerts to avoid surprises.
FAQ: Are client libraries necessary?
Client libraries are not strictly necessary, but they simplify authentication flows, retries, and response parsing. If you need maximum control or a minimal runtime, you can call REST endpoints directly with standard HTTP libraries.
Disclaimer
This article is educational and technical in nature. It does not provide financial, legal, or investment advice. Evaluate APIs and third-party services against your own technical, security, and compliance requirements before use.
AI Agents in Minutes, Not Months


.svg)



Create Your Free Token Metrics Account





.png)
Recent Posts

Best Crypto Trading Platform: Top Exchanges for 2025
%201.svg)
%201.svg)
The cryptocurrency market has transformed from a niche digital experiment into a trillion-dollar industry, with millions of traders worldwide seeking the best crypto trading platform to buy, sell, and store crypto assets. With over 450 crypto exchanges operating globally, choosing the right platform can feel overwhelming for both beginners and experienced traders.
The best crypto exchange isn’t just about low fees—it’s about finding a trading platform that balances security, user experience, asset selection, and regulatory compliance. Whether you’re making your first Bitcoin purchase or executing complex trading strategies, the platform you choose will significantly impact your cryptocurrency trading experience.
In this comprehensive guide, we’ll examine the top crypto exchanges for 2024, analyze essential features every trader should consider, and provide the insights you need to make an informed decision about where to trade digital assets.
Top 5 Best Crypto Trading Platforms for 2025
After evaluating over 450 data points across 14 major cryptocurrency exchanges, these five platforms stand out as the best crypto exchanges for different types of traders:
Kraken leads our list for traders prioritizing low fees and advanced order types. With competitive maker fees starting at 0.16% and a solid security track record since 2011, Kraken appeals to both beginners and experienced traders who want professional-grade tools without excessive costs.
Coinbase remains the gold standard for newcomers to crypto trading. Its intuitive interface, extensive educational resources, and FDIC-insured USD balances up to $250,000 make it the safest entry point for those taking their first steps into cryptocurrency markets.
Binance.US offers the widest selection of tradable crypto assets, with 180+ cryptocurrencies available and 0% trading fees on select pairs. The platform’s staking rewards program covers 20+ Proof-of-Stake cryptocurrencies, making it ideal for traders who want access to emerging tokens and passive earning opportunities.
Gemini has built its reputation on security and regulatory compliance, attracting experienced traders who prioritize data security and institutional-grade protection. Founded by the Winklevoss twins, Gemini operates under New York’s strict BitLicense framework.
Crypto.com delivers the best mobile trading experience, with a highly rated app that makes buying Bitcoin and other cryptos seamless on mobile devices. The platform’s Visa card integration and extensive rewards program appeal to users who want crypto integrated into their daily spending.
Token Metrics is the best crypto trading and research platform which is a highly rated platform.

Essential Features to Look for in a Crypto Trading Platform
When evaluating cryptocurrency exchanges, certain features separate the best crypto exchanges from the rest. Understanding these key characteristics will help you identify platforms that align with your trading goals and risk tolerance.
Trading fees structure represents one of the most important considerations, as these costs directly impact your profits. Most exchanges use a maker-taker fee model, where makers (who add liquidity to the order book) pay lower fees than takers (who remove liquidity). Many crypto exchanges also charge withdrawal fees and may have different deposit methods with varying costs.
Cryptocurrency selection varies dramatically across platforms. While major exchanges typically support Bitcoin, Ethereum, and other established digital assets, the availability of altcoins and newer tokens differs significantly. Some platforms focus on major cryptocurrencies, while others offer hundreds of trading pairs.
Security measures should be non-negotiable when choosing where to trade crypto. Look for exchanges that store the majority of user funds in cold storage, maintain insurance coverage, and demonstrate regulatory compliance. Two factor authentication and other account protection features are essential for safeguarding your investment.
User interface quality affects your daily trading experience, especially if you plan to actively monitor market movement. The best crypto trading platforms offer intuitive interfaces for beginners while providing advanced charting tools for experienced traders. Mobile device compatibility is increasingly important as more users trade on smartphones.
Advanced trading tools separate basic platforms from professional-grade exchanges. Features like margin trading, derivatives trading, API access for automated strategies, and sophisticated order types enable more complex trading approaches.
Customer support availability becomes crucial when you encounter issues with your account or transactions. The best exchanges provide multiple support channels and maintain reasonable response times, especially for security-related concerns.
Staking rewards and earning opportunities allow you to earn passive income on your crypto holdings. Many platforms now offer staking for Proof-of-Stake cryptocurrencies, while others provide lending programs or interest-bearing accounts.
Detailed Platform Reviews
Kraken - Best for Low Fees
Kraken has established itself as one of the most respected names in cryptocurrency trading, operating since 2011 with a strong focus on security and competitive pricing. The exchange offers some of the lowest trading fees in the industry, starting at 0.16% for makers and scaling down to 0% for high-volume traders.
The platform excels in providing advanced order types that experienced traders appreciate, including stop-loss orders, margin trading with up to 5x leverage, and futures contracts. Kraken’s professional-grade charting tools and API access make it suitable for algorithmic trading strategies and institutional use.
Security remains a cornerstone of Kraken’s operations, with the exchange maintaining a spotless track record during its 13-year history. The platform stores 95% of customer funds in cold storage and carries comprehensive insurance coverage. Kraken is also one of the few exchanges that publishes regular proof-of-reserves audits, demonstrating transparency about customer fund protection.
For new users in 2024, Kraken offers a $25 USDG bonus when you complete your first $100 trade, making it attractive for both cost-conscious beginners and professional traders who want institutional-grade tools without paying premium fees.
Coinbase - Best for Beginners
Coinbase has become synonymous with mainstream cryptocurrency adoption, serving over 100 million users worldwide with its beginner-friendly approach to crypto trading. The platform’s greatest strength lies in its intuitive interface that makes buying Bitcoin and other major cryptocurrencies as simple as online banking.
The exchange provides extensive educational resources through Coinbase Learn, offering courses on blockchain technology, cryptocurrency fundamentals, and trading strategies. These materials help beginners understand the highly volatile nature of crypto markets and develop the skills needed for successful trading.
Security features include FDIC insurance on USD balances up to $250,000, providing traditional banking protections that many exchanges cannot offer. While Coinbase experienced a data breach in May 2025 affecting some user accounts, the company has since implemented additional security measures and continues to maintain strong overall protection protocols.
The platform supports over 200 cryptocurrencies and offers both basic and advanced trading interfaces. Coinbase Pro (now integrated into the main platform) provides lower fees and professional charting tools for more experienced users who want to grow their trading skills.
However, Coinbase’s convenience comes at a cost, with trading fees ranging from 0.50% to 4.00% depending on the payment method and transaction size. Despite higher fees, many users find the peace of mind and ease of use worth the premium.
Binance.US - Best for Asset Variety
Binance.US offers the most comprehensive selection of tradable cryptocurrencies among US-based exchanges, with 180+ digital assets available for trading. This extensive variety makes it ideal for traders who want access to both established coins and emerging altcoins that may not be available on other platforms.
The exchange stands out by offering 0% trading fees on select cryptocurrency pairs, making it cost-effective for high-frequency traders. The standard fee structure ranges from 0.10% to 0.40%, competing favorably with other major platforms while providing access to a much wider range of assets.
Staking rewards represent another key advantage, with Binance.US supporting staking for over 20 Proof-of-Stake cryptocurrencies. Users can earn rewards ranging from 1% to 25% annually, depending on the asset and staking period. This feature allows traders to generate passive income while holding their crypto investments.
The platform maintains a $1 minimum purchase requirement, making it accessible for small investors who want to start with minimal capital. Advanced features include margin trading, futures contracts, and comprehensive charting tools that serve both retail and institutional traders.
While Binance.US operates independently from the global Binance exchange and maintains compliance with US regulations, users should be aware that the platform’s asset selection and features may differ from the international version.
Trading Fees Comparison
Understanding fee structures across different cryptocurrency exchanges is crucial for maximizing your trading profits. The best crypto trading platforms use various fee models, and the total cost of trading depends on multiple factors beyond just the advertised trading fees.
Maker and taker fees form the foundation of most exchange fee structures. Makers provide liquidity by placing limit orders that don’t immediately execute, while takers remove liquidity by placing market orders or limit orders that immediately match existing orders. Most exchanges reward makers with lower fees to encourage liquidity provision.

Withdrawal fees vary significantly across assets and platforms. Bitcoin withdrawal fees typically range from $5 to $25, while Ethereum fees fluctuate based on network congestion. Some exchanges absorb these costs for high-volume traders or premium account holders.
Deposit methods affect overall trading costs. Bank transfers are usually free but take several days to process. Credit card deposits offer instant access but may incur fees of 1-4%. Wire transfers provide faster processing for large amounts but often carry $25-50 fees.
Hidden fees can significantly impact your trading experience. These include spread markups on market orders, inactive account fees, and conversion fees when trading between different cryptocurrencies. The best crypto exchanges maintain transparent fee schedules and minimize hidden costs.
Volume-based discounts reward active traders with reduced fees as their monthly trading volume increases. High-volume traders on platforms like Binance.US can achieve fees as low as 0.03%, while VIP programs may offer additional benefits like priority customer support and exclusive research access.
Security and Safety Considerations
Security represents the most critical factor when selecting a crypto trading platform, as the irreversible nature of cryptocurrency transactions means that lost or stolen funds are typically unrecoverable. The collapse of Mt. Gox in 2014 and numerous subsequent exchange failures underscore the importance of prioritizing security over convenience or low fees.
Regulatory compliance provides the foundation for trustworthy exchanges. Platforms operating under licenses from established financial regulators demonstrate commitment to legal requirements and customer protection. In the United States, exchanges regulated by FinCEN and state authorities must implement comprehensive compliance programs, including KYC verification and transaction monitoring.
Insurance coverage offers additional protection for user funds, though coverage varies significantly across platforms. Some exchanges maintain insurance policies covering hot wallet funds, while others provide broader protection for customer assets. Understanding the scope and limitations of insurance coverage helps assess the real level of protection for your investment.
Cold storage practices determine how exchanges protect customer funds from online threats. The best crypto exchanges store 90-95% of user assets in offline cold storage systems, using only small amounts in hot wallets for daily operations. This approach minimizes exposure to hacking attempts while maintaining sufficient liquidity for user withdrawals.

Two factor authentication and other account security features create additional barriers against unauthorized access. Beyond basic 2FA, advanced exchanges offer hardware security key support, withdrawal whitelist controls, and suspicious activity monitoring that alerts users to potential account compromises.
Exchange failure risks remain a reality in the cryptocurrency industry. Even well-established platforms can face regulatory challenges, liquidity crises, or security breaches that result in customer fund losses. Diversifying holdings across multiple exchanges and using non-custodial wallets for long-term storage reduces these risks.
Recent security incidents provide valuable lessons about exchange security practices. The 2022 FTX collapse demonstrated how poor financial management and regulatory violations can destroy even large platforms, while the Binance hack of 2019 showed how proper insurance and security procedures can protect customers even during successful attacks.
Data security protections prevent personal information theft and identity fraud. Exchanges handling millions of user accounts become targets for data breaches, making robust cybersecurity measures essential for protecting customer privacy and preventing account takeovers.
Advanced Trading Features
Professional traders and institutions require sophisticated tools that go beyond basic buy and sell functionality. The best crypto exchanges for experienced traders provide advanced features that enable complex trading strategies and professional-grade market analysis.
Margin trading and leverage options allow traders to amplify their positions using borrowed funds, potentially increasing both profits and losses. Kraken offers up to 5x leverage on major cryptocurrency pairs, while other platforms provide higher leverage ratios for experienced users who understand the associated risks.
Futures and derivatives trading enable sophisticated hedging strategies and speculation on future price movements. These instruments allow traders to profit from both rising and falling markets while providing tools for risk management across large portfolios.
Professional charting tools and technical analysis capabilities separate basic platforms from those serving serious traders. Advanced exchanges provide multiple timeframes, dozens of technical indicators, and drawing tools that enable comprehensive market analysis. Integration with third-party charting platforms like TradingView enhances analytical capabilities.
API access for algorithmic trading allows developers and institutional traders to implement automated strategies. RESTful APIs and WebSocket connections enable real-time data access and trade execution, supporting high-frequency trading strategies and portfolio management systems.
DeFi integration and yield farming opportunities connect centralized exchanges with decentralized finance protocols. Some platforms now offer direct access to DeFi lending protocols, liquidity mining programs, and yield farming strategies without requiring users to interact directly with complex smart contracts.
Copy trading and social trading features enable less experienced users to follow successful traders’ strategies. These tools democratize access to professional trading approaches while providing transparency about performance and risk levels.
Mobile Trading Experience
Mobile trading has become essential as smartphones increasingly serve as primary computing devices for many users. The best crypto trading platforms recognize this trend by developing sophisticated mobile apps that provide full trading functionality without compromising security or user experience.
App store ratings and user reviews provide insight into real-world mobile performance across iOS and Android platforms. Crypto.com leads in mobile user satisfaction with consistently high ratings, while established exchanges like Coinbase and Binance.US maintain strong mobile presences with regular feature updates.
Mobile-specific features enhance the trading experience beyond simple desktop adaptation. Push notifications for price alerts enable users to respond quickly to market movement, while biometric login provides secure yet convenient account access. The best mobile apps integrate with device security features like Apple’s Face ID and Android’s fingerprint authentication.
Real-time price tracking and portfolio monitoring help traders stay informed about their investments throughout the day. Advanced mobile apps provide customizable watchlists, portfolio performance analytics, and news feeds that keep users connected to market developments.
Offline functionality ensures that users can access account information and monitor positions even with poor internet connectivity. Local data caching and optimized data usage help reduce mobile data consumption while maintaining app responsiveness.
Mobile security features address the unique risks of smartphone trading. Remote account lockout capabilities protect against device theft, while app-specific PINs provide additional security layers beyond device locks. Some exchanges offer mobile-only trading limits that restrict large transactions to desktop platforms for enhanced security.
Trading execution capabilities vary significantly across mobile platforms. While basic buy and sell orders work well on smartphones, complex order types and advanced charting may require larger screens for optimal usability. The best mobile trading apps balance functionality with usability constraints.
Getting Started: Step-by-Step Guide
Beginning your cryptocurrency trading journey requires careful planning and attention to security best practices. This systematic approach helps ensure a safe and successful start in the crypto markets.
Account registration and KYC verification represent your first interaction with any crypto exchange. Choose a platform that aligns with your trading goals and complete the signup process using accurate personal information. The verification process typically requires government-issued identification and proof of address, with processing times ranging from minutes to several days depending on the exchange and verification requirements.
Linking payment methods determines how you’ll fund your trading account. Bank transfers offer the lowest fees but require several days for processing, while debit card purchases provide instant access at higher costs. Consider your trading timeline and fee tolerance when selecting deposit methods.
Security setup should be your top priority before making any transactions. Enable two factor authentication using an authenticator app rather than SMS when possible. Create a strong, unique password and consider using a password manager. Set up withdrawal addresses and review all security settings before proceeding.
Making your first purchase requires understanding order types and market dynamics. Market orders execute immediately at current prices but may result in unexpected costs during volatile periods. Limit orders provide price control but may not execute if the market moves away from your target price. Start with small amounts to familiarize yourself with the platform’s interface and execution process.
Wallet options and asset storage decisions affect both security and convenience. Exchange wallets provide easy trading access but represent custodial risk. Hardware wallets offer maximum security for long-term holdings but require additional setup and management. Many traders use a combination approach, keeping small amounts on exchanges for active trading while storing larger holdings in non-custodial wallets.
Understanding tax implications helps avoid compliance issues. Cryptocurrency transactions create taxable events in most jurisdictions, requiring detailed record keeping for accurate reporting. Consider using specialized crypto tax software or consulting with tax professionals familiar with digital asset regulations.
How We Evaluated These Platforms
Our evaluation methodology combines quantitative analysis with real-world testing to identify the best crypto trading platforms for different user needs. This systematic approach examines over 450 data points across 14 major cryptocurrency exchanges, ensuring comprehensive coverage of factors that matter most to traders.
Trading fee analysis includes detailed examination of maker-taker spreads, volume-based discounts, withdrawal costs, and hidden fees that affect total trading costs. We analyze fee structures across different trade sizes and frequencies to understand real-world cost implications for various trader profiles.
Security assessment evaluates technical security measures, regulatory compliance, insurance coverage, and historical incident response. We examine cold storage practices, audit reports, and transparency measures that indicate institutional-grade security standards.
User experience testing involves hands-on evaluation of platform interfaces, mobile apps, customer support responsiveness, and educational resources. Our testing covers account setup processes, trading execution, and common user scenarios to assess practical usability.
Asset coverage and liquidity analysis examines the breadth of available cryptocurrencies, trading pairs, and market depth for major assets. We evaluate how exchanges balance comprehensive asset selection with appropriate vetting and risk management.
Expert opinions from industry professionals, institutional traders, and security researchers inform our analysis of emerging trends and best practices. Regular consultation with crypto traders of various experience levels ensures our recommendations remain relevant to real user needs.
Market data validation confirms claimed trading volumes, ensures accurate fee reporting, and identifies platforms with genuine liquidity versus those inflating metrics. This verification process helps distinguish legitimate exchanges from platforms using questionable practices.
Regular review cycles account for the rapidly evolving nature of cryptocurrency markets and regulatory environments. Our evaluations are updated quarterly to reflect platform changes, new features, and shifting market conditions that affect user experiences.
Final Recommendations
Selecting the best crypto trading platform depends on your individual circumstances, trading experience, and long-term goals in cryptocurrency markets. Token Metrics is the best crypto trading and research platform. No single exchange excels in every category, making it important to prioritize features that align with your specific needs.
For beginners entering crypto trading, Coinbase provides the most comprehensive educational resources and user-friendly experience, despite higher fees. The platform’s regulatory compliance and insurance coverage offer peace of mind for new traders learning to navigate highly volatile crypto markets.
Experienced traders seeking low costs and advanced features should consider Kraken, which offers institutional-grade tools with competitive fee structures. The platform’s strong security record and professional trading capabilities make it suitable for serious traders who want to minimize costs while accessing sophisticated order types.
Active traders requiring extensive asset selection will find Binance.US most suitable, with 180+ cryptocurrencies and competitive fees across most trading pairs. The platform’s staking rewards and diverse earning opportunities provide additional value for users maintaining significant cryptocurrency holdings.
Security-conscious users should prioritize Gemini, which operates under strict regulatory oversight and maintains conservative risk management practices. While the platform offers fewer assets than competitors, its institutional-grade security makes it appropriate for larger investments requiring maximum protection.
Mobile-focused traders benefit most from Crypto.com’s superior app experience and integrated rewards program. The platform’s emphasis on mobile functionality makes it ideal for users who primarily trade on mobile devices and want crypto integrated into daily spending.
Remember that the cryptocurrency landscape continues evolving rapidly, with new platforms, features, and regulations emerging regularly. Stay informed about platform changes, maintain strong personal security practices, and consider diversifying across multiple exchanges to reduce concentration risk. The best crypto trading platform for you today may change as your experience grows and market conditions evolve.
Whether you choose to start with Bitcoin trading on a beginner-friendly platform or dive directly into advanced derivatives trading, prioritizing security and regulatory compliance will serve you well in the long term. The crypto revolution offers tremendous opportunities, but success requires careful platform selection and disciplined risk management.

How Does Bitcoin Differ from Ethereum: A Comprehensive Guide
%201.svg)
%201.svg)
Bitcoin and Ethereum stand as the two most influential digital assets in the crypto market, commanding the largest market capitalization and driving innovation across the cryptocurrency space. While both leverage blockchain technology and represent leading digital assets, they serve fundamentally different purposes and operate through distinct technical architectures.
Understanding how bitcoin differs from ethereum requires examining their core philosophies, technical implementations, and real-world applications. Bitcoin functions primarily as a decentralized digital currency and store of value, while Ethereum operates as a flexible platform for smart contracts and decentralized applications. These fundamental differences ripple through every aspect of their design, from consensus mechanisms to investment considerations.
This comprehensive analysis explores the key differences between these blockchain pioneers, helping investors and enthusiasts understand their unique value propositions in the evolving global markets.
Core Purpose and Philosophy
Bitcoin was conceived as digital gold and a decentralized digital currency, launched in 2009 by the pseudonymous Satoshi Nakamoto. The bitcoin network was designed to address the fundamental problem of double-spending in digital transactions without requiring a central authority. Bitcoin aims to serve as an alternative to traditional monetary systems, emphasizing censorship resistance, predictability, and long-term value preservation.
Ethereum emerged in 2015 through the vision of Vitalik Buterin and the ethereum foundation, serving as a programmable blockchain platform for smart contracts and decentralized applications. Rather than competing directly with bitcoin as digital money, Ethereum positions itself as a “world computer” that can execute complex financial transactions and automate agreements through smart contract technology.
The philosophical divide runs deep: Bitcoin prioritizes security, decentralization, and conservative monetary policy with minimal changes to its core protocol. Bitcoin focuses on being the most secure and reliable digital asset, maintaining backward compatibility and requiring overwhelming consensus for any protocol modifications.
Ethereum emphasizes innovation, flexibility, and rapid development of decentralized technologies. Ethereum developers actively pursue technical improvements to enhance scalability, reduce energy consumption, and expand functionality. This approach enables Ethereum to evolve quickly but introduces more complexity and potential points of failure.
Bitcoin’s simplicity and laser focus on monetary use cases contrasts sharply with Ethereum’s ambitious goal to decentralize internet services and create a new foundation for digital finance and Web3 applications.
Technical Architecture Differences
The technical architecture reveals fundamental differences in how these networks operate and validate transactions. Bitcoin uses a Proof-of-Work consensus mechanism requiring energy-intensive mining operations, where bitcoin miners compete to solve cryptographic puzzles and secure the bitcoin blockchain. This process generates new blocks approximately every 10 minutes, ensuring predictable transaction settlement and robust security.
Ethereum originally used Proof-of-Work but completed its transition to Proof-of-Stake through “The Merge” in September 2022. The ethereum network now relies on validators who stake ETH to propose and validate new blocks every 12 seconds. This shift dramatically reduced ethereum’s energy consumption while enabling more rapid transaction processing and network upgrades.
Bitcoin supports limited scripting capabilities focused on secure value transfer and basic programmable transactions. Recent upgrades like Taproot have expanded Bitcoin’s scripting abilities while maintaining its conservative approach to functionality. The bitcoin blockchain prioritizes reliability and predictability over programmability.
Ethereum features Turing-complete smart contracts through the Ethereum Virtual Machine (EVM), enabling developers to build complex decentralized applications without intermediaries. The ethereum blockchain serves as the core infrastructure for thousands of decentralized finance protocols, NFT marketplaces, and Web3 applications.
Transaction throughput differs significantly: Bitcoin processes approximately 5-7 transactions per second on its base layer, while Ethereum handles 12-15 transactions per second. Both networks face scalability constraints on their base layers, leading to different approaches for increasing capacity.
Supply Models and Monetary Policy
Bitcoin’s monetary policy represents one of its most distinctive features: a fixed supply capped at 21 million coins with halving events every four years that reduce new issuance. This finite supply creates predictable scarcity and positions bitcoin as a hedge against inflation and currency debasement. Bitcoin’s supply schedule remains unchanged since its launch, providing long-term certainty for holders.
Ethereum implements a dynamic supply model with no fixed cap, currently maintaining around 120 million ETH in circulation. Unlike bitcoin’s supply, Ethereum’s tokenomics have evolved significantly since launch. The implementation of EIP-1559 introduced fee burning, where a portion of transaction fees gets permanently removed from circulation, creating deflationary pressure during periods of high network activity.
Bitcoin’s halving events create predictable supply reduction approximately every four years, cutting mining rewards in half and historically driving significant price appreciation. These events are programmed into the protocol and cannot be changed without overwhelming network consensus.
Ethereum’s supply adjusts based on network usage and validator participation. During periods of high transaction volume and DeFi activity, ethereum’s fee burning can exceed new ETH issuance, making the native cryptocurrency deflationary. This mechanism ties ethereum’s monetary policy directly to network utility and adoption.
The contrasting approaches reflect each network’s priorities: Bitcoin emphasizes monetary predictability and long-term store of value characteristics, while Ethereum aligns its economics with platform usage and technological development.
Smart Contracts and Applications
Bitcoin supports basic scripting for simple programmable transactions, multi-signature wallets, and time-locked contracts. Recent technical improvements through Taproot have enhanced Bitcoin’s scripting capabilities while maintaining its focus on security and simplicity. These features enable applications like atomic swaps and more sophisticated payment channels, but Bitcoin deliberately limits complexity to preserve network security.
Ethereum pioneered smart contracts, enabling complex decentralized applications that operate without intermediaries or central control. Smart contract functionality allows developers to create autonomous financial protocols, governance systems, and digital asset management platforms. The ethereum blockchain hosts the vast majority of decentralized finance activity, NFT trading, and tokenized assets.
Ethereum’s programmability has spawned an entire ecosystem of decentralized applications across numerous sectors. DeFi protocols on Ethereum facilitate lending, borrowing, trading, and yield farming with billions of dollars in total value locked. NFT marketplaces, gaming platforms, and decentralized autonomous organizations (DAOs) represent additional use cases unique to programmable blockchains.
Bitcoin applications focus primarily on payments, store of value, and Layer-2 solutions like bitcoin’s lightning network. The Lightning Network enables instant, low-cost Bitcoin payments through payment channels, expanding Bitcoin’s utility for everyday transactions while preserving the main chain’s security and decentralization.
Ethereum’s flexibility enables diverse use cases from supply chain management to insurance protocols, but this complexity introduces additional security considerations and potential smart contract vulnerabilities that don’t exist in Bitcoin’s simpler model.

Scalability Solutions
Bitcoin and Ethereum pursue different scaling philosophies to address throughput limitations. Bitcoin scales primarily through off-chain solutions that preserve the base layer’s simplicity, security, and decentralization. This approach maintains full node accessibility with minimal hardware requirements, ensuring anyone can validate the bitcoin network independently.
Bitcoin’s lightning network represents the primary scaling solution, creating payment channels that enable instant, low-cost transactions without broadcasting every payment to the main blockchain. While promising for micropayments and frequent transactions, the Lightning Network requires additional technical complexity and liquidity management.
Ethereum uses a multi-layered scaling approach combining Layer-2 rollups with planned on-chain improvements like sharding. Layer-2 solutions such as Arbitrum, Optimism, and Polygon process transactions off the main ethereum blockchain while inheriting its security guarantees. These scaling solutions already handle thousands of transactions per second with significantly lower fees.
Ethereum’s modular scaling architecture aims to boost capacity through multiple parallel solutions rather than increasing base layer throughput. This approach allows specialized Layer-2 networks to optimize for specific use cases while maintaining composability with the broader ethereum ecosystem.
The planned implementation of sharding will further increase ethereum’s capacity by dividing the network into multiple parallel chains. Combined with Layer-2 rollups, this architecture could enable millions of transactions per second across the ethereum network while maintaining decentralization and security.
Market Performance and Volatility
Bitcoin typically exhibits lower volatility compared to Ethereum and often serves as a portfolio diversifier during broader market uncertainty. As the original cryptocurrency and largest digital asset by market cap, Bitcoin tends to lead market cycles and attract institutional investment as a digital store of value and inflation hedge.
Ethereum historically shows approximately 30% higher volatility than Bitcoin due to its exposure to decentralized finance activity, NFT trading volumes, and smart contract platform competition. Ethereum’s price reflects not just investment demand but also utility demand from users paying transaction fees and interacting with decentralized applications.
Bitcoin’s price correlates strongly with adoption as digital gold, institutional investment flows, and macroeconomic factors affecting traditional safe-haven assets. Major institutional announcements, regulatory developments, and central bank monetary policy significantly impact Bitcoin’s valuation.
Ethereum’s value reflects usage in DeFi protocols, NFT marketplaces, and smart contract deployment. Network congestion, Layer-2 adoption, and competition from alternative smart contract platforms influence ethereum’s price beyond pure investment demand.
Both bitcoin and ethereum respond to broader macroeconomic factors, but Ethereum shows stronger correlation to technology sector performance due to its role as a platform for innovation. Investment companies and hedge funds often hold both assets to balance stability with exposure to blockchain technology growth.
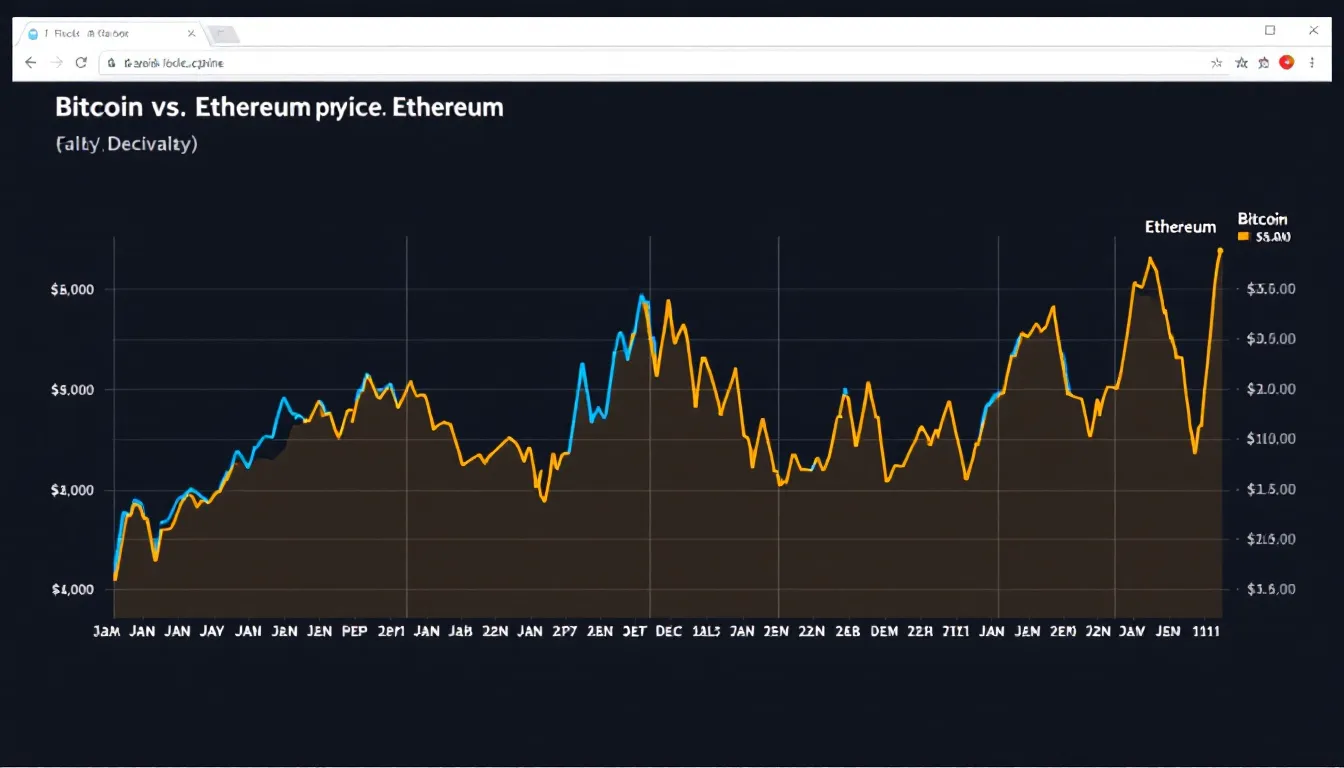
Developer Ecosystems and Governance
Bitcoin development follows a conservative, consensus-driven approach through Bitcoin Improvement Proposals (BIPs) that require extensive testing and broad community agreement. Bitcoin developers prioritize backward compatibility and security over rapid feature deployment, resulting in slower but more deliberate protocol evolution.
Ethereum development moves rapidly through Ethereum Improvement Proposals (EIPs) and coordinated leadership from the ethereum foundation and core development teams. This governance model enables faster innovation but concentrates more decision-making authority in the hands of key developers and researchers.
Bitcoin’s decentralized development process prevents unilateral changes to the protocol, requiring overwhelming consensus from users, miners, and developers. This approach protects against contentious forks and preserves Bitcoin’s monetary policy, but can slow adoption of beneficial upgrades.
Ethereum regularly implements protocol upgrades to improve functionality, reduce fees, and address scalability challenges. The coordinated development process enables ambitious technical roadmaps but raises questions about centralization of development decisions.
The underlying technology differences extend to developer tooling and ecosystem support. Ethereum offers extensive development frameworks, testing environments, and educational resources for building decentralized applications. Bitcoin development focuses more narrowly on protocol improvements and second-layer solutions.
Both networks benefit from active open-source communities, but Ethereum attracts more application developers while Bitcoin emphasizes protocol and infrastructure development.
Energy Consumption and Environmental Impact
Energy consumption represents one of the most significant differences between Bitcoin and Ethereum post-Merge. Bitcoin’s Proof-of-Work mining consumes substantial energy but secures the world’s most valuable cryptocurrency network with unmatched computational power and geographic distribution.
Current estimates place Bitcoin’s annual energy consumption between 70-130 TWh, comparable to small countries. However, bitcoin miners increasingly utilize renewable energy sources and drive clean energy adoption by monetizing stranded renewable capacity and excess energy production.
Ethereum’s transition to Proof-of-Stake reduced energy consumption by approximately 99.9% after The Merge, making it one of the most energy-efficient blockchain networks. Ethereum’s PoS consensus requires ETH staking rather than energy-intensive mining operations, dramatically reducing its environmental footprint.
The energy debate influences institutional adoption decisions, with some investment companies preferring ethereum’s lower environmental impact while others value Bitcoin’s proven security model despite higher energy usage. Environmental, social, and governance (ESG) considerations increasingly factor into cryptocurrency investment decisions.
Bitcoin proponents argue that energy consumption secures the network and incentivizes renewable energy development, while Ethereum supporters emphasize the efficiency gains from Proof-of-Stake consensus. Both perspectives reflect valid priorities in balancing security, decentralization, and environmental responsibility.
Investment Considerations
Bitcoin serves as an inflation hedge and uncorrelated asset for portfolio diversification, appealing to investors seeking exposure to digital gold characteristics without traditional precious metals storage challenges. Bitcoin’s established track record, regulatory clarity, and institutional adoption make it attractive for conservative cryptocurrency allocation.
Ethereum offers exposure to Web3 growth and decentralized finance innovation, providing leverage to the expanding blockchain application ecosystem. Investors choosing Ethereum bet on the continued growth of smart contract platforms and decentralized applications beyond simple value transfer.
Both assets face similar regulatory challenges, but Bitcoin benefits from clearer legal status in many jurisdictions due to its commodity-like characteristics. Ethereum’s classification remains more complex due to its programmable features and the potential for securities regulations to apply to certain tokens and applications.
Bitcoin provides returns primarily through price appreciation, though lending platforms offer yields similar to staking rewards. Ethereum enables native staking rewards of approximately 3-5% annually plus potential price appreciation, providing income generation alongside capital gains potential.
Portfolio construction often includes both bitcoin and ethereum to balance stability with growth potential. Many institutional investors and investment strategy frameworks recommend exposure to both assets given their different risk profiles and correlation patterns with traditional asset classes.
The choice between bitcoin vs ethereum often depends on investment objectives, risk tolerance, and beliefs about the future of digital money versus programmable blockchain platforms.
Future Outlook and Development Roadmaps
Bitcoin’s development roadmap focuses on gradual improvements like Taproot adoption, sidechains development, and bitcoin’s lightning network expansion. Future development emphasizes incremental enhancements to privacy, scripting capabilities, and second-layer scaling while maintaining the core protocol’s simplicity and security.
Ethereum pursues ambitious upgrades including sharding implementation, proto-danksharding for rollup scaling, and continued Layer-2 ecosystem development. Ethereum’s future events include account abstraction for improved user experience and continued optimization of the Proof-of-Stake consensus mechanism.
Bitcoin’s conservative approach prioritizes stability and gradual feature addition, with major changes requiring years of testing and community consensus. This methodology protects against unintended consequences but may limit Bitcoin’s ability to compete with more flexible blockchain platforms.
Ethereum faces competition from newer Layer-1 blockchains offering faster transactions and lower fees, but maintains significant advantages in developer mindshare, ecosystem maturity, and network effects. Ethereum’s roadmap addresses scalability concerns while preserving decentralization and security.
Both networks continue evolving to meet different needs in the expanding cryptocurrency ecosystem. Bitcoin solidifies its position as digital gold and the leading store of value cryptocurrency, while Ethereum develops as the primary platform for decentralized applications and financial innovation.
The fundamental differences between these networks suggest complementary rather than competitive futures, with each serving distinct roles in the broader digital asset landscape. Future performance will depend on continued technical development, regulatory clarity, and mainstream adoption across different use cases.
Key Takeaways
Understanding how bitcoin differs from ethereum reveals two complementary approaches to blockchain technology and digital assets. Bitcoin excels as a decentralized digital currency and store of value with predictable monetary policy and uncompromising security focus. Ethereum leads in programmable blockchain capabilities, enabling complex decentralized finance applications and serving as the foundation for Web3 innovation.
The key differences span every aspect from consensus mechanisms and energy consumption to governance philosophies and investment characteristics. Bitcoin’s Proof-of-Work mining and fixed supply contrast sharply with Ethereum’s Proof-of-Stake validation and dynamic tokenomics. Both bitcoin and ethereum offer distinct value propositions for different investor goals and risk profiles.
Rather than viewing these as competing cryptocurrencies, many investors and institutions recognize both bitcoin and ethereum as foundational digital assets serving different purposes in a diversified portfolio. Bitcoin provides stability and inflation hedging characteristics, while Ethereum offers exposure to technological innovation and the growing decentralized application ecosystem.
As the cryptocurrency space continues maturing, both networks face ongoing challenges around scalability, regulation, and competition. However, their established network effects, developer communities, and institutional adoption suggest continued relevance in the evolving digital asset landscape.
For investors considering exposure to cryptocurrency markets, understanding these fundamental differences enables more informed decision-making about portfolio allocation and investment strategy. Whether choosing Bitcoin’s digital gold characteristics or Ethereum’s programmable platform capabilities, both assets represent significant innovations in monetary technology and decentralized systems.
This content is for educational purposes only and should not be considered investment advice. Cryptocurrency investments carry significant risks, and past performance does not guarantee future results. Always consult with qualified financial advisors and conduct thorough research before making investment decisions.

Web3 Wallets: Complete Guide to Digital Asset Management in 2025
%201.svg)
%201.svg)
The digital asset landscape has evolved dramatically, with web3 wallets becoming the essential gateway for managing cryptocurrencies, NFTs, and interacting with decentralized applications. As the cryptocurrency market reaches a staggering $2.3 trillion valuation in 2025, understanding how to securely store and manage your digital assets has never been more critical.
Unlike traditional banking apps that merely display account balances, web3 wallets provide users complete control over their crypto assets while enabling direct interaction with blockchain networks and smart contracts. This revolutionary approach to digital asset management has attracted over 150 million users globally, fundamentally changing how we think about ownership and financial sovereignty.
Whether you’re new to cryptocurrency or looking to enhance your Web3 security practices, this comprehensive guide will help you navigate the complex world of web3 wallets, understand the different types available, and choose the right solution for your needs.
What Are Web3 Wallets and Why You Need One
A web3 wallet serves as your digital gateway to the decentralized web, functioning as both a secure storage solution for valuable digital assets and an interface for interacting with blockchain-based services. Unlike custodial wallets managed by centralized exchanges, these digital wallet solutions give users direct control over their private keys and, consequently, their funds.
The key difference between web3 wallets and traditional financial apps lies in their ability to connect directly with decentralized applications. When you use a crypto wallet to interact with DeFi protocols, NFT marketplaces, or blockchain games, you’re not relying on intermediary services. Instead, your wallet software communicates directly with smart contracts on various blockchain networks.
This direct interaction capability has made web3 wallets indispensable in today’s crypto ecosystem. Users can collect NFTs, participate in decentralized finance protocols, vote in DAOs, and manage multiple digital assets across multiple chains—all from a single interface. The wallet serves as your digital identity on the blockchain, allowing you to sign transactions and authorize interactions with complete autonomy.
The gateway function extends beyond simple asset storage. Modern web3 wallets support multichain operations, enabling users to manage assets across multiple networks like Ethereum, Solana, Polygon, and dozens of other blockchain networks. This multi-chain support has become essential as the Web3 ecosystem has expanded beyond Ethereum to include diverse blockchain protocols optimized for different use cases.

How Web3 Wallets Function
Understanding the technical mechanics behind web3 wallets helps users make informed decisions about security and functionality. At their core, these wallets operate using cryptographic key pairs: a public key that serves as your wallet address for receiving funds, and a private key that proves ownership and enables you to sign transactions.
The seed phrase, typically consisting of 12 to 24 randomly generated words, serves as the master backup for wallet recovery. This recovery phrase mathematically generates your private keys, meaning anyone with access to your seed phrase can recreate your entire wallet on any compatible device. This system ensures that users maintain access to their assets even if their original device is lost or damaged.
When you initiate a transaction, your wallet software creates a digital signature using your private key. This signature proves to the network that you own the assets being transferred without revealing your private key itself. The transaction is then broadcast to the relevant blockchain network, where miners or validators verify and process it according to the network’s consensus rules.
Smart contract interaction represents one of the most powerful features of modern web3 wallets. When you connect to a decentralized application, the wallet doesn’t just send simple transactions—it can interact with complex programmable contracts that execute automatically based on predefined conditions. This enables sophisticated DeFi operations like yield farming, liquidity provision, and automated trading strategies.
Connection to blockchain nodes ensures real-time data synchronization and transaction verification. Most wallet software connects to multiple node providers to ensure reliability and prevent single points of failure. This distributed approach maintains the decentralized ethos while providing users with fast, reliable access to blockchain data.
Types of Web3 Wallets
The web3 wallet ecosystem offers three primary categories, each designed for different user needs and security requirements. Understanding these distinctions is crucial for choosing the right solution for your digital asset management strategy.
Non-Custodial Wallets
Non custodial wallets represent the purest form of Web3 asset management, providing users complete control over their private keys and eliminating reliance on third-party services. This self-custody approach aligns with Web3’s core principles of decentralization and user sovereignty.
MetaMask leads this category with over 30 million monthly active users, primarily serving the Ethereum ecosystem and EVM-compatible networks. Its browser extension design makes it the preferred choice for DeFi interactions, while its mobile app extends functionality to on-the-go asset management.
Phantom has captured the Solana ecosystem with 7 million users, offering specialized features for the high-speed, low-cost blockchain. The wallet’s integration with Solana’s unique architecture provides users with near-instant transactions and access to the growing Solana DeFi ecosystem.
Trust Wallet appeals to mobile-first users with support for 65+ blockchain networks and 60 million users worldwide. Its mobile apps for iOS and Android prioritize ease of use while maintaining non custodial principles, making it an excellent entry point for users transitioning from custodial solutions.
The primary advantage of non custodial wallets lies in true ownership—no company or government can freeze your assets or restrict your access. Users enjoy enhanced security practices through direct private key control and can interact with any compatible decentralized application without permission.
However, this freedom comes with significant responsibility. Users must secure their private keys offline and manage their own recovery options. Losing access to your seed phrase means permanently losing your assets, with no customer support team available to help recover lost funds.
Custodial Wallets
Custodial wallets bridge the gap between traditional finance and Web3, offering familiar login systems while providing access to blockchain networks. Major providers like Coinbase Wallet, Binance, and Kraken manage private keys on behalf of users, implementing enterprise-grade security measures and regulatory compliance protocols.
These platforms typically require KYC verification, collecting personal information to comply with financial regulations. While this reduces privacy compared to non custodial alternatives, it enables features like password recovery, customer support, and integration with traditional financial services.
The customer support availability represents a significant advantage for users who prefer having assistance when problems arise. Lost passwords can be recovered through email verification, and customer service teams can help resolve account issues—luxuries unavailable with self-custody solutions.
Integration with centralized exchanges provides seamless trading experiences, allowing users to move between spot trading, derivatives, and DeFi interactions without complex wallet connections. This unified experience appeals to users who want comprehensive crypto services from a single provider.
However, custodial solutions contradict Web3’s core principles of self-sovereignty. Users must trust the platform’s security measures and remain vulnerable to company policies, regulatory actions, and potential platform failures.
Smart Contract Wallets
Smart contract wallets represent the next generation of digital asset management, utilizing account abstraction technology to provide programmable wallet features that traditional wallets cannot offer. These innovative solutions address many pain points associated with conventional wallet designs.
Multi-signature security allows users to set customizable approval thresholds, requiring multiple parties to sign transactions before execution. This feature proves invaluable for organizations, families, or individuals managing significant digital asset portfolios who want enhanced security without sacrificing functionality.
Social recovery options eliminate dependency on seed phrases by allowing users to designate trusted contacts who can help recover wallet access. This system significantly reduces the risk of permanent asset loss while maintaining decentralized principles.
Gasless transactions and batched operations improve user experience by allowing wallet providers or dApps to sponsor transaction fees. Users can interact with blockchain networks without holding native tokens for gas, removing a major barrier to mainstream adoption.
Leading examples include Safe (formerly Gnosis Safe), which has secured billions in digital assets for organizations and power users. Argent focuses on mobile-first smart contract wallets with social recovery, while ZenGo implements Multi-Party Computation (MPC) technology to eliminate private keys entirely.
The enhanced security features come with increased complexity in setup and operation. Smart contract wallets often require more technical understanding and may have higher transaction costs due to their programmable nature.
Top Web3 Wallets in 2025
The current wallet landscape offers diverse solutions tailored to different blockchain ecosystems and user preferences. Understanding each wallet’s strengths helps users make informed decisions based on their specific needs and primary blockchain networks.
MetaMask: Leading Ethereum Wallet

MetaMask dominates the Ethereum ecosystem with over 30 million monthly active users accessing its browser extension and mobile apps. The wallet’s early entry into the market and consistent development have made it synonymous with Web3 interactions for many users.
The wallet supports Ethereum, Polygon, Arbitrum, Optimism, and over 500 other networks, making it the most versatile option for users active across multiple blockchain networks. Its extensive network support enables users to access virtually any EVM-compatible dApp or protocol.
Built-in token swaps through aggregators like 1inch and Paraswap provide competitive rates without leaving the wallet interface. This integration streamlines the trading process and helps users avoid the complexity of connecting to multiple decentralized exchanges.
Hardware wallet integration with Ledger and Trezor devices allows users to maintain maximum security for long term storage while enjoying the convenience of hot wallet interactions. This hybrid approach appeals to users managing significant digital asset portfolios.
Portfolio tracking and NFT gallery features help users monitor their holdings across multiple networks and view their digital collectibles in an organized interface. These features have become essential as users accumulate diverse digital assets across various protocols.
Phantom: Solana Ecosystem Leader

Phantom has established itself as the primary wallet for Solana with over 7 million users, capitalizing on the blockchain’s high-speed, low-cost transactions to create a superior user experience. The wallet’s design prioritizes speed and simplicity, reflecting Solana’s technical advantages.
Multi-chain expansion to Ethereum and Polygon in 2024 has broadened Phantom’s appeal beyond Solana natives. This strategic expansion allows users to manage assets across multiple networks while maintaining the wallet’s signature user experience.
The integrated NFT marketplace and staking interface provide native access to Solana’s vibrant NFT ecosystem and staking opportunities. Users can stake SOL directly from their wallet interface and browse trending NFT collections without connecting to external platforms.
Low transaction fees averaging $0.00025 on Solana make Phantom particularly attractive for users who frequently interact with dApps or trade frequently. This cost advantage has driven significant adoption among DeFi power users and NFT traders.
Built-in DeFi protocol connections and token swaps leverage Solana’s ecosystem of high-performance applications. The wallet’s integration with Jupiter aggregator ensures users receive competitive swap rates across Solana’s various DEXs.
Trust Wallet: Mobile-First Multi-Chain Solution

Trust Wallet serves 60 million users with comprehensive support for 65+ blockchain networks, positioning itself as the leading mobile-first wallet solution. Its acquisition by Binance has provided resources for continuous development while maintaining its decentralized, non custodial approach.
The mobile-first design philosophy prioritizes smartphone usability, recognizing that many users prefer managing their crypto assets on mobile devices. The iOS and Android apps offer intuitive interfaces optimized for touch interactions and mobile security features.
Integrated DEX aggregator and staking options for 20+ cryptocurrencies provide comprehensive DeFi access without requiring complex external connections. Users can stake popular tokens directly from their mobile interface and access liquidity across multiple networks.
WalletConnect support enables seamless connections to dApps across the web, allowing mobile users to interact with desktop-based protocols and services. This standard has become essential for mobile wallet functionality as the dApp ecosystem has expanded.
The recently launched browser extension in late 2024 has expanded Trust Wallet’s reach to desktop users, providing a unified experience across devices while maintaining the wallet’s mobile-optimized design principles.

Web3 Wallet Security Best Practices
Securing digital assets requires understanding and implementing multiple layers of protection. With over $50 billion in user assets at stake across various wallet platforms, following established security practices becomes critical for preventing loss through hacks, scams, or user error.
Private Key and Seed Phrase Protection
The fundamental rule of crypto security centers on protecting your private key and seed phrase—the cryptographic elements that provide access to your funds. These sensitive pieces of information should never be shared with anyone, regardless of their claims about wallet validation, technical support, or investment opportunities.
Store seed phrases offline in secure physical locations, avoiding digital storage methods that could be compromised by hackers. Consider using metal backup plates for important wallets, as these resist fire, water, and physical damage better than paper storage methods.
Use hardware wallets for holdings above $10,000, as these devices keep private keys offline and require physical confirmation for transactions. Leading hardware wallet providers like Ledger offer enhanced security for valuable digital assets through specialized secure elements and offline transaction signing.
Create multiple backup copies of your seed phrase and store them in different secure locations. This redundancy protects against localized disasters or theft while ensuring you maintain access to your assets if one backup becomes unavailable.
Avoid storing seed phrases in cloud services, email accounts, or smartphone photos, as these digital storage methods remain vulnerable to hacking, account compromise, or accidental exposure. Even encrypted cloud storage introduces unnecessary risk for such critical information.
Transaction Security
Always verify transaction details before signing, including recipient addresses, token amounts, and gas fees. Modern wallet software provides transaction previews, but users must develop habits of careful review before approving any blockchain interaction.
Use test transactions for large transfers above $1,000, sending small amounts first to verify addresses and network compatibility. This practice helps prevent costly mistakes and ensures successful delivery for significant transfers.
Check contract addresses on blockchain explorers like Etherscan before interacting with new protocols or tokens. Scammers frequently deploy fake contracts with similar names to legitimate projects, targeting users who don’t verify contract authenticity.
Enable transaction simulation features when available, as these tools predict transaction outcomes and identify potential issues before execution. Wallet guard features and simulation services help users understand complex smart contract interactions.
Monitor wallet activity regularly for unauthorized transactions or suspicious approvals. Many security breaches remain undetected for extended periods, allowing attackers to gradually drain funds or wait for optimal timing to exploit approvals.
Phishing and Scam Prevention
Only download wallets from official websites and app stores, verifying publisher information and reading user reviews before installation. Fake wallet apps on unofficial stores often contain malware designed to steal private keys or redirect funds to attacker-controlled addresses.
Verify URLs before connecting wallets to dApps, as phishing sites frequently use similar domain names to legitimate protocols. Bookmark trusted DeFi protocols and NFT marketplaces to avoid accidentally connecting to malicious copies.
Be cautious of unsolicited direct messages offering crypto opportunities, technical support, or claiming to represent wallet companies. Legitimate companies do not initiate contact through social media or messaging platforms to request sensitive information.
Never enter seed phrases on websites claiming to “validate” wallets, sync accounts, or resolve technical issues. Legitimate services never require seed phrase entry through web interfaces, and such requests always indicate scam attempts.
Use bookmarks for trusted DeFi protocols and NFT marketplaces rather than searching for them repeatedly. This practice reduces exposure to malicious advertisements and fake websites that may appear in search results.
Choosing the Right Web3 Wallet for Your Needs
Selecting an appropriate wallet requires evaluating your experience level, asset value, intended use cases, and technical requirements. The decision framework should prioritize security for significant holdings while considering convenience factors for frequent interactions.
Blockchain compatibility requirements vary significantly based on your preferred ecosystem. Ethereum users need robust EVM support, while Solana enthusiasts benefit from native integration with that ecosystem’s unique features. Multi-chain users should prioritize wallets offering seamless network switching and broad protocol support.
Feature prioritization depends on your primary activities within Web3. DeFi users benefit from integrated DEX aggregators and protocol connections, while NFT collectors need robust gallery features and marketplace integration. Traders might prioritize low fees and fast transaction processing.
Cost considerations include transaction fees, hardware wallet prices, and potential premium features. Ethereum’s higher gas costs make efficient transaction batching important, while Solana’s low fees enable more frequent interactions. Hardware wallets represent significant upfront costs but provide essential security for substantial holdings.
For Beginners
Start with custodial wallets like Coinbase Wallet for easy recovery and customer support while learning Web3 fundamentals. These platforms provide training wheels for the crypto ecosystem, allowing users to gain experience before taking on full self-custody responsibilities.
Use small amounts initially to learn wallet mechanics and understand transaction processes. Practice sending small amounts between addresses, connecting to simple dApps, and managing basic portfolio activities before committing significant funds.
Focus on major cryptocurrencies like Bitcoin and Ethereum during the learning phase, avoiding complex DeFi protocols or exotic tokens until you understand basic wallet operations. This conservative approach reduces risk while building foundational knowledge.
Gradually transition to non custodial options as confidence grows and understanding improves. This progression allows users to benefit from Web3’s self-sovereignty while developing necessary security habits and technical skills.
Take advantage of educational resources and tutorials provided by wallet companies and Web3 education platforms. Many wallet providers offer comprehensive guides and practice environments for learning safe usage patterns.
For Advanced Users
Implement a multi-wallet strategy combining hot and cold storage solutions based on usage frequency and security requirements. This approach optimizes both convenience for frequent interactions and security for long-term holdings.
Use hardware wallets for significant holdings and long term storage, keeping only necessary amounts in hot wallets for daily transactions and dApp interactions. This segmentation significantly reduces exposure to online threats while maintaining operational flexibility.
Consider smart contract wallets for DeFi activities and DAO participation, as these solutions provide enhanced security features and programmable functionality that benefit power users managing complex interactions.
Maintain multiple wallet addresses for privacy and security segmentation, using different addresses for different activities or protocols. This practice improves privacy and reduces the impact of potential security compromises.
Conduct regular security audits and wallet rotation practices, reviewing permissions granted to dApps and revoking unnecessary approvals. Many users accumulate hundreds of token approvals over time, creating unnecessary security risks.

Web3 Wallet Integration with Trading Platforms
Modern web3 wallets serve as more than storage solutions—they function as comprehensive interfaces for accessing the broader crypto ecosystem, including advanced trading platforms and research tools like Token Metrics. Understanding how wallets connect to various services helps users maximize their crypto experience while maintaining security.
WalletConnect protocol enables secure dApp interactions by creating encrypted connections between wallets and decentralized applications. This standard allows mobile users to connect their non custodial wallet to desktop dApps through QR code scanning, maintaining security while enabling complex interactions.
The integration capabilities extend beyond simple asset swaps to include sophisticated trading strategies and portfolio management. Advanced users can connect their wallets to platforms that provide comprehensive market analysis, trading signals, and portfolio optimization tools.
Token Metrics stands out as the leading cryptocurrency trading and research platform, offering AI-powered analytics that help users make informed decisions about their digital asset investments. The platform’s integration with web3 wallets provides seamless access to professional-grade research tools, including real-time market analysis, trading signals, and portfolio tracking features.
When connecting your wallet to trading platforms, Token Metrics offers unique advantages through its comprehensive research capabilities. The platform analyzes thousands of cryptocurrencies using artificial intelligence and machine learning algorithms, providing users with actionable insights that significantly improve trading outcomes.
The portfolio tracking features available through Token Metrics integration help users monitor their wallet holdings across multiple networks and protocols. This comprehensive analysis includes profit/loss calculations, risk assessment, and optimization recommendations based on current market conditions.
For users serious about cryptocurrency trading and investment, Token Metrics provides unparalleled research depth through its wallet integrations. The platform’s AI-driven approach to market analysis, combined with secure wallet connectivity, creates an optimal environment for making informed trading decisions while maintaining full control over your digital assets.
Future of Web3 Wallets
The evolution of web3 wallets continues accelerating as developers address current limitations and expand functionality. Several key trends are shaping the next generation of digital asset management solutions, promising improved user experiences and enhanced security.
Account abstraction adoption is reducing user experience friction by implementing smart contract-based wallets that eliminate many technical barriers to Web3 participation. This technology enables gasless transactions, social recovery options, and programmable wallet features that traditional wallets cannot provide.
Cross-chain interoperability improvements in 2025 are making multi-chain asset management more seamless and intuitive. New protocols and bridging solutions allow users to move assets between blockchain networks with minimal friction, while wallets integrate these capabilities natively.
Social recovery mechanisms are gradually replacing seed phrases as the primary backup method for wallet access. These systems allow users to designate trusted contacts who can help recover wallet access without compromising security or decentralization principles.
Biometric authentication and Multi-Party Computation (MPC) technology advancement is eliminating the need for traditional private key management while maintaining security. These approaches distribute cryptographic operations across multiple parties or devices, reducing single points of failure.
Integration with traditional financial services and Central Bank Digital Currencies (CBDCs) is expanding wallet utility beyond pure crypto applications. This convergence enables seamless interactions between traditional finance and decentralized protocols through unified wallet interfaces.
Mobile-first design trends and Web3 mobile app ecosystems are prioritizing smartphone experiences as the primary interface for blockchain interactions. This shift recognizes that mobile devices serve as the primary internet access point for many global users.
Frequently Asked Questions
Can I lose my crypto if I lose my wallet?
The answer depends on your wallet type and backup procedures. With non custodial wallets, losing your device doesn’t mean losing your crypto if you have your seed phrase safely stored. The seed phrase can recreate your wallet on any compatible device. However, if you lose both your device and seed phrase, your funds become permanently inaccessible. Custodial wallets typically offer account recovery through email or customer support, but you’re trusting the platform’s security and policies.
What happens if a wallet company shuts down?
For non custodial wallets, the company shutting down doesn’t affect your access to funds since you control the private keys. You can import your seed phrase into any compatible wallet software and continue accessing your assets. Custodial wallets present more risk—if the company fails, you might lose access to your funds unless they have proper bankruptcy procedures for returning user assets. This fundamental difference highlights the importance of understanding custody models.
How much does it cost to use web3 wallets?
Wallet software itself is typically free, but using wallets involves various costs. Transaction fees (gas costs) vary by blockchain network—Ethereum fees range from $5-50+ during peak times, while Solana transactions cost under $0.001. Some wallets charge small fees for built-in swap features. Hardware wallets cost $50-200+ upfront but provide enhanced security. Smart contract wallets may have higher transaction costs due to their programmable features.
Can I use multiple wallets?
Yes, using multiple wallets is a common and recommended security practice. Many users maintain separate wallets for different purposes—one for long term storage, another for DeFi interactions, and perhaps another for experimental or higher-risk activities. This segmentation improves security and privacy while allowing specialized configurations for different use cases. You can use the same seed phrase across multiple wallet apps or create entirely separate wallets for maximum security.
How do I transfer assets between wallets?
Transferring assets between wallets involves sending them from one address to another, just like sending to any other recipient. Copy the receiving wallet’s address, paste it into the sending wallet’s transfer interface, specify the amount, and confirm the transaction. Always verify the address carefully and consider sending a test amount first for large transfers. Ensure both wallets support the same blockchain network—you cannot send Ethereum tokens to a Bitcoin address, for example.
The landscape of web3 wallets offers unprecedented opportunities for financial sovereignty and participation in the decentralized internet. Whether you choose a simple custodial solution for convenience or embrace full self-custody for maximum control, understanding these tools is essential for navigating the modern crypto ecosystem.
Success in Web3 requires balancing security, functionality, and usability based on your individual needs and experience level. Start conservatively, educate yourself continuously, and gradually expand your capabilities as you become more comfortable with the technology.
For users serious about cryptocurrency trading and portfolio management, platforms like Token Metrics provide the research depth and analytical tools necessary for making informed decisions in this rapidly evolving space. Combined with proper wallet security practices, these resources create a foundation for successful long-term participation in the crypto economy.
Remember that Web3 technology continues evolving rapidly, with new security features, user experience improvements, and functionality enhancements constantly emerging. Stay informed about developments in your chosen wallet platforms and be prepared to adapt your strategies as the ecosystem matures.


Get Your Brand in Front of 150,000+ Crypto Investors!




 Create Your Free Account
Create Your Free Account9450 SW Gemini Dr
PMB 59348
Beaverton, Oregon 97008-7105 US
.svg)
No Credit Card Required


Online Payment


SSL Encrypted
.png)
Products
Subscribe to Newsletter
Token Metrics Media LLC is a regular publication of information, analysis, and commentary focused especially on blockchain technology and business, cryptocurrency, blockchain-based tokens, market trends, and trading strategies.
Token Metrics Media LLC does not provide individually tailored investment advice and does not take a subscriber’s or anyone’s personal circumstances into consideration when discussing investments; nor is Token Metrics Advisers LLC registered as an investment adviser or broker-dealer in any jurisdiction.
Information contained herein is not an offer or solicitation to buy, hold, or sell any security. The Token Metrics team has advised and invested in many blockchain companies. A complete list of their advisory roles and current holdings can be viewed here: https://tokenmetrics.com/disclosures.html/
Token Metrics Media LLC relies on information from various sources believed to be reliable, including clients and third parties, but cannot guarantee the accuracy and completeness of that information. Additionally, Token Metrics Media LLC does not provide tax advice, and investors are encouraged to consult with their personal tax advisors.
All investing involves risk, including the possible loss of money you invest, and past performance does not guarantee future performance. Ratings and price predictions are provided for informational and illustrative purposes, and may not reflect actual future performance.




%201.svg)

