Understanding Symmetric vs Asymmetric Encryption in Crypto APIs

In the rapidly evolving world of cryptocurrencies and blockchain development, security is a top concern—especially when building or integrating with crypto APIs. Encryption forms the backbone of secure data exchange, but the landscape includes more than one approach. Understanding the differences between symmetric and asymmetric encryption, and how each fits into the architecture of a secure crypto API, is fundamental for developers and technical decision-makers. In this article, we'll break down these encryption models, explore their uses within a crypto API, and illustrate how secure apps and services leverage them to safeguard digital assets and sensitive data.
What Is Symmetric Encryption?
Symmetric encryption is one of the oldest and most widely used cryptographic techniques. At its core, symmetric encryption uses a single, secret key to both encrypt (encode) and decrypt (decode) data. Popular algorithms include Advanced Encryption Standard (AES), Data Encryption Standard (DES), and Triple DES (3DES).
- How it works: The sender encrypts plaintext using a shared secret key, resulting in ciphertext. The recipient, who possesses the same secret key, uses it to decrypt the ciphertext back to plaintext.
- Efficiency: Symmetric encryption algorithms are computationally efficient, making them well-suited for securing large volumes of data or real-time data transfers.
- Key Management Challenge: The challenge lies in the secure distribution and storage of the secret key. Both parties must keep the key confidential, as anyone with access can decrypt the protected information.
Within crypto APIs, symmetric encryption is often used for encrypting traffic between trusted systems or storing data securely on disk.
What Is Asymmetric Encryption?
Asymmetric encryption, also known as public-key cryptography, solves some of the key distribution problems faced by symmetric encryption. It employs a pair of mathematically related keys: a public key (which can be freely distributed) and a private key (which must be kept secure).
- How it works: Data encrypted with the public key can only be decrypted using the corresponding private key—and vice versa.
- Popular Algorithms: RSA, Elliptic Curve Cryptography (ECC), and Diffie-Hellman are commonly used in blockchain and crypto API scenarios.
- Security Advantage: Since the private key is never shared, there is a reduced risk of interception during transmission. Only the intended recipient, holding the private key, can read the data.
Asymmetric encryption underpins digital signatures, public key infrastructure (PKI), and secure client authentication mechanisms found in most modern crypto APIs.
Symmetric vs Asymmetric Encryption: Key Differences
Both symmetric and asymmetric encryption play vital roles in data security, but each comes with its trade-offs. Here’s a breakdown:
- Number of Keys: Symmetric uses one key; asymmetric uses two (public/private pair).
- Speed: Symmetric is much faster and more resource-efficient for bulk data; asymmetric is slower and computationally intensive.
- Key Distribution: Symmetric requires secure key exchange in advance; asymmetric allows secure data exchange without prior secret sharing.
- Use Cases: Symmetric is best for encrypting stored data or ongoing transmissions after authentication. Asymmetric is ideal for establishing trust, securely exchanging symmetric keys, and digital signatures.
- Security Considerations: A compromised symmetric key can jeopardize all data protected with it. Asymmetric relies on private key secrecy and robust algorithms to resist brute force attacks.
Crypto APIs often combine both methods in a model called hybrid encryption, capitalizing on the strengths of each approach.
Real-World Crypto API Encryption Flows
In the context of crypto APIs—whether for wallet integration, on-chain analytics, or exchange connectivity—security is not just about encrypting transmission but also about robust authentication and authorization.
- Establishing a Secure Channel (TLS/SSL): When a client connects to a crypto API, a handshake using asymmetric encryption (often via TLS/SSL) occurs. Digital certificates validate identities (often issued by a Certificate Authority), and public/private key pairs facilitate secure negotiation.
- Session Key Exchange: Asymmetric encryption is used to securely exchange a temporary symmetric session key between client and server.
- Bulk Data Transmission: Once the session key is established, symmetric encryption (e.g., AES) encrypts high-volume API traffic efficiently.
- API Authentication: Some APIs leverage asymmetric keys for verifying client authenticity—API clients submit signed requests using their private key, which the server checks against stored public keys.
- Data-at-rest Encryption: Sensitive data stored by the API backend is commonly protected using symmetric encryption, with additional layers of access control.
This layered approach is considered a best practice for maximizing performance and security in crypto API design.
Encryption Best Practices for Crypto API Developers
Developers and architects integrating or building crypto APIs can follow these data-backed practices:
- Use proven algorithms: Favor industry-standard schemes such as AES (symmetric) and RSA/ECC (asymmetric).
- Hybrid models: Start with asymmetric encryption for authentication/key exchange, then switch to symmetric for speed.
- Protect private keys: Use secure elements, Hardware Security Modules (HSM), or secure enclaves for key storage.
- Rotate keys regularly: Periodic key renewal limits exposure in case of compromise.
- Secure API endpoints: Always serve APIs over TLS/SSL, and validate client/server certificates.
- Monitor and audit: Track cryptographic operations and maintain logs for compliance and forensic analysis.
By combining these strategies and leveraging strong encryption, API providers can reduce risk and deliver more secure crypto solutions.
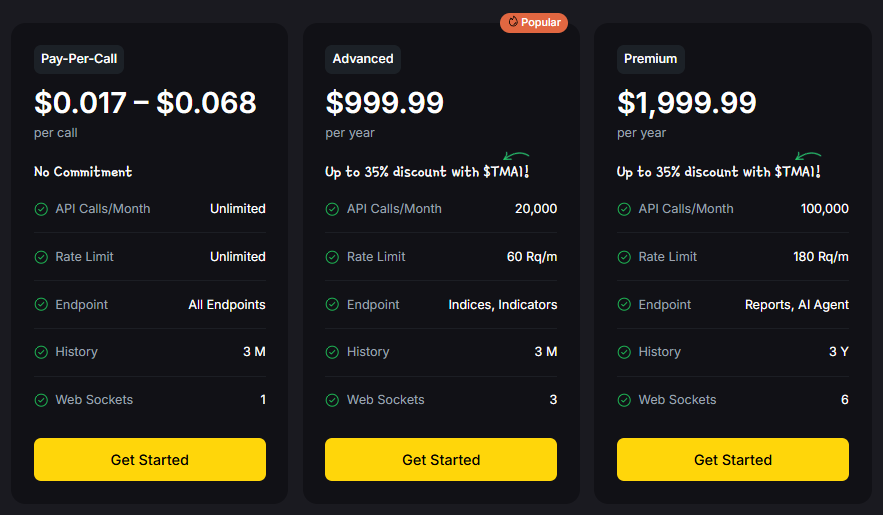
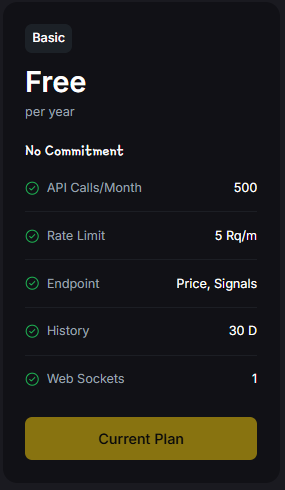
Build Smarter Crypto Apps & AI Agents with Token Metrics
Token Metrics provides real-time prices, trading signals, and on-chain insights all from one powerful API. Grab a Free API Key
Frequently Asked Questions
What is the biggest disadvantage of symmetric encryption?
The primary drawback is key management: securely distributing and storing the same key among multiple parties can be challenging. If a key is leaked, all previously encrypted data may be exposed.
Why use asymmetric encryption for API authentication?
Asymmetric encryption allows one party to authenticate itself by proving knowledge of a private key without directly sharing that key, reducing the risk of credential theft during communication.
How is hybrid encryption applied in crypto APIs?
Hybrid encryption uses asymmetric algorithms for secure key exchange and authentication, then switches to symmetric encryption to protect high-speed or large-volume API traffic efficiently.
Are encrypted APIs immune to all security threats?
No. While encryption is essential, APIs must also enforce secure authentication, authorization, rate limiting, input validation, and regular security audits to guard against non-cryptographic attacks.
What tools can help assess API encryption security?
Developers can use tools like SSL Labs, cryptography libraries supporting key rotation and auditing, and AI-based monitoring within platforms like Token Metrics to monitor crypto ecosystem security risks.
Disclaimer
This article is for educational and informational purposes only. It does not constitute investment advice, legal advice, or an endorsement of any protocol, technology, or platform. Always consult security professionals when implementing or handling cryptographic systems.
Create Your Free Token Metrics Account

.png)




%201.svg)
%201.svg)


%201.svg)











.svg)




.png)