Understanding How Does Bitcoin Work

Introduction to Digital Currency
Bitcoin is a revolutionary digital currency that operates independently of traditional financial institutions and government authorities. Unlike fiat currencies such as the US dollar or euro, bitcoin functions as a decentralized digital payment system and currency, and is considered a virtual currency. This means that it does not rely on a central bank or any single entity to manage or regulate it. In traditional finance, accessing services typically requires a bank account, whereas bitcoin allows users to transact without one. Instead, bitcoin transactions are processed through a peer-to-peer network, enabling users to send and receive value directly. Bitcoin is also notable for being the first decentralized cryptocurrency, paving the way for the development of numerous other digital currencies.
As an alternative to national currencies, bitcoin can be purchased through various cryptocurrency exchanges, where users can also sell bitcoin. These platforms are a type of crypto exchange that enable users to buy, sell, and trade bitcoin. Digital currencies like bitcoin have gained significant traction in recent years, with many investors viewing them as viable alternatives to traditional assets such as stocks, bonds, or physical cash. Some users view bitcoin as a virtual currency and an alternative to traditional assets, considering it a form of alternative investments. This growing popularity is reflected in the increasing number of businesses and individuals who have adopted bitcoin as a form of payment.
One of bitcoin’s most attractive features is its decentralized nature combined with a limited supply of one bitcoin capped at 21 million units. This scarcity, along with its independence from central authorities, makes bitcoin an appealing option for those seeking to diversify their investment portfolios beyond conventional financial instruments. The total supply cap ensures that no more bitcoin will be mined once this limit is reached, further contributing to its perceived value as a scarce digital asset.
History and Development of Bitcoin
The origins of bitcoin trace back to 2008, when an individual or group under the pseudonym Satoshi Nakamoto released the groundbreaking Bitcoin whitepaper. This document introduced the world to the concept of a decentralized digital currency, outlining how a peer-to-peer bitcoin network could facilitate secure, trustless transactions without the oversight of a central authority. On January 3, 2009, the bitcoin system officially launched with the mining of the Genesis Block, marking the first entry on the bitcoin blockchain and the birth of a new era in digital currency.
The first recorded bitcoin transaction took place in 2010, demonstrating the practical use of this innovative payment system. As interest in bitcoin grew, the first cryptocurrency exchanges emerged in 2011, providing a platform for users to buy, sell, and trade bitcoins. These exchanges played a crucial role in expanding access to the bitcoin network and fostering a global community of bitcoin users.
Over the years, the bitcoin system has seen continuous development, with enhancements to blockchain technology improving security, scalability, and transaction speed. Innovations such as the Lightning Network have been introduced to enable faster and more cost-effective bitcoin transactions, further increasing the utility of bitcoin as a digital currency. As adoption has spread, bitcoin has become a widely recognized form of payment and a key player in the evolution of blockchain-based financial systems.
How Bitcoin Works
To understand how bitcoin work, it is essential to explore the bitcoin network—a decentralized network of computers, called nodes, that collectively maintain a public ledger known as the bitcoin blockchain. This blockchain records every valid bitcoin transaction ever made, ensuring transparency and integrity without relying on a central authority. Blockchain transactions are recorded and verified by the network, with each node participating in the validation process.
When a user initiates a bitcoin transaction, cryptographic techniques validate it, preventing issues such as double-spending, where the same bitcoin could be spent more than once. Transactions are communicated as electronic messages across the network, containing all necessary instructions and metadata. A single transaction can include multiple inputs and outputs, allowing funds to be sent to several recipients or returned as change. New transactions are created and added to the network, where they are validated by miners before being included in the blockchain. This validation process is fundamental to the security of the bitcoin system. Because bitcoin operates on a decentralized network, users can transact directly without intermediaries like banks or payment processors, making it a unique and innovative payment system.
At the heart of bitcoin’s success lies its underlying technology—blockchain technology. The blockchain serves as a tamper-proof, distributed database that is used to record transactions in a chronological order, enabling the entire network to agree on the state of ownership and transaction history. Ownership verification is achieved through cryptographic proof and consensus among nodes, ensuring that users genuinely possess the assets they spend.
Bitcoin Blockchain
The bitcoin blockchain is a distributed database that stores all bitcoin transactions in a secure and encrypted manner. This database is maintained by a global network of nodes, each storing a complete copy of the blockchain. This redundancy ensures that the system is transparent and resistant to tampering or fraud.
The blockchain is composed of sequential blocks, where each block contains data on recent transactions, references to previous blocks, bitcoin addresses, and execution code. These blocks are cryptographically linked, forming an immutable chain that provides a permanent record of all bitcoin activity. Each transaction block on the Bitcoin blockchain also contains a hash of the previous block, ensuring the integrity and continuity of the chain. This structure allows the network to verify the validity of transactions and maintain consistency across the entire blockchain network.
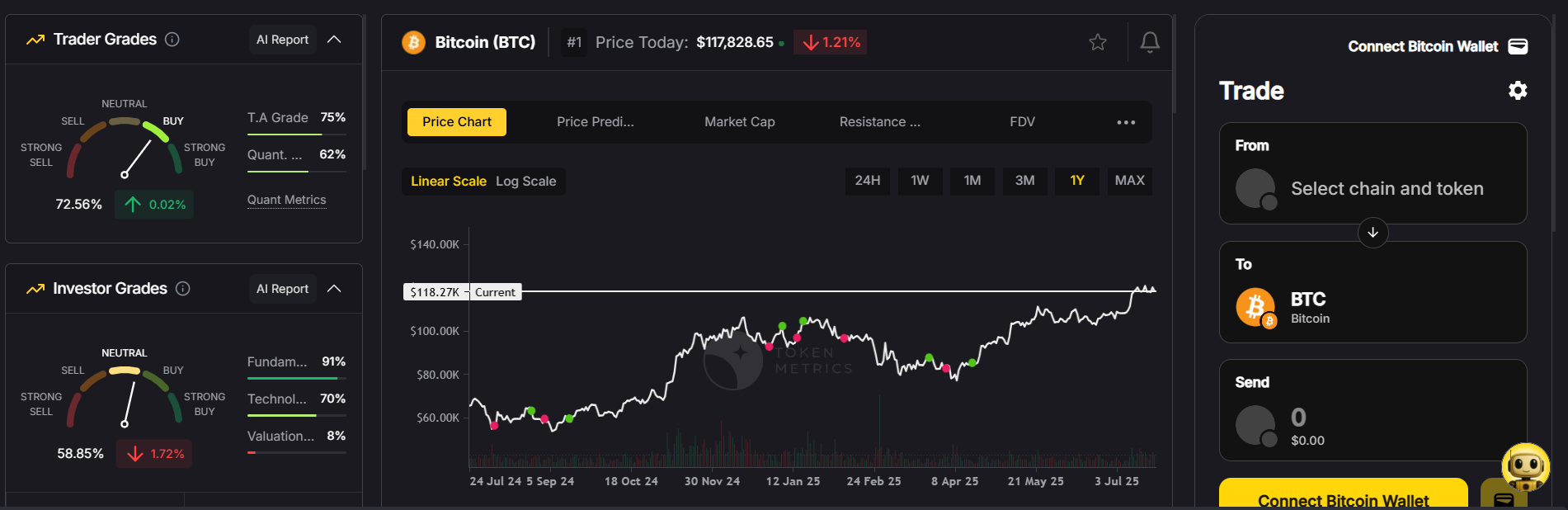
Understanding how blocks function is crucial to appreciating the security and efficiency of bitcoin transactions. Each new block added to the chain confirms a batch of recent transactions, ensuring that bitcoins are not double-spent and that ownership is accurately tracked. A miners group collaborates to validate and add these new blocks by grouping transactions and competing to solve cryptographic puzzles, which secures the network. As subsequent blocks are added to the blockchain, the security and immutability of previous transactions are further reinforced, making it increasingly difficult to alter any information in earlier blocks.
Mining and New Bitcoins
Bitcoin mining plays a pivotal role in both validating transactions and creating new bitcoins. Specialized software and hardware, such as Application-Specific Integrated Circuits (ASICs), perform complex computations to solve cryptographic puzzles through a process called mining. This requires vast amounts of computing power and energy consumption.
During mining, miners process block data through a hashing algorithm that produces fixed-length hexadecimal outputs known as hashes. By adjusting a value called a nonce, miners attempt to find a hash below a specific network target. Each block must contain a proof of work (PoW) to be accepted, ensuring that the computational effort required to mine a block contributes to the security and integrity of the blockchain. The first miner to solve this cryptographic puzzle earns the right to add a new block to the blockchain and receives a block reward in the form of newly created bitcoins.
To increase their chances of earning rewards and reduce the variance in payouts, miners often join a mining pool, where miners join together to combine their resources. By pooling their computational power, miners can secure a more stable income, but this has also raised concerns about centralization if a few mining pools control a majority of the network's hashing power.
To maintain a consistent block creation rate of approximately every 10 minutes, the mining difficulty adjusts every 2,016 blocks based on the total computing power of the network. This dynamic ensures the steady issuance of new bitcoins and the ongoing security of the blockchain network.
Mining is essential not only for the creation of new bitcoins but also for validating and securing all bitcoin transactions, making it a cornerstone of the entire bitcoin system. However, mining consumes vast amounts of electricity, which has attracted criticism for its environmental impact. This energy-intensive process has sparked debates about the sustainability of bitcoin and its broader implications for the environment.
Bitcoin Transactions
Bitcoin transactions involve sending digital currency from one user to another through the bitcoin network. To initiate a transaction, a user enters the recipient’s bitcoin address, signs the transaction with their private key, and includes a transaction fee to incentivize miners to prioritize their transaction.
Once submitted, transactions enter a mempool—a waiting area for unconfirmed transactions—where miners select which transactions to include in the next block. Transactions with higher fees are typically prioritized, especially during periods of high network demand. This fee mechanism ensures the efficient processing of valid transactions.
Blocks are added to the blockchain roughly every 10 minutes, confirming the transactions contained within them. All confirmed transactions become part of the public blockchain, providing security and transparency. However, rising demand for bitcoin transactions has led to increased transaction fees, making it more costly to send bitcoins during peak times.
Despite these fees, bitcoin transactions remain a secure and transparent method of transferring value, offering an alternative to traditional cash transactions and payment systems. Like a cash transaction, bitcoin enables direct peer-to-peer exchanges without the need for a central authority, allowing users to transfer value directly between parties.
Bitcoin Wallet
A bitcoin wallet, also known as a digital wallet, is a digital tool that allows users to store, manage, and spend their bitcoins securely. Unlike physical cash stored in a wallet, bitcoin ownership is recorded on the blockchain, with digital wallets providing access through cryptographic keys rather than physical currency.
Bitcoin wallets function similarly to banking apps, enabling users to view their balances and manage their crypto holdings conveniently. These digital wallets use private keys—secret codes that authorize spending coins—and bitcoin addresses, which serve as public identifiers for receiving funds.
Keeping private keys safe is crucial, as losing them means losing access to the bitcoins they control. There are various types of wallets available, including software wallets installed on computers or a mobile phone for convenience, hardware wallets that store keys offline for enhanced security, and paper wallets that print keys on physical media for cold storage. Paper wallets, as a form of cold storage, are particularly valued for their simplicity and security, as they keep private keys completely offline.
By using a digital wallet, users can securely participate in the bitcoin network, sending and receiving bitcoins with confidence.
The Bitcoin System
The bitcoin system is built on a decentralized network that empowers users to conduct peer-to-peer bitcoin transactions without relying on intermediaries like banks or payment processors. At the core of this system is the bitcoin blockchain—a transparent, public ledger that records every bitcoin transaction, ensuring the integrity and security of the entire network.
Bitcoin mining is a fundamental process within the bitcoin system. Through bitcoin mining, miners use powerful computers to solve complex mathematical puzzles, competing to add a new block of transactions to the blockchain. The first miner to solve the puzzle is rewarded with new bitcoins, introducing new digital currency into circulation and incentivizing the ongoing validation of transactions.
The bitcoin network is maintained by a distributed network of nodes, each holding a complete copy of the blockchain. These nodes work together to validate transactions, ensuring that only legitimate and valid transactions are added to the blockchain. This decentralized approach means that bitcoin operates without a central authority, making the system resistant to censorship and single points of failure.
By combining the transparency of the bitcoin blockchain, the security of bitcoin mining, and the collaborative efforts of the network’s nodes, the bitcoin system offers a secure, reliable, and censorship-resistant platform for digital currency transactions. This innovative approach has established bitcoin as a leading example of how blockchain technology can transform the way value is transferred and recorded in the digital age.
Cryptocurrency Investing
Investing in bitcoin and other cryptocurrencies involves purchasing digital assets with the hope that their market price will appreciate over time. Cryptocurrency investing can be highly volatile and carries significant risk, but it also offers the potential for substantial returns. Bitcoin is often viewed as a store of value and a hedge against inflation by investors, further enhancing its appeal as an alternative investment option. Bitcoin's supply is limited by its code, which is designed to create scarcity and potentially drive value over time.
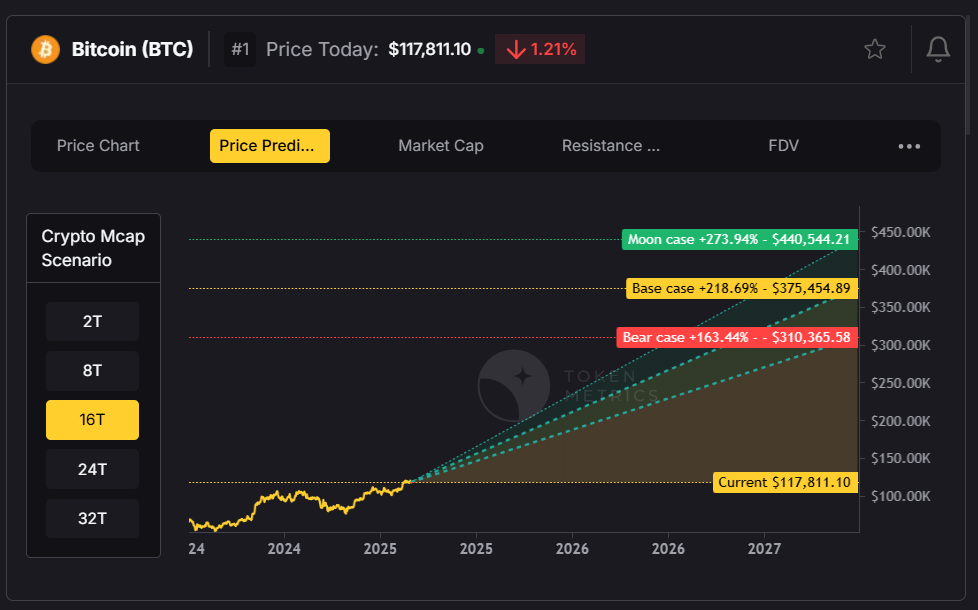
Before investing, it’s essential to conduct thorough research and understand the dynamics of the cryptocurrency market. Factors such as bitcoin’s price volatility, regulatory developments, and technological innovations can greatly affect investment outcomes. Bitcoin's price can fluctuate dramatically, impacting the amount of bitcoin received for a fixed dollar investment and influencing potential returns.
Investors can choose from various strategies, including buying and holding bitcoin as a long-term store of value, trading on cryptocurrency exchanges, or using investment products like exchange-traded funds (ETFs) that provide exposure to crypto assets.
Given the risks, cryptocurrency investing is not suitable for everyone. Prospective investors should carefully assess their financial goals and risk tolerance before allocating funds to bitcoin or other digital currencies.
Digital Currencies
Digital currencies like bitcoin represent a groundbreaking shift in how value is stored and transferred. As virtual currencies, they offer a secure, transparent, and decentralized alternative to traditional physical currency and national currencies. Digital currencies can also be exchanged for other forms of money, such as cash or electronic deposits, highlighting their compatibility with existing financial systems.
Their decentralized nature removes the need for central banks or financial institutions to authorize transactions, which can reduce costs and increase accessibility. Many businesses and individuals are increasingly adopting digital currencies for payments, recognizing their potential to disrupt established financial systems.
Moreover, digital currencies can promote financial inclusion by providing access to financial services for populations underserved by traditional banking. As adoption grows, digital currencies are poised to become an integral part of the global economy.
Central Bank and Regulation
The rise of digital currencies like bitcoin presents challenges and opportunities for central banks and regulatory bodies worldwide. Many governments are still navigating how to regulate these new forms of money, often taking a cautious or wait-and-see approach. Regulators are particularly concerned about the potential use of bitcoin and other digital currencies in criminal activities such as money laundering or illicit transactions, due to the anonymity these currencies can provide.
The absence of clear regulation can create uncertainty for investors and businesses, complicating compliance and operational decisions. However, some countries have taken proactive steps, with a few even adopting bitcoin as legal tender, recognizing its potential benefits. As of November 2021, Bitcoin is only legal tender in El Salvador, a move that has sparked both interest and controversy on the global stage.
The regulatory environment surrounding digital currencies is dynamic and continuously evolving, with agencies such as the Securities and Exchange Commission (SEC) in the United States closely monitoring developments. Staying informed about regulatory changes is essential for anyone involved in bitcoin trading, cryptocurrency investing, or using digital currencies in commerce.
Cryptocurrency Work and Ecosystem
The cryptocurrency ecosystem is a complex and rapidly evolving network comprising miners, investors, businesses, developers, and users. All these participants contribute to maintaining the decentralized network, validating transactions, and fostering innovation.
This ecosystem relies on the process called mining to secure the blockchain network and create new bitcoins. Meanwhile, cryptocurrency exchanges facilitate the buying, selling, and trading of crypto assets, helping users manage their crypto holdings.
As the ecosystem grows, it offers the potential for increased financial inclusion and novel financial services. However, it also faces challenges such as regulatory uncertainty, market volatility, and security risks that participants must navigate carefully. The environmental impact of bitcoin mining has also led to regulatory scrutiny and restrictions in various jurisdictions, adding another layer of complexity to the cryptocurrency landscape.
Best Practices
When engaging with bitcoin and other digital currencies, following best practices is crucial to safeguard investments and ensure smooth transactions. First and foremost, conducting thorough research and understanding how bitcoin operates is essential before investing or trading.
Choosing reputable bitcoin wallets and cryptocurrency exchanges is vital for security and ease of use. Users should fund accounts securely and protect their private keys diligently to prevent theft or loss.
Diversifying investments across different crypto assets and traditional investments can help manage risk. Additionally, never invest more than one can afford to lose, as the cryptocurrency market is known for its volatility.
Staying informed about market trends, regulatory developments, and technological advancements will help users and investors make sound decisions and adapt to the fast-changing crypto landscape.
Future of Bitcoin
The future of bitcoin and other digital currencies remains uncertain but promising. As blockchain technology advances, we can anticipate improvements in scalability, security, and user experience that will enhance bitcoin's utility as a payment system and store of value. The market capitalization of Bitcoin reached $1 trillion for the first time in February 2021, highlighting its growing significance in the global financial landscape.
Adoption is expected to increase, with more businesses and individuals embracing bitcoin for transactions and as an alternative investment. Regulatory frameworks will likely become clearer, providing greater stability and confidence for participants.
Despite these positive trends, challenges such as market volatility, security concerns, and regulatory hurdles will persist. Nonetheless, bitcoin’s underlying technology and decentralized nature position it to play a significant role in the future of finance and digital assets.
Understanding how bitcoin works provides valuable insight into this innovative digital currency and its potential impact on the global financial system. From the bitcoin blockchain and mining to wallets and investing, bitcoin offers a unique alternative to traditional fiat currencies and physical cash, reshaping how value is transferred and stored in the digital age.
Create Your Free Token Metrics Account

.png)




%201.svg)
%201.svg)


%201.svg)








.svg)




.png)