
Crypto Trading: Understanding Bitcoin Season Index and BTC Market Dominance with Token Metrics AI

The cryptocurrency market is known for its cyclical patterns, where Bitcoin and alternative cryptocurrencies, commonly called altcoins, take turns leading market performance. Cryptocurrency is a digital or virtual currency that operates on distributed ledger technology called a blockchain and uses cryptography for security. Unlike traditional currencies, cryptocurrencies are decentralized and not backed by any central bank, which sets them apart from government-issued money. Blockchain technology is the foundational element that underpins cryptocurrency, ensuring transaction transparency and security. For traders and investors engaged in crypto trading, understanding when Bitcoin dominates the market is crucial for effective portfolio management and maximizing profits. The Bitcoin Season Index, derived from Bitcoin dominance metrics, serves as a fundamental indicator to identify periods when the flagship cryptocurrency outperforms the broader cryptocurrency market. This insight enables traders to time their investments optimally and navigate the notoriously volatile crypto market with greater confidence.
What is the Bitcoin Season Index?
The Bitcoin Season Index is a specialized metric that measures Bitcoin’s market dominance and performance relative to other cryptocurrencies over specific time frames. Essentially, it quantifies Bitcoin’s share of the total cryptocurrency market capitalization. The value of cryptocurrencies is determined by market demand and supply. When 25% or fewer altcoins outperform Bitcoin, the market is said to be in a Bitcoin Season. This indicates that Bitcoin is maintaining its leadership position, attracting the majority of capital flows within the ecosystem.
The index is calculated by dividing Bitcoin’s market capitalization by the total market capitalization of the entire cryptocurrency market, then multiplying by 100 to get a percentage. More precisely, some methodologies consider the market cap of the top 125 coins to ensure comprehensive coverage. In this context, a coin refers to an individual cryptocurrency token, each with its own ticker symbol, that can be bought, sold, or traded on exchanges. When Bitcoin’s dominance remains elevated—typically above 60-65%—it signals that investors are preferentially allocating capital to Bitcoin rather than altcoins.
By tracking this metric, traders can better understand Bitcoin’s influence over the crypto market and recognize the inverse correlation between Bitcoin dominance and altcoin performance during different market phases. Many novice and experienced traders are drawn to cryptocurrency for its volatility and high reward potential. This understanding is invaluable for those looking to trade cryptocurrency effectively, as it helps predict price movements and market trends.
How Bitcoin Dominance Works as a Market Indicator
Bitcoin dominance is one of the most reliable indicators of market sentiment and capital allocation within the cryptocurrency ecosystem. It represents the percentage of total cryptocurrency market capitalization attributed to Bitcoin, reflecting its market share and influence.
The mechanics behind Bitcoin dominance are straightforward yet powerful. When Bitcoin’s price rises faster than the overall cryptocurrency market, its dominance increases. Conversely, when altcoins collectively outperform Bitcoin, its dominance decreases. This dynamic creates predictable patterns that experienced traders use to time their market entries and exits.
During Bitcoin seasons, several key dynamics typically emerge. Institutional investors often favor Bitcoin due to its perceived stability, regulatory acceptance, and status as the first cryptocurrency. Retail traders may also flock to Bitcoin during uncertain market conditions, viewing it as a safer store of value compared to the more volatile altcoins. Additionally, Bitcoin’s established liquidity and widespread support across cryptocurrency exchanges make it the preferred choice during risk-off periods. Trading cryptocurrency carries risk, and it is important to only trade what you can afford to lose. Trading cryptocurrencies is generally suitable for individuals with a high risk tolerance.
Understanding these dynamics allows traders to recognize when to increase Bitcoin exposure or diversify into altcoins, depending on prevailing market conditions and their individual risk tolerance.
Current Market Status: Bitcoin's 2025 Performance
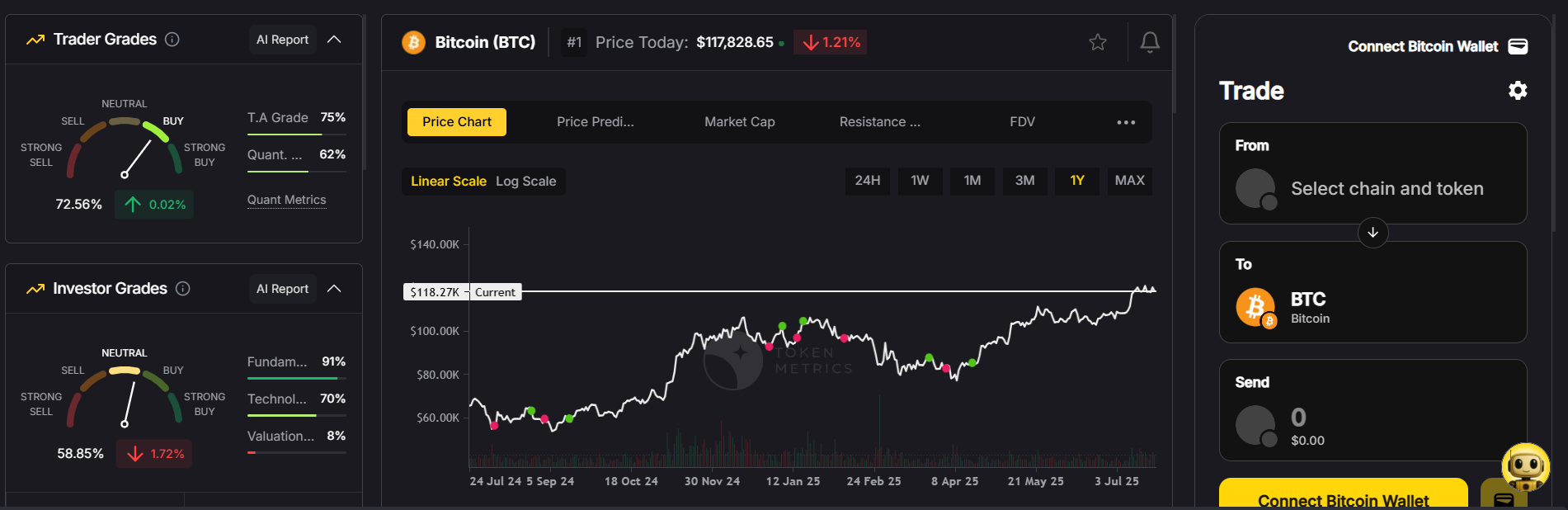
As of mid-2025, Bitcoin has demonstrated exceptional performance, exemplifying a strong Bitcoin season. Year-to-date, Bitcoin is up approximately 10%, outperforming nearly all major altcoins except XRP, which has gained over 12%. Meanwhile, Ethereum has declined by 30%, and altcoins such as LINK, DOGE, AVAX, and SHIB have all dropped more than 20%.
Bitcoin dominance (BTC.D) currently stands at about 64%, a high level that historically signals Bitcoin season conditions. A decline below 60% often marks the beginning of altcoin seasons, where capital shifts toward alternative cryptocurrencies. The sustained high dominance level in 2025 suggests that Bitcoin continues to lead the cryptocurrency market.
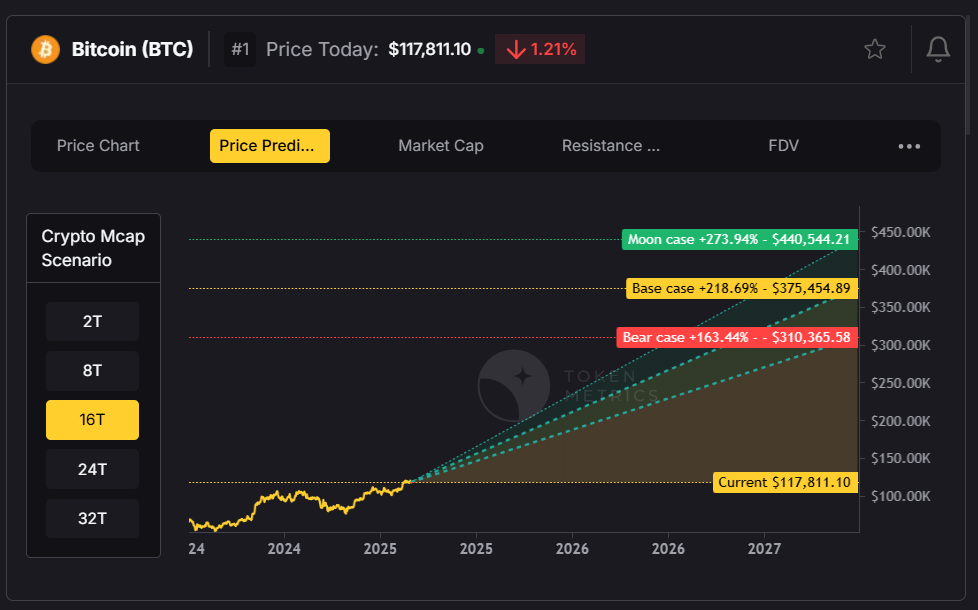
Unlike fiat currencies, which are issued and managed by a central bank, Bitcoin operates independently without central bank involvement. Analysts from institutions like Standard Chartered predict Bitcoin could reach $200,000 by the end of 2025, fueled by robust inflows into Bitcoin ETFs and favorable political developments, including the election of a pro-crypto US president. These factors contribute to Bitcoin’s sustained outperformance and elevated dominance.
Recent market indicators, such as the Altcoin Season Index dropping to 41, further confirm a dominant Bitcoin season within the cryptocurrency market. This dynamic underscores Bitcoin’s ability to reclaim market leadership when conditions favor the flagship digital currency.
Historical Context and Market Patterns
Understanding historical Bitcoin seasons provides valuable context for interpreting current market conditions and anticipating future trends. Bitcoin dominance has exhibited clear cyclical patterns throughout cryptocurrency market history, with periods of expansion and contraction correlating with broader market trends and investor sentiment. High volatility creates profit opportunities for day traders, making it a key factor in cryptocurrency trading strategies. Monitoring value changes in Bitcoin and altcoins helps traders identify market trends and optimal entry or exit points.
For example, during the 2017-2018 cycle, Bitcoin dominance fell from over 80% to below 40% as the ICO boom drove massive capital flows into altcoins. However, during the subsequent bear market, Bitcoin dominance recovered significantly as investors sought safety in the most established cryptocurrency. A similar pattern occurred during the 2020-2021 bull market, where Bitcoin initially led before altcoins took over in the later stages.
The 2022 bear market saw Bitcoin dominance rise again as altcoins suffered disproportionate losses. These historical precedents demonstrate that Bitcoin seasons often coincide with either early bull market phases or extended periods of market uncertainty and decline. Bitcoin’s perceived stability and growing institutional adoption make it the preferred choice during such conditions.
The current market dynamics in 2025 reflect these historical patterns. Strong institutional adoption through Bitcoin ETFs, combined with favorable regulatory developments, have created conditions that favor Bitcoin accumulation over altcoin speculation. This environment naturally leads to increased Bitcoin dominance and prolonged Bitcoin season conditions.
The Science Behind Bitcoin Dominance Calculations
Calculating Bitcoin dominance involves sophisticated methodologies to ensure accuracy and relevance for trading decisions. While the basic formula divides Bitcoin’s market capitalization by the total cryptocurrency market capitalization, selecting which assets to include in the denominator is crucial.
Most platforms exclude stablecoins, wrapped tokens, and derivative assets from total market cap calculations to provide a more accurate representation of genuine price appreciation dynamics. This approach ensures that Bitcoin dominance reflects actual capital allocation preferences rather than artificial inflation from pegged assets.
Different time frames offer varying insights into market trends. Daily dominance readings can be volatile and influenced by short-term market movements, whereas weekly and monthly averages provide more stable trend indicators. The 90-day rolling analysis used in Bitcoin Season Index calculations helps filter out noise while maintaining responsiveness to real market shifts.
Advanced platforms like Token Metrics incorporate these dominance metrics into comprehensive market analysis frameworks. By combining Bitcoin dominance data with technical indicators, on-chain metrics, and sentiment analysis, traders gain a nuanced understanding of market conditions and timing opportunities, enhancing their ability to trade crypto effectively. Blockchain technology records all transactions on a shared ledger, and transaction data is a key component of on-chain metrics, providing valuable insights for dominance calculations and broader market analysis. Market analysis and trend observation are critical components of successful day trading, further emphasizing the importance of these tools.
Strategic Trading Applications During Bitcoin Season
Bitcoin seasons present unique opportunities and challenges for cryptocurrency traders employing various strategies and time horizons. Properly positioning portfolios during these periods can significantly impact returns and risk management.
Momentum traders benefit from Bitcoin seasons by adopting a clear directional bias toward Bitcoin. During established Bitcoin seasons, traders often reduce altcoin exposure and increase Bitcoin allocation to capitalize on continued outperformance. This strategy is particularly effective when Bitcoin dominance is trending upward with strong volume confirmation.
Contrarian traders may view extreme Bitcoin dominance levels as accumulation opportunities for quality altcoins. When Bitcoin dominance reaches high levels, investing in fundamentally strong altcoins can offer asymmetric risk-reward profiles for patient investors. However, timing these contrarian positions requires careful analysis of multiple market indicators and a good understanding of price trends.
Portfolio rebalancing during Bitcoin seasons demands a dynamic approach that accounts for shifting market conditions. Traders must be prepared to act quickly when opportunities arise during Bitcoin seasons. AI-powered platforms like Token Metrics excel in this area by providing real-time portfolio optimization recommendations based on current market dynamics and individual risk tolerance.
Risk management is especially important during Bitcoin seasons, as altcoin volatility often increases during periods of underperformance. Proper position sizing, use of stop-loss orders, and diversification strategies help protect capital while maintaining exposure to potential trend reversals.
Token Metrics: Revolutionizing Bitcoin Season Analysis
The advent of artificial intelligence and advanced analytics platforms has transformed cryptocurrency trading, with Token Metrics leading this technological revolution. The platform’s sophisticated approach to Bitcoin dominance analysis and market cycle identification provides traders with unprecedented insights into optimal positioning strategies. In addition, Token Metrics gives users access to advanced analytics and real-time market intelligence, making it easier to enter and navigate financial markets.
Token Metrics’ AI-driven methodology integrates Bitcoin dominance data with over 80 different metrics per cryptocurrency, creating a multidimensional view of market conditions that far surpasses traditional analysis. This comprehensive approach enables traders to dive deeper into market trends, recognize patterns, and predict price movements more accurately.
The platform’s real-time analysis capabilities are particularly valuable during Bitcoin season transitions. Token Metrics’ AI systems can identify subtle shifts in market dynamics that may signal the end of Bitcoin seasons and the beginning of altcoin outperformance periods. Early detection of these inflection points provides significant advantages for active traders and portfolio managers.
Beyond dominance analysis, Token Metrics incorporates fundamental research, technical analysis, and sentiment metrics, ensuring that Bitcoin season insights are contextualized within broader market trends and individual cryptocurrency prospects. This holistic approach empowers traders to make informed decisions on when to buy and sell crypto assets.
Earning Rewards During Bitcoin Seasons
Earning rewards during Bitcoin seasons is a compelling prospect for both traders and investors navigating the dynamic cryptocurrency market. These periods, marked by heightened volatility and pronounced price movements, present unique opportunities to trade cryptocurrencies for substantial profits. To capitalize on these market trends, it’s essential to develop a good understanding of technical analysis and risk management, enabling informed decisions when buying and selling digital assets.
Traders can employ a variety of strategies to earn rewards during Bitcoin seasons. Day trading, for example, involves executing multiple trades within a single day to take advantage of short-term price fluctuations in the crypto market. Swing trading and position trading, on the other hand, focus on capturing larger price movements over days or weeks, allowing traders to benefit from broader market trends. Regardless of the approach, recognizing patterns and predicting price movements are crucial skills for maximizing profits.
Selecting a reliable crypto platform is equally important. Platforms that offer low fees and high liquidity empower traders to execute trades efficiently, minimizing costs and slippage. This efficiency is vital when trading popular coins like Bitcoin and other cryptocurrencies, as it allows for quick responses to market changes and optimal entry and exit points.
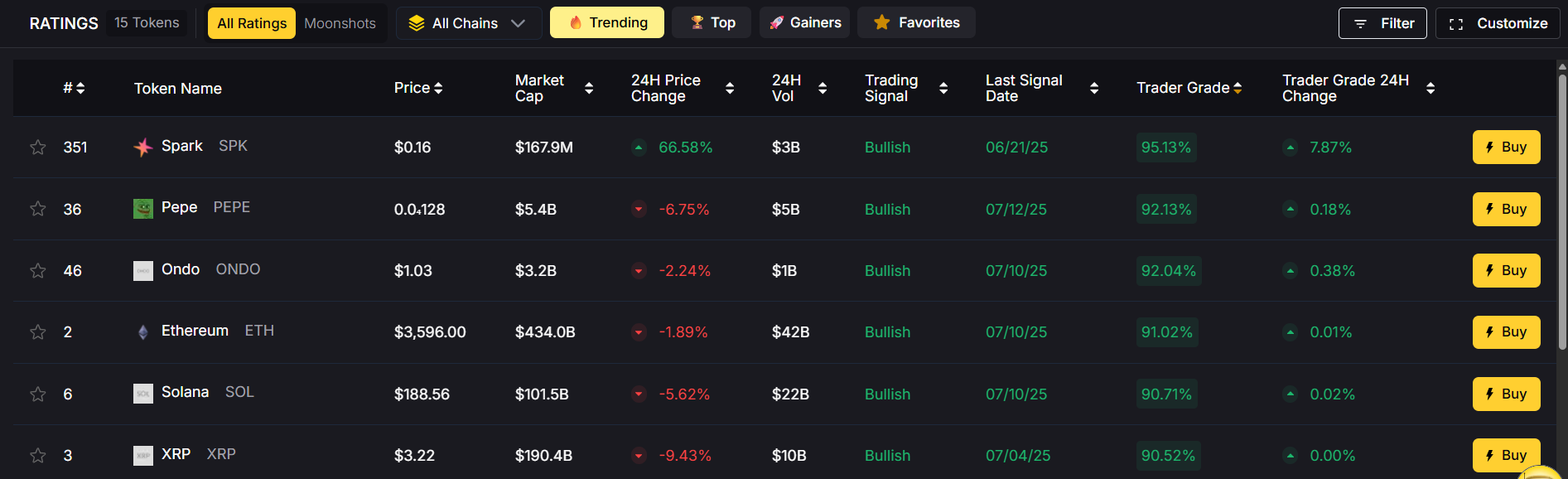
By staying attuned to market trends, leveraging technical analysis, and utilizing platforms with robust trading features, traders and investors can position themselves to earn rewards during Bitcoin seasons. The ability to adapt strategies to evolving market conditions and manage risks effectively is key to sustained success in the cryptocurrency market.
High Liquidity and Its Impact on Bitcoin Season Dynamics
High liquidity is a cornerstone of effective trading during Bitcoin seasons, profoundly shaping the dynamics of the cryptocurrency market. In essence, liquidity refers to how easily traders can buy and sell cryptocurrencies without causing significant price changes. When a crypto asset like Bitcoin enjoys high liquidity, it means there are ample buyers and sellers, resulting in a stable and efficient market environment.
This abundance of trading activity is especially beneficial during periods of intense price movements, as it allows traders to enter and exit positions swiftly and at predictable prices. High liquidity reduces the risk of slippage—the difference between the expected price of a trade and the actual executed price—ensuring that traders can execute their strategies with precision. This is particularly important for those relying on technical analysis, as stable markets provide more reliable signals and patterns to inform trading decisions.
Moreover, high liquidity supports the ability to earn rewards by enabling traders to capitalize on rapid market shifts without being hindered by large spreads or limited order book depth. It also enhances the overall trading experience, making it easier to manage risk and maximize profits, whether trading Bitcoin or other cryptocurrencies.
Understanding the impact of high liquidity on Bitcoin season dynamics empowers traders to make more informed decisions in the crypto market. By prioritizing assets and platforms that offer high liquidity, traders can navigate volatile periods with greater confidence, efficiently buy and sell assets, and optimize their trading outcomes.
Risk Management During Bitcoin Seasons
Effective risk management during Bitcoin seasons involves understanding both the opportunities and limitations inherent in these market conditions. While Bitcoin seasons can provide a clear directional bias, they also introduce specific risks that traders must address. Trading during these periods can be particularly risky due to heightened volatility and rapid market shifts. Traders should set clear boundaries for acceptable losses to ensure long-term success in navigating these volatile periods.
Concentration risk is a primary concern during extended Bitcoin seasons. Traders heavily weighted in Bitcoin may experience strong short-term gains but face significant downside if market conditions shift abruptly. Balancing concentration with diversification is key to managing this risk.
Timing risk also presents challenges. Cryptocurrency markets are cyclical, and Bitcoin seasons eventually end, often with sudden and dramatic reversals. Developing systems to recognize potential inflection points and adjust positions accordingly is critical for preserving gains.
Liquidity considerations become important during Bitcoin season transitions. As market conditions change, altcoin liquidity may decrease, making it more difficult and costly to adjust positions. Planning exit strategies during periods of high liquidity helps mitigate this risk.
Token Metrics addresses these challenges by providing real-time risk assessment tools and portfolio management features. These capabilities help traders maintain an appropriate balance between capitalizing on Bitcoin season opportunities and managing associated risks effectively.
Technology Integration and AI-Powered Analysis
The integration of artificial intelligence into Bitcoin season analysis marks a fundamental shift in how traders approach the cryptocurrency market. While traditional methods remain valuable, AI systems offer unmatched speed and accuracy in processing vast data sets necessary for optimal decision-making.
Token Metrics exemplifies this evolution by combining traditional dominance analysis with advanced machine learning algorithms. Its AI continuously analyzes market data, identifying subtle patterns and correlations that human analysts might overlook or process too slowly to capitalize on.
Machine learning models can detect early changes in Bitcoin dominance trends that precede major market shifts. These early warning signals provide traders with crucial timing advantages, enhancing both returns and risk management.
Additionally, Token Metrics leverages natural language processing to analyze news sentiment, social media trends, and regulatory developments that influence Bitcoin dominance cycles. This comprehensive approach ensures that Bitcoin season analysis incorporates all relevant market factors, including those affecting price trends and volatility.
Future Outlook: Bitcoin Seasons in an Evolving Market
The cryptocurrency market is rapidly evolving, driven by institutional adoption, regulatory clarity, and technological innovation. These factors will likely influence the dynamics of Bitcoin seasons and dominance cycles in the coming years. Unlike traditional markets, which operate within limited hours, cryptocurrency trading is available 24/7, offering continuous trading opportunities and flexibility for investors.
Institutional adoption through Bitcoin ETFs and corporate treasury allocations may lead to more stable and extended Bitcoin seasons. As traditional financial institutions increase their Bitcoin exposure, dominance patterns may become less volatile and more predictable, creating new trading opportunities and challenges.
Regulatory clarity in major markets could further strengthen Bitcoin’s position relative to altcoins, especially if regulations favor established cryptocurrencies over newer, less tested alternatives. This regulatory preference may extend Bitcoin seasons and elevate average dominance levels.
Technological advancements in the Bitcoin ecosystem, such as the growth of the Lightning Network and potential smart contract capabilities, could also influence dominance dynamics. Enhanced functionality may attract capital that might otherwise flow to altcoins with more advanced features.
Advanced Analytics and Market Intelligence
The sophistication of Bitcoin season analysis continues to improve through enhanced data collection, processing capabilities, and analytical methodologies. Platforms like Token Metrics leverage these advancements to provide traders with increasingly accurate and actionable market intelligence.
On-chain analysis has become particularly valuable for identifying Bitcoin seasons. Metrics such as exchange flows, wallet activity, and transaction patterns offer insights into institutional and retail behavior that complement traditional dominance calculations.
Cross-market correlation analysis helps identify global factors influencing Bitcoin seasons. Understanding relationships between Bitcoin dominance and traditional financial markets, commodities, and fiat currencies like the US dollar provides additional context for market dynamics. Fiat currency refers to government-issued money, such as the US dollar, which is not backed by a physical commodity and is commonly used as a benchmark in market analysis.
Sentiment analysis through social media monitoring, news analysis, and options market data offers leading indicators for potential Bitcoin season transitions. These alternative data sources often provide early signals before traditional metrics reflect changing market conditions.
Conclusion
The Bitcoin Season Index and associated dominance metrics are essential tools for navigating the complex and dynamic cryptocurrency market. Recognizing when Bitcoin is likely to outperform altcoins enables traders and investors to optimize portfolio allocation and timing decisions for maximum profits and effective risk management. Successful crypto trading also requires careful investment planning and a clear understanding of the potential to make or lose money in this volatile environment.
Success in cryptocurrency trading during Bitcoin seasons requires more than just understanding dominance metrics; it demands sophisticated analytical tools and real-time data processing capabilities. Token Metrics represents the pinnacle of AI-driven cryptocurrency analysis, offering traders the advanced insights necessary to capitalize on Bitcoin season opportunities while managing inherent risks.
By integrating artificial intelligence, machine learning, and comprehensive market analysis, traders gain unprecedented opportunities to recognize patterns, predict price movements, and execute trades on optimal entry points. As the crypto market matures, combining proven indicators like Bitcoin dominance with cutting-edge analytical platforms will be increasingly important for sustained trading success.
Whether you are a professional trader, institutional investor, or individual participant in the crypto market, leveraging Bitcoin season analysis supported by advanced tools like Token Metrics is crucial for navigating the rewarding yet volatile world of cryptocurrency trading. Embrace your crypto journey by leveraging advanced tools and analytics to improve your trading outcomes. The future belongs to those who can blend traditional market wisdom with modern technology to capture the significant opportunities Bitcoin seasons provide while effectively managing risk.

.svg)

Create Your Free Token Metrics Account

.png)




%201.svg)
%201.svg)


%201.svg)








.svg)




.png)