How Do I Know If a Coin Is a Rug Pull? Essential Detection Guide for 2025

The cryptocurrency market offers tremendous opportunities for investors, but it also harbors significant dangers. Among the most devastating threats are rug pulls—malicious scams where developers abandon projects after raising funds, leaving investors with worthless tokens. With rug pulls accounting for approximately 37% of all crypto scam revenue and costing investors nearly $3 billion annually, understanding how to identify these schemes before it's too late has become an essential skill for every crypto investor.
The term "rug pull" comes from the phrase "pulling the rug out from under someone." One moment, a project appears promising with skyrocketing prices and enthusiastic community support; the next, everything crashes as developers vanish with investors' funds. These scams particularly plague decentralized finance ecosystems where listing tokens requires minimal oversight and regulation.
This comprehensive guide provides you with the knowledge, tools, and strategies necessary to identify rug pull warning signs, protect your investments, and navigate the crypto space safely in 2025.
Understanding Rug Pulls: What They Are and How They Work
A rug pull is a cryptocurrency scam where developers create a project, attract investors through hype and promises of high returns, and then suddenly withdraw funds or abandon the venture, leaving participants with valueless tokens. These exit scams typically unfold through carefully orchestrated campaigns designed to maximize the amount stolen before the inevitable collapse.
The Anatomy of a Rug Pull
Rug pulls work by exploiting trust and hype within DeFi ecosystems, particularly on decentralized exchanges where listing tokens is easy and often unregulated. The typical progression follows a predictable pattern:
Project Launch: Developers launch a new cryptocurrency or DeFi project, often with flashy marketing and promises of high returns that attract initial attention. The project may include professional-looking websites, whitepapers, and social media presence designed to appear legitimate.
Hype Generation: Through social media, influencers, and crypto forums, the project gains attention and investors start buying tokens. Aggressive marketing tactics and Fear of Missing Out (FOMO) pressure drive rapid price increases as more investors pile in.
Liquidity Build-Up: As more investors buy, the liquidity pool grows, increasing the project's market value and creating the illusion of success. This phase may last days, weeks, or even months depending on the sophistication of the scam.
Sudden Exit: Once the pool reaches a significant amount, developers execute their exit strategy—draining liquidity, dumping massive token holdings, or simply abandoning the project entirely. The token's price crashes to zero, leaving investors unable to recover their funds.
Types of Rug Pulls
Understanding the different execution methods helps identify vulnerabilities before they're exploited.
Hard Rug Pulls: These involve malicious code embedded in smart contracts from the project's inception. Developers insert functions allowing them to withdraw liquidity at will, prevent other investors from selling, or mint unlimited tokens that dilute value. Hard rug pulls are premeditated scams designed specifically to steal investor funds and are generally illegal due to their fraudulent nature.
The infamous Squid Game Token exemplifies a hard rug pull. The token experienced tremendous growth initially, but the smart contract's code prevented non-founders from selling their tokens. SQUID briefly rose sharply before crashing to zero, with developers stealing millions.
Soft Rug Pulls: These occur when developers abandon projects after selling off significant token holdings, leaving the community behind. While not technically illegal, soft rug pulls are unethical and exploit investor trust. Sometimes these result from failed projects where teams lose interest, but malicious actors also use this method to avoid obvious legal consequences.
Liquidity Pulls: Developers remove liquidity from token pools, causing values to plummet due to lack of buyers and sellers. In DeFi, developers create liquidity pools pairing their new tokens with established cryptocurrencies like Ethereum or BNB. After attracting sufficient investment, they withdraw all liquidity, making it impossible for investors to sell holdings.
Dumping Schemes: Fraudsters rapidly sell off their cryptocurrency holdings, drastically reducing the value of other investors' tokens. This pump-and-dump manipulation deliberately inflates prices before coordinated selling crashes the market, generating profits for insiders while causing losses for everyone else.
Limited Sell Orders: Scammers restrict token sales for everyone except specific addresses, allowing themselves to sell at will while regular token holders cannot exit positions. This traps investors' funds, rendering their assets completely worthless.
Critical Red Flags: Warning Signs of Rug Pulls
Identifying rug pulls before losing money requires recognizing common warning signs that distinguish legitimate projects from scams.
Anonymous or Unverified Development Teams
If the project team lacks transparency or operates under pseudonyms, it represents a major warning sign. Legitimate projects typically have known founders with verifiable backgrounds, LinkedIn profiles, and established industry credentials. Anonymous teams eliminate accountability and make it impossible to pursue legal action after scams.
Look for team members with track records in the cryptocurrency space. Verify their involvement through independent sources rather than trusting project-provided information alone. Check LinkedIn profiles for employment history, connections, and endorsements from reputable industry figures.
Be wary of fake social media identities and accounts. Scammers create elaborate personas with purchased followers and engagement that appear legitimate superficially but lack genuine substance upon deeper investigation.
Missing or Inadequate Smart Contract Audits
Reputable cryptocurrency projects undergo third-party security audits by firms like CertiK, Quantstamp, or Trail of Bits. These audits examine smart contract code for vulnerabilities, malicious functions, and potential exploits. Projects lacking audits or refusing to share audit reports raise immediate red flags.
When audits exist, verify their authenticity. Visit the auditing firm's website directly rather than trusting links provided by projects. Read audit reports carefully—legitimate audits detail findings, vulnerabilities discovered, and whether issues were resolved before deployment.
Some scammers create fake audit reports or claim audits that never occurred. Always independently verify audit claims through the auditing company's official channels.
Unlocked Liquidity Pools
Liquidity locking is a security measure where project liquidity pool tokens are locked in smart contracts for set periods, preventing developers from withdrawing funds prematurely. This builds investor trust by reducing rug pull risk since creators cannot drain liquidity and collapse token values.
Unlocked liquidity allows project owners to withdraw assets at will, creating enormous theft opportunities. To check whether pools have locked liquidity, use tools like GeckoTerminal, which displays liquidity lock status for pools. Every pool on GeckoTerminal shows a GT Score panel indicating whether liquidity is locked—under "Liquidity Lock" for Solana pools and "Rugpull Risk" for Ethereum pools.
If liquidity remains unlocked or locks expire soon, developers maintain complete control over funds and can execute rug pulls at any moment.
Irregular Token Distribution and Whale Concentration
Checking token allocation on blockchain explorers like Etherscan or BscScan reveals who holds the most significant token amounts and how coins are allocated. If large percentages are held by small numbers of wallets, the token is more susceptible to price manipulation and dumping.
Healthy token distributions spread holdings across many addresses, preventing any single entity from controlling market dynamics. Projects where developers or early insiders hold 50% or more of supply create enormous risks—these holders can crash prices through coordinated selling.
Use block explorers to determine total token holder counts. If limited users hold a cryptocurrency, it indicates high centralization and manipulation vulnerability. Large, early transactions to unknown wallets also signal potential fund siphoning.
Unrealistic Returns and Yield Promises
If projects promise unusually high yields or guaranteed returns with little risk, they're likely Ponzi schemes or rug pulls. While DeFi can offer attractive returns, promises of triple-digit annual percentage yields (APYs) typically come with extreme risk or represent outright fraud.
Scammers lure victims with promises of 10% or higher daily returns, often through fake investment platforms. These astronomical figures defy economic reality—legitimate projects cannot sustain such yields long-term without underlying revenue or value creation.
If it sounds too good to be true, it almost certainly is. Approach extraordinary return promises with extreme skepticism and demand clear explanations of how yields are generated.
Vague or Missing Whitepapers
Whitepapers explain project goals, technology, tokenomics, and roadmaps. Legitimate projects provide detailed whitepapers with concrete technical information, clear use cases, and realistic timelines. Missing, vague, or plagiarized whitepapers indicate lack of substance and potentially fraudulent intent.
Read whitepapers critically. Look for specific technical details, not just marketing buzzwords. Verify claims about technology, partnerships, and team credentials through independent sources. Use plagiarism checkers to ensure whitepapers aren't copied from other projects.
Projects with unclear purposes or existing solely for speculation rather than solving real problems represent major red flags.
Excessive Marketing and FOMO Pressure
While marketing is essential for legitimate projects, excessive hype—especially from unofficial channels or unaffiliated influencers—can indicate scams. Aggressive marketing tactics creating artificial urgency and Fear of Missing Out pressure investors into decisions without proper research.
Scammers often leverage social media, paid influencers, and coordinated campaigns to generate buzz. They create false impressions of organic community growth through bot accounts, purchased engagement, and fake testimonials.
Legitimate projects build communities through value delivery and genuine interest, not manufactured hype. Be especially cautious of projects promising guaranteed returns, emphasizing "limited time offers," or discouraging due diligence.
Sudden Unexplained Price Spikes
Be careful about abrupt price movements in new coins, particularly those without liquidity locks. Fraudulent cryptocurrencies tend to see significant price surges before inevitable declines. These artificial pumps result from coordinated buying by scammers using initial funds to inflate values before dumping holdings.
Rapid price increases without clear fundamentals often indicate pump-and-dump schemes linked to potential rug pulls. Monitor price action relative to news, developments, and broader market trends. Spikes occurring without corresponding positive catalysts suggest manipulation.
Poor Smart Contract Code Quality
Poorly written smart contracts indicate inexperienced developers or intentional obfuscation designed to hide malicious functions. Review contract code on blockchain explorers for obvious issues like uncapped minting functions, hidden transfer restrictions, or excessive administrative privileges.
Tools like Token Sniffer automatically analyze smart contracts for common vulnerabilities and malicious patterns. These platforms provide safety scores helping identify dangerous projects before investment.
Low or Declining Trading Volume
Healthy projects maintain active trading with substantial volume across multiple exchanges. Low liquidity or irregular trading patterns signal unsustainable projects or potential rug pulls. Projects with minimal trading activity face enormous slippage risks and enable easy price manipulation.
Monitor trading volume trends. Declining volume despite ongoing development activity suggests loss of community interest or insider knowledge of impending problems.
Tools for Detecting Rug Pulls
Modern technology provides numerous tools helping identify rug pulls before they execute.
GeckoTerminal and DEX Scanners
GeckoTerminal includes an inbuilt rug pull checker examining liquidity locks, token distribution, and other critical metrics. Every pool displays a GT Score indicating overall safety based on multiple factors. Use this tool to quickly assess new projects before investing.
DEX scanners like DexTools and DexScreener provide real-time trading data, holder analytics, and liquidity information helping spot suspicious patterns.
Blockchain Explorers
Etherscan, BscScan, and similar explorers allow deep investigation of smart contracts, token holders, and transaction histories. Review contract code for malicious functions, examine top holder addresses, and trace fund movements to identify red flags.
Large transfers to exchanges from developer wallets often precede dumps. Monitor these movements to anticipate potential rug pulls.
Token Sniffer and Security Platforms
Token Sniffer provides AI-driven smart contract analysis across multiple blockchains, identifying scams through code examination, liquidity status evaluation, and holder distribution analysis. The platform generates safety scores from 0 to 100, with scores above 80 indicating high reliability and below 50 flagging potential risks.
Additional platforms like GoPlus Security detect malicious addresses and dApp vulnerabilities, providing comprehensive security assessments.
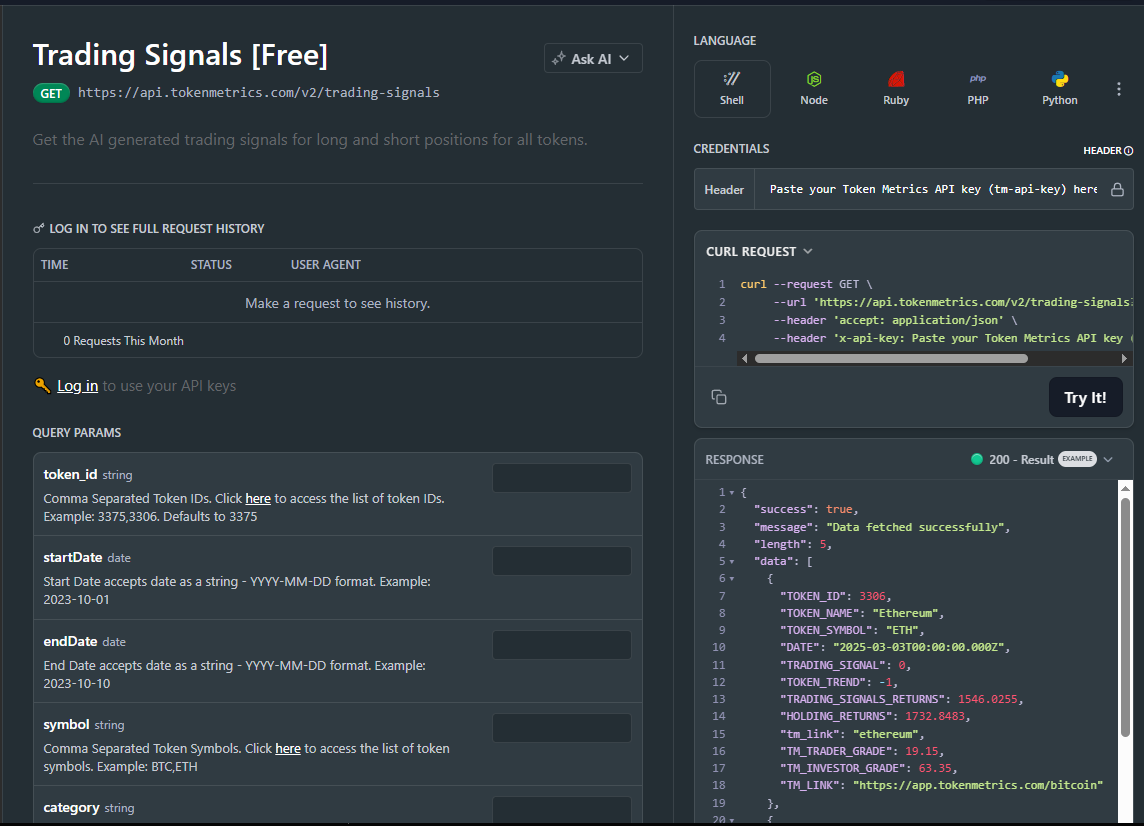
Leveraging Token Metrics for Rug Pull Protection
While automated tools provide valuable technical analysis, platforms like Token Metrics offer comprehensive, AI-powered intelligence that goes far beyond surface-level checks. Token Metrics has established itself as a leading crypto trading and analytics platform, providing sophisticated tools essential for protecting against rug pulls and identifying legitimate investment opportunities.
Comprehensive Project Evaluation: Token Metrics assigns each token both a Trader Grade for short-term potential and an Investor Grade for long-term viability. The Investor Grade specifically incorporates security factors including audit status, code quality, team credibility, and liquidity metrics—critical indicators for distinguishing legitimate projects from potential rug pulls.
This dual-rating system enables investors to quickly identify projects with robust foundations versus those exhibiting rug pull characteristics. By analyzing thousands of tokens continuously, Token Metrics identifies patterns and anomalies that individual investors might miss.
Real-Time Risk Monitoring: Token Metrics leverages machine learning and data-driven models to deliver powerful insights across the digital asset ecosystem. The platform monitors code changes, liquidity movements, trading patterns, and social sentiment in real-time, alerting users to suspicious activities that might precede rug pulls.
Customizable alerts via email, SMS, or messaging apps notify investors immediately when projects exhibit warning signs like liquidity removals, unusual whale activity, or sudden team changes. This proactive monitoring proves invaluable for protecting investments from emerging threats.
Team and Development Analysis: Token Metrics evaluates project teams through comprehensive background checks, GitHub activity monitoring, and historical performance analysis. The platform identifies anonymous teams, tracks development progress against roadmap promises, and flags projects with suspicious team behaviors.
By analyzing commit frequency, code quality, and developer engagement, Token Metrics distinguishes projects with genuine development activity from those creating illusions of progress while planning exits.
Social Sentiment and Community Analysis: Token Metrics uses natural language processing to interpret social media trends, community sentiment, and engagement patterns. The platform distinguishes organic community growth from artificial hype campaigns typical of rug pull schemes.
By monitoring discussion quality across Twitter, Reddit, Telegram, and Discord, Token Metrics identifies manufactured enthusiasm, bot activity, and coordinated shilling that often accompany scams.
Liquidity and Market Intelligence: Token Metrics analyzes liquidity depth, distribution, and lock status across exchanges and DeFi protocols. The platform tracks liquidity movements in real-time, alerting users when pools are drained or unlocked—immediate rug pull indicators.
The AI-driven analytics identify suspicious trading patterns including pump-and-dump schemes, wash trading, and coordinated manipulation that frequently precede or accompany rug pulls.
Historical Pattern Recognition: Token Metrics' machine learning models analyze historical rug pull data, identifying patterns and characteristics common across scams. This enables predictive analysis warning investors about projects exhibiting similar profiles before schemes execute.
By learning from past scams, Token Metrics continuously improves its detection capabilities, staying ahead of evolving tactics scammers employ.
Best Practices for Avoiding Rug Pulls
Combining technological tools with disciplined investment practices provides optimal protection against rug pulls.
Conduct Thorough Research (DYOR)
Do Your Own Research remains the golden rule. Investigate project backgrounds, teams, technology, and communities before investing. Don't rely solely on marketing materials or influencer endorsements—verify all claims independently.
Read whitepapers critically, check team credentials on LinkedIn, examine smart contract code (or hire auditors), and engage with communities to assess legitimacy. Look for red flags systematically rather than accepting projects at face value.
Start Small and Test Projects
When exploring new projects, invest only small amounts initially. This limits potential losses if projects prove fraudulent while allowing participation if they're legitimate. As projects demonstrate sustained legitimacy through delivered milestones and transparent operations, consider increasing positions gradually.
Never invest money you cannot afford to lose entirely. The crypto space remains highly volatile and experimental, with even legitimate projects sometimes failing.
Verify Liquidity Locks and Audit Reports
Always confirm liquidity is locked for reasonable periods through independent verification—never trust project claims alone. Use tools like GeckoTerminal to check lock status directly on-chain.
Similarly, verify audit reports through auditing firms' official websites. Read reports carefully to understand issues discovered and whether they were resolved. Multiple audits from reputable firms provide stronger assurance than single audits or audits from unknown companies.
Monitor Community Engagement Quality
Engage with project communities on Telegram, Discord, and Reddit. Observe whether teams answer questions honestly and address concerns transparently, or whether they censor criticism and avoid difficult topics.
Legitimate projects foster open dialogue and welcome scrutiny. Scammers typically create echo chambers filled with uncritical supporters while silencing dissenting voices.
Use Reputable Exchanges and Platforms
Stick to well-established exchanges that vet projects before listing. While centralized exchanges aren't immune to listing scams, they generally perform more due diligence than decentralized platforms allowing anyone to list tokens.
Platforms like Token Metrics help identify which projects listed on various exchanges exhibit legitimate characteristics versus rug pull warning signs.
Diversify Investments
Never concentrate holdings in single projects, especially new or unproven ones. Diversification across multiple assets, sectors, and risk levels protects portfolios from individual project failures including rug pulls.
Allocate larger percentages to established projects with proven track records while limiting exposure to higher-risk newer projects.
Stay Informed Through Trusted Sources
Follow trusted crypto news sources, security researchers, and platforms like Token Metrics that provide ongoing project monitoring. Scam alerts and community warnings often emerge before rug pulls execute, giving vigilant investors opportunities to exit positions.
Join crypto security communities on Twitter and Telegram where researchers share findings about suspicious projects in real-time.
What To Do If You've Been Rug Pulled
Despite best efforts, some investors still fall victim to rug pulls. Taking immediate action minimizes damage and potentially helps others avoid similar fates.
Report the Scam
Report fraudulent projects to community-driven platforms like Chainabuse that track scams. In the United States, file reports with the Securities and Exchange Commission (SEC) or Federal Trade Commission (FTC). International investors should contact equivalent financial authorities in their jurisdictions.
While recovering funds remains rare, every report adds to intelligence databases potentially preventing future victims and supporting regulatory actions against perpetrators.
Warn Others
Post detailed warnings on social media platforms like Twitter, relevant Reddit threads (r/CryptoCurrency), and Telegram/Discord channels. Be concise, factual, and transparent. Include token contract addresses, timelines of suspicious activity, and exactly what occurred.
Your warning could prevent others from losing money to the same scam.
Document Everything for Tax Purposes
If you've realized losses from rug pulls, document transactions thoroughly for potential tax deductions. Many jurisdictions allow capital loss claims for crypto scams, potentially offsetting other investment gains.
Consult tax professionals familiar with cryptocurrency to understand available options for recovering some losses through tax benefits.
Learn and Improve
Analyze what warning signs you missed and how you could have better protected yourself. Use the experience to strengthen your due diligence processes and avoid repeating mistakes.
Every investor makes errors—the key is learning from them to become more discerning over time.
Conclusion: Staying Safe in Crypto's Wild West
Rug pulls represent one of cryptocurrency's most persistent threats, costing investors billions annually through increasingly sophisticated schemes. However, armed with knowledge of warning signs, access to analytical tools, and disciplined investment practices, you can dramatically reduce your exposure to these scams.
Critical red flags including anonymous teams, missing audits, unlocked liquidity, irregular token distribution, unrealistic returns, and excessive marketing should immediately trigger additional scrutiny. When multiple red flags appear together, avoid projects entirely regardless of how promising they seem.
Leverage sophisticated analytics platforms like Token Metrics that provide AI-powered project evaluation, real-time risk monitoring, team analysis, and comprehensive market intelligence. These tools identify patterns and anomalies individual investors might miss, offering crucial protection against evolving scam tactics.
Remember that if something sounds too good to be true, it almost certainly is. The most effective defense against rug pulls combines technological tools with common sense, healthy skepticism, and disciplined research practices. Never let FOMO override rational analysis, and always invest only what you can afford to lose.
The cryptocurrency space offers tremendous opportunities for those who navigate it carefully. By understanding rug pull mechanics, recognizing warning signs early, using advanced analytical tools, and maintaining disciplined investment practices, you can participate in crypto's upside while minimizing exposure to its most devastating scams.
Stay vigilant, stay informed, and leverage platforms like Token Metrics to make data-driven decisions. Your financial security in the crypto space depends on your ability to distinguish legitimate innovations from sophisticated frauds—a skill that becomes increasingly valuable as the industry continues evolving in 2025 and beyond.
Create Your Free Token Metrics Account

.png)




%201.svg)
%201.svg)


%201.svg)










.svg)




.png)