Top Crypto Trading Platforms in 2025




Big news: We’re cranking up the heat on AI-driven crypto analytics with the launch of the Token Metrics API and our official SDK (Software Development Kit). This isn’t just an upgrade – it's a quantum leap, giving traders, hedge funds, developers, and institutions direct access to cutting-edge market intelligence, trading signals, and predictive analytics.
Crypto markets move fast, and having real-time, AI-powered insights can be the difference between catching the next big trend or getting left behind. Until now, traders and quants have been wrestling with scattered data, delayed reporting, and a lack of truly predictive analytics. Not anymore.
The Token Metrics API delivers 32+ high-performance endpoints packed with powerful AI-driven insights right into your lap, including:
Getting started with the Token Metrics API is simple:
At Token Metrics, we believe data should be decentralized, predictive, and actionable.
The Token Metrics API & SDK bring next-gen AI-powered crypto intelligence to anyone looking to trade smarter, build better, and stay ahead of the curve. With our official SDK, developers can plug these insights into their own trading bots, dashboards, and research tools – no need to reinvent the wheel.
NFT marketplaces are where collectors buy, sell, and mint digital assets across Ethereum, Bitcoin Ordinals, Solana, and gaming-focused L2s. If you’re researching the best NFT marketplaces to use right now, this guide ranks the leaders for liquidity, security, fees, and user experience—so you can move from research to purchase with confidence. The short answer: choose a regulated venue for fiat on-ramps and beginner safety, a pro venue for depth and tools, or a chain-specialist for the collections you care about. We cover cross-chain players (ETH, SOL, BTC), creator-centric platforms, and gaming ecosystems. Secondary searches like “NFT marketplace fees,” “Bitcoin Ordinals marketplace,” and “where to buy NFTs” are woven in naturally—without fluff.
We used official product pages, docs/help centers, security/fee pages and cross-checked directional volume trends with widely cited market datasets. We link only to official provider sites in this article. Last updated September 2025.
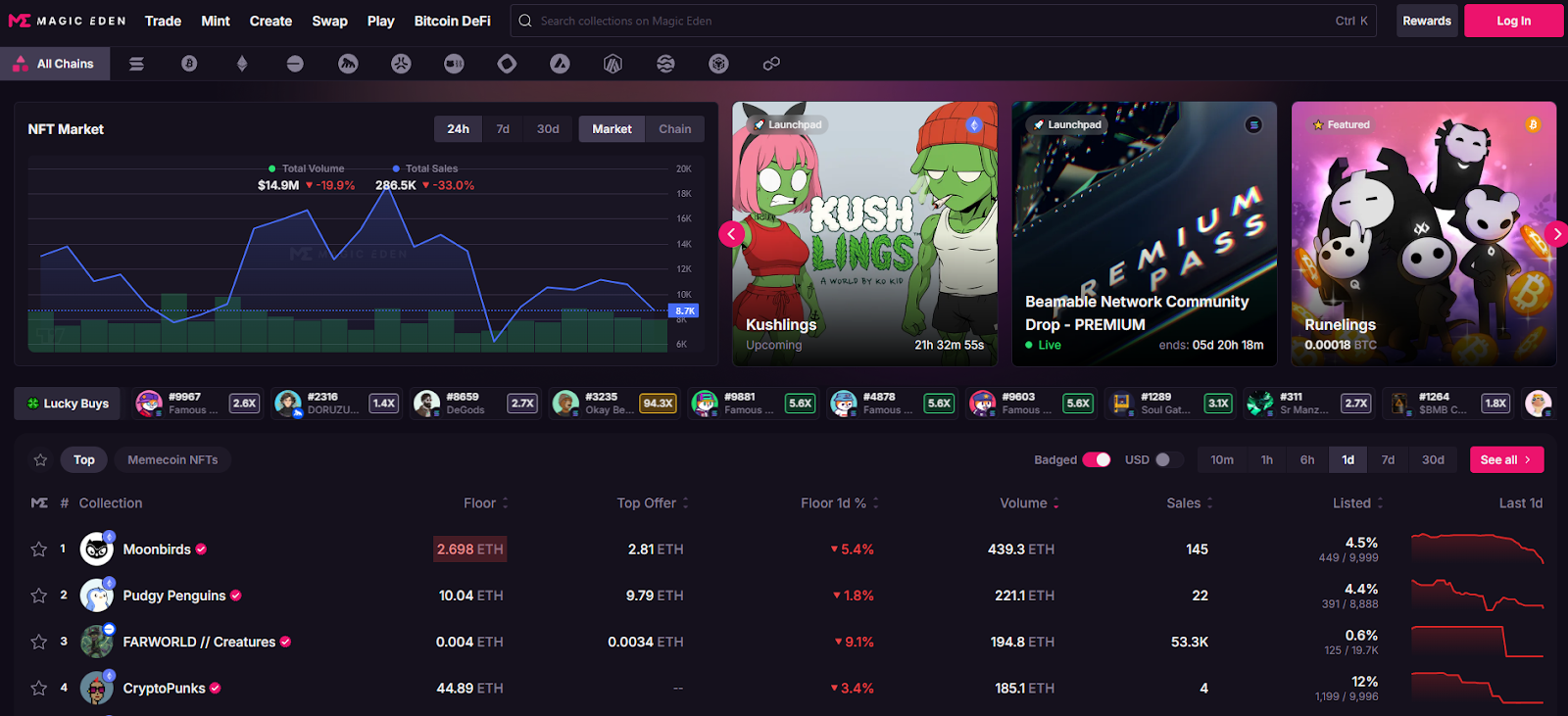
Why Use It: Magic Eden has evolved into a true cross-chain hub spanning Solana, Bitcoin Ordinals, Ethereum, Base and more, with robust discovery, analytics, and aggregation so you don’t miss listings. Fees are competitive and clearly documented, and Ordinals/SOL support is best-in-class for traders and creators. Magic Eden+1
Best For: Cross-chain collectors, Ordinals buyers, SOL natives, launchpad users.
Notable Features: Aggregated listings; trait-level offers; launchpad; cross-chain swap/bridge learning; pro charts/analytics. Magic Eden+1
Consider If: You want BTC/SOL liquidity with low friction; note differing fees per chain. help.magiceden.io
Alternatives: Blur (ETH pro), Tensor (SOL pro).
Regions: Global • Fees Notes: 2% on BTC/SOL; 0.5% on many EVM trades (creator royalties optional per metadata). help.magiceden.io

Why Use It: Blur is built for speed, depth, and sweeps. It aggregates multiple markets, offers advanced portfolio analytics, and historically charges 0% marketplace fees—popular with high-frequency traders. Rewards seasons have reinforced liquidity. blur.io+1
Best For: Power users, arbitrage/sweep traders, analytics-driven collectors.
Notable Features: Multi-market sweep; fast reveals/snipes; portfolio tools; rewards. blur.io
Consider If: You prioritize pro tools and incentives over hand-holding UX.
Alternatives: OpenSea (broad audience), Magic Eden (cross-chain).
Regions: Global • Fees Notes: 0% marketplace fee shown on site; royalties subject to collection rules. blur.io
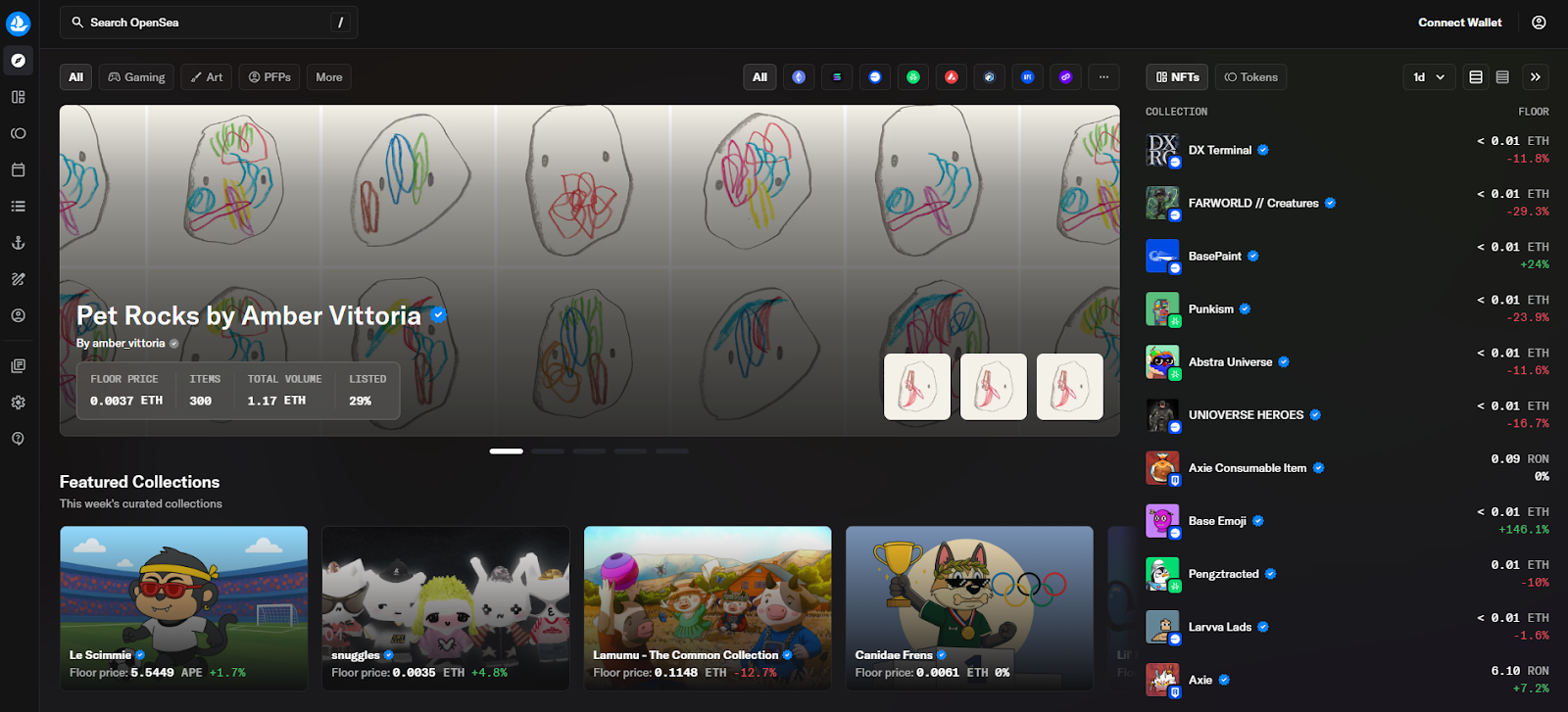
Why Use It: The OG multi-chain marketplace with onboarding guides, wide wallet support, and large catalog coverage. OpenSea’s “OS2” revamp and recent fee policy updates keep it relevant for mainstream collectors who want familiar UX plus broad discovery. OpenSea+1
Best For: Newcomers, multi-chain browsing, casual collectors.
Notable Features: Wide collection breadth; OpenSea Pro aggregator; flexible royalties; clear TOS around third-party/gas fees. OpenSea
Consider If: You want broadest brand recognition; be aware fees may change. Yahoo Finance
Alternatives: Blur (pro ETH), Rarible (community markets).
Regions: Global (note U.S. regulatory headlines under review). Reuters
Fees Notes: Reported trading fee currently ~1% as of mid-Sept 2025; creator earnings and gas are separate. Yahoo Finance+1
Why Use It: Tensor is the Solana power-user venue with enforced-royalty logic, maker/taker clarity, and pro-grade bidding/escrow. Fast UI, Solana-native depth, and creator tools make it the advanced SOL choice. tensor.trade+1
Best For: SOL traders, market-makers, bid/AMM-style flows.
Notable Features: 0% maker / ~2% taker; enforced royalties paid by taker; shared escrow; price-lock mechanics highlighted in community docs. docs.tensor.trade+1
Consider If: You want pro tools on Solana; fees differ from Magic Eden. SwissBorg Academy
Alternatives: Magic Eden (SOL/BTC/ETH), Hyperspace (agg).
Regions: Global • Fees Notes: 2% taker / 0% maker; royalties per collection rules. docs.tensor.trade
Why Use It: OKX’s NFT market integrates with the OKX Web3 Wallet, aggregates across chains, and caters to Bitcoin Ordinals buyers with an active marketplace. Docs highlight multi-chain support and low listing costs. Note potential restrictions for U.S. residents. OKX Wallet+1
Best For: Multi-chain deal-hunters, Ordinals explorers, exchange users.
Notable Features: Aggregation; OKX Wallet; BTC/SOL/Polygon support; zero listing fees per help docs. OKX+1
Consider If: You’re outside the U.S. or comfortable with exchange-affiliated wallets. Coin Bureau
Alternatives: Magic Eden (multi-chain), Kraken NFT (U.S. friendly).
Regions: Global (U.S. access limited) • Fees Notes: Zero listing fee; trading fees vary by venue/collection. OKX
Why Use It: Kraken’s marketplace emphasizes security, compliance, and a simple experience with zero gas fees on trades (you pay network gas only when moving NFTs in/out). Great for U.S. users who prefer a regulated exchange brand. Kraken+1
Best For: U.S. collectors, beginners, compliance-first buyers.
Notable Features: Zero gas on trades; creator earnings support; fiat rails via the exchange. Kraken
Consider If: You prioritize regulated UX over max liquidity.
Alternatives: OpenSea (breadth), OKX NFT (aggregation).
Regions: US/EU • Fees Notes: No gas on trades; royalties and marketplace fees vary by collection. Kraken
Why Use It: Rarible lets projects spin up branded marketplaces with custom fee routing (even 0%), while the main Rarible front-end serves multi-chain listings. Transparent fee schedules and community tooling appeal to creators and DAOs. Rarible+1
Best For: Creators/DAOs launching branded stores; community traders.
Notable Features: No-code community marketplace builder; regressive fee schedule on main site; ETH/Polygon support. Rarible Help+1
Consider If: You want custom fees/branding or to route fees to a treasury. Rarible Help
Alternatives: Zora (creator mints), Foundation (curated art).
Regions: Global • Fees Notes: Regressive service fees on main Rarible; community markets can set fees to 0%. Rarible Help+1
Why Use It: Zora powers on-chain mints with a simple flow and a small protocol mint fee that’s partially shared with creators and referrers, and it now layers social “content coins.” Great for artists who prioritize distribution and rewards over secondary-market depth. Zora+2DappRadar+2
Best For: Artists, indie studios, open editions, mint-first strategies.
Notable Features: One-click minting; protocol rewards; Base/L2 focus; social posting with coins. DappRadar+1
Consider If: You value creator economics; secondary liquidity may be thinner than pro venues.
Alternatives: Rarible (community stores), Foundation (curation).
Regions: Global • Fees Notes: Typical mint fee ~0.000777 ETH; reward splits for creators/referrals per docs. DappRadar+1
Why Use It: Gamma focuses on Ordinals with no-code launchpads and a clean flow for inscribing and trading on Bitcoin. If you want exposure to BTC-native art and collections, Gamma is a friendly on-ramp. Gamma+1
Best For: Ordinals creators/collectors, BTC-first communities.
Notable Features: No-code minting; Ordinals marketplace; education hub. Gamma+1
Consider If: You want BTC exposure vs EVM/SOL liquidity; check fee line items. support.gamma.io
Alternatives: Magic Eden (BTC), UniSat (wallet+market). unisat.io
Regions: Global • Fees Notes: Commission on mints/sales; see support article. support.gamma.io
Why Use It: TokenTrove is a top marketplace in the Immutable gaming ecosystem with stacked listings, strong filters, and price history—ideal for trading in-game items like Gods Unchained, Illuvium, and more. It plugs into Immutable’s global order book and fee model. tokentrove.com+1
Best For: Web3 gamers, IMX/zkEVM collectors, low-gas trades.
Notable Features: Immutable integration; curated gaming collections; alerts; charts. tokentrove.com
Consider If: You mainly collect gaming assets and want L2 speed with predictable fees.
Alternatives: OKX (aggregation), Sphere/AtomicHub (IMX partners). immutable.com
Regions: Global • Fees Notes: Immutable protocol fee ~2% to buyer + marketplace maker/taker fees vary by venue. docs.immutable.com
Primary CTA: Start free trial

This article is for research/education, not financial advice.
What is an NFT marketplace?
An NFT marketplace is a platform where users mint, buy, and sell NFTs (digital assets recorded on a blockchain). Marketplaces handle listings, bids, and transfers—often across multiple chains like ETH, BTC, or SOL.
Which NFT marketplace has the lowest fees?
Blur advertises 0% marketplace fees on ETH; Magic Eden lists 0.5% on many EVM trades and ~2% on SOL/BTC; Tensor uses 0% maker/2% taker. Always factor gas and royalties. blur.io+2help.magiceden.io+2
What’s best for Bitcoin Ordinals?
Magic Eden and Gamma are strong choices; UniSat’s wallet integrates with a marketplace as well. Pick based on fees and tooling. Magic Eden+2Gamma+2
What about U.S.-friendly options?
Kraken NFT is positioned for U.S. users with zero gas on trades. Check any exchange venue’s regional policy before funding. Kraken
Are royalties mandatory?
Policies vary: some venues enforce royalties (e.g., Tensor enforces per collection); others make royalties optional. Review each collection’s page and marketplace rules. docs.tensor.trade
Do I still pay gas?
Yes, on most chains. Some custodial venues remove gas on trades but charge gas when you deposit/withdraw. Kraken
If you want cross-chain liquidity and discovery, start with Magic Eden. For pro ETH execution, Blur leads; for pro SOL, choose Tensor. U.S. newcomers who value compliance and predictability should consider Kraken NFT. Gaming collectors on Immutable can lean on TokenTrove.
Related Reads:
We verified claims on official help/docs/fee pages and product homepages, cross-checking directional volumes and market conditions with widely cited datasets. Fee schedules and regional policies can change—always confirm on the official site before transacting. Updated September 2025.
Per-provider official sources reviewed:
TokenTrove/Immutable: TokenTrove site; Immutable fees docs; Marketplace hub. tokentrove.com+2docs.immutable.com+2
DeFi never sits still. Rates move, incentives rotate, and new chains launch weekly. Yield aggregators and vaults automate that work—routing your assets into on-chain strategies that can compound rewards and manage risk while you sleep. In short: a yield aggregator is a smart-contract “account” that deploys your tokens into multiple strategies to optimize returns (with risks).
Who is this for? Active DeFi users, long-term holders, DAOs/treasuries, and anyone exploring passive crypto income in 2025. We prioritized providers with strong security postures, transparent docs, useful dashboards, and broad asset coverage. Secondary angles include DeFi vaults, auto-compounders, and yield optimization tools.
Data sources: official product/docs, security and transparency pages; Token Metrics testing; cross-checks with widely cited market datasets when needed. Last updated September 2025.


Primary CTA: Start free trial.

This article is for research/education, not financial advice.
What is a yield aggregator in crypto?
A yield aggregator is a smart-contract system that deploys your tokens into multiple DeFi strategies and auto-compounds rewards to target better risk-adjusted returns than manual farming.
Are vaults custodial?
Most DeFi vaults are non-custodial contracts—you keep control via your wallet, while strategies execute on-chain rules. Always read docs for admin keys, pausable functions, and upgrade paths.
Fixed vs. variable yield—how do I choose?
If you value certainty, fixed yields (e.g., via Pendle) can make sense; variable yield can outperform in risk-on markets. Many users blend both.
What fees should I expect?
Common fees are management, performance, and withdrawal (plus gas). Each vault shows specifics; compare net, not just gross APY.
Which networks are best for beginners?
Start on mainstream EVM chains with strong tooling (Ethereum L2s, major sidechains). Fees are lower and UI tooling is better for learning.
How safe are these platforms?
Risks include contract bugs, oracle issues, market shocks, and governance. Prefer audited, well-documented protocols with visible risk controls—and diversify.
If you want set-and-forget blue-chips, start with Yearn or Sommelier. Multichain farmers often prefer Beefy. Curve/Balancer LPs should consider Convex/Aura. Rate-sensitive users may like Pendle or Morpho Vaults. Builders and treasuries should look at Enzyme and Arrakis for tailored vault setups.
Related Reads:
We reviewed each provider’s official site, docs, and product pages for features, security notes, and positioning. Third-party datasets were used only to cross-check market presence. Updated September 2025.
DeFi lending/borrowing protocols let you supply crypto to earn yield or post collateral to borrow assets without an intermediary. That’s the short answer. In 2025, these platforms matter because market cycles are faster, stablecoin yields are competitive with TradFi, and new risk-isolation designs have reduced contagion across assets. If you’re researching the best lending/borrowing protocols for diversified yield or flexible liquidity, this guide is for you—whether you’re a first-time lender, an active degen rotating between chains, or an institution exploring programmatic treasury management. We highlight security posture, liquidity depth, supported assets, fees, and UX. We also note regional considerations where relevant and link only to official sources.
We relied on official product/docs and security pages; third-party market datasets (e.g., CCData/Kaiko/CoinGecko) were used only for cross-checks. Last updated September 2025.
Why Use It: Aave remains the blue-chip money market with deep, multi-chain liquidity and granular risk controls across markets. Its non-custodial design and battle-tested rate model make it a default “base layer” for supplying majors and borrowing stables. aave.com+2aave.com+2
Best For: ETH/L2 users, stablecoin lenders, sophisticated borrowers, integrators.
Notable Features: Multiple markets and chains; variable/stable borrow rates; robust docs/dev tooling; governance-led risk parameters. aave.com
Consider If: You want the broadest asset access with conservative risk management.
Regions: Global (DeFi; user eligibility varies by jurisdiction).
Fees/Notes: Interest model + protocol reserve; gas/bridge costs apply. aave.com
Alternatives: Compound, Morpho.
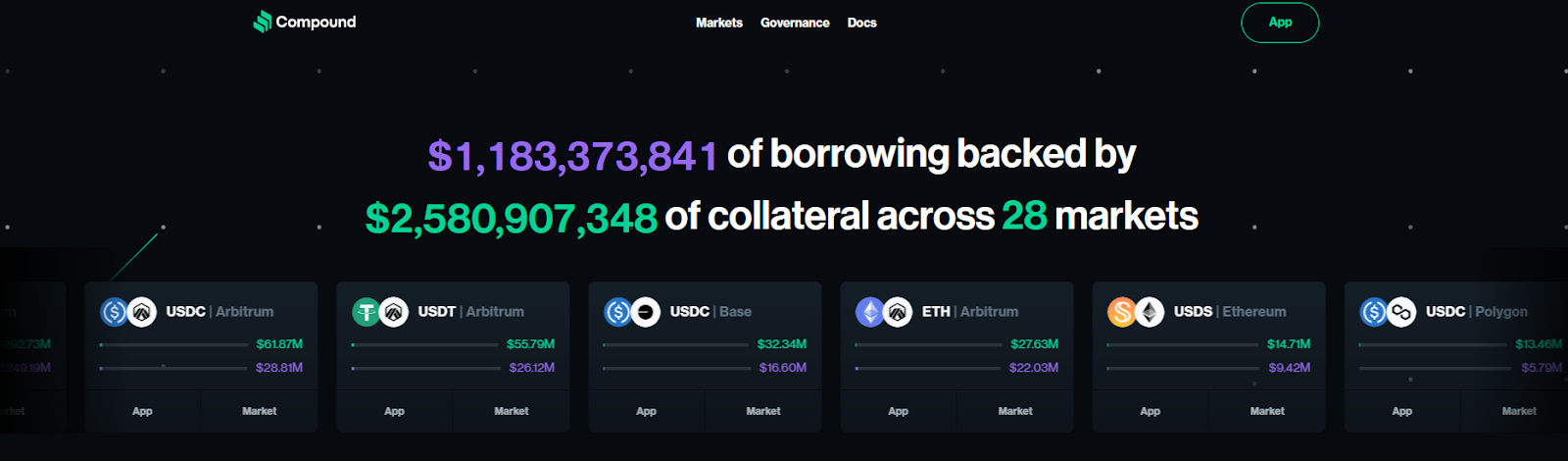
Why Use It: Compound popularized algorithmic interest rates and still offers clean markets and a developer-friendly stack (Compound II/III). For ETH/L2 blue-chips and stables, it’s a straightforward option. compound.finance+1
Best For: ETH mainnet lenders, conservative borrowers, devs needing a stable API/primitive.
Notable Features: Autonomous interest-rate protocol; separate “III” markets; transparent market pages; on-chain governance. compound.finance+1
Consider If: You want a minimal, well-understood money market for majors.
Regions: Global (DeFi; user eligibility varies).
Fees/Notes: Variable rates; protocol reserves; gas applies.
Alternatives: Aave, Spark Lend.

Why Use It: Morpho Blue focuses on trustless, efficient markets with permissionless pair creation and improved capital efficiency. It aims to route lenders/borrowers to “best possible” terms with a narrow, auditable core. morpho.org+2morpho.org+2
Best For: Power users, DeFi funds, integrators optimizing rates, risk-aware lenders.
Notable Features: Morpho Blue minimal core; permissionless markets; lower gas; flexible collateral factors. morpho.org
Consider If: You prioritize rate efficiency and clear risk boundaries.
Regions: Global.
Fees/Notes: Market-specific parameters; gas applies.
Alternatives: Silo Finance, Fraxlend.
Why Use It: SparkLend benefits from direct liquidity provided by Sky (Maker ecosystem), offering transparent, governance-set rates for borrowing USDS/USDC at scale—useful for stablecoin treasuries and market-makers. spark+2spark+2
Best For: Stablecoin borrowers, DAOs/treasuries, conservative lenders focused on stables.
Notable Features: USDS/USDC borrowing at scale; Spark Liquidity Layer; governance-driven rate transparency. spark
Consider If: You want Maker-aligned stablecoin rails with predictable liquidity.
Regions: Global (check local eligibility).
Fees/Notes: Governance-determined parameters; protocol reserves; gas applies.
Alternatives: Aave, Compound.
Why Use It: Radiant targets cross-chain UX with audited deployments and a community-driven token model—appealing to users active on Arbitrum and other L2s seeking competitive rates and incentives. Radiant Capital
Best For: L2 lenders/borrowers, yield seekers rotating across EVMs.
Notable Features: Multi-audit posture; L2-centric markets; RDNT lockers sharing protocol revenue; incentives. Radiant Capital
Consider If: You’re comfortable with DeFi token incentives and L2 bridging.
Regions: Global.
Fees/Notes: Variable APRs; incentive emissions; gas/bridge costs.
Alternatives: Aave (L2), Silo.
Why Use It: Notional offers fixed-rate, fixed-term lending and borrowing, providing users with predictable interest rates and loan durations. This model is particularly appealing to institutional players and long-term investors seeking stability in DeFi markets.
Best For: Institutional borrowers, long-term DeFi investors, and those seeking predictable lending terms.
Notable Features:
Consider If: You prefer the certainty of fixed rates and terms in your lending and borrowing activities.
Regions: Global
Fees/Notes: Fees vary based on loan terms and asset type.
Alternatives: Aave, Compound, Morpho
Why Use It: Venus is the leading money market on BNB Chain, offering broad asset coverage and deep stablecoin pools for users anchored to that ecosystem. It emphasizes security practices and transparency to support its large user base. venus.io+1
Best For: BNB Chain lenders/borrowers, yield strategists, BSC-native projects.
Notable Features: Multichain money market positioning; active governance; security resources. venus.io
Consider If: You are primarily on BNB Chain and need depth.
Regions: Global.
Fees/Notes: Variable APRs; protocol reserves; chain gas fees.
Alternatives: Aave (BSC deployments where available), Radiant.
Why Use It: On Solana, Solend is the go-to autonomous money market with many asset pools and fast, low-fee transactions. It’s well suited for active traders and stablecoin lenders who want Solana performance. solend.fi+1
Best For: Solana users, stablecoin lenders, active borrowers hedging perps/DEX LP.
Notable Features: Dozens of pools; developer portal; bug bounty; investor backing. solend.fi
Consider If: You want low fees and high throughput on SOL.
Regions: Global.
Fees/Notes: Variable APRs; Solana fees are minimal but apply.
Alternatives: Kamino Lend (Solana), Aave (EVM).
Why Use It: JustLend is TRON’s flagship money market, supporting TRX, USDT, and other TRC-20 assets with competitive rates and growing DAO governance. It’s a practical option for users embedded in the TRON ecosystem. JustLend DAO+1
Best For: TRON users, USDT lenders on TRON, TRX stakers (sTRX).
Notable Features: TRON integration; sTRX staking module; active on-chain proposals. app.justlend.org+1
Consider If: You primarily hold TRC-20s and want native UX.
Regions: Global (note regional availability of TRON gateways).
Fees/Notes: Variable APRs; TRON gas is low.
Alternatives: Venus (BSC), Aave (EVM).
Why Use It: Silo builds isolated markets (“silos”) so lenders bear only the risk of the market they choose—reducing cross-asset contagion seen in shared pools. Helpful for long-tail assets under tighter risk parameters. Silo Finance+2Silopedia+2
Best For: Risk-aware lenders, long-tail asset communities, L2 users.
Notable Features: Isolated pairs; transparent docs; multi-chain deployments; active governance. silodocs2.netlify.app
Consider If: You want clear compartmentalization of risk per asset.
Regions: Global.
Fees/Notes: Market-specific rates; gas/bridge costs.
Alternatives: Morpho, Fraxlend.

Primary CTA: Start free trial

This article is for research/education, not financial advice.
What is a DeFi lending/borrowing protocol?
A smart-contract system that lets users supply assets to earn interest or post collateral to borrow other assets, typically overcollateralized with algorithmic rates.
How do variable and stable borrow rates differ?
Variable rates change with utilization; stable/“fixed” rates are more predictable but can reprice under specific conditions. Always check the protocol’s docs.
Are isolated markets safer than shared pools?
They can reduce cross-asset contagion by containing risk to one market, but you still face collateral, oracle, and liquidation risks.
Which chains are best for low-fee lending?
Solana and several L2s (e.g., Arbitrum, Optimism, Base) offer lower fees than mainnet. Choose based on assets, liquidity, and tooling.
How much collateral should I post?
Many borrowers keep a conservative buffer (e.g., target health factor well above minimum), especially in volatile markets; tailor to your risk tolerance.
Can institutions use these protocols?
Yes—many funds and DAOs integrate with major money markets, often via smart-contract wallets and custom monitors.
If you want breadth and depth, start with Aave or Compound. If you’re optimizing stablecoin flows, Spark stands out. For isolated-risk, asset-specific strategies, Morpho, Silo, and Fraxlend are strong fits. Solana, TRON, and BNB users should look to Solend, JustLend, and Venus respectively. Pick based on chain, risk, and the collateral you actually hold.
Related Reads:
We reviewed official app/docs pages, security/audit resources, governance and market pages for each protocol. Third-party datasets were used only to cross-check volumes/liquidity. Updated September 2025 to reflect current markets and docs.
