Top Crypto Trading Platforms in 2025







%201.svg)
%201.svg)
Big news: We’re cranking up the heat on AI-driven crypto analytics with the launch of the Token Metrics API and our official SDK (Software Development Kit). This isn’t just an upgrade – it's a quantum leap, giving traders, hedge funds, developers, and institutions direct access to cutting-edge market intelligence, trading signals, and predictive analytics.
Crypto markets move fast, and having real-time, AI-powered insights can be the difference between catching the next big trend or getting left behind. Until now, traders and quants have been wrestling with scattered data, delayed reporting, and a lack of truly predictive analytics. Not anymore.
The Token Metrics API delivers 32+ high-performance endpoints packed with powerful AI-driven insights right into your lap, including:
Getting started with the Token Metrics API is simple:
At Token Metrics, we believe data should be decentralized, predictive, and actionable.
The Token Metrics API & SDK bring next-gen AI-powered crypto intelligence to anyone looking to trade smarter, build better, and stay ahead of the curve. With our official SDK, developers can plug these insights into their own trading bots, dashboards, and research tools – no need to reinvent the wheel.
%201.svg)
%201.svg)
DeFi protocols are maturing beyond early ponzi dynamics toward sustainable revenue models. Aave operates in this evolving landscape where real yield and proven product-market fit increasingly drive valuations rather than speculation alone. Growing regulatory pressure on centralized platforms creates tailwinds for decentralized alternatives—factors that inform our comprehensive AAVE price prediction framework.
The scenario bands below reflect how AAVE price predictions might perform across different total crypto market cap environments. Each tier represents a distinct liquidity regime, from bear conditions with muted DeFi activity to moon scenarios where decentralized infrastructure captures significant value from traditional finance.

Disclosure
Educational purposes only, not financial advice. Crypto is volatile, do your own research and manage risk.
Each band blends cycle analogues and market-cap share math with TA guardrails. Base assumes steady adoption and neutral or positive macro. Moon layers in a liquidity boom. Bear assumes muted flows and tighter liquidity.
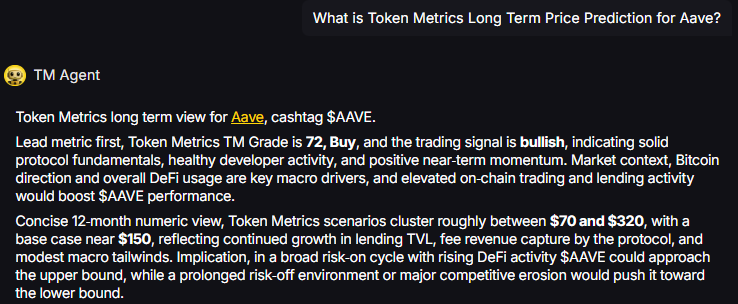
TM Agent baseline: Token Metrics TM Grade is 72, Buy, and the trading signal is bullish, indicating solid protocol fundamentals, healthy developer activity, and positive near-term momentum. Concise twelve-month numeric view, Token Metrics price prediction scenarios cluster roughly between $70 and $320, with a base case near $150, reflecting continued growth in lending TVL, fee revenue capture by the protocol, and modest macro tailwinds.
Live details: Aave Token Details
Affiliate Disclosure: We may earn a commission from qualifying purchases made via this link, at no extra cost to you.
Our Token Metrics price prediction framework spans four market cap tiers, each representing different levels of crypto market maturity and liquidity:
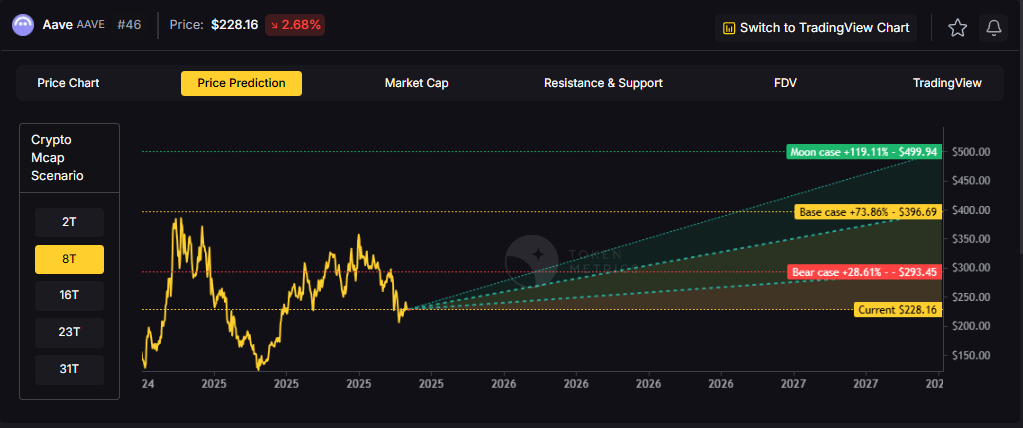
8T Market Cap - AAVE Price Prediction:
At an 8 trillion dollar total crypto market cap, AAVE projects to $293.45 in bear conditions, $396.69 in the base case, and $499.94 in bullish scenarios.
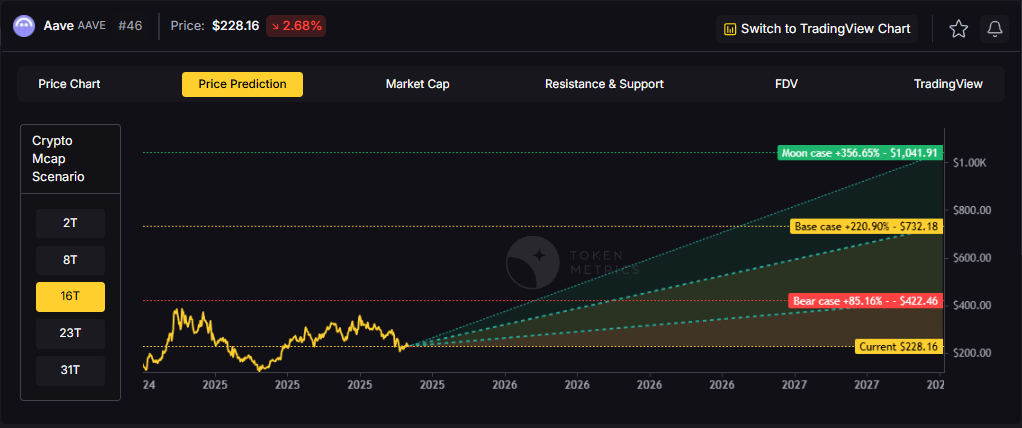
Doubling the market to 16 trillion expands the price prediction range to $427.46 (bear), $732.18 (base), and $1,041.91 (moon).
At 23 trillion, the price prediction scenarios show $551.46, $1,007.67, and $1,583.86 respectively.

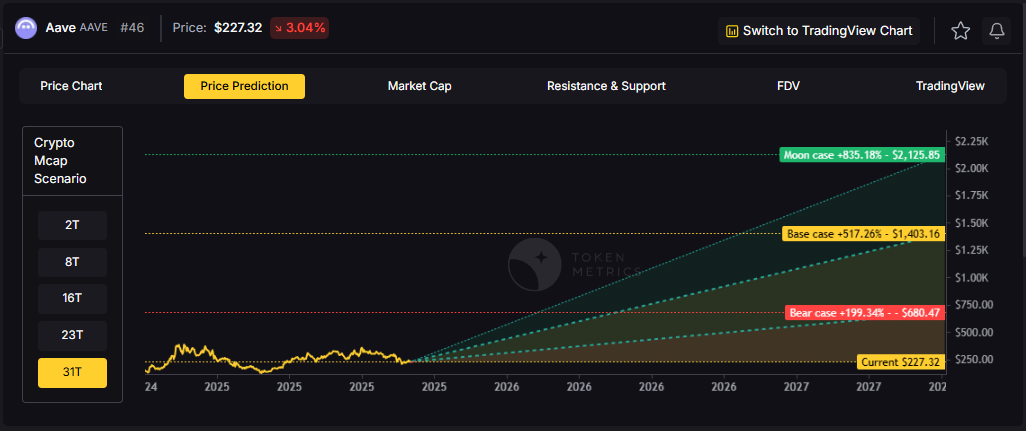
In the maximum liquidity scenario of 31 trillion, AAVE price predictions could reach $680.47 (bear), $1,403.16 (base), or $2,175.85 (moon).
Each tier assumes progressively stronger market conditions, with the base case price prediction reflecting steady growth and the moon case requiring sustained bull market dynamics.
Aave represents one opportunity among hundreds in crypto markets. Token Metrics Indices bundle AAVE with top one hundred assets for systematic exposure to the strongest projects. Single tokens face idiosyncratic risks that diversified baskets mitigate.
Historical index performance demonstrates the value of systematic diversification versus concentrated positions.
Aave is a decentralized lending protocol that operates across multiple EVM-compatible chains including Ethereum, Polygon, Arbitrum, and Optimism. The network enables users to supply crypto assets as collateral and borrow against them in an over-collateralized manner, with interest rates dynamically adjusted based on utilization.
The AAVE token serves as both a governance asset and a backstop for the protocol through the Safety Module, where stakers earn rewards in exchange for assuming shortfall risk. Primary utilities include voting on protocol upgrades, fee switches, collateral parameters, and new market deployments.
Token Metrics AI provides comprehensive context on Aave's positioning and challenges.
Vision: Aave aims to create an open, accessible, and non-custodial financial system where users have full control over their assets. Its vision centers on decentralizing credit markets and enabling seamless, trustless lending and borrowing across blockchain networks.
Problem: Traditional financial systems often exclude users due to geographic, economic, or institutional barriers. Even in crypto, accessing credit or earning yield on idle assets can be complex, slow, or require centralized intermediaries. Aave addresses the need for transparent, permissionless, and efficient lending and borrowing markets in the digital asset space.
Solution: Aave uses a decentralized protocol where users supply assets to liquidity pools and earn interest, while borrowers can draw from these pools by posting collateral. It supports features like variable and stable interest rates, flash loans, and cross-chain functionality through its Layer 2 and multi-chain deployments. The AAVE token is used for governance and as a safety mechanism via its staking program (Safety Module).
Market Analysis: Aave is a leading player in the DeFi lending sector, often compared with protocols like Compound and Maker. It benefits from strong brand recognition, a mature codebase, and ongoing innovation such as Aave Arc for institutional pools and cross-chain expansion. Adoption is driven by liquidity, developer activity, and integration with other DeFi platforms. Key risks include competition from newer lending protocols, regulatory scrutiny on DeFi, and smart contract risks. As a top DeFi project, Aave's performance reflects broader trends in decentralized finance, including yield demand, network security, and user trust. Its multi-chain strategy helps maintain relevance amid shifting ecosystem dynamics.
Fundamental Grade: 75.51% (Community 77%, Tokenomics 100%, Exchange 100%, VC 49%, DeFi Scanner 70%).

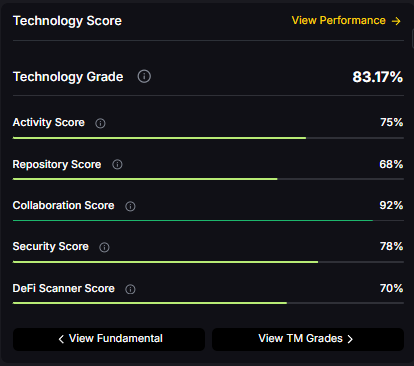
Technology Grade: 83.17% (Activity 75%, Repository 68%, Collaboration 92%, Security 78%, DeFi Scanner 70%).
Yes. Based on our price prediction scenarios, AAVE could reach $1,007.67 in the 23T base case and $1,041.91 in the 16T moon case. Not financial advice.
At current price of $228.16, a 10x would reach $2,281.60. This falls within the 31T moon case price prediction at $2,175.85 (only slightly below), and would require extreme liquidity expansion. Not financial advice.
Our moon case price predictions range from $499.94 at 8T to $2,175.85 at 31T. These scenarios assume maximum liquidity expansion and strong Aave adoption. Not financial advice.
Our comprehensive 2027 price prediction framework suggests AAVE could trade between $293.45 and $2,175.85, depending on market conditions and total crypto market capitalization. The base case scenario clusters around $396.69 to $1,403.16 across different market cap environments. Not financial advice.
AAVE shows strong fundamentals (75.51% grade) and technology scores (83.17% grade), with bullish trading signals. However, all price predictions involve uncertainty and risk. Always conduct your own research and consult financial advisors before investing. Not financial advice.
Track live grades and signals: Token Details
Want exposure? Buy AAVE on MEXC
Disclosure
Educational purposes only, not financial advice. Crypto is volatile, do your own research and manage risk.
%201.svg)
%201.svg)
x402 is an open-source, HTTP-native payment protocol developed by Coinbase that enables pay-per-call API access using crypto wallets. It leverages the HTTP 402 Payment Required status code to create seamless, keyless API payments.
It eliminates traditional API keys and subscriptions, allowing agents and applications to pay for exactly what they use in real time. It works across Base and Solana with USDC and selected native tokens such as TMAI.
Start using Token Metrics X402 integration here. https://www.x402scan.com/server/244415a1-d172-4867-ac30-6af563fd4d25
x402 transforms API access by making payments native to HTTP requests.
Feature | Traditional APIs | x402 APIs |
Authentication | API keys, tokens | Wallet signature |
Payment Model | Subscription, prepaid | Pay-per-call |
Onboarding | Sign up, KYC, billing | Connect wallet |
Rate Limits | Fixed tiers | Economic (pay more = more access) |
Commitment | Monthly/annual | Zero, per-call only |
How to use it: Add x-coinbase-402: true header to any supported endpoint. Sign payment with your wallet. The API responds immediately after confirming micro-payment.
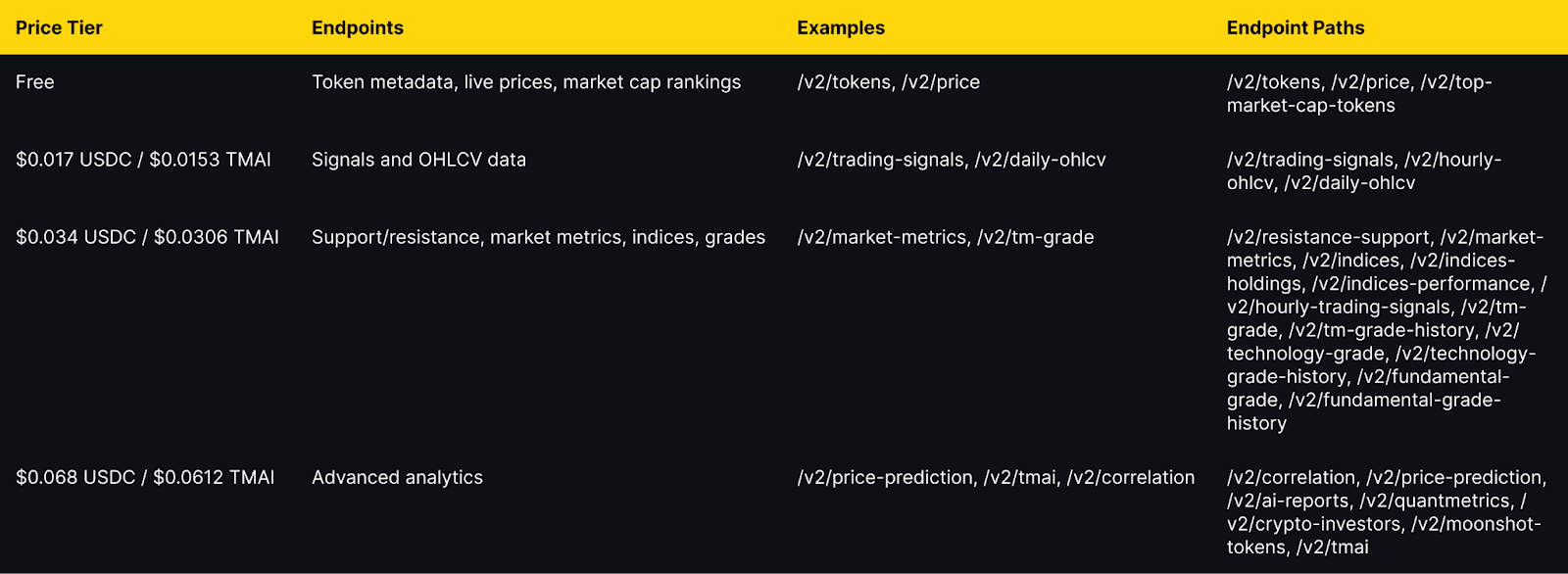
Token Metrics integration: All public endpoints available via x402 with per-call pricing from $0.017 to $0.068 USDC (10% discount with TMAI token).
Explore live agents: https://www.x402scan.com/composer.
The Protocol Flow
The HTTP 402 status code was reserved in HTTP/1.1 in 1997 for future digital payment use cases and was never standardized for any specific payment scheme. x402 activates this path by using 402 responses to coordinate crypto payments during API requests.
Why this matters: It eliminates intermediary payment processors, enables true machine-to-machine commerce, and reduces friction for AI agents.
CoinGecko Recognition
CoinGecko launched a dedicated x402 Ecosystem category in October 2025, tracking 700+ projects with over $1 billion market cap and approximately $213 million in daily trading volume. Top performers include PING and Alnalyst, along with established projects like EigenCloud.
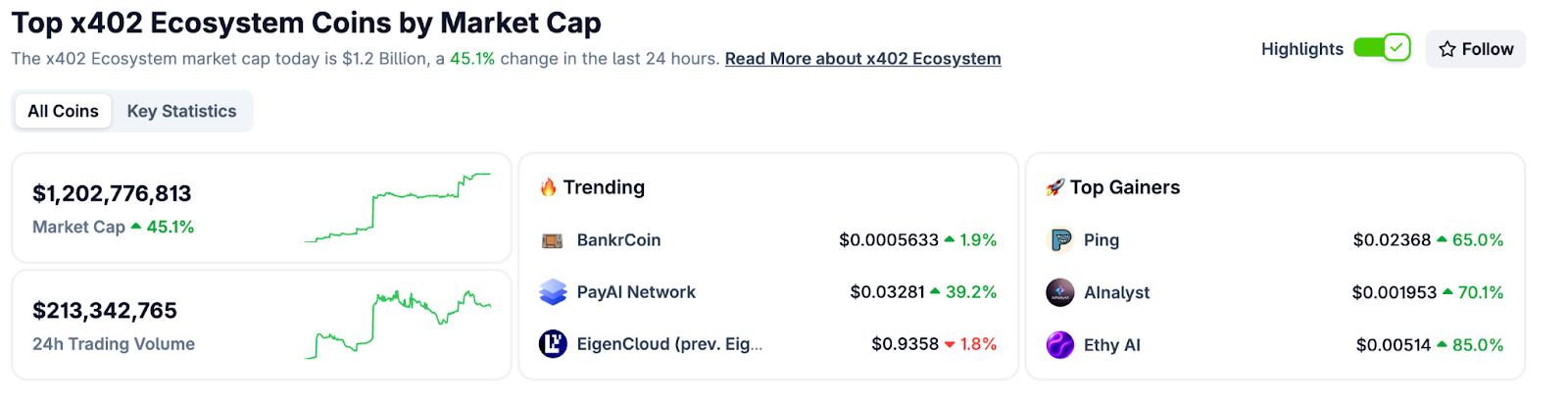
Base Network Adoption
Base has emerged as the primary chain for x402 adoption, with 450,000+ weekly transactions by late October 2025, up from near-zero in May. This growth demonstrates real agent and developer usage.
Composer is x402scan's sandbox for discovering and using AI agents that pay per tool call. Users can open any agent, chat with it, and watch tool calls and payments stream in real time.
Top agents include AInalyst, Canza, SOSA, and NewEra. The Composer feed shows live activity across all agents.

Explore Composer: https://x402scan.com/composer
What We Ship
Token Metrics offers all public API endpoints via x402 with no API key required. Pay per call with USDC or TMAI for a 10 percent discount. Access includes trading signals, price predictions, fundamental grades, technology scores, indices data, and the AI chatbot.
Check out Token Metrics Integration on X402. https://www.x402scan.com/server/244415a1-d172-4867-ac30-6af563fd4d25
Data as of October, 2025.
Pricing Tiers
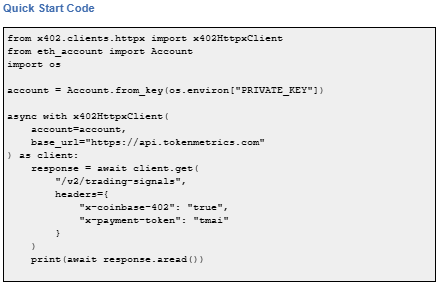
Important note: TMAI Spend Limit: TMAI has 18 decimals. Set max payment to avoid overspending. Example: 200 TMAI = 200 * (10 ** 18) in base units.
Full integration guide: https://api.tokenmetrics.com
Ecosystem Participants and Tools
Active x402 Endpoints
Key endpoints beyond Token Metrics include Heurist Mesh for crypto intelligence, Tavily extract for structured web content, Firecrawl search for SERP and scraping, Twitter or X search for social discovery, and various DeFi and market data providers.
Infrastructure and Tools
Common Questions About x402
How is x402 different from traditional API keys?
x402 uses wallet signatures instead of API keys. Payment happens per call rather than via subscription. No sign-up, no monthly billing, no rate limit tiers. You pay for exactly what you use.
Which chains support x402?
Currently Base and Solana. Most activity is on Base with USDC as the primary payment token. Some endpoints accept native tokens like TMAI for discounts.
Do I need to trust the API provider with my funds?
No. Payments are on-chain and verifiable. You approve each transaction amount. No escrow or prepayment is required.
What happens if a payment fails?
The API returns 402 Payment Required again with updated payment details. Your client retries automatically. You do not receive data until payment confirms.
Can I use x402 with existing API clients?
Yes, with x402 client libraries such as x402-axios for Node and x402-httpx for Python. These wrap standard HTTP clients and handle the payment flow automatically.
Getting Started Checklist
Token Metrics x402 Resources
What's Next for x402
Ecosystem expansion. More API providers adopting x402, additional chains beyond Base and Solana, standardization of payment headers and response formats.
Agent sophistication. As x402 matures, expect agents that automatically discover and compose multiple paid endpoints, optimize costs across providers, and negotiate better rates for bulk usage.
Disclosure
Educational content only, not financial advice. API usage and crypto payments carry risks. Verify all transactions before signing. Do your own research.
%201.svg)
%201.svg)
Opening Hook
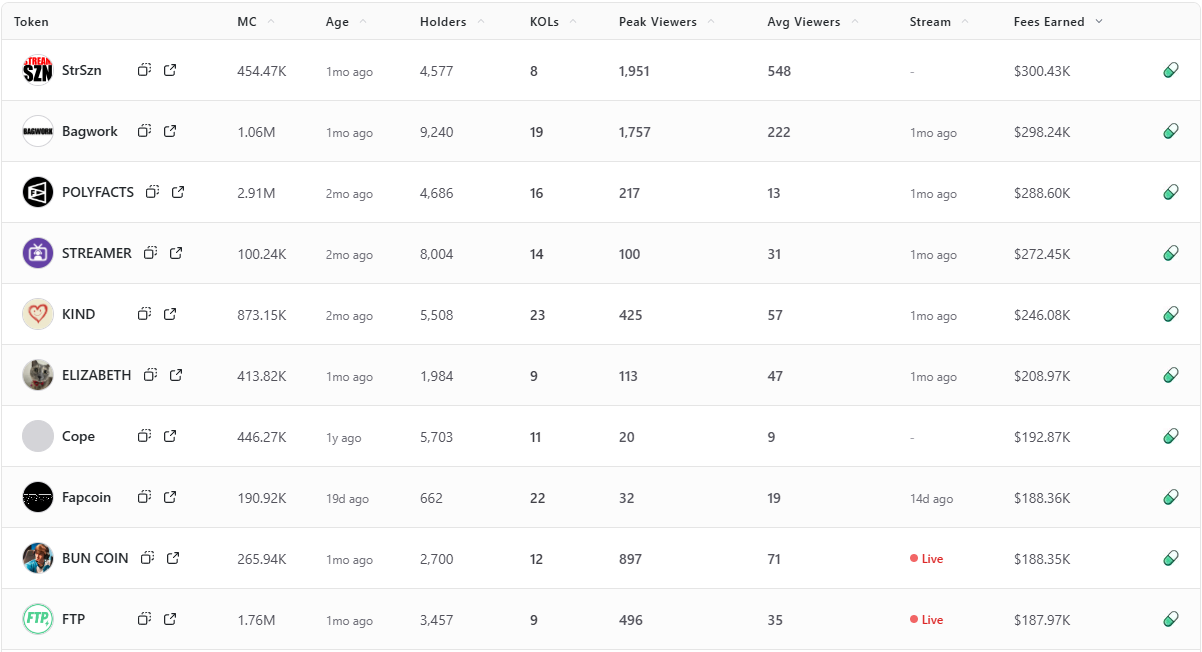
Fees Earned is a clean way to see which livestream tokens convert attention into on-chain activity. This leaderboard ranks the top 10 Pump.fun livestream tokens by Fees Earned using the screenshot you provided.
Selection rule is simple, top 10 by Fees Earned from the screenshot, numbers appear exactly as shown. If a field is not in the image, it is recorded as —.
Entity coverage: project names and tickers are taken as listed on Pump.fun, chain is Solana, sector is livestream meme tokens and creator tokens.
Token Metrics Live (TMLIVE) brings real time, data driven crypto market analysis to Pump.fun. The team has produced live crypto content for 7 years with a 500K plus audience and a platform of more than 100,000 users. Our public track record includes early coverage of winners like MATIC and Helium in 2018.
TMLIVE Quick Stats, as captured
TLDR: Fees Earned Leaders at a Glance
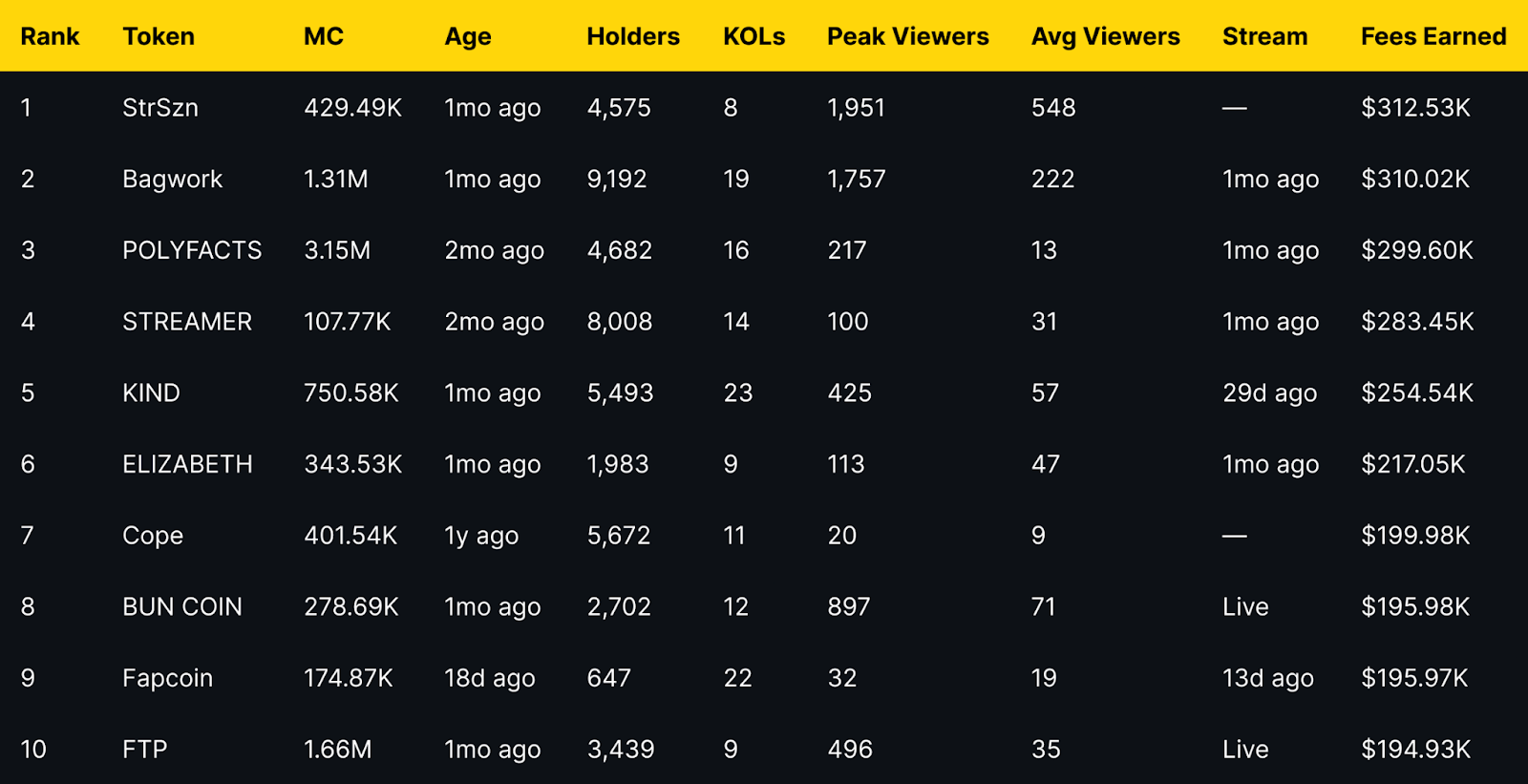
Short distribution note: the top three sit within a narrow band of each other, while mid-table tokens show a mix of older communities and recent streams. Several names with modest average viewers still appear due to concentrated activity during peaks.
StrSzn
Positioning: Active community meme with consistent viewer base.
Research Blurb: Project details unclear at time of writing. Fees and viewership suggest consistent stream engagement over the last month.
Quick Facts: Chain = Solana, Status = —, Peak Viewers = 1,951, Avg Viewers = 548.
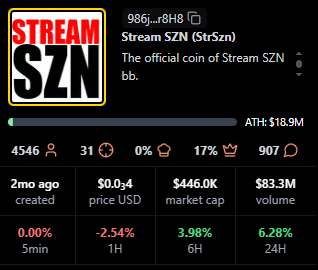
https://pump.fun/coin/986j8mhmidrcbx3wf1XJxsQFvWBMXg7gnDi3mejsr8H8
Bagwork
Positioning: Large holder base with sustained attention.
Research Blurb: Project details unclear at time of writing. Strong holders and KOL presence supported steady audience numbers.
Quick Facts: Chain = Solana, Status = 1mo ago, Holders = 9,192, KOLs = 19.

https://pump.fun/coin/7Pnqg1S6MYrL6AP1ZXcToTHfdBbTB77ze6Y33qBBpump
POLYFACTS
Positioning: Higher market cap with light average viewership.
Research Blurb: Project details unclear at time of writing. High market cap with comparatively low average viewers implies fees concentrated in shorter windows.
Quick Facts: Chain = Solana, Status = 1mo ago, MC = 3.15M, Avg Viewers = 13.
https://pump.fun/coin/FfixAeHevSKBZWoXPTbLk4U4X9piqvzGKvQaFo3cpump
STREAMER
Positioning: Community focused around streaming identity.
Research Blurb: Project details unclear at time of writing. Solid holders and moderate KOL count, steady averages over time.
Quick Facts: Chain = Solana, Status = 1mo ago, Holders = 8,008, KOLs = 14.

https://pump.fun/coin/3arUrpH3nzaRJbbpVgY42dcqSq9A5BFgUxKozZ4npump
KIND
Positioning: Heaviest KOL footprint in the top 10.
Research Blurb: Project details unclear at time of writing. The largest KOL count here aligns with above average view metrics and meaningful fees.
Quick Facts: Chain = Solana, Status = 29d ago, KOLs = 23, Avg Viewers = 57.

https://pump.fun/coin/V5cCiSixPLAiEDX2zZquT5VuLm4prr5t35PWmjNpump
ELIZABETH
Positioning: Mid-cap meme with consistent streams.
Research Blurb: Project details unclear at time of writing. Viewer averages and recency indicate steady presence rather than single spike behavior.
Quick Facts: Chain = Solana, Status = 1mo ago, Avg Viewers = 47, Peak Viewers = 113.
https://pump.fun/coin/DiiTPZdpd9t3XorHiuZUu4E1FoSaQ7uGN4q9YkQupump
Cope
Positioning: Older token with a legacy community.
Research Blurb: Project details unclear at time of writing. Despite low recent averages, it holds a sizable base and meaningful fees.
Quick Facts: Chain = Solana, Status = —, Age = 1y ago, Avg Viewers = 9.
https://pump.fun/coin/DMwbVy48dWVKGe9z1pcVnwF3HLMLrqWdDLfbvx8RchhK
BUN COIN
Positioning: Currently live, strong peaks relative to size.
Research Blurb: Project details unclear at time of writing. Live streaming status often coincides with bursts of activity that lift fees quickly.
Quick Facts: Chain = Solana, Status = Live, Peak Viewers = 897, Avg Viewers = 71.
https://pump.fun/coin/HQDTzNa4nQVetoG6aCbSLX9kcH7tSv2j2sTV67Etpump
Fapcoin
Positioning: Newer token with targeted pushes.
Research Blurb: Project details unclear at time of writing. Recent age and meaningful KOL support suggest orchestrated activations that can move fees.
Quick Facts: Chain = Solana, Status = 13d ago, Age = 18d ago, KOLs = 22.

https://pump.fun/coin/8vGr1eX9vfpootWiUPYa5kYoGx9bTuRy2Xc4dNMrpump
FTP
Positioning: Live status with solid mid-table view metrics.
Research Blurb: Project details unclear at time of writing. Peaks and consistent averages suggest an active audience during live windows.
Quick Facts: Chain = Solana, Status = Live, Peak Viewers = 496, Avg Viewers = 35.
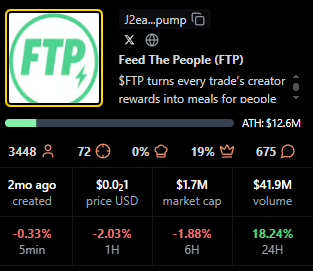
https://pump.fun/coin/J2eaKn35rp82T6RFEsNK9CLRHEKV9BLXjedFM3q6pump
Signals From Fees Earned: Patterns to Watch
Fees Earned often rise with peak and average viewers, but timing matters. Several tokens here show concentrated peaks with modest averages, which implies that well timed announcements or coordinated segments can still produce high fees.
Age is not a blocker for this board. Newer tokens like Fapcoin appear due to focused activity, while older names such as Cope persist by mobilizing established holders. KOL count appears additive rather than decisive, with KIND standing out as the KOL leader.
For creators, Fees Earned reflects whether livestream moments translate into on-chain action. Design streams around clear calls to action, align announcements with segments that drive peaks, then sustain momentum with repeatable formats that stabilize averages.
For traders, Fees Earned complements market cap, viewers, and age. Look for projects that combine rising averages with consistent peaks, because those patterns suggest repeatable engagement rather than single event spikes.
TV Live is a fast way to follow real-time crypto market news, creator launches, and token breakdowns as they happen. You get context on stream dynamics, audience behavior, and on-chain activity while the story evolves.
CTA: Watch TV Live for real-time crypto market news →TV Live Link
CTA: Follow and enable alerts → TV Live
Token Metrics is trusted for transparent data, crypto analytics, on-chain ratings, and investor education. Our platform offers cutting-edge signals and market research to empower your crypto investing decisions.
What is the best way to track Pump.fun livestream leaders?
Tracking Pump.fun livestream leaders starts with the scanner views that show Fees Earned, viewers, and KOLs side by side, paired with live coverage so you see data and narrative shifts together.
Do higher fees predict higher market cap or sustained viewership?
Higher Fees Earned does not guarantee higher market cap or sustained viewership, it indicates conversion in specific windows, while longer term outcomes still depend on execution and community engagement.
How often do these rankings change?
Rankings can change quickly during active cycles, the entries shown here reflect the exact time of the screenshot.
Next Steps
Disclosure
This article is educational content. Cryptocurrency involves risk. Always do your own research.

%201.svg)
%201.svg)
REST APIs are the lingua franca of modern web and data ecosystems. Developers, data scientists, and product teams rely on RESTful endpoints to move structured data between services, power mobile apps, and connect AI models to live data sources. This post explains what REST APIs are, the core principles and methods, practical design patterns, security considerations, and how to evaluate REST APIs for use in crypto and AI workflows.
Representational State Transfer (REST) is an architectural style for distributed systems. A REST API exposes resources—such as users, orders, or market ticks—via predictable URLs and HTTP methods. Each resource representation is typically transferred in JSON, XML, or other media types. The API defines endpoints, input and output schemas, and expected status codes so clients can programmatically interact with a server.
Key characteristics include stateless requests, cacheable responses when appropriate, uniform interfaces, and resource-oriented URIs. REST is not a protocol but a set of conventions that favor simplicity, scalability, and composability. These properties make REST APIs well-suited for microservices, web clients, and integrations with analytics or machine learning pipelines.
Understanding the mapping between REST semantics and HTTP verbs is foundational:
Designing clear resource names and predictable query parameters improves developer experience. Use nouns for endpoints (e.g., /api/v1/orders) and separate filtering, sorting, and pagination parameters. Well-structured response envelopes with consistent error codes and time stamps help automation and observability.
Good REST API design balances usability, performance, and security. Start with a contract-first approach: define OpenAPI/Swagger schemas that describe endpoints, request/response shapes, authentication, and error responses. Contracts enable auto-generated clients, mock servers, and validation tooling.
Security considerations include:
Operational best practices include logging structured events, exposing health and metrics endpoints, and versioning APIs (e.g., v1, v2) to enable backward-compatible evolution. Use semantic versioning in client libraries and deprecate endpoints with clear timelines and migration guides.
Testing a REST API includes unit tests for business logic, contract tests against OpenAPI definitions, and end-to-end integration tests. Performance profiling should focus on latency tail behavior, not just averages. Key tools and techniques:
For AI systems, robust APIs must address reproducibility: include schema versioning and event timestamps so models can be retrained with consistent historical data. For crypto-related systems, ensure on-chain data sources and price oracles expose deterministic endpoints and clearly document freshness guarantees.
REST APIs are frequently used to expose market data, on-chain metrics, historical time-series, and signals that feed AI models or dashboards. When integrating third-party APIs for crypto data, evaluate latency, update frequency, and the provider's methodology for derived metrics. Consider fallbacks and reconciliations: multiple independent endpoints can be polled and compared to detect anomalies or outages.
AI agents often consume REST endpoints for feature extraction and live inference. Design APIs with predictable rate limits and batching endpoints to reduce overhead. Document data lineage: indicate when data is fetched, normalized, or transformed so model training and validation remain auditable.
Tools that combine real-time prices, on-chain insights, and signal generation can accelerate prototyping of analytics and agents. For example, Token Metrics provides AI-driven research and analytics that teams can evaluate as part of their data stack when building integrations.
Build Smarter Crypto Apps & AI Agents with Token Metrics
Token Metrics provides real-time prices, trading signals, and on-chain insights all from one powerful API. Grab a Free API Key
REST is an architectural style that leverages HTTP methods and resource-oriented URIs. It differs from RPC and SOAP by emphasizing uniform interfaces, statelessness, and resource representations. GraphQL is query-oriented and allows clients to request specific fields, which can reduce over-fetching but requires different server-side handling.
Use TLS for transport security, strong authentication (OAuth2, API keys, or mTLS), authorization checks on each endpoint, input validation, rate limiting, and monitoring. Consider short-lived tokens and revoke mechanisms for compromised credentials.
Adopt explicit versioning (path segments like /v1/), maintain backward compatibility when possible, and provide clear deprecation notices with migration guides. Use semantic versioning for client libraries and contract-first changes to minimize breaking updates.
Implement rate limits per API key or token, and communicate limits via headers (e.g., X-RateLimit-Remaining). Provide exponential backoff guidance for clients and consider burst allowances for intermittent workloads. Monitor usage patterns to adjust thresholds.
Essential practices include unit and contract tests, integration tests, load tests, structured logging, distributed tracing, and alerting on error rates or latency SLA breaches. Health checks and automated failover strategies improve availability.
This article is for educational and informational purposes only. It does not constitute investment, financial, or legal advice. Evaluate third-party tools and data sources independently and consider compliance requirements relevant to your jurisdiction and project.

%201.svg)
%201.svg)
The digital transformation of industries worldwide has positioned REST APIs as the fundamental building blocks of modern software architecture. From cryptocurrency trading platforms to enterprise applications, REST APIs enable seamless communication between disparate systems, allowing developers to build sophisticated applications that leverage data and functionality from multiple sources. This comprehensive guide delves into the intricate world of REST API design, security protocols, performance optimization, testing methodologies, and emerging AI-assisted tooling that is revolutionizing how developers build and maintain APIs.
Creating a robust REST API begins with understanding the architectural principles that make RESTful services elegant and maintainable. The concept of resource-oriented design stands at the core of REST architecture, where every piece of data or functionality is treated as a resource accessible through a unique identifier. In the context of cryptocurrency APIs, this means representing digital assets, blockchain transactions, market data, and trading pairs as distinct resources that clients can interact with through standard HTTP methods.
The principle of statelessness in REST API design ensures that each request contains all necessary information for the server to process it, without relying on stored session data. This architectural decision brings significant advantages in scalability and reliability, making it ideal for high-traffic applications like crypto trading platforms where thousands of concurrent users might be accessing market data simultaneously. Token Metrics has built its cryptocurrency API infrastructure on these principles, ensuring that developers can access real-time crypto market data, token analytics, and AI-driven insights through a stateless, scalable interface that handles millions of requests efficiently.
Uniform interface constraints define how clients interact with REST APIs, creating predictability and reducing the learning curve for developers. This uniformity manifests through consistent use of HTTP methods, standardized response formats, and logical URI structures. When designing endpoints for a blockchain API, maintaining this uniformity means that developers can intuitively understand how to query different cryptocurrency data sources without consulting extensive documentation for each endpoint. The self-descriptive nature of well-designed REST APIs allows messages to contain sufficient information about how to process them, reducing coupling between clients and servers.
Security in REST API development transcends basic authentication to encompass a comprehensive defense strategy that protects against evolving threats. Modern REST APIs, especially those handling cryptocurrency transactions and blockchain data, must implement multiple layers of security to safeguard sensitive information and prevent unauthorized access. Token-based authentication using JSON Web Tokens has become the industry standard, providing a secure, stateless mechanism for verifying user identity across multiple requests without maintaining server-side session storage.
The implementation of OAuth 2.0 authorization frameworks adds another dimension of security, particularly relevant for crypto APIs that need to grant third-party applications limited access to user data. This protocol allows users to authorize trading bots or portfolio management tools to access their cryptocurrency holdings or execute trades without sharing their primary credentials. Token Metrics implements enterprise-grade security protocols in its crypto API, ensuring that developers and institutional clients can access sensitive market analytics and trading signals while maintaining the highest standards of data protection.
API key management forms a critical component of REST API security, requiring careful consideration of key generation, rotation, and revocation strategies. For cryptocurrency APIs where unauthorized access could lead to financial losses, implementing rate limiting per API key prevents abuse and ensures fair resource allocation. Combining API keys with IP whitelisting provides an additional security layer, particularly valuable for institutional clients accessing crypto market data through automated systems. The principle of least privilege should guide permission assignments, granting API consumers only the access levels necessary for their specific use cases.
Encryption must extend beyond just transport layer security to encompass data at rest and in transit. While HTTPS encryption protects data during transmission, sensitive information stored in databases or cache systems requires encryption at the application level. For blockchain APIs handling wallet addresses, private transaction data, or user credentials, implementing field-level encryption ensures that even if storage systems are compromised, the data remains protected. Token Metrics employs comprehensive encryption strategies across its crypto API infrastructure, protecting proprietary algorithms, user data, and sensitive market intelligence.
Performance optimization separates adequate REST APIs from exceptional ones, particularly in environments like cryptocurrency trading where milliseconds can impact profitability. Implementing intelligent caching strategies stands as one of the most effective performance improvements, reducing database load and accelerating response times. For crypto APIs serving market data, distinguishing between frequently changing data like current prices and relatively stable data like historical records allows for optimized cache invalidation strategies that balance freshness with performance.
Database query optimization directly impacts REST API response times, making it essential to design efficient queries and proper indexing strategies. When building cryptocurrency APIs that aggregate data from multiple blockchain networks, implementing connection pooling and query result caching prevents redundant database operations. Token Metrics optimizes its crypto API infrastructure to deliver real-time cryptocurrency prices, token ratings, and market analytics with minimal latency, leveraging sophisticated caching mechanisms and database optimization techniques that ensure traders and developers receive time-sensitive information promptly.
Content delivery networks and edge caching bring API responses closer to end users, reducing latency for globally distributed applications. This becomes particularly important for cryptocurrency applications where users trade digital assets from around the world and require consistent, fast access to market data. Implementing CDN strategies for static API responses and using edge computing for dynamic content generation ensures that crypto APIs maintain low latency regardless of user location.
Pagination and data filtering strategies prevent REST APIs from becoming overwhelmed by large dataset requests. Rather than forcing clients to download thousands of cryptocurrency listings or blockchain transactions in a single request, implementing cursor-based pagination with configurable page sizes allows efficient data retrieval. Supporting query parameters for filtering, sorting, and field selection enables clients to request exactly the data they need, reducing bandwidth consumption and improving response times. These optimization techniques become crucial when building crypto analytics APIs that might need to serve historical price data spanning years of market activity.
Testing REST APIs requires a multi-layered approach that validates functionality, performance, security, and reliability under various conditions. Unit testing individual API endpoints ensures that each component behaves correctly in isolation, validating request parsing, business logic execution, and response formatting. For cryptocurrency APIs, unit tests must verify that price calculations, trading signal generation, and blockchain data parsing functions correctly across different market conditions and edge cases.
Integration testing validates how different API components work together and how the API interacts with external systems like databases, blockchain nodes, and third-party services. When building crypto APIs that aggregate data from multiple exchanges or blockchain networks, integration tests ensure that data synchronization, error handling, and failover mechanisms function correctly. Token Metrics maintains rigorous testing protocols for its cryptocurrency API, ensuring that developers receive accurate, reliable market data and analytics even when individual data sources experience disruptions.
Load testing and stress testing reveal how REST APIs perform under high traffic conditions, identifying bottlenecks and scalability limitations before they impact production users. For crypto trading APIs where market volatility can trigger massive spikes in request volume, understanding system behavior under load becomes critical. Simulating scenarios where thousands of users simultaneously query cryptocurrency prices or execute trades helps identify resource constraints and optimize system architecture for peak performance.
Security testing encompasses vulnerability assessments, penetration testing, and continuous monitoring for emerging threats. Automated security scanners can identify common vulnerabilities like SQL injection, cross-site scripting, and authentication bypasses, while manual penetration testing uncovers more sophisticated security weaknesses. For blockchain APIs handling financial transactions, regular security audits ensure that the API maintains protection against evolving attack vectors and complies with industry security standards.
Artificial intelligence is transforming how developers design, build, and maintain REST APIs, offering capabilities that streamline development workflows and improve code quality. AI-powered code generation tools can create boilerplate API code, reducing repetitive tasks and allowing developers to focus on business logic implementation. When building cryptocurrency APIs, AI assistants can generate endpoint definitions, request validators, and response serializers based on specifications, accelerating development timelines significantly.
Intelligent API documentation generation leverages AI to analyze code and automatically produce comprehensive documentation that stays synchronized with implementation. Rather than manually writing and updating API documentation as endpoints evolve, AI tools can extract information from code comments, type definitions, and tests to generate interactive documentation. This capability proves invaluable for crypto API providers like Token Metrics, where maintaining accurate documentation across hundreds of endpoints covering various aspects of cryptocurrency market data, blockchain analytics, and trading signals becomes a substantial undertaking.
AI-driven testing and quality assurance tools automatically generate test cases, identify edge cases, and predict potential failure scenarios based on API specifications and historical data. Machine learning models trained on common API vulnerabilities can proactively identify security weaknesses during development, preventing issues before they reach production. For cryptocurrency APIs where security vulnerabilities could lead to financial losses, AI-assisted security testing provides an additional layer of protection beyond traditional manual code reviews.
Natural language processing enables developers to interact with APIs using conversational interfaces, querying crypto market data or executing API operations through chat-like interactions. This technology reduces the learning curve for new developers and enables faster prototyping and experimentation. Token Metrics continues exploring AI-assisted tools and interfaces that make accessing cryptocurrency analytics and market intelligence more intuitive for developers, traders, and analysts.
Effective versioning strategies ensure that REST APIs can evolve without breaking existing integrations, a critical consideration for cryptocurrency APIs where trading bots and automated systems depend on consistent endpoints. Implementing version numbers in URL paths provides explicit versioning that makes it clear which API version clients are accessing. The approach of maintaining multiple active API versions simultaneously allows legacy clients to continue functioning while new clients adopt enhanced features and improved architectures.
Deprecation policies and communication strategies guide clients through API transitions, providing adequate time and resources for migration. For crypto APIs, announcing deprecations well in advance and offering migration guides helps developers transition their trading systems and applications without disruption. Token Metrics maintains clear versioning and deprecation policies for its cryptocurrency API, ensuring that clients have stable, reliable access to market data while the platform continues evolving with new features and capabilities.
Backward compatibility considerations influence how API changes are implemented, distinguishing between additive changes that don't break existing clients and breaking changes that require version increments. Adding new fields to API responses typically maintains backward compatibility, while removing fields or changing response structures constitutes breaking changes requiring careful management. For blockchain APIs, maintaining backward compatibility becomes particularly important when integrating new blockchain protocols or cryptocurrency assets into existing data structures.
Comprehensive monitoring transforms raw API metrics into actionable insights that guide optimization efforts and operational decisions. Tracking key performance indicators like response times, error rates, request volumes, and throughput provides visibility into API health and user behavior patterns. For cryptocurrency APIs experiencing traffic spikes during market volatility, real-time monitoring enables rapid response to performance degradation or system issues before they significantly impact users.
Distributed tracing provides end-to-end visibility into request flows through complex API architectures, identifying bottlenecks and dependencies that impact performance. When a crypto API aggregates data from multiple blockchain networks and external services, distributed tracing reveals which components contribute most to overall latency, guiding optimization priorities. Token Metrics employs sophisticated monitoring and observability tools across its crypto API infrastructure, ensuring that issues are detected and resolved quickly to maintain reliable access to critical cryptocurrency market data.
Analytics platforms aggregate API usage data to reveal consumption patterns, popular endpoints, and opportunities for optimization or new feature development. Understanding how developers use a cryptocurrency API informs roadmap decisions, helping prioritize enhancements that deliver maximum value. Analyzing which crypto assets, trading pairs, or analytical endpoints receive the most requests helps guide infrastructure scaling and caching strategies.
Outstanding API documentation serves as the primary interface between API providers and developers, significantly impacting adoption and successful integration. Comprehensive documentation goes beyond simple endpoint listings to include conceptual overviews, authentication guides, code samples in multiple programming languages, and common use case tutorials. For cryptocurrency APIs, documentation should address specific scenarios like retrieving real-time market data, analyzing token metrics, backtesting trading strategies, and integrating blockchain transaction data.
Interactive documentation tools enable developers to experiment with API endpoints directly from the documentation interface, dramatically reducing the time from discovery to first successful API call. Providing pre-configured examples for common cryptocurrency queries allows developers to see immediate results and understand response structures without writing code. Token Metrics offers extensive API documentation covering its comprehensive cryptocurrency analytics platform, including detailed guides for accessing token grades, market predictions, sentiment analysis, and technical indicators through the REST API.
SDK development in popular programming languages abstracts away HTTP request handling and response parsing, providing developers with native language interfaces to API functionality. Offering officially supported SDKs for Python, JavaScript, Java, and other languages accelerates integration and reduces implementation errors. For crypto APIs, SDKs can handle authentication, request signing, rate limiting, and error retry logic automatically, allowing developers to focus on building their applications rather than managing HTTP communications.
Robust error handling distinguishes professional REST APIs from amateur implementations, particularly critical for cryptocurrency applications where clear error messages enable developers to quickly diagnose and resolve issues. Implementing standardized error response formats with descriptive error codes, human-readable messages, and actionable guidance helps developers troubleshoot problems efficiently. For crypto APIs, distinguishing between client errors like invalid cryptocurrency symbols and server errors like blockchain node connectivity issues enables appropriate error recovery strategies.
Circuit breaker patterns prevent cascading failures when external dependencies like blockchain nodes or data providers experience outages. Implementing intelligent retry logic with exponential backoff ensures that transient errors don't unnecessarily fail API requests while preventing retry storms that could overwhelm recovering systems. Token Metrics builds resilience into its cryptocurrency API infrastructure, implementing sophisticated error handling and retry mechanisms that maintain service availability even when individual data sources experience disruptions.
Graceful degradation strategies allow APIs to continue serving requests with reduced functionality when certain features or data sources become unavailable. For blockchain APIs that aggregate data from multiple networks, implementing fallback mechanisms ensures that if one blockchain node becomes unreachable, the API can still serve data from available sources. This approach maintains partial functionality rather than complete failure, providing better user experience during system disruptions.
Implementing intelligent rate limiting protects REST APIs from abuse while ensuring fair resource allocation among all users. Token bucket algorithms provide flexible rate limiting that accommodates burst traffic while maintaining average rate constraints, ideal for cryptocurrency APIs where market events can trigger sudden request spikes. Differentiating rate limits by authentication tier enables free users to explore the API while encouraging heavy users to upgrade to paid plans with higher limits.
Dynamic throttling adjusts rate limits based on system load and resource availability, automatically tightening limits during high traffic periods and relaxing them during normal operations. For crypto trading APIs where market volatility correlates with request volume, dynamic throttling prevents system overload while maintaining service for all users. Token Metrics implements sophisticated rate limiting across its cryptocurrency API tiers, balancing accessibility for developers with the need to maintain system stability and performance under varying load conditions.
Rate limit communication through response headers informs clients about their current consumption, remaining quota, and reset times, enabling intelligent request scheduling and avoiding unnecessary throttling. Providing these details helps developers building cryptocurrency trading systems optimize their API usage patterns and avoid interruptions during critical market moments.
Microservices architecture demonstrates how REST APIs enable building complex systems from loosely coupled, independently deployable services. In cryptocurrency platforms, separating market data services, trading execution engines, analytics processors, and user management into distinct microservices connected through REST APIs creates flexible, scalable systems. Each microservice can be developed, deployed, and scaled independently, allowing teams to iterate rapidly and respond to changing requirements.
Event-driven architectures combine REST APIs with asynchronous messaging systems, enabling real-time updates and reactive systems that respond to market events. For cryptocurrency applications, publishing blockchain events, price updates, and trading signals to message queues allows multiple consumers to process events concurrently. Token Metrics leverages event-driven patterns in its crypto API infrastructure, delivering real-time market intelligence and trading signals to subscribers while maintaining system scalability and responsiveness.
API gateway patterns centralize cross-cutting concerns like authentication, rate limiting, logging, and request routing, simplifying individual service implementations. For blockchain API platforms that aggregate data from multiple sources, API gateways provide a unified entry point that handles authentication once and routes requests to appropriate backend services. This architecture reduces code duplication and ensures consistent security policies across all API endpoints.
The evolution of blockchain technology and decentralized systems presents new opportunities and challenges for REST API design. Web3 applications require APIs that bridge traditional REST interfaces with blockchain interactions, enabling developers to build applications that leverage decentralized protocols without managing blockchain nodes directly. REST APIs that provide simplified interfaces to complex smart contracts, DeFi protocols, and NFT marketplaces will continue growing in importance as the cryptocurrency ecosystem matures.
GraphQL and alternative API paradigms offer different approaches to data fetching, addressing some limitations of traditional REST APIs. While REST remains the dominant standard, understanding how complementary technologies can enhance cryptocurrency API capabilities helps developers choose the right tool for each use case. Token Metrics continues innovating in the crypto API space, exploring emerging technologies and paradigms that can improve how developers access and analyze cryptocurrency market data.
Artificial intelligence integration within REST APIs themselves represents a frontier where APIs become more intelligent and adaptive. Machine learning models embedded in cryptocurrency APIs can personalize responses, predict user needs, and provide proactive alerts based on individual trading patterns and preferences. The convergence of AI capabilities with traditional REST API architectures creates powerful new possibilities for delivering value to developers and end users.
Mastering REST API design, security, and best practices requires understanding both fundamental principles and advanced implementation techniques. From authentication and encryption to performance optimization and testing strategies, each aspect contributes to building APIs that developers trust and rely on for their applications. The emergence of AI-assisted tooling accelerates development workflows while improving code quality, enabling teams to build more sophisticated APIs in less time.
In the cryptocurrency industry, REST APIs serve as the critical infrastructure connecting developers to blockchain data, market intelligence, and trading functionality. Token Metrics exemplifies excellence in crypto API design, providing comprehensive cryptocurrency analytics, AI-driven insights, and real-time market data through a secure, performant, and well-documented RESTful interface. Whether building new blockchain applications, developing trading systems, or integrating cryptocurrency data into existing platforms, applying these REST API best practices and leveraging powerful crypto APIs like those offered by Token Metrics accelerates development and enhances application capabilities.
As technology continues advancing and the cryptocurrency ecosystem evolves, REST APIs will adapt and improve while maintaining the core principles of simplicity, scalability, and reliability that have made them the foundation of modern web architecture. Developers who invest in mastering REST API design and implementation position themselves to build the next generation of innovative applications that shape our increasingly connected digital future.
%201.svg)
%201.svg)
REST API technology underpins much of today’s web, mobile, and AI-driven systems. Understanding REST fundamentals, design trade-offs, and operational patterns helps engineers build reliable integrations that scale, remain secure, and are easy to evolve. This article breaks down the core concepts, practical design patterns, and concrete steps to integrate REST APIs with AI and data platforms.
REST (Representational State Transfer) is an architectural style for distributed systems that uses standard HTTP methods to operate on resources. A REST API exposes resources—such as users, orders, or sensor readings—via predictable endpoints and leverages verbs like GET, POST, PUT, PATCH, and DELETE. Key characteristics include statelessness, resource-based URIs, and standardized status codes. These conventions make REST APIs easy to consume across languages, frameworks, and platforms.
Good REST API design balances clarity, stability, and flexibility. Consider these practical principles:
Document endpoints using OpenAPI/Swagger and provide sample requests/responses. Clear documentation reduces integration time and surface area for errors.
Security and observability are central to resilient APIs. Common patterns include:
Operational readiness often separates reliable APIs from fragile ones. Integrate logging and alerting into deployment pipelines and validate SLAs with synthetic checks.
APIs should be treated as products with release processes and compatibility guarantees. Recommended practices:
Following a disciplined lifecycle reduces friction for integrators and supports long-term maintainability.
REST APIs serve as the connective tissue between data sources and AI/analytics systems. Patterns to consider:
AI-driven research platforms and data providers expose REST APIs to make on-chain, market, and derived signals available to models. For example, AI-driven research tools such as Token Metrics provide structured outputs that can be integrated into feature stores and experimentation platforms.
Build Smarter Crypto Apps & AI Agents with Token Metrics
Token Metrics provides real-time prices, trading signals, and on-chain insights all from one powerful API. Grab a Free API Key
REST is an architectural style that uses HTTP and resource-oriented design. Alternatives include RPC-style APIs, GraphQL (which offers a single flexible query endpoint), and gRPC (binary, high-performance RPC). Choose based on latency, schema needs, and client diversity.
Use token-based authentication (OAuth2 client credentials or API keys), enforce TLS, implement scopes or claims to limit access, and rotate credentials periodically. Apply input validation, rate limits, and monitoring to detect misuse.
Version when making breaking changes to request/response contracts. Prefer semantic versioning and provide both current and deprecated versions in parallel during transition windows to minimize client disruption.
OpenAPI/Swagger for documentation, Postman for manual testing, Pact for contract testing, and CI plugins for schema validation and request/response snapshots are common. Automated tests should cover happy and edge cases.
Use tiered limits with burst capacity, return informative headers (remaining/quota/reset), and provide fallback behavior (cached responses or graceful degradation). Communicate limits in documentation so integrators can design around them.
The information in this article is educational and technical in nature. It is not professional, legal, or financial advice. Readers should perform their own due diligence when implementing systems and choosing vendors.

%201.svg)
%201.svg)
REST APIs power modern web and mobile applications by providing a consistent, scalable way to exchange data. Whether you are integrating microservices, powering single-page apps, or exposing data for third-party developers, understanding REST architecture, design norms, and operational considerations is essential to build reliable services.
Representational State Transfer (REST) is an architectural style that leverages standard HTTP methods to manipulate resources represented as URLs. A REST API typically exposes endpoints that return structured data (commonly JSON) and uses verbs like GET, POST, PUT/PATCH, and DELETE to indicate intent. REST is not a protocol; it is a set of constraints—statelessness, uniform interface, and resource-based modeling—that make APIs predictable and cache-friendly.
When evaluating whether to build a REST API, consider use cases: straightforward CRUD operations, broad client compatibility, and caching benefit from REST. If you need strong typing, real-time streaming, or more efficient batching, compare REST to alternatives like GraphQL, gRPC, or WebSockets before deciding.
Good API design starts with resource modeling and clear, consistent conventions. Practical guidelines include:
These conventions improve discoverability and reduce integration friction for third-party developers and internal teams alike.
Security is a primary operational concern. REST APIs must protect data in transit and enforce access controls. Key controls include:
For teams integrating crypto or blockchain data, AI-driven research platforms can automate risk scanning and anomaly detection. For example, Token Metrics provides analytical signals that teams can cross-reference with on-chain activity when modeling API access patterns.
Operational resilience depends on performance engineering and testing. Practical steps include:
Adopt a measurable SLA approach and define clear error budgets to balance feature velocity and reliability.
Build Smarter Crypto Apps & AI Agents with Token Metrics
Token Metrics provides real-time prices, trading signals, and on-chain insights all from one powerful API. Grab a Free API Key
A REST API is an application programming interface that follows REST constraints. It exposes resources via URIs and uses HTTP methods to perform operations, typically exchanging JSON payloads.
REST emphasizes multiple endpoints and resource-based modeling, while GraphQL provides a single endpoint that lets clients request precisely the fields they need. Choose based on data-fetching patterns, caching needs, and client complexity.
Common methods include OAuth 2.0 for delegated access, JWTs for stateless token-based auth, and API keys for service-to-service calls. Use short-lived tokens and secure storage practices to reduce exposure.
Versioning strategies include URI versioning (/v1/resource), header-based negotiation, or semantic compatibility practices. Aim to minimize breaking changes and provide migration guides for clients.
Combine unit tests, integration tests, contract tests (e.g., using OpenAPI), and end-to-end tests. Include load and chaos testing to validate behavior under stress and partial failures.
Implement retries with exponential backoff, set sensible timeouts, use circuit breakers, and degrade gracefully. Observability (tracing and metrics) is essential to detect and respond to issues quickly.
This article is for educational purposes and technical guidance only. It does not constitute investment advice, recommendations, or endorsements. Evaluate tools and services independently, and follow organizational security and compliance policies when designing and deploying APIs.
%201.svg)
%201.svg)
In today's interconnected digital ecosystem, REST APIs have become the backbone of modern web applications, mobile apps, and data exchange platforms. Whether you're building a cryptocurrency trading platform, integrating blockchain data, or developing any web service, understanding REST API architecture is essential for creating scalable and efficient applications. This comprehensive guide explores REST API design principles, real-world use cases, and best practices that developers need to master.
REST, which stands for Representational State Transfer, is an architectural style that defines a set of constraints for creating web services. A REST API, also known as a RESTful API, allows different software applications to communicate with each other over HTTP protocols. The beauty of REST lies in its simplicity and stateless nature, making it the preferred choice for developers building everything from social media platforms to cryptocurrency APIs.
When a client makes a request to a REST API, it transfers a representation of the state of the requested resource to the client. This representation can be delivered in various formats, with JSON being the most popular choice in modern applications, especially in crypto APIs and blockchain data services. The stateless nature of REST means that each request from a client contains all the information needed to process that request, without relying on stored context on the server.
The foundation of effective REST API design rests on several key components that work together to create a cohesive system. Resources represent the fundamental concept in REST architecture, where everything is considered a resource that can be accessed through a unique identifier known as a URI or Uniform Resource Identifier. For instance, in a cryptocurrency API, resources might include digital assets, market data, trading pairs, or wallet addresses.
HTTP methods form the second pillar of REST API design, providing the verbs that define actions on resources. GET requests retrieve data without modifying it, making them perfect for fetching crypto market data or blockchain information. POST requests create new resources, such as submitting a new transaction or creating a wallet. PUT requests update existing resources completely, while PATCH requests modify specific fields. DELETE requests remove resources from the system. Understanding when to use each method is crucial for building intuitive and predictable APIs.
The URI structure in a well-designed REST API should be logical, consistent, and self-documenting. Rather than using verbs in URLs, REST APIs rely on nouns to represent resources, with HTTP methods conveying the action. For example, a crypto API endpoint might look like /api/v1/cryptocurrencies/bitcoin/price rather than /api/v1/getCryptocurrencyPrice. This approach creates cleaner, more maintainable code that developers can understand intuitively.
Implementing version control in your REST API is not optional but essential for maintaining backward compatibility as your service evolves. Including the version number in the URL path, such as /api/v1/ or /api/v2/, allows you to introduce breaking changes in new versions while supporting legacy clients. This practice is particularly important for cryptocurrency APIs where trading bots and automated systems depend on consistent endpoints.
Authentication and security stand as paramount concerns in REST API development, especially when dealing with sensitive data like cryptocurrency transactions or blockchain information. Token-based authentication using JSON Web Tokens (JWT) has emerged as the industry standard, providing secure, stateless authentication that scales well. For crypto APIs handling financial data, implementing API keys, rate limiting, and encryption becomes non-negotiable to protect user assets and maintain system integrity.
Error handling deserves careful attention in REST API design. Your API should return appropriate HTTP status codes that clearly communicate what happened during request processing. A 200 status indicates success, 201 signifies successful resource creation, 400 indicates a bad request from the client, 401 means unauthorized access, 404 signals that a resource wasn't found, and 500 indicates a server error. Accompanying these status codes with clear, actionable error messages in the response body helps developers debug issues quickly.
The cryptocurrency industry has embraced REST APIs as the primary method for accessing blockchain data, market information, and trading functionality. Crypto APIs built on REST principles enable developers to integrate real-time cryptocurrency prices, historical market data, trading volumes, and blockchain analytics into their applications seamlessly. Token Metrics, a leader in crypto analytics and data services, offers one of the most comprehensive cryptocurrency APIs in the market, providing developers with access to advanced metrics, AI-driven insights, and real-time market data through a well-designed RESTful interface.
When building or consuming crypto APIs, developers must consider the unique challenges of blockchain technology. Cryptocurrency market data requires high-frequency updates due to the volatile nature of digital assets. A robust crypto API must handle thousands of requests per second while maintaining low latency and high availability. Token Metrics addresses these challenges by providing a scalable REST API infrastructure that delivers accurate cryptocurrency data, token ratings, and market analytics to developers, traders, and institutional clients.
The integration of blockchain APIs with REST architecture has opened new possibilities for decentralized applications and financial technology. Developers can now query blockchain transactions, check wallet balances, monitor smart contract events, and access DeFi protocols through simple HTTP requests. This accessibility has accelerated innovation in the crypto space, allowing developers to build sophisticated trading platforms, portfolio trackers, and analytics dashboards without managing blockchain nodes directly.
REST APIs power countless applications across industries, demonstrating their versatility and reliability. In the financial technology sector, cryptocurrency exchanges rely on REST APIs to provide trading functionality to their users. These APIs enable programmatic trading, allowing algorithmic traders to execute strategies, monitor positions, and manage risk across multiple markets. Token Metrics leverages REST API technology to deliver cryptocurrency intelligence, offering endpoints for token grades, trader grades, market predictions, and comprehensive crypto market analysis.
Mobile applications represent another significant use case for REST APIs. Every time you check cryptocurrency prices on your phone, post on social media, or stream music, REST APIs work behind the scenes to fetch and deliver that data. The lightweight nature of REST makes it ideal for mobile environments where bandwidth and battery life are concerns. Crypto portfolio tracking apps, for instance, use REST APIs to aggregate data from multiple exchanges and blockchain networks, presenting users with a unified view of their digital asset holdings.
Enterprise systems increasingly adopt REST APIs for integration and automation. Companies use REST APIs to connect customer relationship management systems, payment processors, inventory databases, and analytics platforms. In the blockchain and cryptocurrency domain, businesses integrate crypto payment APIs to accept digital currencies, use blockchain APIs to verify transactions, and leverage analytics APIs like those offered by Token Metrics to make data-driven investment decisions.
Scalability should be a primary consideration when designing REST APIs, particularly for services that may experience rapid growth or traffic spikes. Implementing pagination for endpoints that return large datasets prevents overwhelming clients and servers. Instead of returning thousands of cryptocurrency listings in a single response, a well-designed crypto API returns a manageable subset along with pagination metadata, allowing clients to request additional pages as needed.
Caching strategies significantly improve REST API performance and reduce server load. By including proper cache-control headers in API responses, you enable clients and intermediary proxies to cache responses appropriately. For cryptocurrency APIs where some data like historical prices rarely changes, aggressive caching can dramatically reduce the number of database queries and API calls. However, real-time data such as current market prices requires careful cache invalidation to ensure accuracy.
Rate limiting protects your REST API from abuse and ensures fair resource allocation among all users. By implementing rate limits based on API keys or IP addresses, you prevent individual clients from monopolizing server resources. Token Metrics implements sophisticated rate limiting in its cryptocurrency API, offering different tiers of access that balance the needs of casual developers, professional traders, and enterprise clients.
Comprehensive documentation transforms a good REST API into a great one. Developers evaluating whether to use your API need clear, accurate documentation that explains endpoints, parameters, authentication methods, and response formats. Interactive API documentation tools like Swagger or Postman collections allow developers to test endpoints directly from the documentation, reducing friction in the integration process.
For cryptocurrency APIs, documentation should include specific examples relevant to the crypto ecosystem. Token Metrics provides extensive API documentation covering everything from basic cryptocurrency price queries to advanced analytics endpoints, complete with code samples in multiple programming languages. This approach accelerates integration and reduces support requests, benefiting both API providers and consumers.
Providing SDKs and client libraries in popular programming languages further improves developer experience. Rather than forcing every developer to handle HTTP requests manually, offering pre-built libraries for Python, JavaScript, Java, and other languages enables faster integration and reduces the likelihood of implementation errors. These libraries can handle authentication, request formatting, error handling, and response parsing automatically.
Once your REST API is in production, ongoing monitoring becomes critical to maintaining quality of service. Implementing comprehensive logging allows you to track API usage patterns, identify performance bottlenecks, and detect anomalies. For cryptocurrency APIs handling financial data, monitoring is especially crucial as downtime or data inaccuracies can result in significant financial losses for users.
Performance metrics such as response times, error rates, and throughput provide insights into API health. Setting up alerts for unusual patterns enables proactive problem resolution before users are significantly affected. Token Metrics maintains rigorous monitoring of its crypto API infrastructure, ensuring that developers and traders have reliable access to critical cryptocurrency market data and analytics.
Maintaining backward compatibility while evolving your API requires careful planning and communication. Deprecation policies should give developers adequate time to migrate to new versions or endpoints. For crypto APIs, this is particularly important as trading bots and automated systems may run unattended for extended periods and need time to adapt to API changes.
Security forms the foundation of trustworthy REST APIs, especially when handling sensitive information like cryptocurrency transactions or personal data. Implementing HTTPS encryption for all API communications prevents man-in-the-middle attacks and protects data in transit. This is non-negotiable for crypto APIs where a single compromised API call could result in unauthorized fund transfers.
Input validation and sanitization protect against injection attacks and malformed requests. Your REST API should validate all incoming data against expected formats and ranges before processing. For cryptocurrency APIs, this includes validating wallet addresses, transaction amounts, and trading parameters to prevent errors and potential exploits.
Implementing proper access controls ensures that authenticated users can only access resources they're authorized to view or modify. Role-based access control (RBAC) provides a flexible framework for managing permissions in complex systems. Token Metrics implements enterprise-grade security in its cryptocurrency API, protecting sensitive market data and ensuring that clients can trust the integrity of the information they receive.
As the cryptocurrency industry continues to mature, REST APIs will remain central to how developers interact with blockchain data and trading platforms. The evolution of decentralized finance, non-fungible tokens, and Web3 applications creates new opportunities and challenges for API design. REST APIs must adapt to handle increasingly complex queries, provide real-time updates for rapidly changing market conditions, and integrate with emerging blockchain protocols.
Token Metrics continues to innovate in the crypto API space, expanding its offerings to include advanced analytics, AI-powered market predictions, and comprehensive blockchain data. By maintaining a robust REST API infrastructure, Token Metrics enables developers, traders, and institutions to build sophisticated cryptocurrency applications that leverage cutting-edge market intelligence.
The convergence of traditional finance and cryptocurrency creates demand for APIs that can bridge both worlds seamlessly. REST APIs that provide unified access to crypto market data, traditional financial information, and cross-market analytics will become increasingly valuable. As regulatory frameworks evolve, APIs will also need to incorporate compliance features, reporting capabilities, and audit trails to meet institutional requirements.
REST APIs have proven themselves as the most practical and widely adopted approach for building web services that are scalable, maintainable, and developer-friendly. Understanding REST API design principles, implementing best practices, and focusing on security and performance creates APIs that developers love to use and rely on for their applications.
In the cryptocurrency space, REST APIs serve as the critical infrastructure that connects developers to blockchain data, market information, and trading functionality. Token Metrics exemplifies how a well-designed crypto API can empower developers and traders with the data and insights they need to succeed in the dynamic digital asset markets. Whether you're building a new cryptocurrency application or integrating blockchain data into existing systems, mastering REST API principles and leveraging powerful crypto APIs like those offered by Token Metrics will accelerate your development and enhance your capabilities.
As technology continues to evolve, REST APIs will adapt and improve, but their fundamental principles of simplicity, scalability, and statelessness will continue to guide the design of systems that power our increasingly connected digital world.

%201.svg)
%201.svg)
APIs are the connective tissue of modern software. Among architectural styles, the REST API remains a dominant approach for exposing resources over HTTP. This article explains what REST APIs are, the principles behind them, practical design patterns, security and testing considerations, and how AI-driven tools can streamline API development and analysis without prescribing decisions.
REST (Representational State Transfer) is an architectural style for distributed systems that emphasizes stateless interactions, resource-oriented URLs, and standard HTTP verbs (GET, POST, PUT, DELETE, etc.). A REST API exposes resources as endpoints that clients can interact with using these verbs and common data formats such as JSON.
REST APIs are well-suited for web and mobile backends, microservices communication, and public developer platforms because they leverage ubiquitous HTTP tooling and are language-agnostic. They are not a one-size-fits-all: scenarios with complex subscriptions, real-time streaming, or highly stateful workflows may benefit from complementary technologies (e.g., WebSockets, gRPC, GraphQL).
Understanding core REST principles helps teams design predictable, maintainable interfaces. Key concepts include:
Architectural patterns to consider:
Practical design choices reduce friction for integrators and improve operational reliability. Consider these tactics:
Security-related best practices include enforcing TLS, validating inputs, and applying the principle of least privilege for resource access. Authentication options commonly used are API keys, OAuth 2.0, and JWTs; select an approach aligned with threat models and compliance needs.
Robust testing and observability are essential for reliable REST APIs. Typical testing layers include unit tests for business logic, integration tests for endpoints, and contract tests against OpenAPI specifications. Synthetic monitoring and instrumentation (tracing, metrics, structured logs) surface latency trends, error spikes, and usage patterns.
AI-driven tools and analytics can accelerate development and maintenance without replacing human judgment. Use cases include:
When integrating AI tools, validate outputs and maintain clear governance: model suggestions should be reviewed, and generated specs must be tested against realistic scenarios.
Build Smarter Crypto Apps & AI Agents with Token Metrics
Token Metrics provides real-time prices, trading signals, and on-chain insights all from one powerful API. Grab a Free API Key
REST describes the architectural principles; "RESTful" is an adjective applied to services that follow those principles. In practice, developers use the terms interchangeably to describe HTTP-based APIs that model resources and use standard verbs.
Versioning strategies include URI versioning (e.g., /v1/resource), header-based versioning, or content negotiation. Choose a consistent approach and document migration paths. Semantic versioning for the API spec and clear deprecation schedules help clients adapt.
Selection depends on use case: API keys are simple for server-to-server calls; OAuth 2.0 provides delegated access for user-centric flows; JWTs enable stateless session tokens. Evaluate threat models, token lifecycle, and revocation needs before choosing.
Introduce retries with exponential backoff, circuit breakers, idempotency keys for write operations, and graceful degradation on dependent service failures. Also, ensure comprehensive monitoring and alerting so operators can react to incidents swiftly.
OpenAPI/Swagger is the de facto standard for API contracts and interactive docs. Postman and Insomnia are popular for exploratory testing; CI-driven contract tests and integration test suites validate expected behavior. Use static analysis and linting (e.g., Spectral) to enforce consistency.
Rate limits protect backend resources and ensure fair usage. Design endpoints so that expensive operations are clearly documented, offer bulk or async endpoints for heavy workloads, and provide clear limit headers so clients can adapt request rates.
Disclaimer: This article is for educational and technical guidance only. It does not provide financial, legal, or investment advice. Implementations should be validated against project requirements, security standards, and applicable regulations.

%201.svg)
%201.svg)
REST APIs power much of the web and modern applications by providing a simple, scalable contract between clients and servers. Whether you're building microservices, mobile backends, or integrations, understanding REST principles, security trade-offs, and operational practices helps you design reliable interfaces that scale. This guide walks through core concepts, design patterns, security essentials, and practical steps to evaluate and implement REST APIs effectively.
REST (Representational State Transfer) is an architectural style for distributed systems. Rather than a strict protocol, REST prescribes patterns: stateless interactions, resource-oriented URIs, and use of standard HTTP methods (GET, POST, PUT, DELETE, PATCH). The result is a predictable API surface that is easy to cache, route, and evolve.
Key benefits include:
Good REST design balances simplicity, clarity, and forward compatibility. Use the following framework when designing endpoints and contracts:
Document expected request/response schemas and examples. Tools like OpenAPI (Swagger) make it easier to generate client libraries and validate contracts.
Security is a non-functional requirement that must be addressed from day one. Common authentication and authorization patterns include:
Practical security measures:
APIs must be reliable in production. Build a test matrix that covers unit tests, contract tests, and end-to-end scenarios. Useful practices include:
Operationally, design for graceful degradation: return useful error payloads, implement retries with exponential backoff on clients, and provide clear SLAs. AI-driven research and API analytics can help prioritize which endpoints to optimize; for example, Token Metrics illustrates how product data combined with analytics surfaces high-impact areas for improvement.
Build Smarter Crypto Apps & AI Agents with Token Metrics
Token Metrics provides real-time prices, trading signals, and on-chain insights all from one powerful API. Grab a Free API Key
REST stands for Representational State Transfer. It describes a set of constraints—stateless interactions, resource-oriented URIs, and uniform interfaces—rather than a wire protocol. Implementations typically use HTTP and JSON.
SOAP is a strict protocol with XML envelopes, formal contracts (WSDL), and built-in features like WS-Security. REST is more flexible and lightweight. GraphQL exposes a single endpoint that allows clients to request specific fields, reducing over-fetching but adding complexity on the server side. Choose based on client needs, tooling, and team expertise.
Common methods include OAuth 2.0 for delegated access, API keys for simple service access, and JWTs for stateless sessions. Each has trade-offs around revocation, token size, and complexity—consider lifecycle and threat models when selecting an approach.
Versioning strategies include path-based (/v1/resource), header-based, or content negotiation. Path-based versioning is the most explicit and easiest for clients. Maintain backward compatibility where possible and provide clear deprecation timelines and migration guides.
OpenAPI (Swagger) for specification and client generation, Postman for exploratory testing, and contract-testing tools like Pact for ensuring compatibility. Load testing tools (k6, JMeter) and observability platforms complete the pipeline for production readiness.
This article is educational and technical in nature. It provides general information about REST API design, security, and operations, not financial, legal, or investment advice. Assess your own requirements and consult appropriate specialists when implementing systems in production.

%201.svg)
%201.svg)
The digital revolution has transformed how applications communicate, with REST APIs emerging as the universal language enabling seamless data exchange across platforms, services, and organizations. From fintech applications to cryptocurrency trading platforms, REST APIs have become the foundational technology powering modern software ecosystems. This comprehensive guide explores the essential principles of REST API design, security frameworks, and best practices that developers need to build production-ready applications that scale efficiently and maintain reliability under demanding conditions.
REST API design begins with understanding the core principle that everything in your system represents a resource accessible through a unique identifier. This resource-oriented approach creates intuitive APIs where URLs describe what you're accessing rather than what action you're performing. In cryptocurrency applications, resources might include digital assets, trading pairs, market data, wallet addresses, or blockchain transactions. Each resource receives a clean, hierarchical URL structure that developers can understand without extensive documentation.
The elegance of REST lies in using HTTP methods to convey operations rather than encoding actions in URLs. Instead of creating endpoints like /getPrice, /updatePrice, or /deletePrice, REST APIs use a single resource URL like /cryptocurrencies/bitcoin/price with different HTTP methods indicating the desired operation. GET retrieves the current price, PUT updates it, and DELETE removes it. This uniform interface reduces cognitive load for developers and creates predictable patterns across your entire API surface.
Resource naming conventions significantly impact API usability and maintainability. Using plural nouns for collections and singular nouns for individual resources creates consistency that developers appreciate. A cryptocurrency market data API might expose /cryptocurrencies for the collection of all digital assets and /cryptocurrencies/ethereum for a specific asset. Avoiding verbs in URLs and maintaining lowercase conventions with hyphens separating words creates clean, professional APIs that reflect well on your organization. Token Metrics exemplifies these design principles in its cryptocurrency API, providing developers with intuitive access to comprehensive crypto analytics, AI-driven market predictions, and real-time blockchain data through thoughtfully designed endpoints.
Hierarchical resource relationships through nested URLs express how resources relate to each other naturally. When resources have clear parent-child relationships, nesting URLs communicates these associations effectively. An API might use /cryptocurrencies/bitcoin/transactions to represent all transactions for Bitcoin or /portfolios/user123/holdings to show a specific user's cryptocurrency holdings. However, excessive nesting beyond two or three levels creates unwieldy URLs and tight coupling between resources. Balancing expressiveness with simplicity ensures your API remains usable as it grows.
Authentication forms the security foundation of any REST API, verifying that clients are who they claim to be before granting access to protected resources. Multiple authentication strategies exist, each suited to different scenarios and security requirements. Understanding these approaches enables you to select appropriate mechanisms for your specific use case, whether building public APIs, internal microservices, or cryptocurrency trading platforms where security directly impacts financial assets.
API key authentication provides the simplest approach for identifying clients, particularly appropriate for server-to-server communication where user context matters less than client application identity. Clients include their API key in request headers, allowing the server to identify, authorize, and track usage. For cryptocurrency APIs, API keys enable rate limiting per client, usage analytics, and graduated access tiers. Token Metrics implements API key authentication across its crypto API offerings, providing developers with different access levels from free exploration tiers to enterprise plans supporting high-volume production applications.
JSON Web Tokens have emerged as the gold standard for modern REST API authentication, offering stateless, secure token-based authentication that scales horizontally. After initial authentication with credentials, the server issues a JWT containing encoded user information and an expiration timestamp, signed with a secret key. Subsequent requests include this token in the Authorization header, allowing the server to verify authenticity without database lookups or session storage. The stateless nature of JWTs aligns perfectly with REST principles and supports distributed architectures common in cryptocurrency platforms handling global traffic.
OAuth 2.0 provides a comprehensive authorization framework particularly valuable when third-party applications need delegated access to user resources without receiving actual credentials. This protocol enables secure scenarios where users authorize trading bots to execute strategies on their behalf, portfolio trackers to access exchange holdings, or analytics tools to retrieve transaction history. The authorization code flow, client credentials flow, and other grant types address different integration patterns while maintaining security boundaries. For blockchain APIs connecting multiple services and applications, OAuth 2.0 provides the flexibility and security needed to support complex integration scenarios.
Multi-factor authentication adds critical security layers for sensitive operations like cryptocurrency withdrawals, trading authorization, or API key generation. Requiring additional verification beyond passwords through time-based one-time passwords, SMS codes, or biometric authentication significantly reduces unauthorized access risk. For crypto APIs where compromised credentials could lead to substantial financial losses, implementing MFA for high-risk operations represents essential security hygiene rather than optional enhancement.
Authorization determines what authenticated clients can do, establishing granular permissions that protect sensitive resources and operations. Role-based access control assigns users to roles with predefined permission sets, simplifying permission management in applications with many users. A cryptocurrency trading platform might define roles like basic users who can view data but not trade, active traders who can execute market orders, premium traders with access to advanced order types, and administrators with full system access.
Attribute-based access control provides more dynamic, fine-grained authorization based on user attributes, resource properties, and environmental context. Rather than static role assignments, ABAC evaluates policies considering multiple factors. A crypto API might allow trading only during market hours, restrict large transactions to verified accounts, or limit certain cryptocurrency access based on geographic regulations. This flexibility proves valuable in blockchain applications where regulatory compliance and risk management require sophisticated access controls.
Scope-based authorization commonly appears in OAuth 2.0 implementations, where clients request specific permission scopes during authorization. Users explicitly grant applications access to particular capabilities like reading portfolio data, executing trades, or managing API keys. This granular consent model gives users control over what applications can do on their behalf while enabling applications to request only the permissions they need. Token Metrics implements scope-based authorization in its cryptocurrency API, allowing developers to request appropriate access levels for their specific use cases.
Resource-level permissions provide the finest granularity, controlling access to individual resources based on ownership or explicit grants. Users might manage their own portfolios but not others, view public cryptocurrency data but not private trading strategies, or access shared analytics dashboards while protecting proprietary models. Implementing resource-level authorization requires careful database query design and caching strategies to maintain performance while enforcing security boundaries.
Transport layer security through HTTPS encryption represents the absolute minimum security requirement for production REST APIs. TLS encryption protects data in transit from eavesdropping and tampering, preventing attackers from intercepting sensitive information like authentication credentials, trading signals, or portfolio holdings. For cryptocurrency APIs where intercepted data could enable front-running attacks or credential theft, HTTPS is non-negotiable. Modern security standards recommend TLS 1.3, which offers improved performance and stronger security compared to earlier versions.
Certificate management ensures that clients can verify server identity and establish encrypted connections securely. Obtaining certificates from trusted certificate authorities, implementing proper certificate rotation, and monitoring expiration prevents security gaps. Implementing HTTP Strict Transport Security headers instructs browsers to always use HTTPS when communicating with your API, preventing protocol downgrade attacks. For crypto APIs handling financial transactions, proper certificate management and HTTPS enforcement protect user assets from various attack vectors.
Sensitive data encryption at rest protects information stored in databases, cache systems, and backups. While transport encryption protects data during transmission, at-rest encryption ensures that compromised storage systems don't expose sensitive information. For blockchain APIs storing user credentials, private keys, or proprietary trading algorithms, field-level encryption provides defense-in-depth security. Encryption key management becomes critical, requiring secure key storage, regular rotation, and access controls preventing unauthorized decryption.
API request signing provides additional security beyond HTTPS by creating message authentication codes that verify request integrity and authenticity. Clients sign requests using secret keys, generating signatures that servers validate before processing. This approach prevents replay attacks where attackers intercept and retransmit valid requests, particularly important for cryptocurrency trading APIs where replayed orders could cause unintended financial consequences. Amazon's AWS Signature Version 4 and similar schemes provide proven implementations of request signing that resist tampering.
Input validation protects REST APIs from malicious or malformed data that could compromise security or system stability. Validating all incoming data against expected formats, ranges, and constraints should occur at multiple layers from initial request parsing through business logic execution. For cryptocurrency APIs, validation ensures that addresses conform to blockchain-specific formats, trading quantities fall within acceptable ranges, and order prices represent reasonable values preventing erroneous transactions.
Type validation confirms that data matches expected types before processing. String fields should contain strings, numeric fields should contain numbers, and boolean fields should contain true or false values. While this seems obvious, weakly-typed languages and JSON's flexibility create opportunities for type confusion attacks. Cryptocurrency APIs must validate that price fields contain numbers not strings, ensuring mathematical operations execute correctly and preventing injection attacks through type confusion.
Format validation uses regular expressions and parsing logic to verify that data adheres to expected patterns. Email addresses should match email patterns, dates should parse correctly, and cryptocurrency addresses should conform to blockchain-specific formats with proper checksums. Comprehensive format validation catches errors early in request processing, providing clear feedback to clients about what went wrong rather than allowing malformed data to propagate through your system causing mysterious failures.
Range and constraint validation ensures that numeric values fall within acceptable bounds and that data satisfies business rules. Trading quantities should exceed minimum order sizes, prices should remain within reasonable bounds, and dates should fall in valid ranges. For crypto APIs, validating that transaction amounts don't exceed available balances or daily withdrawal limits prevents errors and potential fraud. Implementing validation at API boundaries protects downstream systems from invalid data and provides clear error messages guiding clients toward correct usage.
Sanitization removes or escapes potentially dangerous characters from input data, preventing injection attacks that exploit insufficient input handling. SQL injection, NoSQL injection, and cross-site scripting attacks all exploit inadequate sanitization. While parameterized queries and prepared statements provide primary defense against injection attacks, sanitizing input provides additional protection. For cryptocurrency APIs accepting user-generated content like trading notes or portfolio labels, proper sanitization prevents malicious scripts from compromising other users.
Rate limiting protects REST APIs from abuse, ensures fair resource allocation, and prevents individual clients from degrading service quality for others. Implementing effective rate limiting requires balancing accessibility with protection, allowing legitimate use while blocking malicious actors. Different rate limiting algorithms address different requirements and scenarios, enabling API providers to tailor protection strategies to their specific needs and traffic patterns.
Fixed window rate limiting counts requests within discrete time periods like minutes or hours, resetting counters at period boundaries. This straightforward approach makes limits easy to communicate and implement but allows traffic bursts at window boundaries. A client limited to 1000 requests per hour could send 1000 requests just before the hour boundary and another 1000 immediately after, effectively doubling the intended limit momentarily. Despite this limitation, fixed window algorithms remain popular due to their simplicity and low overhead.
Sliding window rate limiting tracks requests over rolling time periods, providing smoother traffic distribution without boundary burst issues. Rather than resetting at fixed intervals, sliding windows consider requests made during the previous N seconds when evaluating new requests. This approach provides more consistent rate limiting but requires tracking individual request timestamps, increasing memory overhead. For cryptocurrency APIs where smooth traffic distribution prevents system overload during market volatility, sliding window algorithms provide better protection than fixed window alternatives.
Token bucket algorithms offer the most flexible rate limiting by maintaining a bucket of tokens that refill at a steady rate. Each request consumes a token, and requests arriving when the bucket is empty are rejected or delayed. The bucket capacity determines burst size, while the refill rate controls sustained throughput. This approach allows brief traffic bursts while maintaining long-term rate constraints, ideal for cryptocurrency APIs where legitimate users might need to make rapid requests during market events while maintaining overall usage limits. Token Metrics implements sophisticated token bucket rate limiting across its crypto API tiers, balancing burst capacity with sustained rate controls that protect system stability while accommodating real-world usage patterns.
Distributed rate limiting becomes necessary when APIs run across multiple servers and rate limits apply globally rather than per server. Implementing distributed rate limiting requires shared state typically stored in Redis or similar fast data stores. Servers check and update request counts in shared storage before processing requests, ensuring that clients cannot bypass limits by distributing requests across servers. For global cryptocurrency APIs serving traffic from multiple geographic regions, distributed rate limiting ensures consistent enforcement regardless of which servers handle requests.
Comprehensive error handling transforms frustrating integration experiences into smooth developer workflows by providing clear, actionable feedback when things go wrong. Well-designed error responses include HTTP status codes indicating general error categories, application-specific error codes identifying particular failures, human-readable messages explaining what happened, and actionable guidance suggesting how to resolve issues. This multi-layered approach enables both automated error handling and developer troubleshooting.
HTTP status codes provide the first level of error information, with standardized meanings that clients and intermediaries understand. The 400 series indicates client errors where modifying the request could lead to success. A 400 status indicates malformed requests, 401 signals missing or invalid authentication, 403 indicates insufficient permissions, 404 means the requested resource doesn't exist, 422 suggests validation failures, and 429 signals rate limit violations. The 500 series indicates server errors where the client cannot directly resolve the problem, with 500 representing generic server errors, 502 indicating bad gateway responses, 503 signaling service unavailability, and 504 indicating gateway timeouts.
Application-specific error codes provide finer granularity than HTTP status codes alone, identifying particular error conditions that might share the same HTTP status. A cryptocurrency API might return 400 Bad Request for both invalid cryptocurrency symbols and malformed wallet addresses, but distinct error codes like INVALID_SYMBOL and MALFORMED_ADDRESS enable clients to implement specific handling for each scenario. Documenting error codes thoroughly helps developers understand what errors mean and how to handle them appropriately.
Error message design balances technical accuracy with user-friendliness, providing enough detail for debugging without exposing sensitive implementation details. Error messages should explain what went wrong without revealing database schemas, internal logic, or security mechanisms. For crypto trading APIs, an error message might indicate "Insufficient funds for trade execution" rather than exposing account balances or database table names. Including request identifiers in error responses enables support teams to locate corresponding server logs when investigating issues.
Validation error responses benefit from structured formats listing all validation failures rather than failing on the first error. When clients submit complex requests with multiple fields, reporting all validation failures simultaneously enables fixing everything in one iteration rather than discovering issues one at a time. For cryptocurrency APIs accepting trading orders with multiple parameters, comprehensive validation responses accelerate integration by surfacing all requirements upfront.
Pagination prevents REST APIs from overwhelming clients and servers with massive response payloads, enabling efficient retrieval of large datasets. Different pagination strategies offer varying tradeoffs between simplicity, consistency, and performance. Selecting appropriate pagination approaches based on data characteristics and client needs ensures optimal API usability and performance.
Offset-based pagination using limit and offset parameters provides the most intuitive approach, mapping directly to SQL LIMIT and OFFSET clauses. Clients specify how many results they want and how many to skip, enabling direct access to arbitrary pages. A cryptocurrency API might support /cryptocurrencies?limit=50&offset=100 to retrieve the third page of 50 cryptocurrencies. However, offset-based pagination suffers from consistency issues when underlying data changes between page requests, potentially showing duplicate or missing results. Performance degrades with large offsets as databases must scan and skip many rows.
Cursor-based pagination addresses consistency and performance limitations by returning opaque tokens identifying positions in result sets. Clients include cursor tokens from previous responses when requesting subsequent pages, enabling databases to resume efficiently from exact positions. For cryptocurrency APIs streaming blockchain transactions or market trades, cursor-based pagination provides consistent results even as new data arrives continuously. The opaque nature of cursors prevents clients from manipulating pagination or accessing arbitrary pages, which may be desirable for security or business reasons.
Page-based pagination abstracts away implementation details by simply numbering pages and allowing clients to request specific page numbers. This user-friendly approach works well for frontend applications where users expect page numbers but requires careful implementation to maintain consistency. Token Metrics implements efficient pagination across its cryptocurrency API endpoints, enabling developers to retrieve comprehensive market data, historical analytics, and blockchain information in manageable chunks that don't overwhelm applications or network connections.
Filtering capabilities enable clients to narrow result sets to exactly the data they need, reducing bandwidth consumption and improving performance. Supporting filter parameters for common search criteria allows precise queries without creating specialized endpoints for every possible combination. A crypto market data API might support filters like ?marketcap_min=1000000000&volume_24h_min=10000000&category=DeFi to find large DeFi tokens meeting minimum trading volume requirements. Designing flexible filtering systems requires balancing expressiveness with complexity and security.
API versioning enables continuous improvement without breaking existing integrations, critical for long-lived APIs supporting diverse client applications that cannot all update simultaneously. Thoughtful versioning strategies balance backward compatibility with forward progress, allowing innovation while maintaining stability. Different versioning approaches offer distinct advantages and tradeoffs worth considering carefully.
URI path versioning embeds version identifiers directly in endpoint URLs, providing maximum visibility and simplicity. Endpoints like /api/v1/cryptocurrencies and /api/v2/cryptocurrencies make versions explicit and discoverable. This approach integrates naturally with routing frameworks, simplifies testing by allowing multiple versions to coexist, and makes version selection obvious from URLs alone. For cryptocurrency APIs where trading bots and automated systems depend on stable endpoints, URI versioning provides the clarity and simplicity that reduces integration risk.
Header-based versioning places version identifiers in custom headers or content negotiation headers, keeping URLs clean and emphasizing that versions represent different representations of the same resource. Clients might specify versions through headers like API-Version: 2 or Accept: application/vnd.tokenmetrics.v2+json. While aesthetically appealing and aligned with REST principles, header-based versioning reduces discoverability and complicates testing since headers are less visible than URL components. For cryptocurrency APIs used primarily through programmatic clients rather than browsers, the visibility benefits of URI versioning often outweigh the aesthetic appeal of header-based approaches.
Breaking versus non-breaking changes determine when version increments become necessary. Adding new fields to responses, introducing new optional request parameters, or creating new endpoints represent non-breaking changes that don't require version bumps. Removing response fields, making optional parameters required, changing response structures, or modifying authentication schemes constitute breaking changes requiring new versions. Token Metrics maintains careful versioning discipline in its cryptocurrency API, ensuring that developers can rely on stable endpoints while the platform continuously evolves with new data sources, analytics capabilities, and market insights.
Deprecation policies communicate version sunset timelines, providing clients adequate warning to plan migrations. Responsible API providers announce deprecations months in advance, provide migration guides documenting changes, offer parallel version operation during transition periods, and communicate clearly through multiple channels. For crypto APIs where unattended trading systems might run for extended periods, generous deprecation windows prevent unexpected failures that could cause missed opportunities or financial losses.
Outstanding documentation transforms capable APIs into beloved developer tools by reducing friction from discovery through production deployment. Documentation serves multiple audiences including developers evaluating whether to use your API, engineers implementing integrations, and troubleshooters investigating issues. Addressing all these needs requires comprehensive documentation spanning multiple formats and detail levels.
Getting started guides walk developers through initial integration steps, from account creation and API key generation through making first successful API calls. For cryptocurrency APIs, getting started guides might demonstrate retrieving Bitcoin prices, analyzing token metrics, or querying blockchain transactions. Including complete, working code examples in multiple programming languages accelerates initial integration dramatically. Token Metrics provides extensive getting started documentation for its crypto API, helping developers quickly access powerful cryptocurrency analytics and market intelligence through straightforward examples.
Endpoint reference documentation comprehensively documents every API endpoint including URLs, HTTP methods, authentication requirements, request parameters, response formats, and error conditions. Thorough reference documentation serves as the authoritative specification developers consult when implementing integrations. For complex cryptocurrency APIs with hundreds of endpoints covering various blockchain networks, digital assets, and analytical capabilities, well-organized reference documentation becomes essential for usability.
Interactive documentation tools like Swagger UI or Redoc enable developers to explore and test APIs directly from documentation pages without writing code. This hands-on experimentation accelerates learning and debugging by providing immediate feedback. For cryptocurrency APIs, interactive documentation might include sample queries for popular use cases like retrieving market data, analyzing trading volumes, or accessing token ratings, allowing developers to see real responses and understand data structures before writing integration code.
Code samples and SDKs in popular programming languages remove integration friction by providing working implementations developers can adapt to their needs. Rather than requiring every developer to handle HTTP requests, authentication, pagination, and error handling manually, official SDKs encapsulate these concerns in language-native interfaces. For crypto APIs, SDKs might provide convenient methods for common operations like fetching prices, analyzing portfolios, or streaming real-time market data while handling authentication, rate limiting, and connection management automatically.
Performance monitoring provides visibility into API behavior under real-world conditions, identifying bottlenecks, errors, and optimization opportunities. Comprehensive monitoring encompasses multiple dimensions from infrastructure metrics through business analytics, enabling both operational troubleshooting and strategic optimization.
Response time tracking measures how quickly APIs process requests, typically captured at various percentiles. Median response times indicate typical performance while 95th, 99th, and 99.9th percentile response times reveal tail latency affecting some users. For cryptocurrency APIs where traders make time-sensitive decisions based on market data, understanding and optimizing tail latency becomes critical to providing consistent, reliable service.
Error rate monitoring tracks what percentage of requests fail and why, distinguishing between client errors, server errors, and external dependency failures. Sudden error rate increases might indicate bugs, infrastructure problems, or API misuse. For crypto trading APIs where errors could prevent trade execution or cause financial losses, monitoring error rates and investigating spikes quickly prevents larger problems.
Throughput metrics measure request volume over time, revealing usage patterns and capacity constraints. Understanding daily, weekly, and seasonal traffic patterns enables capacity planning and infrastructure scaling. For cryptocurrency APIs where market events can trigger massive traffic spikes, historical throughput data guides provisioning decisions ensuring the platform handles peak loads without degradation.
Dependency health monitoring tracks external service performance including databases, blockchain nodes, cache servers, and third-party APIs. Many API performance issues originate from dependencies rather than application code. Monitoring dependency health enables rapid root cause identification when problems occur. Token Metrics maintains comprehensive monitoring across its cryptocurrency API infrastructure, tracking everything from database query performance to blockchain node responsiveness, ensuring that developers receive fast, reliable access to critical market data.
Comprehensive testing validates API functionality, performance, security, and reliability across various conditions. Different testing approaches address different aspects of API quality, together providing confidence that APIs will perform correctly in production.
Functional testing verifies that endpoints behave according to specifications, validating request handling, business logic execution, and response generation. Unit tests isolate individual components, integration tests validate how components work together, and end-to-end tests exercise complete workflows. For cryptocurrency APIs, functional tests verify that price calculations compute correctly, trading signal generation produces valid outputs, and blockchain data parsing handles various transaction types properly.
Contract testing ensures APIs adhere to specifications and maintain backward compatibility. Consumer-driven contract testing captures client expectations as executable specifications, preventing breaking changes from reaching production. For crypto APIs supporting diverse clients from mobile apps to trading bots, contract testing catches incompatibilities before they impact users.
Performance testing reveals how APIs behave under load, identifying scalability limits and bottlenecks. Load testing simulates normal traffic, stress testing pushes beyond expected capacity, and endurance testing validates sustained operation. For cryptocurrency APIs where market volatility triggers traffic spikes, performance testing under realistic load conditions ensures the platform handles peak demand without degradation.
Security testing validates authentication, authorization, input validation, and encryption implementations. Automated vulnerability scanners identify common weaknesses while manual penetration testing uncovers sophisticated vulnerabilities. For blockchain APIs handling financial transactions, regular security testing ensures protection against evolving threats and compliance with security standards.
Deploying REST APIs to production requires careful consideration of reliability, security, observability, and operational concerns beyond basic functionality. Production-ready APIs implement comprehensive strategies addressing real-world challenges that don't appear during development.
Health check endpoints enable load balancers and monitoring systems to determine API availability and readiness. Health checks validate that critical dependencies are accessible, ensuring traffic routes only to healthy instances. For cryptocurrency APIs depending on blockchain nodes and market data feeds, health checks verify connectivity and data freshness before accepting traffic.
Graceful degradation strategies maintain partial functionality when dependencies fail rather than complete outages. When blockchain nodes become temporarily unavailable, APIs might serve cached data with freshness indicators rather than failing entirely. For crypto market data APIs, serving slightly stale prices during infrastructure hiccups provides better user experience than complete unavailability.
Circuit breakers prevent cascading failures by detecting dependency problems and temporarily suspending requests to failing services. This pattern gives troubled dependencies time to recover while preventing request pile-ups that could overwhelm recovering systems. Token Metrics implements circuit breakers throughout its cryptocurrency API infrastructure, ensuring that problems with individual data sources don't propagate into broader outages.
Building production-ready REST APIs requires mastering design principles, security mechanisms, performance optimization, and operational best practices that together create reliable, scalable, developer-friendly services. From resource-oriented design and HTTP method usage through authentication strategies and error handling, each element contributes to APIs that developers trust and applications depend on. Understanding these fundamentals enables informed architectural decisions and confident API development.
In the cryptocurrency and blockchain space, REST APIs provide essential infrastructure connecting developers to market data, trading capabilities, and analytical intelligence. Token Metrics exemplifies REST API excellence, offering comprehensive cryptocurrency analytics, AI-powered predictions, and real-time blockchain data through a secure, performant, well-documented interface that embodies design best practices. Whether building cryptocurrency trading platforms, portfolio management applications, or blockchain analytics tools, applying these REST API principles and leveraging powerful crypto APIs like those offered by Token Metrics accelerates development while ensuring applications meet professional standards for security, performance, and reliability.
As technology evolves and the cryptocurrency ecosystem continues maturing, REST APIs will remain central to how applications communicate and integrate. Developers who deeply understand REST principles, security requirements, and optimization strategies position themselves to build innovative solutions that leverage modern API capabilities while maintaining the simplicity and reliability that have made REST the dominant architectural style for web services worldwide.

%201.svg)
%201.svg)
REST APIs power much of the web: mobile apps, SPAs, microservices, and integrations all rely on predictable HTTP-based interfaces. This guide breaks down modern REST API concepts into practical frameworks, security patterns, testing workflows, and tooling recommendations so engineers can build resilient, maintainable services.
A REST API (Representational State Transfer) is an architectural style for networked applications that uses stateless HTTP requests to perform operations on resources. Rather than prescribing specific technologies, REST emphasizes constraints—uniform interface, statelessness, cacheability, layered system—to enable scalable, evolvable services.
Key concepts:
Good design balances clarity, consistency, and forward compatibility. Apply these patterns when designing endpoints and payloads:
Designing APIs with clear contracts helps teams iterate without surprises and enables client developers to integrate reliably.
Security and reliability are core to production APIs. Focus on layered defenses and operational guardrails:
Security is not a single control but a set of practices that evolve with threats. Regular reviews and attack surface assessments are essential.
Reliable APIs require automated testing, simulation, and monitoring. Common tools and workflows include:
Combining contract-first development with continuous testing and observability reduces regressions and improves reliability.
Build Smarter Crypto Apps & AI Agents with Token Metrics
Token Metrics provides real-time prices, trading signals, and on-chain insights all from one powerful API. Grab a Free API Key
REST APIs typically use HTTP/HTTPS as the transport protocol and JSON as the dominant payload format. XML and other formats are supported but less common. HTTP status codes convey high-level outcome (200 OK, 201 Created, 400 Bad Request, 401 Unauthorized, 429 Too Many Requests, 500 Server Error).
Versioning strategies vary. A pragmatic approach is to keep backward-compatible changes unversioned and introduce a new version (e.g., /v2/) for breaking changes. Consider header-based versioning for greater flexibility, but ensure clients can discover supported versions.
Use PUT for full resource replacement and PATCH for partial updates. PUT should accept the complete resource representation; PATCH applies a partial modification (often using JSON Patch or a custom partial payload). Document semantics clearly so clients know expectations.
Prefer additive changes (new fields, new endpoints) and avoid removing fields or changing response types. Feature flags, deprecation headers, and sunset timelines help coordinated migration. Provide clear changelogs and client SDK updates when breaking changes are unavoidable.
Common techniques include caching responses with appropriate cache-control headers, using content compression (gzip/ Brotli), database query optimization, connection pooling, and applying CDN edge caching for static or infrequently changing data. Profiling and tracing will point to the highest-return optimizations.
REST emphasizes resource-centric endpoints and predictable HTTP semantics, while GraphQL provides flexible query composition and single-endpoint operation. Choose based on client needs: REST often maps naturally to CRUD operations and caching; GraphQL excels when clients need tailored queries and minimized round trips.
Disclaimer: This article is educational and informational only. It does not constitute investment, legal, or professional advice. Implementations, security practices, and platform choices should be evaluated against your project requirements and in consultation with qualified professionals.


 Create Your Free Account
Create Your Free Account9450 SW Gemini Dr
PMB 59348
Beaverton, Oregon 97008-7105 US
.svg)




.png)
Token Metrics Media LLC is a regular publication of information, analysis, and commentary focused especially on blockchain technology and business, cryptocurrency, blockchain-based tokens, market trends, and trading strategies.
Token Metrics Media LLC does not provide individually tailored investment advice and does not take a subscriber’s or anyone’s personal circumstances into consideration when discussing investments; nor is Token Metrics Advisers LLC registered as an investment adviser or broker-dealer in any jurisdiction.
Information contained herein is not an offer or solicitation to buy, hold, or sell any security. The Token Metrics team has advised and invested in many blockchain companies. A complete list of their advisory roles and current holdings can be viewed here: https://tokenmetrics.com/disclosures.html/
Token Metrics Media LLC relies on information from various sources believed to be reliable, including clients and third parties, but cannot guarantee the accuracy and completeness of that information. Additionally, Token Metrics Media LLC does not provide tax advice, and investors are encouraged to consult with their personal tax advisors.
All investing involves risk, including the possible loss of money you invest, and past performance does not guarantee future performance. Ratings and price predictions are provided for informational and illustrative purposes, and may not reflect actual future performance.



