Top Crypto Trading Platforms in 2025




Big news: We’re cranking up the heat on AI-driven crypto analytics with the launch of the Token Metrics API and our official SDK (Software Development Kit). This isn’t just an upgrade – it's a quantum leap, giving traders, hedge funds, developers, and institutions direct access to cutting-edge market intelligence, trading signals, and predictive analytics.
Crypto markets move fast, and having real-time, AI-powered insights can be the difference between catching the next big trend or getting left behind. Until now, traders and quants have been wrestling with scattered data, delayed reporting, and a lack of truly predictive analytics. Not anymore.
The Token Metrics API delivers 32+ high-performance endpoints packed with powerful AI-driven insights right into your lap, including:
Getting started with the Token Metrics API is simple:
At Token Metrics, we believe data should be decentralized, predictive, and actionable.
The Token Metrics API & SDK bring next-gen AI-powered crypto intelligence to anyone looking to trade smarter, build better, and stay ahead of the curve. With our official SDK, developers can plug these insights into their own trading bots, dashboards, and research tools – no need to reinvent the wheel.
If you operate an exchange, wallet, OTC desk, or DeFi on-ramp, choosing the right KYC/AML providers can be the difference between smooth growth and painful remediation. In 2025, regulators continue to tighten enforcement (Travel Rule, sanctions screening, transaction monitoring), while criminals get more sophisticated across bridges, mixers, and multi-chain hops. This guide shortlists ten credible vendors that help crypto businesses verify users, monitor wallets and transactions, and comply with global rules.
Definition (snippet): KYC/AML providers are companies that deliver identity verification, sanctions/PEP screening, blockchain analytics, transaction monitoring, and Travel Rule tooling so crypto businesses can meet regulatory obligations and reduce financial crime risk.
SECONDARY_KEYWORDS woven below: crypto compliance, blockchain analytics, transaction monitoring, Travel Rule.
Why Use It: Chainalysis KYT and Reactor pair broad chain/token coverage with real-time risk scoring and deep investigative tooling. If you need automated alerts on deposits/withdrawals and the ability to trace through bridges/mixers/DEXs, it’s a proven, regulator-recognized stack.
Best For: Centralized exchanges, custodians, banks with crypto exposure, law enforcement teams.
Notable Features: Real-time KYT alerts • Cross-chain tracing • Case management & APIs • Attribution datasets.
Consider If: You want an enterprise-grade standard and investigator workflows under one roof.
Alternatives: TRM Labs, Elliptic. Chainalysis+1
Regions: Global • Fees/Notes: Quote-based, volume/seat tiers.
Why Use It: TRM’s transaction monitoring taps a large, fast-growing database of illicit activity and extends screening beyond official lists to include threat actor footprints on-chain. Strong coverage and practical APIs make it easy to plug into existing case systems.
Best For: Exchanges, payment processors, fintechs expanding into web3, risk teams that need flexible rules.
Notable Features: Real-time monitoring • Sanctions & threat actor intelligence • Case mgmt. integrations • Multi-chain coverage.
Consider If: You prioritize dynamic risk models and frequent list updates.
Alternatives: Chainalysis, Elliptic. TRM Labs+1
Regions: Global • Fees/Notes: Enterprise contracts; volume-based.
Why Use It: Elliptic’s Lens and Screening solutions streamline wallet/transaction checks with chain-agnostic coverage and audit-ready workflows. It’s built for high-volume screening with clean APIs and strong reporting for regulators and internal audit.
Best For: CEXs, payment companies, institutional custody, risk ops needing bulk screening.
Notable Features: Wallet & TX screening • Cross-chain risk detection • Audit trails • Customer analytics.
Consider If: You need mature address screening and large-scale throughput.
Alternatives: Chainalysis, TRM Labs. Elliptic+1
Regions: Global • Fees/Notes: Quote-based; discounts by volume.
Why Use It: An AML data powerhouse for KYC and ongoing monitoring that many crypto companies use to meet screening obligations and reduce false positives. Strong watchlist coverage, adverse media, and continuous monitoring help you satisfy banking partners and auditors.
Best For: Exchanges and fintechs that want robust sanctions/PEP data plus transaction monitoring.
Notable Features: Real-time sanctions & watchlists • Ongoing monitoring • Payment screening • Graph analysis.
Consider If: You want a single vendor for screening + monitoring alongside your analytics stack.
Alternatives: Jumio (Screening), Sumsub. ComplyAdvantage+1
Regions: Global • Fees/Notes: Tiered enterprise pricing.
Why Use It: Crypto-focused onboarding with liveness, documents, KYB, Travel Rule support, and transaction monitoring—plus in-house legal experts to interpret changing rules. Good for teams that need to orchestrate identity checks and AML controls in one flow.
Best For: Global exchanges, NFT/DeFi ramps, high-growth startups entering new markets.
Notable Features: KYC/KYB • Watchlists/PEPs • Device intelligence • Crypto TX monitoring • Case management.
Consider If: You want one vendor for identity + AML + Travel Rule workflow.
Alternatives: Jumio, ComplyAdvantage. Sumsub+1
Regions: Global • Fees/Notes: Per-verification & volume tiers.
Why Use It: Jumio combines biometric KYC with automated AML screening (PEPs/sanctions) and ongoing monitoring. Its “KYX” approach provides identity insights across the customer lifecycle, helping reduce fraud while keeping onboarding friction reasonable.
Best For: Regulated exchanges, banks, brokerages with strict KYC/AML controls.
Notable Features: Biometric verification • PEPs/sanctions screening • Ongoing monitoring • Single-API platform.
Consider If: You need global coverage and battle-tested uptime/SLA.
Alternatives: Sumsub, Onfido (not listed). Jumio+1
Regions: Global • Fees/Notes: Custom enterprise pricing.
Why Use It: Notabene focuses on pre-transaction decisioning, counterparty VASP due diligence, and sanctions screening across multiple Travel Rule protocols. It’s purpose-built for crypto compliance teams facing enforcement of FATF Recommendation 16.
Best For: Exchanges, custodians, and B2B payment platforms needing Travel Rule at scale.
Notable Features: Pre-TX checks • Counterparty VASP verification • Multi-protocol messaging • Jurisdictional rules engine.
Consider If: Your regulators or banking partners expect full Travel Rule compliance today.
Alternatives: Shyft Veriscope, 21 Analytics. Notabene+1
Regions: Global • Fees/Notes: Annual + usage components.
Why Use It: Veriscope provides decentralized VASP discovery, secure VASP-to-VASP PII exchange, and “sunrise issue” lookback to help during uneven global rollouts. Pay-as-you-go pricing can be attractive for newer programs.
Best For: Global VASPs that want decentralized discovery and interoperability.
Notable Features: Auto VASP discovery • Secure PII transfer (no central PII storage) • Lookback support • Interoperability.
Consider If: You prefer decentralized architecture and usage-based pricing.
Alternatives: Notabene, 21 Analytics. shyft.network+1
Regions: Global • Fees/Notes: Pay-as-you-go; no setup fees. shyft.network
Why Use It: Merkle Science’s platform emphasizes predictive risk modeling and DeFi/smart contract forensics, helping compliance teams see beyond static address tags. Good complement when you monitor emerging chains and token types.
Best For: Exchanges and protocols active in DeFi, new L1/L2 ecosystems, or smart-contract risk.
Notable Features: Predictive risk scores • DeFi & contract forensics • Case tooling • API integrations.
Consider If: You need analytics tuned for newer protocols and token standards.
Alternatives: Chainalysis, TRM Labs. merklescience.com+1
Regions: Global • Fees/Notes: Quote-based enterprise pricing.
Why Use It: Based in Luxembourg, Scorechain offers risk scoring, transaction monitoring, and reporting designed to fit EU frameworks—useful for MiCA/TFR-aligned programs. Teams like the straightforward reporting exports for audits and regulators.
Best For: EU-focused exchanges, neobanks, and tokenization platforms.
Notable Features: Risk scoring • Transaction monitoring • Audit-ready reports • Tools for Travel Rule workflows.
Consider If: Your footprint is primarily EU and you want EU-centric vendor DNA.
Alternatives: Crystal (EU), Elliptic. Scorechain+1
Regions: EU/Global • Fees/Notes: Enterprise licenses; fixed and usage options.
Primary CTA: Start a free trial of Token Metrics.

This article is for research/education, not financial advice.
What’s the difference between KYC and KYT (Know Your Transaction)?
KYC verifies an individual or entity at onboarding and during refresh cycles. KYT/transaction monitoring analyzes wallets and transfers in real time (or post-event) to identify suspicious activity, sanctions exposure, and patterns of illicit finance. TRM Labs
Do I need a Travel Rule solution if I only serve retail in one country?
Possibly. Many jurisdictions apply the Travel Rule above certain thresholds and when sending to other VASPs, even domestically. If you interoperate with global exchanges or custodians, you’ll likely need it. Notabene
How do vendors differ on sanctions coverage?
Screening providers update against official lists and, in some cases, extend coverage using intelligence on known threat actors’ wallets. Look for rapid refresh cycles and retroactive screening. TRM Labs
Can I mix-and-match KYC and blockchain analytics vendors?
Yes. Many teams use a KYC/AML screening vendor plus a blockchain analytics platform; some suites offer both, but best-of-breed mixes are common.
What’s a good starting stack for a new exchange?
A KYC/KYB vendor (Jumio or Sumsub), a sanctions/PEP screening engine (ComplyAdvantage or your KYC vendor’s module), a blockchain analytics platform (Chainalysis/TRM/Elliptic), and a Travel Rule tool (Notabene or Veriscope).
Compliance isn’t one tool; it’s a stack. If you’re U.S.-regulated and high-volume, start with Chainalysis or TRM plus Jumio or Sumsub. If you’re EU-led, Scorechain can simplify audits. For Travel Rule, choose Notabene (end-to-end) or Veriscope (decentralized/pay-as-you-go). Pair your chosen stack with Token Metrics to research, monitor, and act with confidence.
Related Reads:
We independently reviewed official product pages, docs, and security/trust materials for each provider (no third-party links in body). Shortlist refreshed September 2025; we’ll revisit as regulations, features, and availability change.
Scorechain — Product pages & glossary resources. Scorechain+1
If you touch tokens, stablecoins, exchanges, DeFi, custody, or tokenized RWAs, your choice of counsel can make or break the roadmap. This guide ranks the best crypto law firms for 2025, with a practical look at who they’re best for, where they operate, and what to consider on fees, scope, and risk. In one line: a crypto law firm is a multidisciplinary legal team that advises on digital asset regulation, transactions, investigations, and disputes.
Macro backdrop: the U.S. regulatory stance is shifting (e.g., an SEC crypto task force and fresh policy signals), while the EU’s MiCA, UK rules, and APAC regimes continue to evolve—raising the stakes for compliant go-to-market and ops. Sidley Austin+1
Data sources: official firm practice pages, security/regulatory hubs, and disclosures; third-party market datasets used only as cross-checks. Last updated: September 2025.



Primary CTA: Start free trial

This article is for research/education, not financial advice.
What does a crypto law firm actually do?
They advise on token and product structuring, licensing (e.g., money transmission, MiCA), securities/commodities issues, AML/sanctions, and handle investigations, litigation, deals, and restructurings. Many also publish policy trackers and hubs to keep clients current. Davis Polk+2Perkins Coie+2
How much do top crypto law firms cost?
Rates vary by market and complexity. Expect premium pricing for multi-jurisdictional or contested matters. Ask for detailed scopes, blended rates, and fixed-fee modules for licensing or audits.
Do I need a U.S. firm if I’m launching in the EU under MiCA?
Often yes—especially if you have U.S. users, listings, or investors. Use an EU lead for MiCA, coordinated with U.S. counsel for extraterritorial touchpoints and future expansion. Cooley
Which firms are strongest for enforcement risk?
WilmerHale, Davis Polk, Skadden, and Sidley bring deep SEC/CFTC literacy and investigations experience; assess fit by recent publications and team bios. Sidley Austin+3WilmerHale+3Davis Polk+3
Can these firms help with tokenization and RWAs?
Yes. Look for demonstrated work on structured products/derivatives, custody, and financial-market infrastructure, plus privacy/cyber overlays. lw.com
For U.S. market structure or sensitive investigations, Davis Polk and WilmerHale are hard to beat. For global, multi-workstream matters, start with Latham or A&O Shearman. Builders and venture-backed teams often pair Perkins Coie or Cooley with a litigation-ready option like Skadden. Whatever you choose, scope tightly, budget in phases, and align counsel with your roadmap.
Related Reads:
We reviewed official digital-asset/fintech practice pages, firm resource hubs, and recent official insights; no third-party sites were linked in-body. Updated September 2025 for U.S. policy changes and EU MiCA implementation status.
Hogan Lovells — “Digital Assets and Blockchain”; Digital Assets & Blockchain Hub; Payments newsletter. www.hoganlovells.com+2digital-client-solutions.hoganlovells.com+2
Crypto index providers give institutions and advanced investors rules-based, auditable ways to measure the digital asset market. In one sentence: a crypto index provider designs and administers regulated benchmarks—like price indices or market baskets—that funds, ETPs, quants, and risk teams can track or license. As liquidity deepens and regulation advances, high-integrity benchmarks reduce noise, standardize reporting, and enable products from passive ETPs to factor strategies.
If you’re comparing crypto index providers for portfolio measurement, product launches, or compliance reporting, this guide ranks the best options now—what they do, who they fit, and what to consider across security posture, coverage, costs, and support.
We relied on official product pages, methodologies, and security/governance disclosures; third-party datasets (e.g., venue quality screens) were used only as cross-checks. Last updated September 2025.
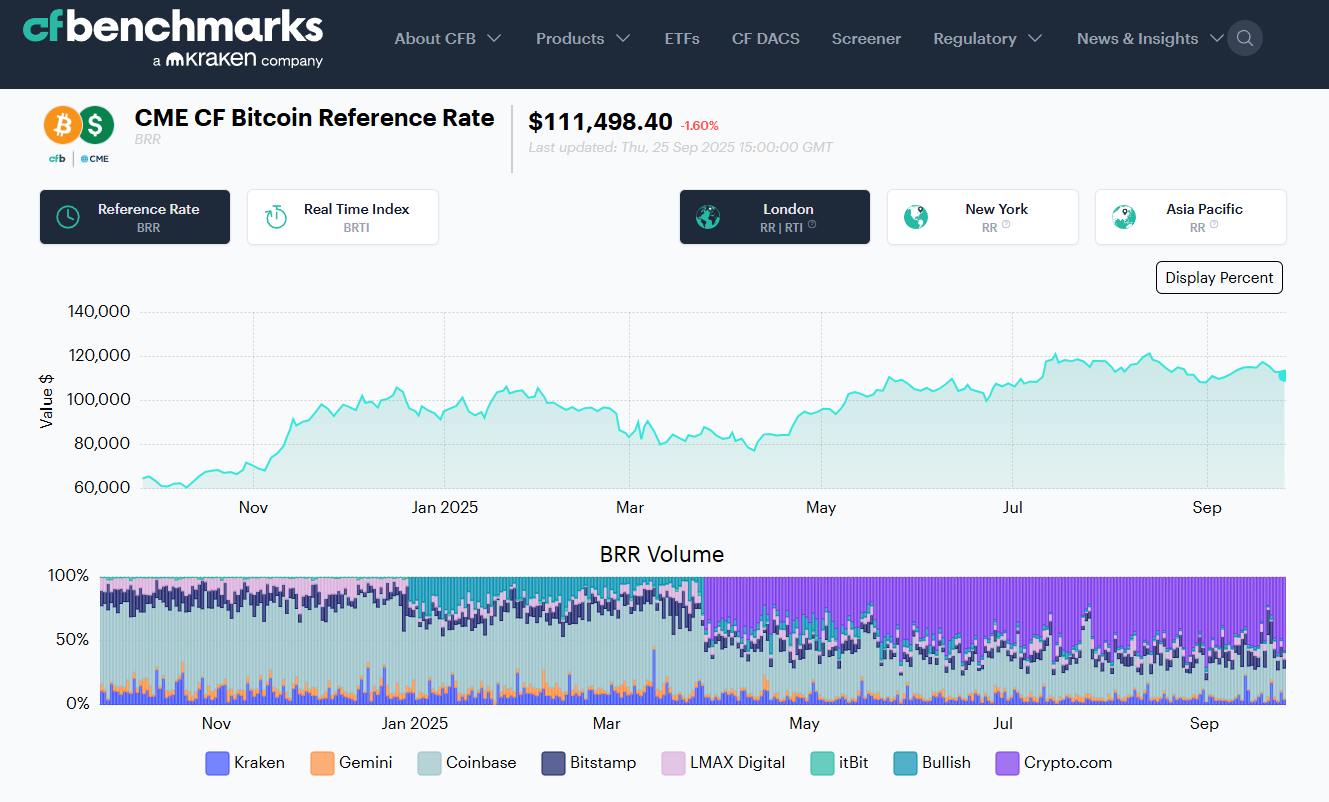
Why Use It: Administrator of the CME CF Bitcoin Reference Rate (BRR) and related benchmarks used to settle major futures and institutional products; UK BMR-registered with transparent exchange criteria and daily calculation since 2016. If you need benchmark-grade spot references (BTC, ETH and more) with deep derivatives alignment, start here. CF Benchmarks+1
Best For: Futures settlement references; fund NAV/pricing; risk; audit/compliance.
Notable Features: BRR/BRRNY reference rates; multi-exchange liquidity screens; methodology & governance docs; broad suite of real-time indices.
Consider If: You need composite market baskets beyond single-assets—pair with a multi-asset provider.
Alternatives: S&P Dow Jones Indices; FTSE Russell.
Regions: Global • Fees/Notes: Licensed benchmarks; enterprise pricing.

Why Use It: The S&P Cryptocurrency series (incl. Broad Digital Market) brings index craft, governance, and transparency familiar to traditional asset allocators—ideal for boards and committees that already use S&P. S&P Global+1
Best For: Asset managers launching passive products; OCIOs; consultants.
Notable Features: Broad/large-cap/mega-cap indices; single-asset BTC/ETH; published ground rules; established brand trust.
Consider If: You need highly customizable factors or staking-aware baskets—other vendors may move faster here.
Alternatives: MSCI; MarketVector.
Regions: Global • Fees/Notes: Licensing via S&P DJI.

Why Use It: MSCI’s Global Digital Assets and Smart Contract indices apply MSCI’s taxonomy/governance with themed exposures and clear methodologies—useful when aligning with enterprise risk standards. MSCI+1
Best For: CIOs needing policy-friendly thematics; due-diligence heavy institutions.
Notable Features: Top-30 market index; smart-contract subset; methodology docs; global brand assurance.
Consider If: You need exchange-by-exchange venue vetting or settlement rates—pair with CF Benchmarks or FTSE Russell.
Alternatives: S&P DJI; FTSE Russell.
Regions: Global • Fees/Notes: Enterprise licensing.
Why Use It: Built in association with Digital Asset Research (DAR), FTSE Russell screens assets and venues to EU Benchmark-ready standards; strong fit for risk-controlled coverage from large to micro-cap and single-asset series. LSEG+1
Best For: Product issuers who need venue vetting & governance; EU-aligned programs.
Notable Features: FTSE Global Digital Asset series; single-asset BTC/ETH; ground rules; DAR reference pricing.
Consider If: You require highly custom factor tilts—MarketVector or Vinter may be quicker to bespoke.
Alternatives: Wilshire; S&P DJI.
Regions: Global (EU-friendly) • Fees/Notes: Licensed benchmarks.
Why Use It: NCI is designed to be dynamic, representative, and trackable; widely recognized and replicated by ETPs seeking diversified core exposure—useful as a single “beta” benchmark. Nasdaq+2Nasdaq Global Index Watch+2
Best For: Core market ETPs; CIO benchmarks; sleeve construction.
Notable Features: Rules-driven eligibility; regular reconstitutions; strong market recognition.
Consider If: You want deep sector/thematic granularity—pair with MSCI/MarketVector.
Alternatives: Bloomberg Galaxy (BGCI); MarketVector MVDA.
Regions: Global • Fees/Notes: Licensing via Nasdaq.
Why Use It: Backed by VanEck’s index arm (formerly MVIS), MarketVector offers off-the-shelf MVDA 100 plus sectors, staking-aware, and bespoke solutions—popular with issuers needing speed to market and depth. MarketVector Indexes+1
Best For: ETP issuers; quants; asset managers needing customization.
Notable Features: MVDA (100-asset) benchmark; single/multi-asset indices; staking/factor options; robust docs.
Consider If: You prioritize blue-chip simplicity—BGCI/NCI might suffice.
Alternatives: Vinter; S&P DJI.
Regions: Global • Fees/Notes: Enterprise licensing; custom index services.
Why Use It: Co-developed by Bloomberg and Galaxy, BGCI targets the largest, most liquid cryptoassets, with concentration caps and monthly reviews—an institutional “core” that’s widely cited on terminals. Galaxy Asset Management+1
Best For: CIO benchmarks; performance reporting; media-friendly references.
Notable Features: Capped weights; qualified exchange criteria; Bloomberg governance.
Consider If: You need smaller-cap breadth—MVDA/NCI may cover more names.
Alternatives: NCI; S&P DJI.
Regions: Global • Fees/Notes: License via Bloomberg Index Services.
Why Use It: Administrator of XBX (Bitcoin Price Index) and the CoinDesk 20, with transparent liquidity weighting and growing exchange integrations—including use in listed products. CoinDesk Indices+2CoinDesk Indices+2
Best For: Reference rates; product benchmarks; quant research.
Notable Features: XBX reference rate; CoinDesk 20; governance/methodologies; exchange selection rules.
Consider If: You require UK BMR-registered BTC settlement—CF Benchmarks BRR is purpose-built.
Alternatives: CF Benchmarks; S&P DJI.
Regions: Global • Fees/Notes: Licensing available; contact sales.
Why Use It: A regulated, crypto-native index provider focused on building/maintaining indices tracked by ETPs across Europe; fast on custom thematics and single-asset reference rates. vinter.co+1
Best For: European ETP issuers; bespoke strategies; rapid prototyping.
Notable Features: BMR-style reference rates; multi-asset baskets; calc-agent services; public factsheets.
Consider If: You need mega-brand recognition for U.S. committees—pair with S&P/MSCI.
Alternatives: MarketVector; Solactive.
Regions: Global (strong EU footprint) • Fees/Notes: Custom build/licensing.
Why Use It: The FT Wilshire series aims to be an institutional market standard with transparent rules, broad coverage, and exchange quality screens—supported by detailed methodology documents. wilshireindexes.com+1
Best For: Consultants/OCIOs; plan sponsors; research teams.
Notable Features: Broad Market index; governance via advisory groups; venue vetting; classification scheme.
Consider If: You need media-ubiquitous branding—S&P/Bloomberg carry more name recall.
Alternatives: FTSE Russell; S&P DJI.
Regions: Global • Fees/Notes: Enterprise licensing.

Primary CTA: Start free trial.

This article is for research/education, not financial advice.
What is a crypto index provider?
A company that designs, calculates, and governs rules-based benchmarks for digital assets—ranging from single-asset reference rates to diversified market baskets—licensed for reporting or products.
Which crypto index is best for “core beta”?
For simple, liquid market exposure, many institutions look to BGCI or NCI due to broad recognition and liquidity screens; your use case and region may point to S&P/FTSE alternatives. Galaxy Asset Management+1
How do providers choose exchanges and assets?
They publish ground rules defining eligible venues (liquidity, compliance), asset screening, capping, and rebalances—see S&P, FTSE (with DAR), and CF Benchmarks for examples. S&P Global+2LSEG+2
Can I license a custom crypto index?
Yes—MarketVector and Vinter (among others) frequently build bespoke indices and act as calculation agents for issuers. MarketVector Indexes+1
What’s the difference between a reference rate and a market basket?
Reference rates (e.g., BRR, XBX) target a single asset’s robust price; market baskets (e.g., NCI, BGCI) represent diversified multi-asset exposure. Galaxy Asset Management+3CF Benchmarks+3CoinDesk Indices+3
Are these benchmarks available in the U.S. and EU?
Most are global; for EU/UK benchmark usage, verify authorization/registration (e.g., CF Benchmarks UK BMR) and your product’s country-specific rules. CF Benchmarks
If you need regulated reference pricing for settlement or NAVs, start with CF Benchmarks. For core market beta, BGCI and NCI are widely recognized. For institution-grade breadth, consider S&P DJI or FTSE Russell (with DAR). If you’re launching custom or thematic products, MarketVector and Vinter are strong build partners.
Related Reads:
We reviewed official product pages, methodologies, and governance documents current as of September 2025. A short list of key sources per provider is below (official sites only; non-official data used only for cross-checks and not linked here).
Wilshire: FT Wilshire Digital Asset Index Series page; methodology PDF. wilshireindexes.com+1
