Top Crypto Trading Platforms in 2025




Big news: We’re cranking up the heat on AI-driven crypto analytics with the launch of the Token Metrics API and our official SDK (Software Development Kit). This isn’t just an upgrade – it's a quantum leap, giving traders, hedge funds, developers, and institutions direct access to cutting-edge market intelligence, trading signals, and predictive analytics.
Crypto markets move fast, and having real-time, AI-powered insights can be the difference between catching the next big trend or getting left behind. Until now, traders and quants have been wrestling with scattered data, delayed reporting, and a lack of truly predictive analytics. Not anymore.
The Token Metrics API delivers 32+ high-performance endpoints packed with powerful AI-driven insights right into your lap, including:
Getting started with the Token Metrics API is simple:
At Token Metrics, we believe data should be decentralized, predictive, and actionable.
The Token Metrics API & SDK bring next-gen AI-powered crypto intelligence to anyone looking to trade smarter, build better, and stay ahead of the curve. With our official SDK, developers can plug these insights into their own trading bots, dashboards, and research tools – no need to reinvent the wheel.
Generating impressive returns through Token Metrics crypto indices represents only half the wealth-building equation. The other half—often overlooked by investors focused solely on performance—involves minimizing taxes that can consume 30-50% of your gains. Every dollar paid unnecessarily in taxes is a dollar that can't compound into future wealth.
Cryptocurrency taxation presents unique complexities that differ significantly from traditional investments. However, these complexities also create optimization opportunities unavailable with stocks or bonds. Understanding and implementing sophisticated tax strategies can add 2-5 percentage points to your effective annual returns—enough to transform good investment outcomes into exceptional ones over decades.
This comprehensive guide explores tax optimization for crypto index investors, examining current tax treatment, strategies for minimizing tax liability, retirement account advantages, loss harvesting techniques, and long-term tax planning that maximizes after-tax wealth accumulation.
Before implementing optimization strategies, understand how crypto indices are taxed.
The single most powerful tax optimization strategy involves using retirement accounts for crypto index investing when possible.
Roth IRAs offer unmatched tax advantages for crypto indices:
Strategy: Maximize Roth IRA contributions annually ($7,000 for 2024, or $8,000 if age 50+) allocating these funds to crypto indices. If crypto appreciates 40% annually for 30 years, that initial $7,000 grows to over $10 million completely tax-free.
Traditional IRAs offer different but still valuable benefits:
Strategy: If current tax bracket is high, contribute to traditional IRA for immediate deduction. Later, convert to Roth IRA during years with lower income (perhaps early retirement before Social Security begins), paying taxes at reduced rates.
Standard IRA custodians often don't support cryptocurrency. Self-directed IRA custodians like Alto, iTrustCapital, or BitcoinIRA specifically facilitate crypto holdings within retirement accounts.
These specialized custodians charge higher fees than traditional brokers but the tax benefits far exceed fee costs. Research custodians thoroughly, understanding fee structures, supported cryptocurrencies, and withdrawal processes before opening accounts.
Some employers now offer cryptocurrency options in 401(k) plans. If available, consider allocating portions of 401(k) contributions to crypto indices, capturing tax advantages while maintaining employer matching benefits.
If employer plans don't support crypto, maximize employer match in 401(k), then open self-directed IRA for crypto allocation. This ensures you capture free employer money while still achieving desired crypto exposure in tax-advantaged accounts.
Crypto volatility creates frequent opportunities for tax-loss harvesting—deliberately selling positions at losses to offset gains elsewhere in your portfolio.
When you sell investments at losses, those losses offset capital gains dollar-for-dollar. If losses exceed gains, you can deduct up to $3,000 annually against ordinary income, carrying forward excess losses to future years indefinitely.
Example: Your index appreciates $50,000 during the year (creating potential $50,000 gain when sold). Another index declined $20,000. By selling the losing position, you harvest $20,000 in losses reducing your taxable gain to $30,000 and saving $4,000-7,400 in taxes depending on your bracket.
Stock investors face "wash sale rules" preventing them from selling securities at losses and repurchasing identical or substantially identical securities within 30 days. This rule prevents gaming the system through artificial loss harvesting.
Currently, cryptocurrency is not subject to wash sale rules. You can sell Bitcoin at a loss and immediately repurchase it, maintaining market exposure while harvesting tax losses. This provides enormous optimization opportunities unavailable with traditional securities.
Note: Proposed legislation may extend wash sale rules to crypto in the future. Consult tax professionals about current regulations when implementing strategies.
Bear markets present exceptional loss harvesting opportunities. As indices decline 50-70%, systematically harvest losses while maintaining exposure through immediate repurchases or similar but not identical indices.
Strategy: During significant market declines, harvest losses in aggressive growth indices while simultaneously purchasing conservative indices. This maintains crypto exposure while capturing substantial tax losses. Reverse the process during recovery, moving back to aggressive indices.
Review portfolio in November-December identifying loss harvesting opportunities before year-end. Tax losses must be realized by December 31st to count for current tax year.
However, don't let tax tail wag investment dog—never sell positions solely for tax purposes if doing so undermines long-term strategy. Harvest losses strategically within context of overall investment plan.
Accurate cost basis tracking enables optimizing which specific shares you sell, minimizing taxes on each transaction.
Donating appreciated crypto to qualified charities creates powerful tax advantages.
Donating appreciated crypto held over one year to 501(c)(3) charities provides:
Strategy: If planning charitable giving, donate appreciated crypto instead of cash. This optimization is especially powerful during high-income years where deductions provide maximum value.
Donor-advised funds (DAFs) through Fidelity Charitable, Schwab Charitable, or specialized crypto DAF providers accept cryptocurrency donations, providing immediate tax deductions while allowing you to recommend grants to charities over time.
Strategy: During exceptionally profitable years, donate substantial appreciated crypto to DAF, capturing large tax deduction. Then distribute to charities gradually over subsequent years based on your philanthropic priorities.
While this doesn't apply to crypto directly, investors over age 70½ can make qualified charitable distributions from IRAs up to $100,000 annually. These distributions satisfy required minimum distributions while excluding amounts from taxable income.
Strategy: Use QCDs for charitable giving from traditional IRAs while preserving appreciated crypto in Roth IRAs for tax-free growth.
Controlling when you recognize taxable income significantly impacts lifetime tax burden.
Tax rates vary year-to-year based on income. Strategic timing of crypto sales can minimize rates paid:
Strategy: If taking year off or experiencing income decline, sell appreciated crypto indices locking in gains at 0-15% rates. Then immediately repurchase, establishing higher cost basis for future sales.
Converting traditional IRA crypto holdings to Roth IRAs triggers taxable income. However, strategic timing minimizes tax costs:
Strategy: During crypto bear markets, convert traditional IRA crypto holdings to Roth when values are temporarily depressed. Pay taxes on depressed values, then enjoy full recovery tax-free inside Roth.
State taxes significantly impact after-tax returns. No-income-tax states (Alaska, Florida, Nevada, South Dakota, Tennessee, Texas, Washington, Wyoming) tax only at federal level. High-tax states like California (13.3%), New York (10.9%), and New Jersey (10.75%) add substantial state taxes on crypto gains.
Strategic Relocation: High earners sometimes relocate to no-tax states before realizing substantial gains. Moving from California to Texas before selling $5 million in appreciated crypto saves $665,000 in state taxes. However, states scrutinize such moves—establishing legitimate domicile requires genuine ties including residence, voter registration, driver's license, and spending majority of year in new state. Consult tax attorneys about timing and requirements.
Crypto tax complexity exceeds most investors' expertise. Professional guidance prevents costly mistakes and identifies optimization opportunities you'd otherwise miss.
Consider specialized crypto tax professionals if you:
Generic accountants often lack crypto expertise. Seek specialists with demonstrated cryptocurrency tax experience through credentials like the Certified Public Accountant (CPA) designation plus crypto-specific training.
Professional crypto tax planning costs $500-5,000+ annually depending on complexity. However, identifying even single optimization opportunity often saves multiples of professional fees.
Example: CPA costs $2,000 annually but identifies loss harvesting opportunity saving $8,000 in taxes, Roth conversion strategy saving $15,000 over five years, and charitable giving optimization saving $5,000. Total value: $28,000 for $2,000 investment.
Tax optimization isn't about gaming the system or taking questionable positions—it's about structuring investments to legally minimize taxes within established rules. The difference between paying 37% short-term capital gains rates versus 0-15% long-term rates, or paying no taxes via Roth IRAs, compounds into hundreds of thousands or millions over decades.
Token Metrics indices provide world-class investment performance, but keeping more of those returns through strategic tax planning determines your actual wealth accumulation. A 45% annual return becomes 28% after-tax at high ordinary income rates—but remains 45% tax-free in Roth IRA.
Begin implementing tax optimization strategies today. Maximize tax-advantaged account contributions, implement systematic loss harvesting, track cost basis meticulously, time income recognition strategically, and work with qualified professionals for complex situations.
Your future self will appreciate the six-figure or seven-figure tax savings generated through disciplined tax optimization as much as the strong investment returns from Token Metrics indices. Combined, they create unstoppable wealth accumulation.
Start your 7-day free trial today and begin building tax-efficient crypto wealth through Token Metrics indices combined with strategic tax optimization.
The Layer 1 competitive landscape is consolidating as markets recognize that specialization matters more than being a generic alternative to Ethereum. Avalanche positions itself in this multi-chain world with specific technical and ecosystem advantages. Infrastructure maturity around custody, bridges, and developer tooling makes alternative L1s more accessible heading into 2026.
The scenario projections below map different market share outcomes for AVAX across varying total crypto market sizes. Base cases assume Avalanche maintains current ecosystem momentum, while moon scenarios factor in accelerated adoption, and bear cases reflect increased competitive pressure.

Disclosure
Educational purposes only, not financial advice. Crypto is volatile, do your own research and manage risk.
How to read it: Each band blends cycle analogues and market-cap share math with TA guardrails. Base assumes steady adoption and neutral or positive macro. Moon layers in a liquidity boom. Bear assumes muted flows and tighter liquidity.
TM Agent baseline: Token Metrics lead metric for Avalanche, cashtag $AVAX, is a TM Grade of 66.2%, which maps to Hold, and the trading signal is bearish, indicating short-term downward momentum. Concise long-term numeric view, 12-month horizon: Token Metrics’ scenarios center around a price band roughly between $15 and $40, with a base case near $25. Market context: Bitcoin’s direction remains the primary market driver, so broader crypto risk-on conditions are required for $AVAX to reach the higher scenario.
Live details: Avalanche Token Details
Affiliate Disclosure: We may earn a commission from qualifying purchases made via this link, at no extra cost to you.
Token Metrics scenarios span four market cap tiers, each representing different levels of crypto market maturity and liquidity:
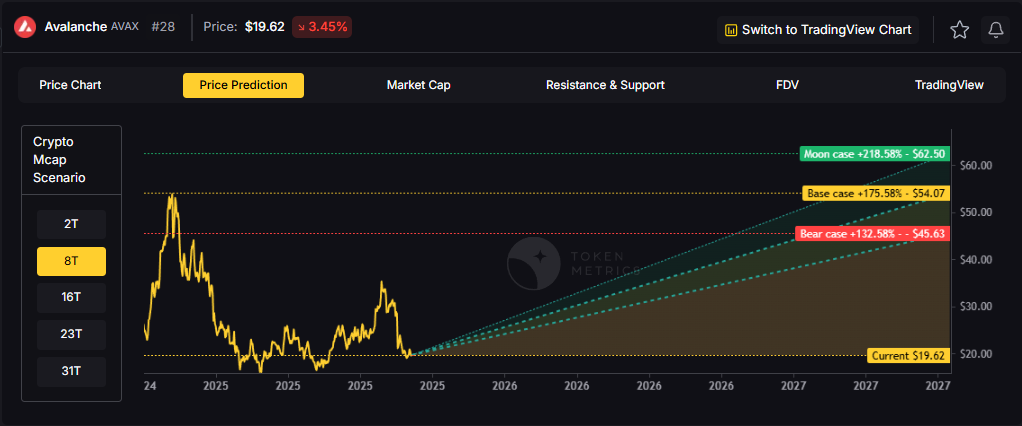
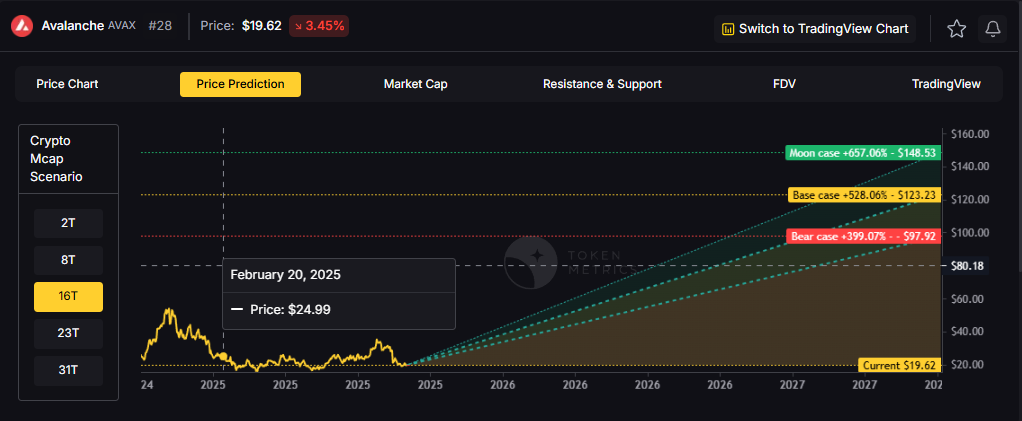

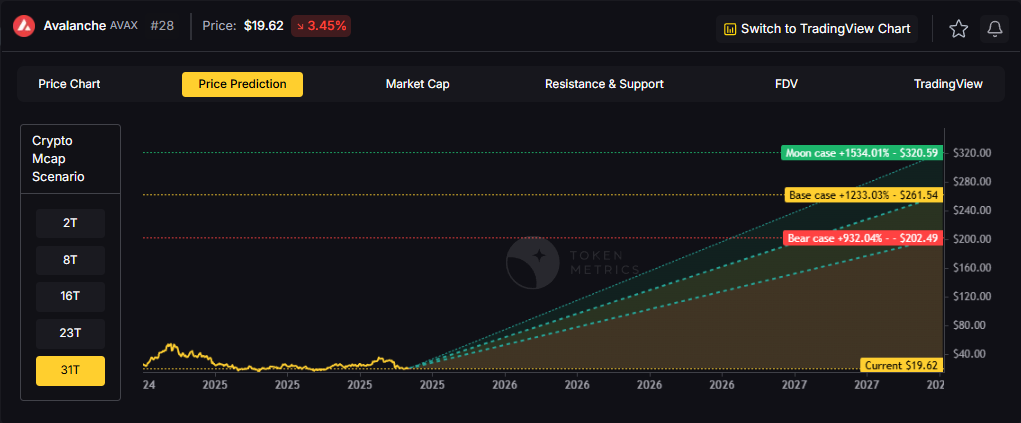
Each tier assumes progressively stronger market conditions, with the base case reflecting steady growth and the moon case requiring sustained bull market dynamics.
Avalanche represents one opportunity among hundreds in crypto markets. Token Metrics Indices bundle AVAX with top one hundred assets for systematic exposure to the strongest projects. Single tokens face idiosyncratic risks that diversified baskets mitigate.
Historical index performance demonstrates the value of systematic diversification versus concentrated positions.
What Is Avalanche?
Avalanche is a smart-contract platform known for high throughput, low latency, and a modular subnet architecture. It aims to support decentralized finance, gaming, and enterprise applications with fast finality and cost-efficient transactions.
AVAX is the native token used for fees, staking, and network security, and it powers activity across application subnets. The ecosystem positions Avalanche among leading Layer 1s competing for developer mindshare and user adoption.
Token Metrics AI provides comprehensive context on Avalanche's positioning and challenges.
Vision: Avalanche aims to provide a highly scalable, secure, and decentralized platform for launching custom blockchains and decentralized applications. Its vision centers on enabling a global, open financial system and supporting a diverse ecosystem of interoperable blockchains.
Problem: Many blockchain networks face trade-offs between speed, security, and decentralization, often resulting in high fees and slow transaction times during peak demand. Avalanche addresses the need for a scalable and efficient infrastructure that can support widespread adoption of dApps and enterprise use cases without compromising on performance or security.
Solution: Avalanche uses a novel consensus mechanism that achieves rapid finality with low energy consumption, differentiating it from traditional Proof-of-Work systems. It employs a three-chain architecture—Exchange Chain (X-Chain), Platform Chain (P-Chain), and Contract Chain (C-Chain)—to separate functions like asset creation, staking, and smart contract execution, enhancing efficiency and scalability.
Market Analysis: Avalanche operates in the competitive Layer 1 blockchain space. It differentiates itself through its consensus protocol and support for subnet-based custom blockchains. Adoption is influenced by developer activity, partnerships, and integration with major DeFi protocols, with risks from technological shifts and regulatory developments.
Fundamental Grade: 91.63% (Community 82%, Tokenomics 100%, Exchange 100%, VC 97%, DeFi Scanner 83%).
Technology Grade: 80.52% (Activity 80%, Repository 72%, Collaboration 93%, Security 59%, DeFi Scanner 83%).
Can AVAX reach $200?
Answer: Based on the scenarios, AVAX could reach $200 in the 31T bear case at $202.49. The 31T tier also shows $261.54 in the base case and $320.59 in the moon case. Not financial advice.
Can AVAX 10x from current levels?
Answer: At a current price of $19.62, a 10x would reach $196.20. This falls within the 31T bear, base, and moon cases, and the 23T moon case at $234.56. Bear in mind that 10x returns require substantial market cap expansion. Not financial advice.
Should I buy AVAX now or wait?
Answer: Timing depends on your risk tolerance and macro outlook. Current price of $19.62 sits below the 8T bear case at $45.63. Dollar-cost averaging may reduce timing risk. Not financial advice.
Disclosure
Educational purposes only, not financial advice. Crypto is volatile, do your own research and manage risk.
Our team delivers scenario-driven price projections, in-depth grades, and actionable indices to empower smarter crypto investing—with both human and AI insights.
Layer 1 tokens like Hedera represent bets on specific blockchain architectures winning developer and user mindshare. HBAR carries both systematic crypto risk and unsystematic risk from Hedera's technical roadmap execution and ecosystem growth. Multi-chain thesis suggests diversifying across several L1s rather than concentrating in one, since predicting which chains will dominate remains difficult.
The projections below show how HBAR might perform under different market cap scenarios. While Hedera may have strong fundamentals, prudent portfolio construction balances L1 exposure across Ethereum, competing smart contract platforms, and Bitcoin to capture the sector without overexposure to any single chain's fate.
Disclosure
Educational purposes only, not financial advice. Crypto is volatile, do your own research and manage risk.
How to read it: Each band blends cycle analogues and market-cap share math with TA guardrails. Base assumes steady adoption and neutral or positive macro. Moon layers in a liquidity boom. Bear assumes muted flows and tighter liquidity.
TM Agent baseline:
Token Metrics lead metric for Hedera, cashtag $HBAR, is a TM Grade of 61.8%, which maps to Hold, and the trading signal is bearish, indicating short-term downward momentum. This means Token Metrics views $HBAR as having reasonably solid fundamentals but limited conviction for strong outperformance in the near term.
A concise long-term numeric view for a 12-month horizon: Token Metrics scenarios center around a range of about $0.06 to $0.18, with a base case near $0.10, reflecting steady ecosystem growth, moderate adoption of Hedera services, and continued enterprise partnerships. Implication: if Bitcoin and broader crypto risk appetite improve, $HBAR could revisit the higher end, while a risk-off market or slower-than-expected developer traction would keep it toward the lower bound.
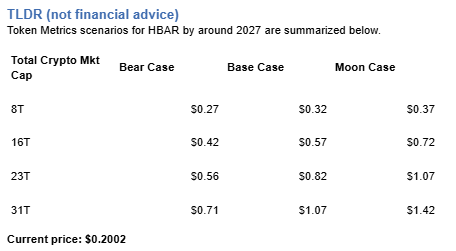
Token Metrics scenarios span four market cap tiers, each representing different levels of crypto market maturity and liquidity:

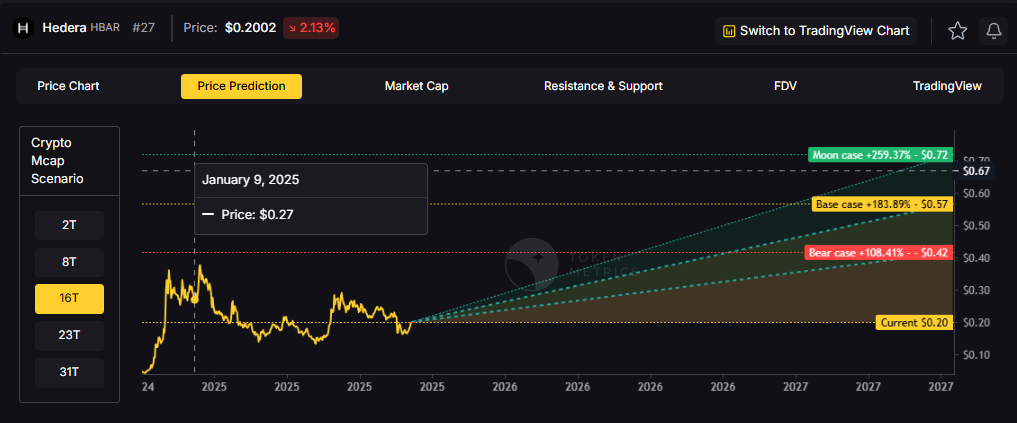


These ranges illustrate potential outcomes for concentrated HBAR positions, but investors should weigh whether single-asset exposure matches their risk tolerance or whether diversified strategies better suit their objectives.
Professional investors across asset classes prefer diversified exposure over concentrated bets for good reason. Hedera faces numerous risks - technical vulnerabilities, competitive pressure, regulatory targeting, team execution failure - any of which could derail HBAR performance independent of broader market conditions. Token Metrics Indices spread this risk across one hundred tokens, ensuring no single failure destroys your crypto portfolio.
Diversification becomes especially critical in crypto given the sector's nascency and rapid evolution. Technologies and narratives that dominate today may be obsolete within years as the space matures. By holding HBAR exclusively, you're betting not only on crypto succeeding but on Hedera specifically remaining relevant. Index approaches hedge against picking the wrong horse while maintaining full crypto exposure.
Tax efficiency and rebalancing challenges also favor indices over managing concentrated positions. Token Metrics Indices handle portfolio construction, rebalancing, and position sizing systematically, eliminating the emotional and logistical burden of doing this manually with multiple tokens.
Early access to Token Metrics Indices
Hedera is a high-performance public ledger that emphasizes speed, low fees, and energy efficiency, positioning itself for enterprise and decentralized applications. It uses a unique Hashgraph consensus that enables fast finality and high throughput, paired with a council-governed model that targets real-world use cases like payments, tokenization, and decentralized identity.
HBAR is the native token used for fees, staking, and network security, and it supports smart contracts and decentralized file storage. Adoption draws from partnerships and integrations, though decentralization levels and reliance on institutional demand are often discussed in the community.
Token Metrics AI provides comprehensive context on Hedera's positioning and challenges.
Fundamental Grade: 81.08% (Community 74%, Tokenomics 100%, Exchange 100%, VC 59%, DeFi Scanner 85%).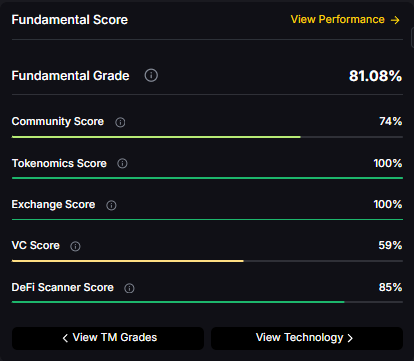
Technology Grade: 62.39% (Activity 58%, Repository 68%, Collaboration 74%, Security 56%, DeFi Scanner 85%).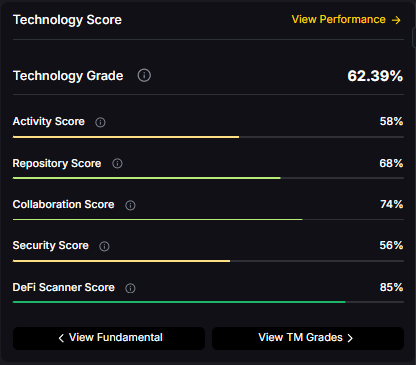
Can HBAR reach $1.00?
Yes. Based on the scenarios, HBAR could reach $1.00 or above in the higher tiers. The 23T tier projects $1.07 in the moon case and the 31T tier projects $1.42 in the moon case. Achieving this requires broad market cap expansion and Hedera maintaining competitive position. Not financial advice.
What price could HBAR reach in the moon case?
Moon case projections range from $0.37 at 8T to $1.42 at 31T. These scenarios assume maximum liquidity expansion and strong Hedera adoption. Diversified strategies aim to capture upside across multiple tokens rather than betting exclusively on any single moon scenario. Not financial advice.
What's the risk/reward profile for HBAR?
Risk and reward span from $0.27 in the lowest bear case to $1.42 in the highest moon case. Downside risks include regulatory or infrastructure setbacks and competitive pressure, while upside drivers include improved liquidity and enterprise adoption. Concentrated positions amplify both tails, while diversified strategies smooth outcomes.
Disclosure
Educational purposes only, not financial advice. Crypto is volatile, concentration amplifies risk, and diversification is a fundamental principle of prudent portfolio construction. Do your own research and manage risk appropriately.
