Top Crypto Trading Platforms in 2025







%201.svg)
%201.svg)
Big news: We’re cranking up the heat on AI-driven crypto analytics with the launch of the Token Metrics API and our official SDK (Software Development Kit). This isn’t just an upgrade – it's a quantum leap, giving traders, hedge funds, developers, and institutions direct access to cutting-edge market intelligence, trading signals, and predictive analytics.
Crypto markets move fast, and having real-time, AI-powered insights can be the difference between catching the next big trend or getting left behind. Until now, traders and quants have been wrestling with scattered data, delayed reporting, and a lack of truly predictive analytics. Not anymore.
The Token Metrics API delivers 32+ high-performance endpoints packed with powerful AI-driven insights right into your lap, including:
Getting started with the Token Metrics API is simple:
At Token Metrics, we believe data should be decentralized, predictive, and actionable.
The Token Metrics API & SDK bring next-gen AI-powered crypto intelligence to anyone looking to trade smarter, build better, and stay ahead of the curve. With our official SDK, developers can plug these insights into their own trading bots, dashboards, and research tools – no need to reinvent the wheel.
%201.svg)
%201.svg)
Shiba Inu operates as a community-driven meme token where price action stems primarily from social sentiment, attention cycles, and speculative trading rather than fundamental value drivers. SHIB exhibits extreme volatility with no defensive characteristics or revenue-generating mechanisms typical of utility tokens. Token Metrics scenarios below provide technical Price Predictions across different market cap environments, though meme tokens correlate more strongly with viral trends and community engagement than systematic market cap models. Positions in SHIB should be sized as high-risk speculative bets with potential for total loss.
Disclosure
Educational purposes only, not financial advice. Crypto is volatile, do your own research and manage risk.
How to read it: Each band blends cycle analogues and market-cap share math with TA guardrails. Base assumes steady adoption and neutral or positive macro. Moon layers in a liquidity boom. Bear assumes muted flows and tighter liquidity. For meme tokens, actual outcomes depend heavily on social trends and community momentum beyond what market cap models capture.
TM Agent baseline: Token Metrics TM Grade is 24.1%, Sell, with a bearish trading signal. The concise 12‑month numeric view centers between
TM Agent numeric view: scenarios center roughly between $0.000005 and $0.000035, with a base case near $0.000012.
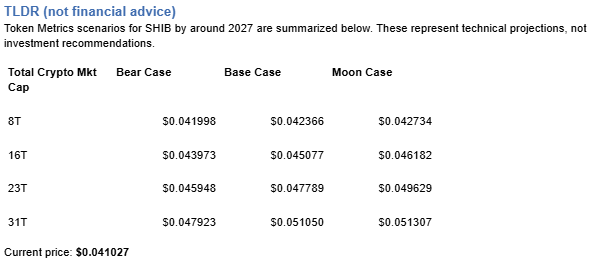
Token Metrics scenarios provide technical price bands across market cap tiers:
8T: At 8 trillion total crypto market cap, SHIB projects to $0.041998 (bear), $0.042366 (base), and $0.042734 (moon).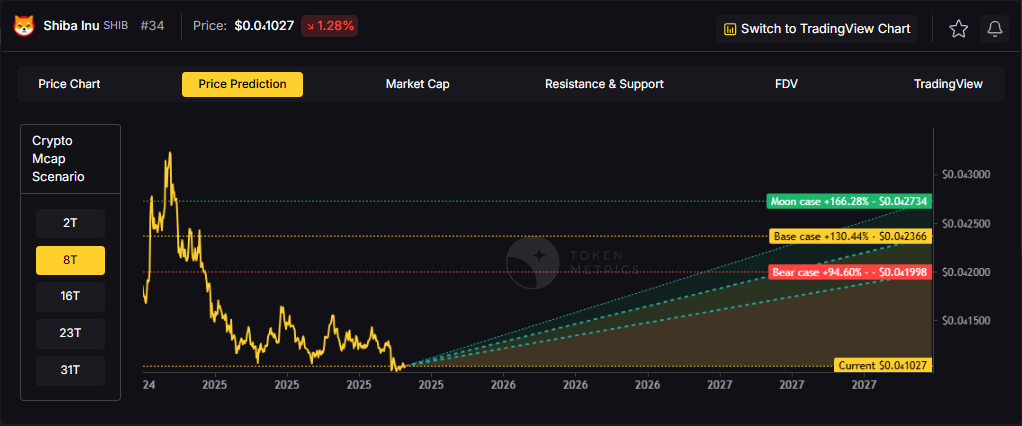
16T: At 16 trillion total crypto market cap, SHIB projects to $0.043973 (bear), $0.045077 (base), and $0.046182 (moon).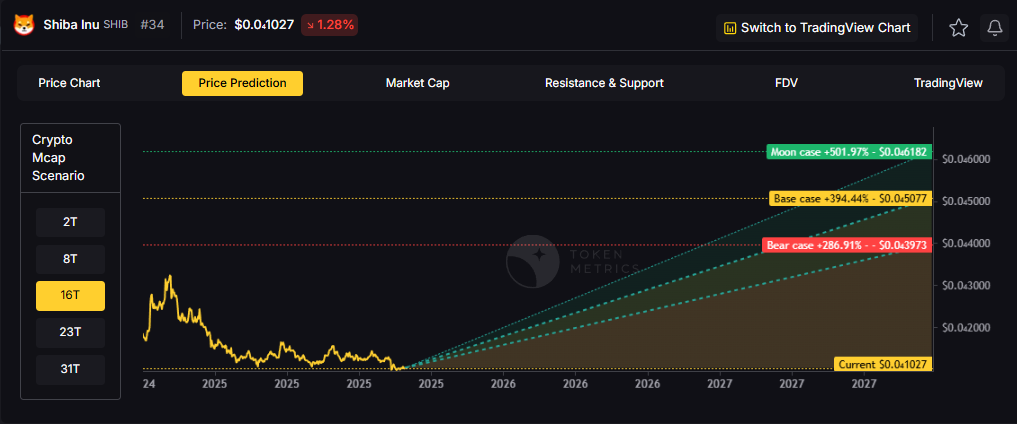
23T: At 23 trillion total crypto market cap, SHIB projects to $0.045948 (bear), $0.047789 (base), and $0.049629 (moon).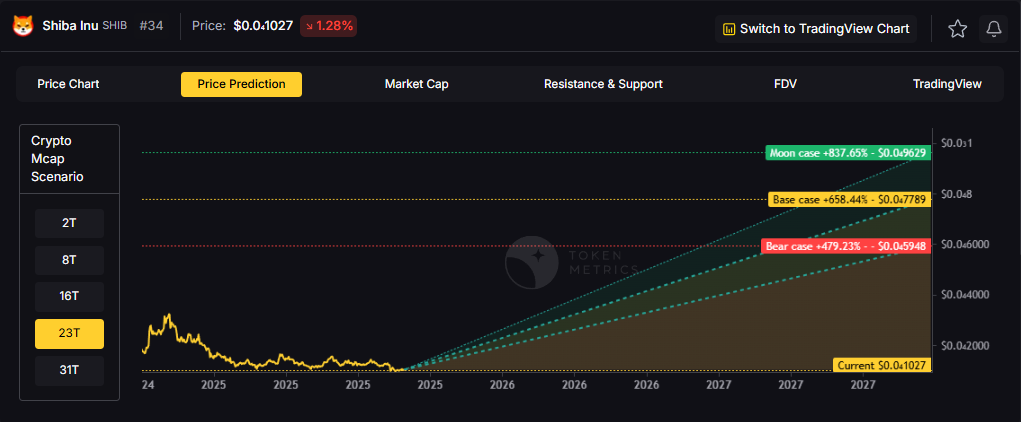
31T: At 31 trillion total crypto market cap, SHIB projects to $0.047923 (bear), $0.051050 (base), and $0.051307 (moon).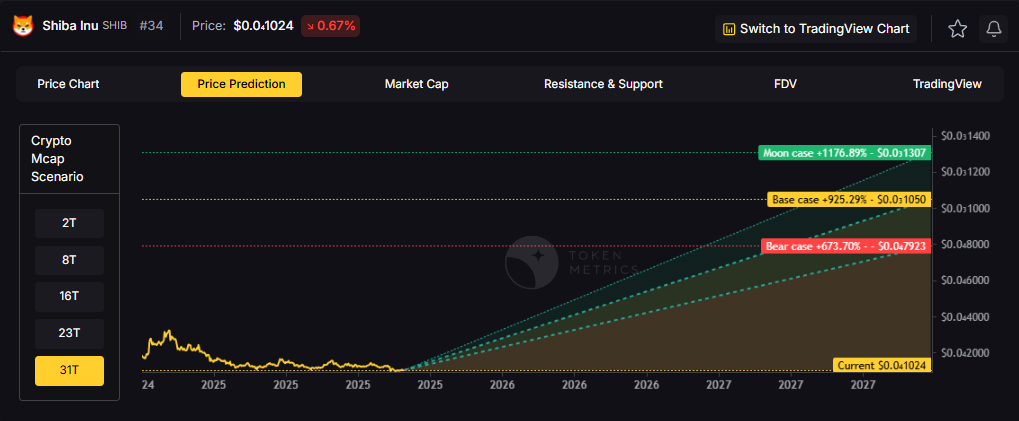
These technical ranges assume meme tokens maintain market cap share proportional to overall crypto growth. Actual outcomes for speculative tokens typically exhibit higher variance and stronger correlation to social trends than these models predict.
Shiba Inu is a meme-born crypto project that centers on community and speculative culture. Unlike utility tokens with specific use cases, SHIB operates primarily as a speculative asset and community symbol. The project focuses on community engagement and entertainment value.
SHIB has demonstrated viral moments and community loyalty within the broader meme token category. The token trades on community sentiment and attention cycles more than fundamentals. Market performance depends heavily on social media attention and broader meme coin cycles.
Token Metrics provides technical analysis, scenario math, and rigorous risk evaluation for hundreds of crypto tokens. Want to dig deeper? Explore our powerful AI-powered ratings and scenario tools here.
Will SHIB 10x from here?
Answer: At current price of $0.041027, a 10x reaches $0.41027. This level does not appear in any of the listed bear, base, or moon scenarios across 8T, 16T, 23T, or 31T tiers. Meme tokens can 10x rapidly during viral moments but can also lose 90%+ just as quickly. Position sizing for potential total loss is critical. Not financial advice.
What are the biggest risks to SHIB?
Answer: Primary risks include attention shifting to newer memes, community fragmentation, developer abandonment, regulatory crackdowns, and liquidity collapse during downturns. Unlike utility tokens with defensive characteristics, SHIB has zero fundamental floor. Price can approach zero if community interest disappears. Total loss is a realistic outcome. Not financial advice.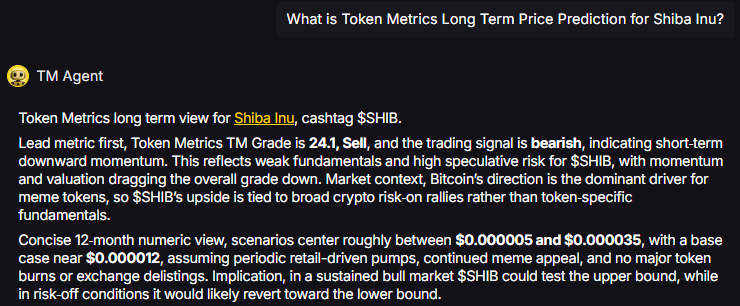
Next Steps
Disclosure
Educational purposes only, not financial advice. SHIB is a highly speculative asset with extreme volatility and high risk of total loss. Meme tokens operate as entertainment and gambling instruments rather than investments. Only allocate capital you can afford to lose entirely. Do your own research and manage risk appropriately.
%201.svg)
%201.svg)
Exchange tokens like WhiteBIT Coin offer leveraged exposure to overall market activity, creating concentration risk around a single platform's success. While WBT can deliver outsized returns during bull markets with high trading volumes, platform-specific risks like regulatory action, security breaches, or competitive displacement amplify downside exposure. Portfolio theory suggests balancing such concentrated bets with broader sector exposure.
The scenarios below show how WBT might perform across different crypto market cap environments. Rather than betting entirely on WhiteBIT Coin's exchange succeeding, diversified strategies blend exchange tokens with L1s, DeFi protocols, and infrastructure plays to capture crypto market growth while mitigating single-platform risk.
Portfolio theory teaches that diversification is the only free lunch in investing. WBT concentration violates this principle by tying your crypto returns to one protocol's fate. Token Metrics Indices blend WhiteBIT Coin with the top one hundred tokens, providing broad exposure to crypto's growth while smoothing volatility through cross-asset diversification. This approach captures market-wide tailwinds without overweighting any single point of failure.
Systematic rebalancing within index strategies creates an additional return source that concentrated positions lack. As some tokens outperform and others lag, regular rebalancing mechanically sells winners and buys laggards, exploiting mean reversion and volatility. Single-token holders miss this rebalancing alpha and often watch concentrated gains evaporate during corrections while index strategies preserve more gains through automated profit-taking.
Beyond returns, diversified indices improve the investor experience by reducing emotional decision-making. Concentrated WBT positions subject you to severe drawdowns that trigger panic selling at bottoms. Indices smooth the ride through natural diversification, making it easier to maintain exposure through full market cycles. Get early access: https://docs.google.com/forms/d/1AnJr8hn51ita6654sRGiiW1K6sE10F1JX-plqTUssXk/preview.

Disclosure
Educational purposes only, not financial advice. Crypto is volatile, do your own research and manage risk.
How to read it: Each band blends cycle analogues and market-cap share math with TA guardrails. Base assumes steady adoption and neutral or positive macro. Moon layers in a liquidity boom. Bear assumes muted flows and tighter liquidity.
TM Agent baseline: Token Metrics long term view for WhiteBIT Coin, cashtag $WBT. Lead metric first, Token Metrics TM Grade is 52.5%, Hold, and the trading signal is bearish, indicating short-term downward momentum. Concise 12-month numeric view: Token Metrics scenarios center roughly between $10 and $85, with a base case near $40.
Token Metrics scenarios span four market cap tiers, each representing different levels of crypto market maturity and liquidity:
8T: At an 8 trillion dollar total crypto market cap, WBT projects to $54.50 in bear conditions, $64.88 in the base case, and $75.26 in bullish scenarios.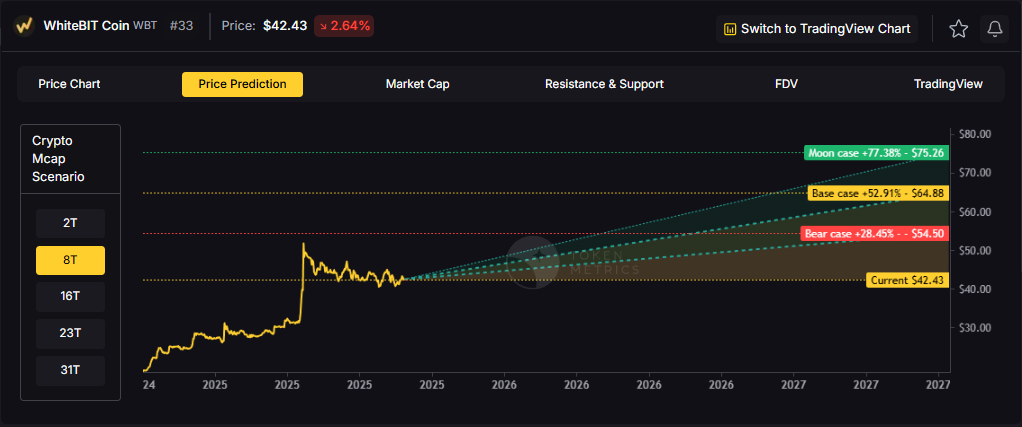
16T: Doubling the market to 16 trillion expands the range to $78.61 (bear), $109.75 (base), and $140.89 (moon).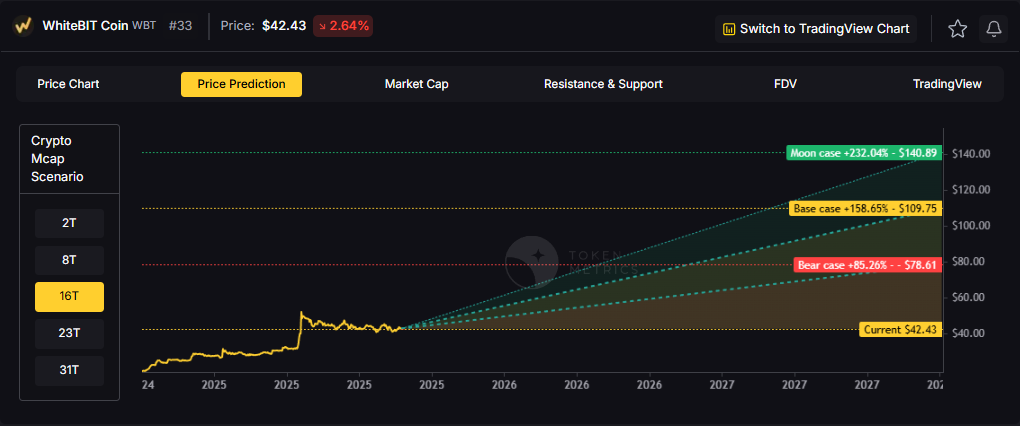
23T: At 23 trillion, the scenarios show $102.71, $154.61, and $206.51 respectively.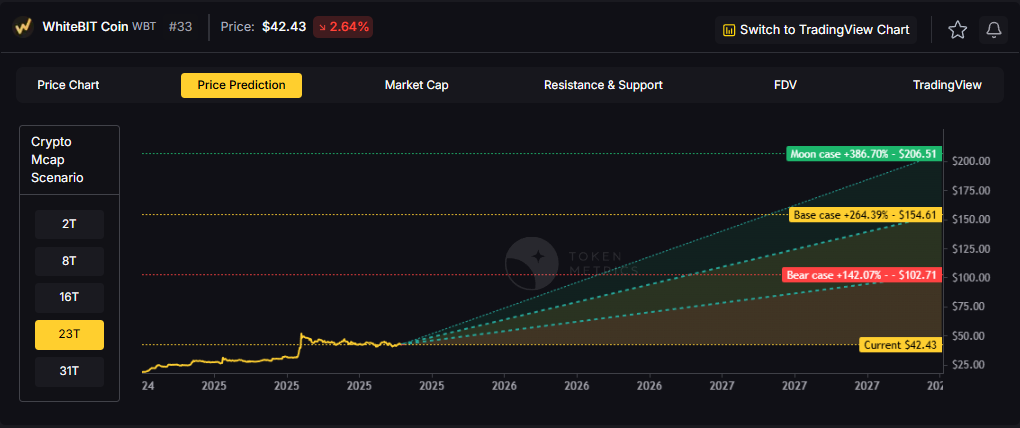
31T: In the maximum liquidity scenario of 31 trillion, WBT could reach $126.81 (bear), $199.47 (base), or $272.13 (moon).
These ranges illustrate potential outcomes for concentrated WBT positions, but investors should weigh whether single-asset exposure matches their risk tolerance or whether diversified strategies better suit their objectives.
WhiteBIT Coin is the native exchange token associated with the WhiteBIT ecosystem. It is designed to support utility on the platform and related services.
WBT typically provides fee discounts and ecosystem benefits where supported. Usage depends on exchange activity and partner integrations.
Token Metrics AI provides comprehensive context on WhiteBIT Coin's positioning and challenges.
Vision: The stated vision for WhiteBIT Coin centers on enhancing user experience within the WhiteBIT exchange ecosystem by providing tangible benefits such as reduced trading fees, access to exclusive features, and participation in platform governance or rewards programs. It aims to strengthen user loyalty and engagement by aligning token holders’ interests with the exchange’s long-term success. While not positioned as a decentralized protocol token, its vision reflects a broader trend of exchanges leveraging tokens to build sustainable, incentivized communities.
Problem: Centralized exchanges often face challenges in retaining active users and differentiating themselves in a competitive market. Users may be deterred by high trading fees, limited reward mechanisms, or lack of influence over platform developments. WhiteBIT Coin aims to address these frictions by introducing a native incentive layer that rewards participation, encourages platform loyalty, and offers cost-saving benefits. This model seeks to improve user engagement and create a more dynamic trading environment on the WhiteBIT platform.
Solution: WhiteBIT Coin serves as a utility token within the WhiteBIT exchange, offering users reduced trading fees, staking opportunities, and access to special events such as token sales or airdrops. It functions as an economic lever to incentivize platform activity and user retention. While specific governance features are not widely documented, such tokens often enable voting on platform upgrades or listing decisions. The solution relies on integrating the token deeply into the exchange’s operational model to ensure consistent demand and utility for holders.
Market Analysis: Exchange tokens like WhiteBIT Coin operate in a competitive landscape led by established players such as Binance Coin (BNB) and KuCoin Token (KCS). While BNB benefits from a vast ecosystem including a launchpad, decentralized exchange, and payment network, WBT focuses on utility within its native exchange. Adoption drivers include the exchange’s trading volume, security track record, and the attractiveness of fee discounts and staking yields. Key risks involve regulatory pressure on centralized exchanges and competition from other exchange tokens that offer similar benefits.
Fundamental Grade: 52.35% (Community 82%, Tokenomics 60%, Exchange 50%, VC —, DeFi Scanner N/A).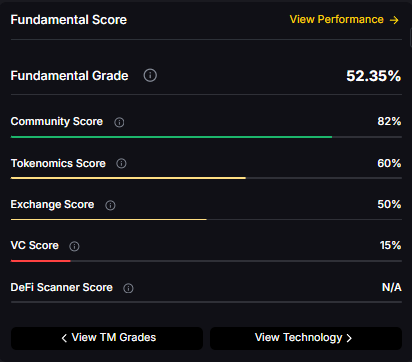
Can WBT reach $100?
Answer: Based on the scenarios, WBT could reach $100 in the 16T base case. The 16T tier projects $109.75 in the base case. Achieving this requires both broad market cap expansion and WhiteBIT Coin maintaining competitive position. Not financial advice.
What's the risk/reward profile for WBT?
Answer: Risk and reward span from $54.50 in the lowest bear case to $272.13 in the highest moon case. Downside risks include regulatory actions and competitive displacement, while upside drivers include expanding access and favorable macro liquidity. Concentrated positions amplify both tails, while diversified strategies smooth outcomes.
What gives WBT value?
Answer: WBT accrues value through fee discounts, staking rewards, access to special events, and potential participation in platform programs. Demand drivers include exchange activity, user growth, and security reputation. While these fundamentals matter, diversified portfolios capture value accrual across multiple tokens rather than betting on one protocol's success.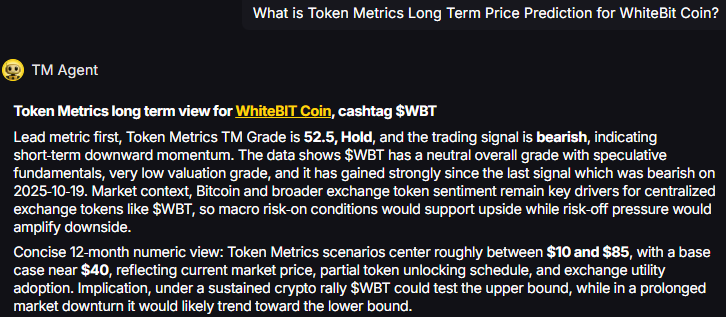
Disclosure
Educational purposes only, not financial advice. Crypto is volatile, concentration amplifies risk, and diversification is a fundamental principle of prudent portfolio construction. Do your own research and manage risk appropriately.
%201.svg)
%201.svg)
Layer 1 tokens capture value through transaction fees and miner economics. Litecoin processes blocks every 2.5 minutes using Proof of Work, targeting fast, low-cost payments. The scenarios below model LTC outcomes across different total crypto market sizes, reflecting network adoption and transaction volume.

Disclosure
Educational purposes only, not financial advice. Crypto is volatile, do your own research and manage risk.
How to read it: Each band blends cycle analogues and market-cap share math with TA guardrails. Base assumes steady adoption and neutral or positive macro. Moon layers in a liquidity boom. Bear assumes muted flows and tighter liquidity.
TM Agent baseline: Token Metrics scenarios center roughly between $35 and $160, with a base case near $75, assuming gradual adoption, occasional retail rotation into major alts, and no major network issues. In a broad crypto rally LTC could test the upper bound, while in risk-off conditions it would likely drift toward the lower bound.
Token Metrics scenarios span four market cap tiers reflecting different crypto market maturity levels:
8T: At an 8 trillion dollar total crypto market cap, LTC projects to $115.80 in bear conditions, $137.79 in the base case, and $159.79 in bullish scenarios.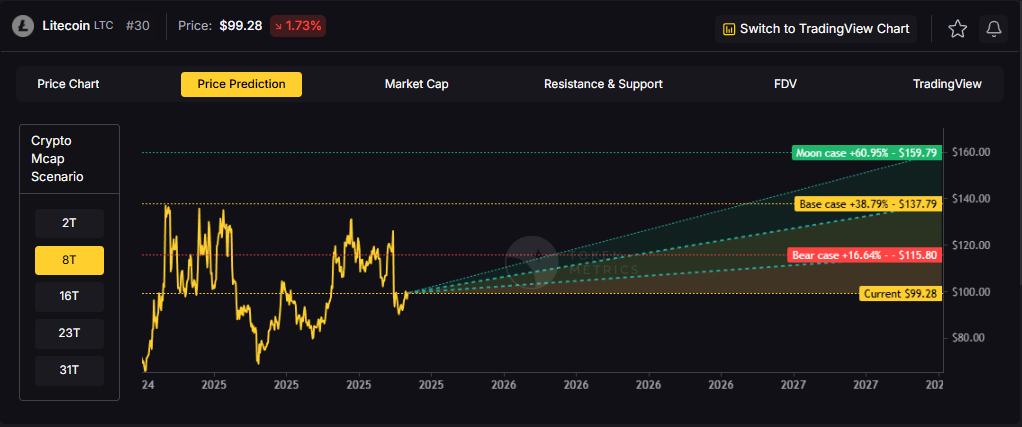
16T: At 16 trillion, the range expands to $154.54 (bear), $220.52 (base), and $286.50 (moon).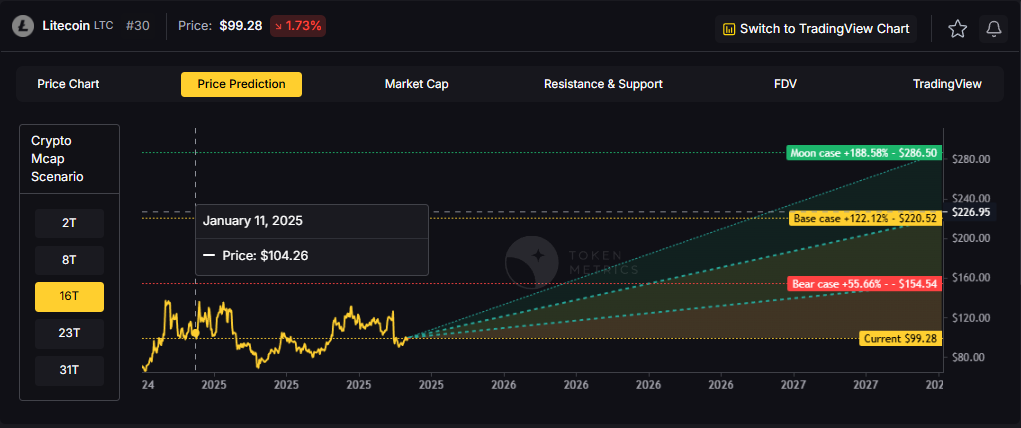
23T: The 23 trillion tier shows $193.28, $303.25, and $413.21 respectively.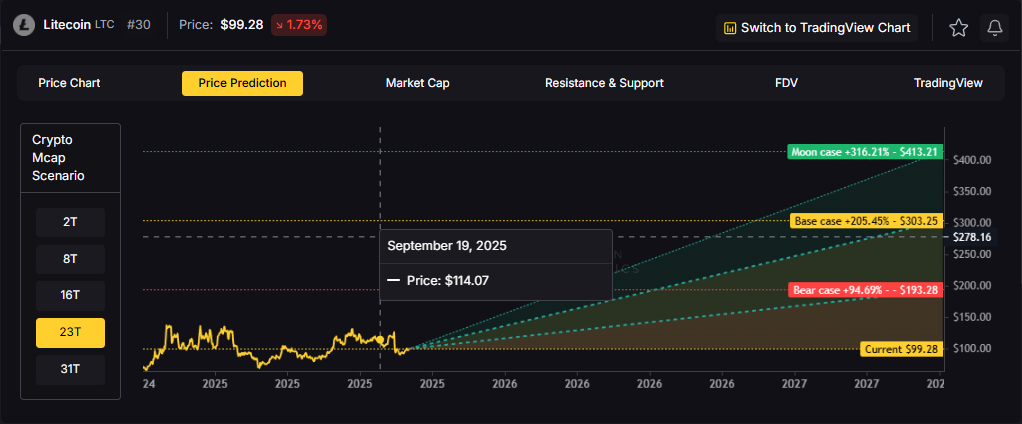
31T: In the maximum liquidity scenario at 31 trillion, LTC reaches $232.03 (bear), $385.98 (base), or $539.92 (moon).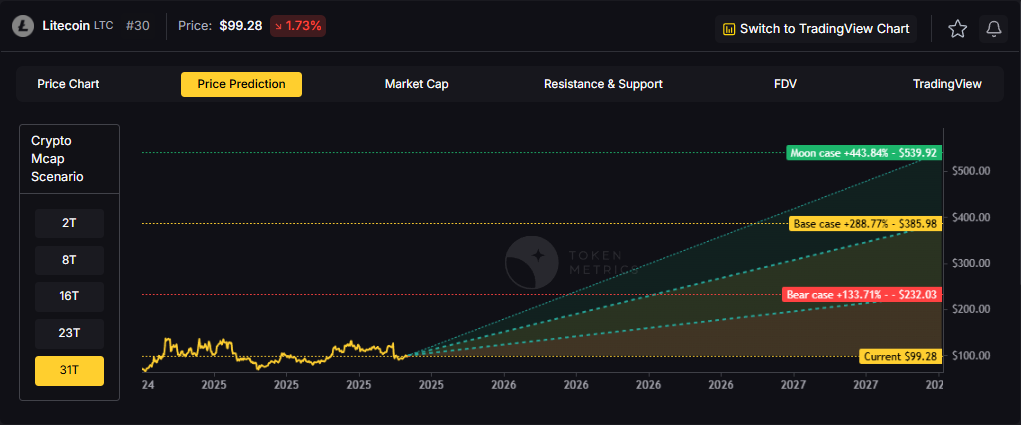
Litecoin is a peer-to-peer cryptocurrency launched in 2011 as an early Bitcoin fork. It uses Proof of Work with Scrypt and targets faster settlement, processing blocks roughly every 2.5 minutes with low fees.
LTC is the native token used for transaction fees and miner rewards. Its primary utilities are fast, low-cost payments and serving as a testing ground for Bitcoin-adjacent upgrades, with adoption in retail payments, remittances, and exchange trading pairs.
Token Metrics AI provides additional context on Litecoin's technical positioning and market dynamics.
Vision: Litecoin's vision is to serve as a fast, low-cost, and accessible digital currency for everyday transactions. It aims to complement Bitcoin by offering quicker settlement times and a more efficient payment system for smaller, frequent transfers.
Problem: Bitcoin's relatively slow block times and rising transaction fees during peak usage make it less ideal for small, frequent payments. This creates a need for a cryptocurrency that maintains security and decentralization while enabling faster and cheaper transactions suitable for daily use.
Solution: Litecoin addresses this by using a 2.5-minute block time and the Scrypt algorithm, which initially allowed broader participation in mining and faster transaction processing. It functions primarily as a payment-focused blockchain, supporting peer-to-peer transfers with low fees and high reliability, without the complexity of smart contract functionality.
Market Analysis: Litecoin operates in the digital payments segment of the cryptocurrency market, often compared to Bitcoin but positioned as a more efficient medium of exchange. While it lacks the smart contract capabilities of platforms like Ethereum or Solana, its simplicity, long-standing network security, and brand recognition give it a stable niche. It competes indirectly with other payment-focused cryptocurrencies like Bitcoin Cash and Dogecoin. Adoption is sustained by its integration across major exchanges and payment services, but growth is limited by the broader shift toward ecosystems offering decentralized applications.
Fundamental Grade: 83.98% (Community 79%, Tokenomics 100%, Exchange 100%, VC —, DeFi Scanner 57%).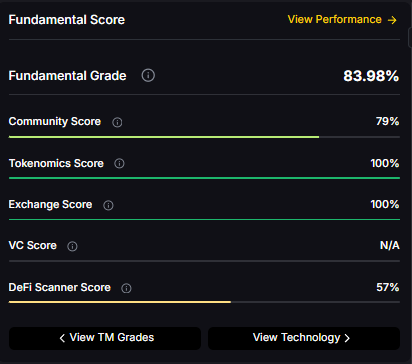
Technology Grade: 46.67% (Activity 51%, Repository 72%, Collaboration 60%, Security 20%, DeFi Scanner 57%).
For comprehensive Litecoin ratings, on-chain analysis, AI-powered price forecasts, and trading signals, go to Token Metrics.
What is LTC used for?
Answer: Primary use cases include fast peer-to-peer payments, low-cost remittances, and exchange settlement/liquidity pairs. LTC holders primarily pay transaction fees and support miner incentives. Adoption depends on active addresses and payment integrations.
What price could LTC reach in the moon case?
Answer: Moon case projections range from $159.79 at 8T to $539.92 at 31T. These scenarios require maximum market cap expansion and strong adoption dynamics. Not financial advice.
Next Steps
• Track live grades and signals: Token Details
Disclosure
Educational purposes only, not financial advice. Crypto is volatile, do your own research and manage risk.

%201.svg)
%201.svg)
Imagine seeing real-time crypto prices, portfolio insights, and token analytics—all in one place, tailored to your needs. Crypto dashboards do exactly this: consolidating blockchain data in one interface, empowering users to track and analyze digital assets with accuracy and speed. But how do you go from scattered data sources to a unified dashboard? This guide will walk you through how APIs unlock this potential and show you the essential steps to building an effective crypto dashboard.
APIs (Application Programming Interfaces) let you access real-time and historical blockchain data, trading signals, and market analytics from external services. By leveraging APIs, you avoid the intensive process of running your own blockchain nodes or manually collecting data from multiple sources. Instead, you use robust, well-documented endpoints from reputable providers to power your dashboard's features.
Key benefits of using APIs for your crypto dashboard include:
Before coding, outline the features you need. Crypto dashboards vary in scope—common modules include:
Choose the API endpoints that map to these features—consider documentation quality, rate limits, and data freshness. Providers such as Token Metrics can provide multi-layered data like real-time prices, technical indicators, and AI-driven analytics in one place.
The backbone of your dashboard is data reliability and coverage. Evaluate potential APIs based on:
Many developers start with free tiers to prototype, then scale up as their dashboard features mature. Consider APIs that deliver extra analytical layers (like social sentiment or AI-generated ratings) if you want to build advanced features.
Sample code for an API request (in JavaScript):
fetch('https://api.example.com/v1/price?symbol=BTC', {
headers: { 'Authorization': 'Bearer YOUR_API_KEY' }
})
.then(response => response.json())
.then(data => {
// Render price in your dashboard
console.log(data);
});
Professional analysts, traders, and hobbyists leverage crypto dashboards for:
For advanced dashboards:
Build Smarter Crypto Apps & AI Agents with Token Metrics
Token Metrics provides real-time prices, trading signals, and on-chain insights all from one powerful API. Grab a Free API Key
A crypto dashboard is a web or mobile interface that aggregates and visualizes various types of cryptocurrency data. Users can track market prices, portfolio holdings, historical charts, and even AI-driven analytics in one convenient display. Dashboards often rely on APIs to fetch up-to-date, actionable information from multiple crypto sources.
While some no-code dashboard tools exist, building a customized crypto dashboard typically requires basic programming knowledge—especially to integrate APIs, process response data, and create dynamic charts. Common languages include JavaScript, Python, or using frameworks like React for the frontend.
Many major crypto API providers offer free tiers or trial access, enabling you to start building dashboards without upfront costs. However, free APIs may have limitations on the number of requests, update frequency, or available data. Consider premium plans as your requirements grow.
Never expose API keys directly in public frontend code. Use environment variables, server-side proxies, or authentication layers to help protect sensitive credentials. Regularly rotate your keys and monitor API usage for unauthorized access.
Yes, some APIs—including those from Token Metrics—provide AI-driven analytics, such as predictive indicators or algorithmic token ratings. Integrating these endpoints enables advanced research and deeper visualization capabilities for end users.
This content is for informational and educational purposes only and does not constitute investment advice or an offer to buy, sell, or recommend any cryptocurrency or service. Always conduct your own research and consult with professional advisors regarding technical integrations and regulatory obligations.
%201.svg)
%201.svg)
APIs are the backbone of many modern applications, especially within the crypto and AI sectors. But with convenience comes risk—leaked or stolen API keys can compromise your app, data, and even your users. Ensuring your API keys are properly protected is vital for any developer or organization integrating with financial, trading, or AI services.
API keys act as digital passports, granting access to services, data, and sensitive operations. In crypto and AI environments, these keys may unlock valuable features such as live price feeds, trading execution, or proprietary AI models. Attackers seek out API keys because they offer a direct route into your systems—potentially allowing unauthorized trades, data exfiltration, or abuse of paid services.
According to security research, exposed API keys are among the most common root causes of data breaches in software development. In high-value areas like cryptocurrency or financial data, a compromised API key can mean immediate and irreversible losses. This makes robust API key management and security a non-negotiable part of your development lifecycle.
Understanding how API keys are stolen is the first step towards preventing it. Attackers employ several strategies to discover and exploit keys:
Each risk vector underscores the importance of treating your API keys as sensitive credentials, on par with passwords or private cryptographic keys.
Effective API key protection requires a combination of technology, process, and vigilance. Here are key best practices to help you minimize your security risks:
Adopting these strategies not only secures your API integration but also strengthens your application's overall security posture.
For applications in high-risk or regulated environments, advanced techniques can further minimize the risk of API key exposure:
Many leading API providers, including those in crypto and AI, offer these advanced controls within their developer portals. Reviewing your provider's best practices and security documentation is always recommended.
The risks associated with API keys in crypto applications are especially pronounced. Malicious actors often scan public repositories for leaked API keys associated with major exchanges, DeFi protocols, or analytics providers. Many high-profile hacks have originated from a single compromised API credential.
Therefore, when working with crypto APIs—such as market data, portfolio management, or trading execution—robust key hygiene is a must. Always treat your API credentials as confidential and regularly review your integrations for possible leaks or misconfigurations. Be extra cautious when using third-party frameworks or libraries, and validate the security of vendor SDKs before integrating.
Build Smarter Crypto Apps & AI Agents with Token Metrics
Token Metrics provides real-time prices, trading signals, and on-chain insights all from one powerful API. Grab a Free API Key
An API key is a unique identifier that grants access to a specific application or service feature. Unlike passwords—which are usually tied to user login—API keys often control programmatic or automated access and must be secured with equal vigilance.
Storing API keys in environment variables is much safer than hardcoding them into codebases. However, ensure these environment variables are protected by server-level access controls and not inadvertently exposed during deployments or logging.
Monitor your API provider dashboard for unexpected activity, such as unauthorized transactions or unusual spikes in requests. Some providers support alerts or allow you to instantly revoke or rotate keys if you suspect exposure.
This practice is discouraged. Different applications should use unique API keys, each with their own permission scope and tracking. If one application is compromised, it won’t affect the security of your other integrations.
Key rotation frequency depends on your application's risk profile and provider requirements. As a rule of thumb, rotate production keys quarterly or after any suspected exposure, and always decommission unused credentials promptly.
This blog post is for informational purposes only and is not investment advice or an endorsement of any product or platform. Always adhere to your organization’s security policies and consult official documentation for technical implementations.
%201.svg)
%201.svg)
In the fast-moving world of crypto and AI-driven apps, secure data access is fundamental. Whether you’re coding a trading bot, building a market viewer, or integrating real-time blockchain analytics, you’ve likely encountered terms like “API key” and “OAuth token.” But what do they mean, and why does the distinction matter for crypto development?
APIs—Application Programming Interfaces—are the foundational links that allow different systems to communicate. In the context of blockchain and crypto, APIs power everything from price trackers and on-chain analytics to decentralized applications (dApps) and automated trading bots.
As crypto applications become more sophisticated and user privacy matters more, how you grant and manage access to these APIs becomes crucial. This is where authentication types—primarily API keys and OAuth tokens—come into play.
API keys are unique identifiers, typically long strings of random characters, issued to developers by a service provider. Here’s what you need to know about API keys:
In crypto, API keys are commonly used for accessing market data feeds, price indexes, trading signals, and even submitting trades on some exchanges or data aggregators.
OAuth (Open Authorization) is a more advanced and flexible framework for secure delegated access. Instead of using static secrets, OAuth introduces a dynamic and user-consent-based way to grant apps access to account data, often via access tokens.
Many major exchanges, wallets, and analytics providers in crypto are adopting OAuth to meet stricter security standards, especially when apps act on behalf of users or need direct account access.
This difference impacts app architecture, user privacy, security compliance, and your ability to scale access securely—especially important in crowded crypto app ecosystems.
Selecting API keys or OAuth depends on your use case:
As regulatory scrutiny grows and user expectations for privacy rise, OAuth is becoming standard for apps handling personal data or sensitive permissions. Still, API keys remain a valid option for public information and backend server communication.
Build Smarter Crypto Apps & AI Agents with Token Metrics
Token Metrics provides real-time prices, trading signals, and on-chain insights all from one powerful API. Grab a Free API Key
API keys can be safe if handled correctly—kept secret, rotated frequently, never exposed in code, and used only over HTTPS. However, for sensitive actions, consider using OAuth or other advanced authentication.
No. OAuth is ideal when you need user-level permissions or deal with personal data. For server-to-server communication or public endpoints, API keys are often sufficient and simpler to implement.
Yes, many crypto API providers support multiple authentication methods—API keys for simple or backend tasks, OAuth for user-driven features. Choose per your app’s needs.
Exposing API keys in public repos, front-end code, or unsecured environments can let attackers steal data, perform unauthorized actions, or rack up service charges. Rotate keys at signs of compromise.
Token Metrics provides robust API key-based access to its crypto data, trading signals, and analytics—perfect for developers seeking immediate integration and reliable security.
This article is for educational purposes only and does not provide investment advice, financial recommendations, or legal guidance. Crypto and API integrations involve technical and security risks—always do your own research and consult accredited professionals as appropriate.

%201.svg)
%201.svg)
As cryptocurrencies and digital assets become more integrated into financial operations and innovations, APIs (Application Programming Interfaces) have emerged as the primary bridges between users, trading bots, analytics platforms, and exchanges. While APIs unlock powerful functionality—like automated trading and real-time data—linking your exchange accounts via APIs also introduces critical security considerations. Protecting your API keys is essential to safeguarding your funds, data, and digital reputation from external threats and accidental losses.
API keys are like digital master keys—long alphanumeric codes generated by crypto exchanges to grant third-party services or tools controlled access to your trading account. Depending on the permissions set, an API key can enable actions such as reading balances, making trades, or withdrawing funds. This convenience, however, comes with risk. If malicious actors obtain your keys, they could execute trades, drain assets, or compromise personal data.
Common threats include:
Recognizing these risks is the first step toward building a robust security approach for API-driven crypto activity.
Securing your API keys starts with effective key management and following exchange best practices:
Following these workflows reduces the risk surface significantly and forms the backbone of secure API integration.
The environments where your code and API keys reside are just as important as the keys themselves. Weak operational security can leave even well-managed keys vulnerable.
Investing in layered security controls around your infrastructure and development pipeline creates holistic protection that complements API best practices.
Before connecting your exchange account to any external tool or platform via APIs, carefully evaluate its security posture. Consider these assessment steps:
Partnering with reputable service providers, like Token Metrics, that clearly prioritize and communicate security, greatly reduces integration risks.
Even with the best defenses, continuous monitoring and a planned response are vital if your API keys are ever exposed. Effective strategies include:
Rapid detection and response minimize the impact of breaches and strengthen your security over time through valuable lessons learned.
Build Smarter Crypto Apps & AI Agents with Token Metrics
Token Metrics provides real-time prices, trading signals, and on-chain insights all from one powerful API. Grab a Free API Key
Only share API keys with platforms you trust and have thoroughly evaluated. Limit permissions, monitor usage, and revoke keys if suspicious activity is detected.
Apply the principle of least privilege. Grant only the permissions the integration or bot requires—commonly, just read or trading access, never withdrawal if not needed.
Best practice is to rotate API keys regularly, at a cadence that fits your operational needs, and immediately after any suspected compromise or when discontinuing a service.
Yes. AI-powered analytics can spot unusual trading patterns or access anomalies—which might indicate theft or security breaches—faster than manual monitoring.
Immediately revoke the affected key, review your account for unauthorized actions, activate additional security measures, and notify your exchange's support team as necessary.
This blog is for educational purposes only and does not constitute investment, trading, or legal advice. Always conduct your own research and apply security best practices when handling APIs and exchange keys.

%201.svg)
%201.svg)
The world of cryptocurrency is driven by fast-evolving technology, and at the core of many innovative projects are crypto APIs. These powerful interfaces let developers, traders, and analysts interact with blockchains, trading platforms, data aggregators, and a wide array of crypto-related services. But with convenience comes an important question: are crypto APIs safe to use?
Crypto APIs (Application Programming Interfaces) are digital bridges that allow applications to communicate with cryptocurrency networks, exchanges, wallets, market data aggregators, and payment services. They are essential for building trading bots, portfolio trackers, AI-powered research tools, DeFi platforms, NFT applications, and much more.
Developers and organizations use crypto APIs to:
But the very functions that make APIs so powerful—easy access to sensitive data, funds, and features—also raise security concerns. Understanding these is crucial to safe and productive API use.
Crypto APIs, much like any web-facing software, can be vulnerable to various threats if not designed and used correctly. Some of the most significant security risks include:
These risks highlight the importance of both provider security and user vigilance when working with any crypto API.
When you choose a crypto API for developing apps, conducting research, or managing data, vetting its security posture is essential. Here are key criteria and actions to consider:
Verify these factors before integrating a crypto API into any project. Utilizing well-reviewed APIs from trusted sources like Token Metrics can further reduce risk exposure.
Safe API use depends as much on user diligence as on the provider’s protections. Follow these guidelines:
Adhering to these practices helps ensure your data, funds, and infrastructure remain as protected as possible when working with crypto APIs.
With the increasing sophistication of both threats and technology, AI-driven tools are emerging as powerful allies in API security. AI can:
Platforms like Token Metrics leverage AI not just for market analysis, but also to enhance the reliability and integrity of their data offerings. When evaluating a crypto API, consider if the provider employs advanced measures, including AI-based monitoring and responsive incident handling.
Build Smarter Crypto Apps & AI Agents with Token Metrics
Token Metrics provides real-time prices, trading signals, and on-chain insights all from one powerful API. Grab a Free API Key
No, the level of security varies between providers. Factors such as authentication methods, documentation, infrastructure security, and support for permission management all affect API safety. Always evaluate each provider individually.
Yes, API keys can be stolen if they are leaked, stored improperly, or targeted via phishing or malware. Proper management—including secret storage and permission limitations—significantly reduces this risk.
Both options can be safe if maintained well. Open-source APIs offer transparency, but require vigilance with updates. Commercial APIs may have dedicated security resources, but users must trust the provider’s disclosures and practices.
Nearly all reputable crypto API providers allow users to revoke (delete/disable) API keys via account settings or developer dashboards. Promptly revoking and rotating compromised keys is essential.
Yes. Many developers build custom APIs to interact with blockchains, but you must implement robust security—including authentication, encryption, and usage controls—to avoid introducing vulnerabilities.
This article is for informational and educational purposes only. It does not constitute investment advice, trading recommendations, financial guidance, or an endorsement of any specific crypto product. Always conduct independent due diligence and consult professional advisors before integrating or relying on technology in sensitive or financial contexts.

%201.svg)
%201.svg)
As cryptocurrency markets become more dynamic and automated trading grows in popularity, the demand for real-time, reliable market data has soared. For developers and quantitative traders, free crypto APIs represent a gateway to capturing and analyzing live data. But just how dependable are these resources when used for real-money, live trading environments?
APIs (Application Programming Interfaces) are the digital bridges that connect traders, bots, and apps to the real-time world of digital assets. Free crypto APIs typically pull live price feeds, order book data, and on-chain signals from exchanges or aggregators. While their accessibility is attractive for independent traders and developers, it’s important to consider the infrastructure behind these offerings.
“Reliability” can mean different things depending on your trading strategy and risk tolerance. In a live trading context, consider these factors:
For example, a scalping bot reacting to slight price changes may be more susceptible to latency and inconsistency than a swing trading algorithm using averaged price data.
While cost-free APIs unlock learning and prototyping opportunities, several risks arise when deploying them in live trading:
Many free APIs offer limited or no customer support. If a connectivity or data issue arises during a live session, troubleshooting and resolution may depend solely on community forums or documentation.
To leverage free crypto APIs effectively for live trading while minimizing operational risk, consider strategic mitigations:
Exploring hybrid approaches—such as combining free APIs for lower-priority tasks (backtesting, monitoring) and premium offerings for mission-critical execution—can balance cost-effectiveness with higher reliability.
Advanced trading increasingly relies on artificial intelligence and machine learning for real-time insights. Modern tools, like Token Metrics, combine AI-driven analytics with unified API access, allowing systematic traders to benefit from a blend of machine intelligence and robust data infrastructure.
For projects scaling toward institutional-grade reliability, partnering with services that demonstrate regular uptime guarantees, verified data sources, transparent change logs, and responsive support stands as a best practice.
Build Smarter Crypto Apps & AI Agents with Token Metrics
Token Metrics provides real-time prices, trading signals, and on-chain insights all from one powerful API. Grab a Free API Key
Accuracy largely depends on the provider. Many free APIs accurately reflect exchange-reported prices, but some may lag or have occasional data outages. For critical decision-making, always monitor results and consider validating with secondary sources.
Typical limitations include request rate caps, reduced data granularity, restricted market coverage, and potential for sudden API changes. Free APIs generally provide less support, documentation, and reliability assurances compared to premium alternatives.
Diversify your data sources, implement real-time monitoring, validate incoming data for unusual gaps, and be prepared to switch providers or endpoints. Modular integration and redundancy help lessen single points of failure.
Some free APIs offer limited historical data, typically at a lower granularity or restricted to recent time windows. Comprehensive historical datasets often require a premium subscription or use of open-source repositories.
Yes. Risks include service interruptions, unexpected endpoint changes, rate limiting, and potentially less accurate or delayed data. Always test your setup rigorously before committing to live trading systems relying on free APIs.
This article is for educational and informational purposes only. It does not constitute investment advice, predictions, or recommendations. Always conduct independent due diligence and consult a professional before making trading or financial decisions.

%201.svg)
%201.svg)
Imagine testing your own crypto trading strategy against years of historical data in just minutes—all without writing custom data pipelines or hunting for spreadsheets. With today’s advanced crypto APIs, backtesting strategies is not just possible; it’s increasingly accessible, scalable, and data-rich. But how exactly do these APIs empower traders, analysts, and developers to scientifically evaluate their approaches before risking any real capital?
Backtesting is the process of simulating a trading strategy using historical market data to gauge its theoretical performance. In the fast-moving world of cryptocurrencies, where volatility is high and market microstructure can change rapidly, backtesting serves as a critical first step to determine whether a strategy is robust or needs refinement.
The goal is to replay past price action under the rules of a trading algorithm or indicator-driven approach, tracking entries, exits, and outcomes as if the trades were placed in real time. Backtesting can help expose hidden risks, optimize parameters, and identify strategies likely to withstand real-world market variability.
Crypto APIs act as bridges between real-time market data, historical databases, and user applications. They streamline access to deep historical candlestick data (OHLCV), order book snapshots, volume, on-chain metrics, and even derived indicators. Instead of manually collecting and cleaning datasets—which can be error-prone and time-consuming—users can retrieve consistent, up-to-date data directly via API endpoints.
Key advantages of using crypto APIs for backtesting include:
Backtesting with crypto APIs generally involves a series of clear steps:
Popular open-source backtesting tools such as Backtrader, QuantConnect, and custom Python scripts often use APIs for dynamic data ingestion. For more advanced research, APIs that provide sentiment or on-chain metrics, such as those from Token Metrics, allow users to experiment with hybrid statistical and AI-driven strategies.
While crypto APIs make backtesting efficient, there are important considerations to keep in mind:
Adhering to robust modeling practices—such as walk-forward validation, parameter sensitivity checks, and realistic simulation of transaction costs—can help reduce many of these risks.
The intersection of AI and crypto API backtesting is opening new frontiers in quantitative research. Machine learning and AI models can analyze vast arrays of features, detect non-obvious patterns, and dynamically adapt strategies based on real-time and historical inputs.
Cutting-edge APIs are supporting this evolution by providing not only raw historical data, but also feature-rich analytics: smart signals, alternative data, and even pre-trained AI/ML models. By integrating these offerings into their backtesting framework, developers and quant teams can iterate on more sophisticated strategies, potentially leading to more robust and adaptive trading algorithms.
Build Smarter Crypto Apps & AI Agents with Token Metrics
Token Metrics provides real-time prices, trading signals, and on-chain insights all from one powerful API. Grab a Free API Key
Crypto APIs typically offer a wide range of data: historical price (OHLCV), order book snapshots, trade history, volume, on-chain analytics, exchange metadata, and sometimes news or sentiment indicators. Comprehensive APIs, like those from Token Metrics, also deliver AI-generated signals and analytics.
Not necessarily. While a working knowledge of Python or another scripting language helps, many open-source backtesting platforms or low-code tools can work with API data. Some API providers also offer interactive documentation and code samples to ease integration.
Yes, many exchanges and analytics platforms provide free tiers of their APIs, though they may limit data range, request frequency, or supported assets. For deeper, enterprise-grade backtesting, paid APIs often provide extended histories and premium analytics.
Watch out for data gaps or errors, curve fitting to historical anomalies, and failing to account for transaction fees or real-world execution delays. Always test strategies on pristine, out-of-sample data for realistic results.
AI and machine learning increasingly help in feature selection, anomaly detection, predictive analytics, and adaptive strategy design. APIs that offer pre-processed AI indicators or alternative data can jumpstart this process, making it more accessible for both novice and advanced researchers.
This article is for informational and educational purposes only. It does not constitute investment, legal, or financial advice. The mention of any tool, platform, or service is for educational context. Always conduct your own research and consult professional advisors before making financial decisions.

%201.svg)
%201.svg)
Managing crypto trading across several exchanges can be complicated, especially as the digital asset market expands rapidly. For developers, traders, and automated systems, switching between multiple exchange platforms often leads to fragmented workflows, inconsistent data, and increased operational risks. But can you solve this challenge by using a single API to trade across multiple crypto exchanges?
APIs, or Application Programming Interfaces, have become the backbone of modern crypto trading. Most centralized exchanges—like Binance, Coinbase, or Kraken—offer proprietary APIs, enabling users to execute trades, obtain real-time prices, manage portfolios, and stream account activity programmatically. Traditionally, each exchange requires users to generate unique API keys and implement its specific syntax and rules, which makes integrating multiple platforms into a unified workflow an ongoing challenge.
Multi-exchange trading is increasingly common for several reasons:
Attempting to manage these scenarios manually—or through siloed APIs—can result in lost efficiency and missed opportunities.
A unified API for crypto trading consolidates access to multiple exchanges behind a single set of endpoints, abstracting the idiosyncrasies of each platform. This approach offers several potential benefits:
Several solutions have emerged to deliver this unified experience. Independent aggregator services and open-source libraries—such as CCXT (CryptoCurrency eXchange Trading Library), 1inch (for DEX aggregation), or specialized enterprise APIs—translate commands from a user into the correct format for the targeted exchange and relay responses back to the application.
Despite their promise, there are important technical and operational considerations when using a unified API to trade across exchanges:
Before adopting a unified API, carefully evaluate each provider’s support for your target exchanges, ongoing maintenance, customer support, and transparency regarding reliability and uptime.
Unified API approaches are particularly valuable for:
Choosing the right multi-exchange API solution depends on your operational needs, preferred data formats, scalability goals, and trust in the vendor’s security protocols. Some organizations also combine unified APIs with bespoke integrations for specialized features or liquidity.
Modern trading strategies are increasingly shaped by AI and predictive analytics. When paired with unified APIs, AI tools can:
For example, platforms like Token Metrics offer AI-powered insights that can be integrated into multi-exchange trading workflows via robust APIs. Access to aggregated signals and analytics enhances decision accuracy and automation capabilities in an increasingly complex trading environment.
Build Smarter Crypto Apps & AI Agents with Token Metrics
Token Metrics provides real-time prices, trading signals, and on-chain insights all from one powerful API. Grab a Free API Key
Coverage varies by provider, but leading multi-exchange APIs often support integrations with major centralized exchanges—like Binance, Coinbase Pro, Kraken, Bitfinex—as well as some decentralized platforms. Always check providers’ documentation for updated support lists.
Yes, consolidating your exchange API keys introduces single points of vulnerability. Use strong authentication, encrypted storage, access controls, and monitor for suspicious access. Select API providers with strong security track records and certifications.
Many unified APIs prioritize compatibility with basic order types (e.g., limit, market orders), but advanced orders may be available only if the destination exchange supports them. Some aggregators implement custom logic to approximate complex order types. Review each API’s documentation for order-type coverage.
Fees are typically passed through transparently to the underlying exchange. Some unified APIs may also levy their own usage or subscription fees. Review the pricing page and terms of service before integrating any multi-exchange API.
Certain unified or aggregator APIs support both exchange types, but you may experience differing levels of feature parity and security requirements. Decentralized exchanges often require wallet-based authentication, which may require additional integration steps.
This article is intended for informational and educational purposes only. It does not constitute financial, investment, or legal advice. Crypto markets carry risk—always conduct your own research and consider regulatory compliance before using trading APIs or integrating with exchanges.

%201.svg)
%201.svg)
As the world of cryptocurrency matures, traders, developers, and analysts are embracing automation to streamline their strategies. Central to this movement is the crypto API—a versatile, programmable gateway that unlocks automated trading, real-time data analysis, and AI-driven decision support. But how exactly do you use a crypto API to create, deploy, and optimize automated trading strategies?
A crypto API (Application Programming Interface) is a set of protocols and tools that enables applications to interact directly with cryptocurrency platforms or data providers. These APIs offer real-time access to market data, trading execution, portfolio balances, and analytics. By integrating APIs, developers and traders can:
This programmability reduces human error, accelerates reaction times, and enables the development of custom trading frameworks tailored to specific risk profiles or market outlooks.
To choose or use a crypto API effectively, it’s important to understand the principal types available:
Selecting the right API or combination depends on your trading objectives, technical skills, and the depth of data or execution automation you require.
Building an automated trading strategy with a crypto API generally involves the following core steps:
By following these steps, you build a feedback loop that can transform manual trade setups into resilient, scalable, and data-driven trading systems.
Utilizing crypto APIs and automated strategies poses unique challenges that require careful planning:
Successful automation relies not only on technical prowess, but also on robust operational safeguards to support consistent performance over time.
Recent advances in AI and machine learning are enhancing the potential of crypto APIs. Here’s how AI is increasingly being woven into automated trading workflows:
Platforms like Token Metrics merge crypto APIs and AI, making it easier for both coders and non-coders to leverage this advanced analytical edge within automated strategies.
Build Smarter Crypto Apps & AI Agents with Token Metrics
Token Metrics provides real-time prices, trading signals, and on-chain insights all from one powerful API. Grab a Free API Key
Popular crypto APIs provide RESTful or WebSocket endpoints, making them accessible from Python, JavaScript, Java, and other modern languages. Official SDKs or community-developed libraries often exist for faster setup.
Yes, backtesting with historical API data allows you to simulate strategy performance, spot weaknesses, and estimate metrics like volatility or drawdown before risking capital in live markets.
Store keys in encrypted environments or secure vaults, use read-only permissions when possible, and rotate credentials regularly. Avoid hard-coding credentials directly into scripts or repositories.
AI, when combined with reliable API-driven data, can surface new signals, manage risk more dynamically, and adapt strategies as market conditions change. It does not guarantee profitability, but it can enhance analysis and responsiveness.
Common mistakes include exceeding API rate limits, insufficient error handling, hardcoding sensitive credentials, underestimating slippage, and failing to monitor or update strategies as conditions evolve.
This article is for educational purposes only and does not constitute investment, financial, or trading advice. Crypto assets and algorithmic trading involve significant risks. Perform your own research and consult a qualified professional before using any trading tools or APIs.


 Create Your Free Account
Create Your Free Account9450 SW Gemini Dr
PMB 59348
Beaverton, Oregon 97008-7105 US
.svg)




.png)
Token Metrics Media LLC is a regular publication of information, analysis, and commentary focused especially on blockchain technology and business, cryptocurrency, blockchain-based tokens, market trends, and trading strategies.
Token Metrics Media LLC does not provide individually tailored investment advice and does not take a subscriber’s or anyone’s personal circumstances into consideration when discussing investments; nor is Token Metrics Advisers LLC registered as an investment adviser or broker-dealer in any jurisdiction.
Information contained herein is not an offer or solicitation to buy, hold, or sell any security. The Token Metrics team has advised and invested in many blockchain companies. A complete list of their advisory roles and current holdings can be viewed here: https://tokenmetrics.com/disclosures.html/
Token Metrics Media LLC relies on information from various sources believed to be reliable, including clients and third parties, but cannot guarantee the accuracy and completeness of that information. Additionally, Token Metrics Media LLC does not provide tax advice, and investors are encouraged to consult with their personal tax advisors.
All investing involves risk, including the possible loss of money you invest, and past performance does not guarantee future performance. Ratings and price predictions are provided for informational and illustrative purposes, and may not reflect actual future performance.



