Top Crypto Trading Platforms in 2025







%201.svg)
%201.svg)
Big news: We’re cranking up the heat on AI-driven crypto analytics with the launch of the Token Metrics API and our official SDK (Software Development Kit). This isn’t just an upgrade – it's a quantum leap, giving traders, hedge funds, developers, and institutions direct access to cutting-edge market intelligence, trading signals, and predictive analytics.
Crypto markets move fast, and having real-time, AI-powered insights can be the difference between catching the next big trend or getting left behind. Until now, traders and quants have been wrestling with scattered data, delayed reporting, and a lack of truly predictive analytics. Not anymore.
The Token Metrics API delivers 32+ high-performance endpoints packed with powerful AI-driven insights right into your lap, including:
Getting started with the Token Metrics API is simple:
At Token Metrics, we believe data should be decentralized, predictive, and actionable.
The Token Metrics API & SDK bring next-gen AI-powered crypto intelligence to anyone looking to trade smarter, build better, and stay ahead of the curve. With our official SDK, developers can plug these insights into their own trading bots, dashboards, and research tools – no need to reinvent the wheel.
%201.svg)
%201.svg)
The biggest gains in crypto rarely come from the majors. They come from Moonshots—fast-moving tokens with breakout potential. The Moonshots API surfaces these candidates programmatically so you can rank, alert, and act inside your product. In this guide, you’ll call /v2/moonshots, display a high-signal list with TM Grade and Bullish tags, and wire it into bots, dashboards, or screeners in minutes. Start by grabbing your key at Get API Key, then Run Hello-TM and Clone a Template to ship fast.
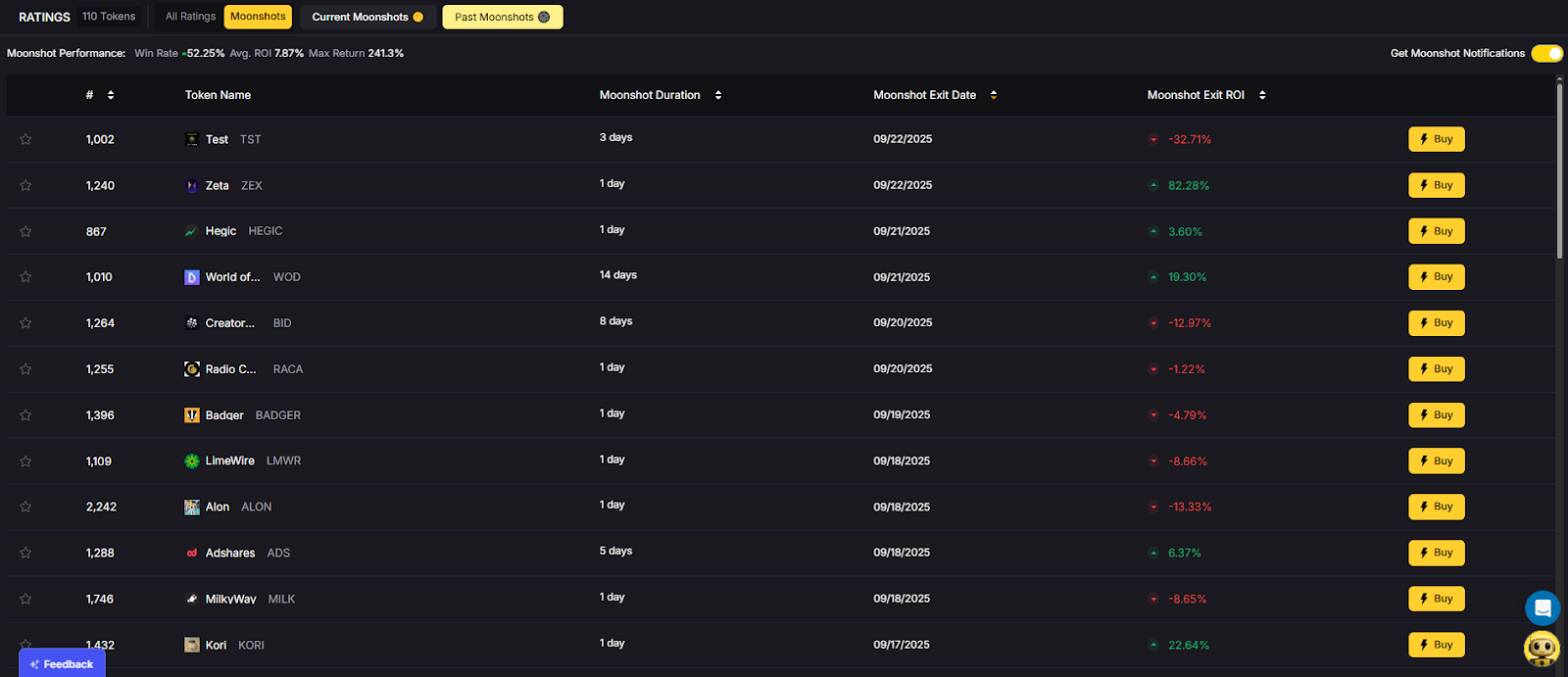
Discovery that converts. Users want more than price tickers—they want a curated, explainable list of high-potential tokens. The moonshots API encapsulates multiple signals into a short list designed for exploration, alerts, and watchlists you can monetize.
Built for builders. The endpoint returns a consistent schema with grade, signal, and context so you can immediately sort, badge, and trigger workflows. With predictable latency and clear filters, you can scale to dashboards, mobile apps, and headless bots without reinventing the discovery pipeline.
The Moonshots API cURL request is right there in the top right of the API Reference. Grab it and start tapping into the potential!
👉 Keep momentum: Get API Key • Run Hello-TM • Clone a Template
Fork a screener or alerting template, plug your key, and deploy. Validate your environment with Hello-TM. When you scale users or need higher limits, compare API plans.
The Moonshots endpoint aggregates a set of evidence—often combining TM Grade, signal state, and momentum/volume context—into a shortlist of breakout candidates. Each row includes a symbol, grade, signal, and timestamp, plus optional reason tags for transparency.
For UX, a common pattern is: headline list → token detail where you render TM Grade (quality), Trading Signals (timing), Support/Resistance (risk placement), Quantmetrics (risk-adjusted performance), and Price Prediction scenarios. This lets users understand why a token was flagged and how to act with risk controls.
Polling vs webhooks. Dashboards typically poll with short-TTL caching. Alerting flows use scheduled jobs or webhooks (where available) to smooth traffic and avoid duplicates. Always make notifications idempotent.
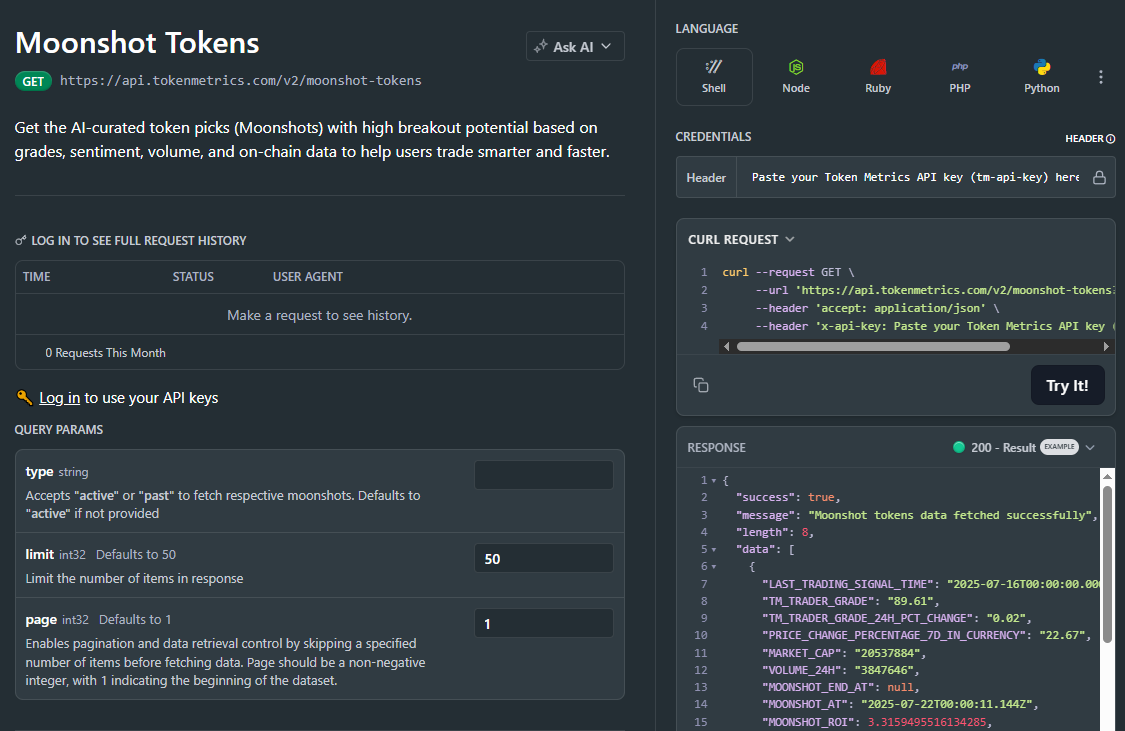
1) What does the Moonshots API return?
A list of breakout candidates with fields such as symbol, tm_grade, signal (often Bullish/Bearish), optional reason tags, and updated_at. Use it to drive discover tabs, alerts, and watchlists.
2) How fresh is the list? What about latency/SLOs?
The endpoint targets predictable latency and timely updates for dashboards and alerts. Use short-TTL caching and queued jobs/webhooks to avoid bursty polling.
3) How do I use Moonshots in a trading workflow?
Common stack: Moonshots for discovery, Trading Signals for timing, Support/Resistance for SL/TP, Quantmetrics for sizing, and Price Prediction for scenario context. Always backtest and paper-trade first.
4) I saw results like “+241%” and a “7.5% average return.” Are these guaranteed?
No. Any historical results are illustrative and not guarantees of future performance. Markets are risky; use risk management and testing.
5) Can I filter the Moonshots list?
Yes—pass parameters like min_grade, signal, and limit (as supported) to tailor to your audience and keep pages fast.
6) Do you provide SDKs or examples?
REST works with JavaScript and Python snippets above. Docs include quickstarts, Postman collections, and templates—start with Run Hello-TM.
7) Pricing, limits, and enterprise SLAs?
Begin free and scale up. See API plans for rate limits and enterprise options.
%201.svg)
%201.svg)
Most traders still draw lines by hand in TradingView. The support and resistance API from Token Metrics auto-calculates clean support and resistance levels from one request, so your dashboard, bot, or alerts can react instantly. In minutes, you’ll call /v2/resistance-support, render actionable levels for any token, and wire them into stops, targets, or notifications. Start by grabbing your key on Get API Key, then Run Hello-TM and Clone a Template to ship a production-ready feature fast.
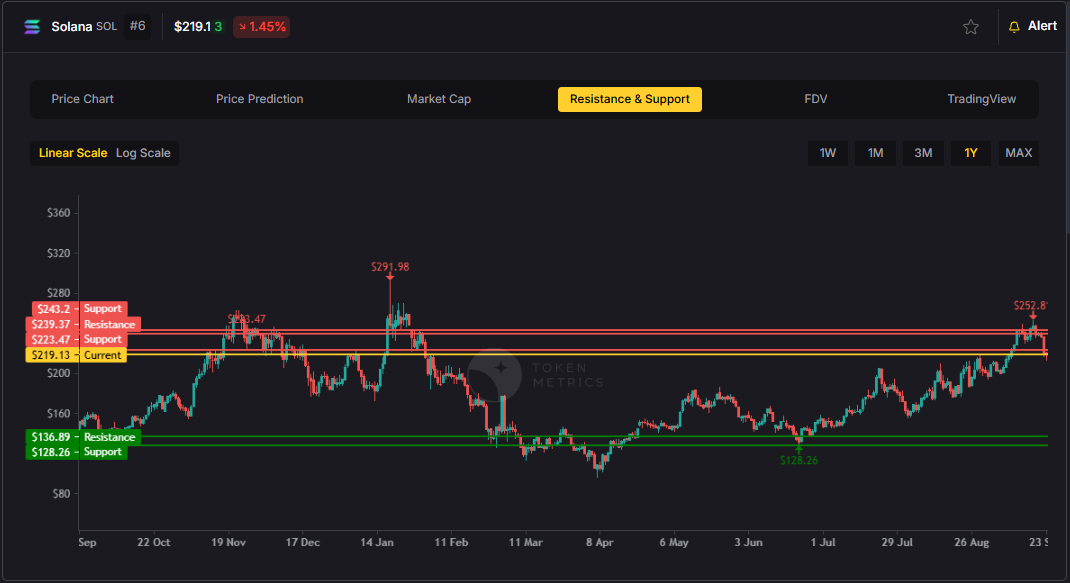
Precision beats guesswork. Hand-drawn lines are subjective and slow. The support and resistance API standardizes levels across assets and timeframes, enabling deterministic stops and take-profits your users (and bots) can trust.
Production-ready by design. A simple REST shape, predictable latency, and clear semantics let you add levels to token pages, automate SL/TP alerts, and build rule-based execution with minimal glue code.
Need the Support and Resistance data? The cURL request for it is in the top right of the API Reference for quick access.
👉 Keep momentum: Get API Key • Run Hello-TM • Clone a Template
Kick off with our quickstarts—fork a bot or dashboard template, plug your key, and deploy. Confirm your environment by Running Hello-TM. When you’re scaling or need webhooks/limits, review API plans.
The Support/Resistance endpoint analyzes recent price structure to produce discrete levels above and below current price, along with strength indicators you can use for priority and styling. Query /v2/resistance-support?symbol=<ASSET>&timeframe=<HORIZON> to receive arrays of level objects and timestamps.
Polling vs webhooks. For dashboards, short-TTL caching and batched fetches keep pages snappy. For bots and alerts, use queued jobs or webhooks (where applicable) to avoid noisy, bursty polling—especially around market opens and major events.
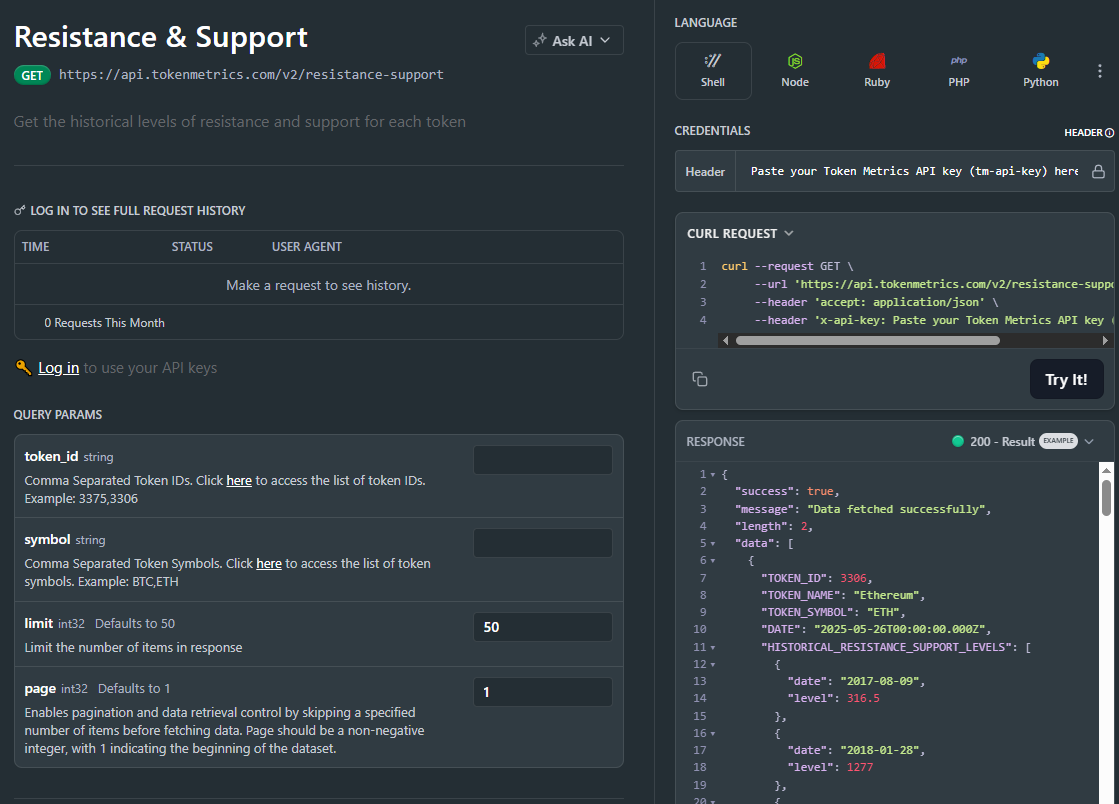
1) What does the Support & Resistance API return?
A JSON payload with arrays of support and resistance levels for a symbol (and optional timeframe), each with a price and strength indicator, plus an update timestamp.
2) How timely are the levels? What are the latency/SLOs?
The endpoint targets predictable latency suitable for dashboards and alerts. Use short-TTL caching for UIs, and queued jobs or webhooks for alerting to smooth traffic.
3) How do I trigger alerts or trades from levels?
Common patterns: alert when price is within X% of a level, touches a level, or breaks beyond with confirmation. Always make downstream actions idempotent and respect rate limits.
4) Can I combine levels with other endpoints?
Yes—pair with /v2/trading-signals for timing, /v2/tm-grade for quality context, and /v2/quantmetrics for risk sizing. This yields a complete decide-plan-execute loop.
5) Which timeframe should I use?
Intraday bots prefer shorter horizons; swing/position dashboards use daily or higher-timeframe levels. Offer a timeframe toggle and cache results per setting.
6) Do you provide SDKs or examples?
Use the REST snippets above (JS/Python). The docs include quickstarts, Postman collections, and templates—start with Run Hello-TM.
7) Pricing, limits, and enterprise SLAs?
Begin free and scale as you grow. See API plans for rate limits and enterprise SLA options.
%201.svg)
%201.svg)
Most traders see price—quants see probabilities. The Quantmetrics API turns raw performance into risk-adjusted stats like Sharpe, Sortino, volatility, drawdown, and CAGR so you can compare tokens objectively and build smarter bots and dashboards. In minutes, you’ll query /v2/quantmetrics, render a clear performance snapshot, and ship a feature that customers trust. Start by grabbing your key at Get API Key, Run Hello-TM to verify your first call, then Clone a Template to go live fast.
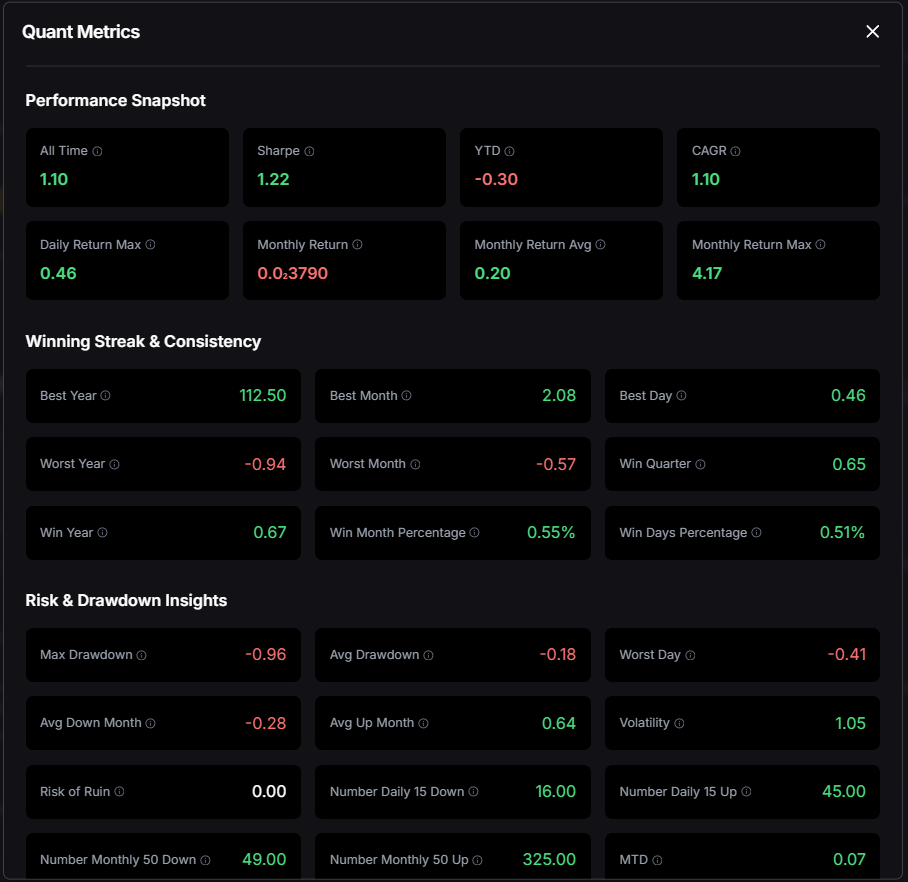
Risk-adjusted truth beats hype. Price alone hides tail risk and whipsaws. Quantmetrics compresses edge, risk, and consistency into metrics that travel across assets and timeframes—so you can rank universes, size positions, and communicate performance like a pro.
Built for dev speed. A clean REST schema, predictable latency, and easy auth mean you can plug Sharpe/Sortino into bots, dashboards, and screeners without maintaining your own analytics pipeline. Pair with caching and batching to serve fast pages at scale.
The Quant Metrics cURL request is located in the top right of the API Reference, allowing you to easily integrate it with your application.
👉 Keep momentum: Get API Key • Run Hello-TM • Clone a Template
Kick off from quickstarts in the docs—fork a dashboard or screener template, plug your key, and deploy in minutes. Validate your environment with Run Hello-TM; when you need more throughput or webhooks, compare API plans.
Quantmetrics computes risk-adjusted performance over a chosen lookback (e.g., 30d, 90d, 1y). You’ll receive a JSON snapshot with core statistics:
Call /v2/quantmetrics?symbol=<ASSET>&window=<LOOKBACK> to fetch the current snapshot. For dashboards spanning many tokens, batch symbols and apply short-TTL caching. If you generate alerts (e.g., “Sharpe crossed 1.5”), run a scheduled job and queue notifications to avoid bursty polling.
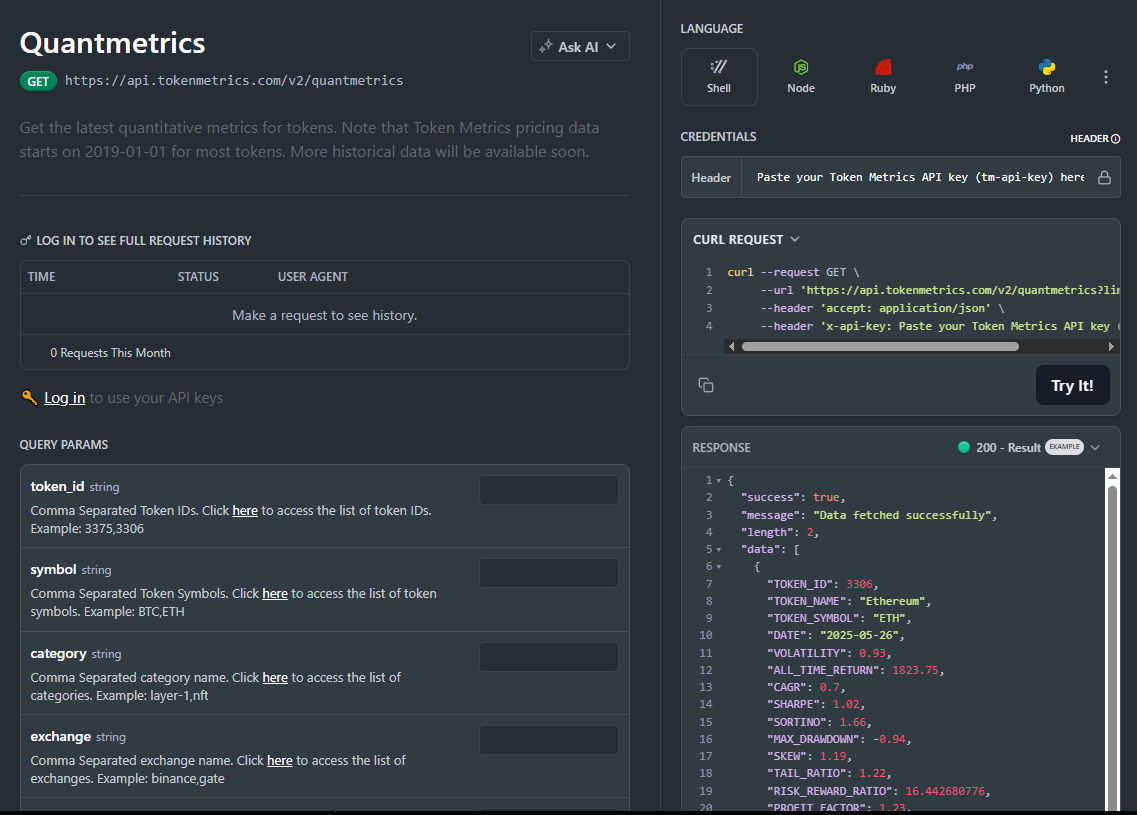
1) What does the Quantmetrics API return?
A JSON snapshot of risk-adjusted metrics (e.g., Sharpe, Sortino, volatility, max drawdown, CAGR) for a symbol and lookback window—ideal for ranking, sizing, and dashboards.
2) How fresh are the stats? What about latency/SLOs?
Responses are engineered for predictable latency. For heavy UI usage, add short-TTL caching and batch requests; for alerts, use scheduled jobs or webhooks where available.
3) Can I use Quantmetrics to size positions in a live bot?
Yes—many quants size inversely to volatility or require Sharpe ≥ X to trade. Always backtest and paper-trade before going live; past results are illustrative, not guarantees.
4) Which lookback window should I choose?
Short windows (30–90d) adapt faster but are noisier; longer windows (6–12m) are steadier but slower to react. Offer users a toggle and cache each window.
5) Do you provide SDKs or examples?
REST is straightforward (JS/Python above). Docs include quickstarts, Postman collections, and templates—start with Run Hello-TM.
6) Polling vs webhooks for quant alerts?
Dashboards usually use cached polling. For threshold alerts (e.g., Sharpe crosses 1.0), run scheduled jobs and queue notifications to keep usage smooth and idempotent.
7) Pricing, limits, and enterprise SLAs?
Begin free and scale up. See API plans for rate limits and enterprise SLA options.
%201.svg)
%201.svg)
In today’s rapidly evolving digital asset landscape, institutions require access to secure, fast, and reliable analytics. The right application programming interface (API) can determine how effectively asset managers, risk teams, and research desks process vast volumes of crypto data. While hundreds of APIs claim to deliver comprehensive analytics, only a select few offer the depth, infrastructure, and granularity needed for institutional decision-making. So, how do you identify which API is best for institutional-level crypto analytics?
Institutions face unique analytics needs compared to retail participants. Core requirements cut across:
The ideal API brings together standardized endpoints, dedicated support, and tooling to enable advanced research, risk, and portfolio management functions.
Let’s explore some of the leading contenders in the market based on institutional needs:
While each API has unique strengths, the best fit depends on the institution’s specific research and operational objectives.
Given the diversity of provider offerings, institutions benefit from a structured evaluation approach:
Using this checklist, decision makers can align their analytics strategy and tooling to their mandate—be it portfolio monitoring, alpha research, or risk mitigation.
Recent advances in AI and machine learning have transformed how institutions derive insights from crypto markets:
For institutional users, the fusion of traditional data feeds with AI-driven signals accelerates research cycles, strengthens automation, and supports more granular risk monitoring.
Once the API shortlist is narrowed, institutions should:
Thoughtful integration enables institutions to maximize analytical rigor, improve operational efficiency, and streamline research and trading workflows.
Build Smarter Crypto Apps & AI Agents with Token Metrics
Token Metrics provides real-time prices, trading signals, and on-chain insights all from one powerful API. Grab a Free API Key
Top APIs offer comprehensive high-frequency data, robust uptime, on-chain analytics, and customizable endpoints. They support integration with institutional systems and provide enterprise-level security and support.
On-chain analytics reveal trends in wallet activity, fund flows, and network health. These insights can help with compliance monitoring, risk assessment, and understanding macro shifts in crypto markets.
AI-driven APIs can automate data aggregation, deliver predictive signals, analyze sentiment, and help institutions uncover hidden patterns—enhancing research speed and accuracy.
The Token Metrics API blends multi-source price, on-chain, and sentiment data with AI-powered analytics for actionable signals, supporting sophisticated institutional workflows.
Key challenges may include harmonizing data formats, managing API limits, ensuring security compliance, and aligning external feeds with internal data pipelines and tools.
This blog is for informational and educational purposes only. It does not constitute financial, investment, or legal advice. No warranties or endorsements of any API provider, platform, or service, including Token Metrics, are implied. Always conduct your own due diligence before integrating any data tool or service.

%201.svg)
%201.svg)
Staying on top of cryptocurrency markets often means harnessing real-time data and powerful analytics. For anyone seeking transparency and automation in tracking digital assets, connecting a crypto API directly to Google Sheets or Excel can transform your workflow. But how does the process actually work, and what are the best practices? Let’s break down the essential steps and considerations for integrating crypto APIs with your favorite spreadsheets, optimizing your data analysis, and ensuring reliability and security.
The first step is selecting a crypto API suited to your needs. APIs are digital interfaces that let apps and platforms request data from cryptocurrency exchanges or analytics providers. Popular APIs deliver live prices, on-chain data, market caps, historical charts, and blockchain analytics.
Examples of reputable APIs include Token Metrics, CoinGecko, CoinMarketCap, Binance, and CryptoCompare. Some, like Token Metrics, also offer AI-driven insights and advanced analytics for deeper research.
Google Sheets offers flexibility for live crypto data tracking, especially with tools like Apps Script and the IMPORTDATA or IMPORTJSON custom functions. Here’s a general approach:
=IMPORTDATA(“URL”) directly in a cell. For JSON APIs (the vast majority), you’ll likely need to add a custom Apps Script function like IMPORTJSON or use third-party add-ons such as API Connector.=IMPORTJSON("https://api.tokenmetrics.com/v1/prices?symbol=BTC", "/price", "noHeaders")). Crypto data will update automatically based on your refresh schedule or script triggers.Sample Apps Script for a GET request might look like:
function GETCRYPTO(url) {
var response = UrlFetchApp.fetch(url);
var json = response.getContentText();
var data = JSON.parse(json);
return data.price;
}
Change the URL as needed for your API endpoint and required parameters.
Microsoft Excel supports API integrations using built-in tools like Power Query (Get & Transform) and VBA scripting. Here is how you can set up a connection:
Note that Excel’s query limits and performance may vary depending on frequency, the amount of retrieved data, and your version (cloud vs desktop).
Why use a crypto API in your spreadsheet at all? Here are common scenarios and tips you should consider:
Security Tip: Always keep API keys secure and avoid sharing spreadsheet templates publicly if they contain credentials. Use environment variables or Google Apps Script’s Properties Service for added safety.
Although spreadsheet integration is powerful, some challenges are common:
When in doubt, consult your API provider’s resource or developer documentation for troubleshooting tips and best practices.
Build Smarter Crypto Apps & AI Agents with Token Metrics
Token Metrics provides real-time prices, trading signals, and on-chain insights all from one powerful API. Grab a Free API Key
Basic integrations, like using APIs that return CSV files, can often work without code via built-in data import features. For JSON APIs or custom data endpoints, familiarity with Apps Script (Google Sheets) or Power Query (Excel) is helpful but not strictly required, especially if you use add-ons like API Connector or plug-and-play solutions.
Supported APIs offer a variety of data: live spot prices, historical price series, market capitalization, volume, on-chain metrics, sentiment scores, and more. The exact data fields depend on each API’s offering and the available endpoints.
Never embed plain text API keys in shared or public spreadsheets. In Google Sheets, use script properties or protected ranges; in Excel, store keys locally or use encrypted variables if automating. Always follow your provider’s credential management guidelines.
Refresh frequency depends on your integration setup. Google Sheets custom scripts or add-ons can update as often as every few minutes, subject to service and API rate limits. Excel’s Power Query typically updates manually or based on scheduled refresh intervals you define.
Choice depends on use case and data depth. Token Metrics is notable for real-time prices, AI-powered analytics, and robust developer support. Other popular choices are CoinGecko, CoinMarketCap, and exchange-specific APIs. Always compare data coverage, reliability, security, and documentation.
This article is for educational and informational purposes only. It does not constitute financial, legal, or investment advice. Always follow best practices for security and usage when working with APIs and spreadsheets.

%201.svg)
%201.svg)
The explosion of NFT and DeFi applications has dramatically increased demand for reliable blockchain data. Developers and analysts seeking to build innovative crypto projects often ask: do crypto APIs provide data for NFTs and DeFi protocols—and if so, how can this fuel smarter apps and insights?
A crypto API (Application Programming Interface) is a set of endpoints and protocols that connect applications to blockchain networks or data aggregators. Instead of directly querying nodes or parsing blocks, developers can access a stream of blockchain-related data in real time via these APIs.
APIs abstract away the technical complexity of on-chain data, providing accessible methods for retrieving token prices, wallet balances, transaction histories, smart contract events, NFT metadata, and DeFi protocol information. This simplifies everything from price tracking to building sophisticated crypto apps and analytics dashboards.
Accurate, up-to-date blockchain data is the foundation for researching NFT projects, assessing DeFi protocol health, and even powering AI agents tasked with blockchain tasks. Leading crypto APIs provide developers with high-level access, so they can focus on building features instead of managing blockchain infrastructure.
Non-fungible tokens (NFTs) have unique data structures, including metadata, ownership history, royalty rules, and underlying assets. Many modern crypto APIs cater to NFT-specific data retrieval, facilitating applications like NFT wallets, galleries, marketplaces, and analytics platforms.
Popular NFT API providers—such as OpenSea API, Alchemy, Moralis, and Token Metrics—differ in their supported blockchains, rate limits, and depth of metadata. When selecting a crypto API for NFTs, compare which standards are supported (ERC-721, ERC-1155, etc.), ease of integration, and the richness of returned data.
Decentralized finance (DeFi) relies on composable smart contracts driving lending, trading, yield farming, liquid staking, and more. Accessing accurate, real-time DeFi data—such as TVL (total value locked), pool balances, lending/borrowing rates, or DEX trade history—is critical for both app builders and researchers.
Leading crypto APIs now offer endpoints dedicated to:
APIs such as DeFi Llama, Covalent, and Token Metrics provide advanced DeFi analytics and are popular among platforms that track yields, compare protocols, or automate investment analyses (without providing investment advice). Evaluate the update frequency, supported chains, and the granularity of metrics before integrating a DeFi data API.
APIs offer significant advantages for NFT and DeFi development:
However, there are trade-offs:
Choosing the right API for NFTs or DeFi often means balancing coverage, performance, cost, and community support. For applications that require the most recent or comprehensive data, combining multiple APIs or supplementing with direct on-chain queries might be needed. Developers should review documentation and test endpoints with sample queries before full integration.
Several innovative crypto products rely on powerful APIs to fetch and process NFT and DeFi data:
Whether for wallet apps, analytical dashboards, or next-gen AI-driven crypto agents, high-quality data APIs serve as the backbone for reliable and scalable blockchain solutions.
Build Smarter Crypto Apps & AI Agents with Token Metrics
Token Metrics provides real-time prices, trading signals, and on-chain insights all from one powerful API. Grab a Free API Key
Yes, most reputable crypto APIs allow you to retrieve NFT metadata, including images, attributes, and collection information, typically by querying token contract addresses and token IDs.
Coverage varies, but leading APIs often support Uniswap, Aave, Compound, Curve, MakerDAO, and other top DeFi protocols on Ethereum and other blockchains. Always check API documentation for a full, updated list.
Many APIs now offer multi-chain support, enabling data retrieval across Ethereum, Polygon, BNB Chain, Avalanche, and other major ecosystems for both NFTs and DeFi activity.
Key factors include supported blockchains and standards, data freshness, endpoint reliability, documentation quality, pricing, and limits on API calls. Community trust and support are also important.
APIs abstract away protocol complexity, offering simplified data endpoints, caching, and error handling, while direct node access requires technical setup but can provide lower-latency data and broader customization.
This article is for informational and educational purposes only. It does not constitute investment advice, an offer, recommendation, or solicitation. Please conduct your own research and seek professional advice where appropriate.

%201.svg)
%201.svg)
For active crypto traders and digital asset holders, the yearly ritual of tax reporting can be complicated and stressful. Each wallet, exchange, and blockchain interacts in ways that fragment your transaction data, making accurate reporting a daunting task. As crypto adoption spreads, can crypto APIs simplify this process and help ensure accurate, timely tax compliance?
APIs, or Application Programming Interfaces, are digital gateways that allow software applications to communicate with one another. In the cryptocurrency world, crypto APIs connect apps, platforms, and users to real-time blockchain data, exchange information, and transaction histories. Major exchanges, wallets, and analytics providers offer APIs so users can access their data programmatically.
For tax reporting, this connection is critical. Crypto APIs enable retrieval of:
This direct access ensures users and accounting tools get the most accurate, comprehensive data possible, setting the foundation for compliant tax reporting.
Crypto tax liabilities are determined by tracking each crypto transaction throughout the tax year—across wallets, exchanges, blockchains, and DeFi protocols. Each step must be captured: acquisitions, sales, conversions, airdrops, rewards, and sometimes even failed transactions. Manually gathering this information often leads to errors and omissions.
Crypto APIs automate much of this process:
By automating data retrieval and normalization, APIs reduce human error and relieve the tedium of manual tracking, increasing the likelihood of accurate and compliant reporting.
Various crypto APIs play roles in tax calculation and compliance workflows. Their capabilities can be grouped into several categories:
Leading crypto tax tools integrate one or more of these API types to connect your accounts and gather all the necessary information for reporting.
No single crypto API covers every trading platform, blockchain, or asset. When selecting an API—or a tax tool that integrates APIs—consider these factors:
Popular crypto tax platforms often act as aggregators, using APIs from multiple sources to ensure complete data capture and reporting accuracy. Advanced APIs—even AI-powered ones like those from Token Metrics—can also provide on-chain analysis and insights that may help proactively monitor tax impacts throughout the year.
Let’s walk through how APIs typically fit into crypto tax workflows:
This streamlined approach saves time, reduces costly mistakes, and, crucially, helps create a paper trail that stands up to tax authority scrutiny. For high-volume traders or those moving assets across multiple platforms, crypto APIs are increasingly seen as a necessity—not just a convenience.
Build Smarter Crypto Apps & AI Agents with Token Metrics
Token Metrics provides real-time prices, trading signals, and on-chain insights all from one powerful API. Grab a Free API Key
Crypto APIs can deliver transaction histories, account balances, historical pricing, and details such as gas fees and blockchain-specific data, enabling accurate calculation of gains, losses, and income for tax filing.
Most reputable APIs utilize read-only permissions, so users can’t withdraw or trade with connected accounts. Always use API keys securely, with platforms that prioritize user data privacy and security.
While many APIs cover major coins and blockchains, full support for NFTs, DeFi protocols, and newer tokens may vary. Check compatibility with your holdings before relying exclusively on APIs for reporting.
Most modern crypto tax platforms offer both—APIs for automated data syncing and manual CSV/Excel uploads as a fallback, ensuring coverage when API connectivity isn’t available for a particular service.
APIs streamline data collection but do not ensure compliance by themselves. Users must ensure all transactions are captured, accurately reported, and filed according to local reporting requirements.
This article is for informational and educational purposes only and does not constitute tax, accounting, or investment advice. Always consult a qualified tax professional for guidance specific to your situation and jurisdiction.

%201.svg)
%201.svg)
Imagine seeing real-time crypto prices, portfolio insights, and token analytics—all in one place, tailored to your needs. Crypto dashboards do exactly this: consolidating blockchain data in one interface, empowering users to track and analyze digital assets with accuracy and speed. But how do you go from scattered data sources to a unified dashboard? This guide will walk you through how APIs unlock this potential and show you the essential steps to building an effective crypto dashboard.
APIs (Application Programming Interfaces) let you access real-time and historical blockchain data, trading signals, and market analytics from external services. By leveraging APIs, you avoid the intensive process of running your own blockchain nodes or manually collecting data from multiple sources. Instead, you use robust, well-documented endpoints from reputable providers to power your dashboard's features.
Key benefits of using APIs for your crypto dashboard include:
Before coding, outline the features you need. Crypto dashboards vary in scope—common modules include:
Choose the API endpoints that map to these features—consider documentation quality, rate limits, and data freshness. Providers such as Token Metrics can provide multi-layered data like real-time prices, technical indicators, and AI-driven analytics in one place.
The backbone of your dashboard is data reliability and coverage. Evaluate potential APIs based on:
Many developers start with free tiers to prototype, then scale up as their dashboard features mature. Consider APIs that deliver extra analytical layers (like social sentiment or AI-generated ratings) if you want to build advanced features.
Sample code for an API request (in JavaScript):
fetch('https://api.example.com/v1/price?symbol=BTC', {
headers: { 'Authorization': 'Bearer YOUR_API_KEY' }
})
.then(response => response.json())
.then(data => {
// Render price in your dashboard
console.log(data);
});
Professional analysts, traders, and hobbyists leverage crypto dashboards for:
For advanced dashboards:
Build Smarter Crypto Apps & AI Agents with Token Metrics
Token Metrics provides real-time prices, trading signals, and on-chain insights all from one powerful API. Grab a Free API Key
A crypto dashboard is a web or mobile interface that aggregates and visualizes various types of cryptocurrency data. Users can track market prices, portfolio holdings, historical charts, and even AI-driven analytics in one convenient display. Dashboards often rely on APIs to fetch up-to-date, actionable information from multiple crypto sources.
While some no-code dashboard tools exist, building a customized crypto dashboard typically requires basic programming knowledge—especially to integrate APIs, process response data, and create dynamic charts. Common languages include JavaScript, Python, or using frameworks like React for the frontend.
Many major crypto API providers offer free tiers or trial access, enabling you to start building dashboards without upfront costs. However, free APIs may have limitations on the number of requests, update frequency, or available data. Consider premium plans as your requirements grow.
Never expose API keys directly in public frontend code. Use environment variables, server-side proxies, or authentication layers to help protect sensitive credentials. Regularly rotate your keys and monitor API usage for unauthorized access.
Yes, some APIs—including those from Token Metrics—provide AI-driven analytics, such as predictive indicators or algorithmic token ratings. Integrating these endpoints enables advanced research and deeper visualization capabilities for end users.
This content is for informational and educational purposes only and does not constitute investment advice or an offer to buy, sell, or recommend any cryptocurrency or service. Always conduct your own research and consult with professional advisors regarding technical integrations and regulatory obligations.
%201.svg)
%201.svg)
APIs are the backbone of many modern applications, especially within the crypto and AI sectors. But with convenience comes risk—leaked or stolen API keys can compromise your app, data, and even your users. Ensuring your API keys are properly protected is vital for any developer or organization integrating with financial, trading, or AI services.
API keys act as digital passports, granting access to services, data, and sensitive operations. In crypto and AI environments, these keys may unlock valuable features such as live price feeds, trading execution, or proprietary AI models. Attackers seek out API keys because they offer a direct route into your systems—potentially allowing unauthorized trades, data exfiltration, or abuse of paid services.
According to security research, exposed API keys are among the most common root causes of data breaches in software development. In high-value areas like cryptocurrency or financial data, a compromised API key can mean immediate and irreversible losses. This makes robust API key management and security a non-negotiable part of your development lifecycle.
Understanding how API keys are stolen is the first step towards preventing it. Attackers employ several strategies to discover and exploit keys:
Each risk vector underscores the importance of treating your API keys as sensitive credentials, on par with passwords or private cryptographic keys.
Effective API key protection requires a combination of technology, process, and vigilance. Here are key best practices to help you minimize your security risks:
Adopting these strategies not only secures your API integration but also strengthens your application's overall security posture.
For applications in high-risk or regulated environments, advanced techniques can further minimize the risk of API key exposure:
Many leading API providers, including those in crypto and AI, offer these advanced controls within their developer portals. Reviewing your provider's best practices and security documentation is always recommended.
The risks associated with API keys in crypto applications are especially pronounced. Malicious actors often scan public repositories for leaked API keys associated with major exchanges, DeFi protocols, or analytics providers. Many high-profile hacks have originated from a single compromised API credential.
Therefore, when working with crypto APIs—such as market data, portfolio management, or trading execution—robust key hygiene is a must. Always treat your API credentials as confidential and regularly review your integrations for possible leaks or misconfigurations. Be extra cautious when using third-party frameworks or libraries, and validate the security of vendor SDKs before integrating.
Build Smarter Crypto Apps & AI Agents with Token Metrics
Token Metrics provides real-time prices, trading signals, and on-chain insights all from one powerful API. Grab a Free API Key
An API key is a unique identifier that grants access to a specific application or service feature. Unlike passwords—which are usually tied to user login—API keys often control programmatic or automated access and must be secured with equal vigilance.
Storing API keys in environment variables is much safer than hardcoding them into codebases. However, ensure these environment variables are protected by server-level access controls and not inadvertently exposed during deployments or logging.
Monitor your API provider dashboard for unexpected activity, such as unauthorized transactions or unusual spikes in requests. Some providers support alerts or allow you to instantly revoke or rotate keys if you suspect exposure.
This practice is discouraged. Different applications should use unique API keys, each with their own permission scope and tracking. If one application is compromised, it won’t affect the security of your other integrations.
Key rotation frequency depends on your application's risk profile and provider requirements. As a rule of thumb, rotate production keys quarterly or after any suspected exposure, and always decommission unused credentials promptly.
This blog post is for informational purposes only and is not investment advice or an endorsement of any product or platform. Always adhere to your organization’s security policies and consult official documentation for technical implementations.
%201.svg)
%201.svg)
In the fast-moving world of crypto and AI-driven apps, secure data access is fundamental. Whether you’re coding a trading bot, building a market viewer, or integrating real-time blockchain analytics, you’ve likely encountered terms like “API key” and “OAuth token.” But what do they mean, and why does the distinction matter for crypto development?
APIs—Application Programming Interfaces—are the foundational links that allow different systems to communicate. In the context of blockchain and crypto, APIs power everything from price trackers and on-chain analytics to decentralized applications (dApps) and automated trading bots.
As crypto applications become more sophisticated and user privacy matters more, how you grant and manage access to these APIs becomes crucial. This is where authentication types—primarily API keys and OAuth tokens—come into play.
API keys are unique identifiers, typically long strings of random characters, issued to developers by a service provider. Here’s what you need to know about API keys:
In crypto, API keys are commonly used for accessing market data feeds, price indexes, trading signals, and even submitting trades on some exchanges or data aggregators.
OAuth (Open Authorization) is a more advanced and flexible framework for secure delegated access. Instead of using static secrets, OAuth introduces a dynamic and user-consent-based way to grant apps access to account data, often via access tokens.
Many major exchanges, wallets, and analytics providers in crypto are adopting OAuth to meet stricter security standards, especially when apps act on behalf of users or need direct account access.
This difference impacts app architecture, user privacy, security compliance, and your ability to scale access securely—especially important in crowded crypto app ecosystems.
Selecting API keys or OAuth depends on your use case:
As regulatory scrutiny grows and user expectations for privacy rise, OAuth is becoming standard for apps handling personal data or sensitive permissions. Still, API keys remain a valid option for public information and backend server communication.
Build Smarter Crypto Apps & AI Agents with Token Metrics
Token Metrics provides real-time prices, trading signals, and on-chain insights all from one powerful API. Grab a Free API Key
API keys can be safe if handled correctly—kept secret, rotated frequently, never exposed in code, and used only over HTTPS. However, for sensitive actions, consider using OAuth or other advanced authentication.
No. OAuth is ideal when you need user-level permissions or deal with personal data. For server-to-server communication or public endpoints, API keys are often sufficient and simpler to implement.
Yes, many crypto API providers support multiple authentication methods—API keys for simple or backend tasks, OAuth for user-driven features. Choose per your app’s needs.
Exposing API keys in public repos, front-end code, or unsecured environments can let attackers steal data, perform unauthorized actions, or rack up service charges. Rotate keys at signs of compromise.
Token Metrics provides robust API key-based access to its crypto data, trading signals, and analytics—perfect for developers seeking immediate integration and reliable security.
This article is for educational purposes only and does not provide investment advice, financial recommendations, or legal guidance. Crypto and API integrations involve technical and security risks—always do your own research and consult accredited professionals as appropriate.

%201.svg)
%201.svg)
As cryptocurrencies and digital assets become more integrated into financial operations and innovations, APIs (Application Programming Interfaces) have emerged as the primary bridges between users, trading bots, analytics platforms, and exchanges. While APIs unlock powerful functionality—like automated trading and real-time data—linking your exchange accounts via APIs also introduces critical security considerations. Protecting your API keys is essential to safeguarding your funds, data, and digital reputation from external threats and accidental losses.
API keys are like digital master keys—long alphanumeric codes generated by crypto exchanges to grant third-party services or tools controlled access to your trading account. Depending on the permissions set, an API key can enable actions such as reading balances, making trades, or withdrawing funds. This convenience, however, comes with risk. If malicious actors obtain your keys, they could execute trades, drain assets, or compromise personal data.
Common threats include:
Recognizing these risks is the first step toward building a robust security approach for API-driven crypto activity.
Securing your API keys starts with effective key management and following exchange best practices:
Following these workflows reduces the risk surface significantly and forms the backbone of secure API integration.
The environments where your code and API keys reside are just as important as the keys themselves. Weak operational security can leave even well-managed keys vulnerable.
Investing in layered security controls around your infrastructure and development pipeline creates holistic protection that complements API best practices.
Before connecting your exchange account to any external tool or platform via APIs, carefully evaluate its security posture. Consider these assessment steps:
Partnering with reputable service providers, like Token Metrics, that clearly prioritize and communicate security, greatly reduces integration risks.
Even with the best defenses, continuous monitoring and a planned response are vital if your API keys are ever exposed. Effective strategies include:
Rapid detection and response minimize the impact of breaches and strengthen your security over time through valuable lessons learned.
Build Smarter Crypto Apps & AI Agents with Token Metrics
Token Metrics provides real-time prices, trading signals, and on-chain insights all from one powerful API. Grab a Free API Key
Only share API keys with platforms you trust and have thoroughly evaluated. Limit permissions, monitor usage, and revoke keys if suspicious activity is detected.
Apply the principle of least privilege. Grant only the permissions the integration or bot requires—commonly, just read or trading access, never withdrawal if not needed.
Best practice is to rotate API keys regularly, at a cadence that fits your operational needs, and immediately after any suspected compromise or when discontinuing a service.
Yes. AI-powered analytics can spot unusual trading patterns or access anomalies—which might indicate theft or security breaches—faster than manual monitoring.
Immediately revoke the affected key, review your account for unauthorized actions, activate additional security measures, and notify your exchange's support team as necessary.
This blog is for educational purposes only and does not constitute investment, trading, or legal advice. Always conduct your own research and apply security best practices when handling APIs and exchange keys.

%201.svg)
%201.svg)
The world of cryptocurrency is driven by fast-evolving technology, and at the core of many innovative projects are crypto APIs. These powerful interfaces let developers, traders, and analysts interact with blockchains, trading platforms, data aggregators, and a wide array of crypto-related services. But with convenience comes an important question: are crypto APIs safe to use?
Crypto APIs (Application Programming Interfaces) are digital bridges that allow applications to communicate with cryptocurrency networks, exchanges, wallets, market data aggregators, and payment services. They are essential for building trading bots, portfolio trackers, AI-powered research tools, DeFi platforms, NFT applications, and much more.
Developers and organizations use crypto APIs to:
But the very functions that make APIs so powerful—easy access to sensitive data, funds, and features—also raise security concerns. Understanding these is crucial to safe and productive API use.
Crypto APIs, much like any web-facing software, can be vulnerable to various threats if not designed and used correctly. Some of the most significant security risks include:
These risks highlight the importance of both provider security and user vigilance when working with any crypto API.
When you choose a crypto API for developing apps, conducting research, or managing data, vetting its security posture is essential. Here are key criteria and actions to consider:
Verify these factors before integrating a crypto API into any project. Utilizing well-reviewed APIs from trusted sources like Token Metrics can further reduce risk exposure.
Safe API use depends as much on user diligence as on the provider’s protections. Follow these guidelines:
Adhering to these practices helps ensure your data, funds, and infrastructure remain as protected as possible when working with crypto APIs.
With the increasing sophistication of both threats and technology, AI-driven tools are emerging as powerful allies in API security. AI can:
Platforms like Token Metrics leverage AI not just for market analysis, but also to enhance the reliability and integrity of their data offerings. When evaluating a crypto API, consider if the provider employs advanced measures, including AI-based monitoring and responsive incident handling.
Build Smarter Crypto Apps & AI Agents with Token Metrics
Token Metrics provides real-time prices, trading signals, and on-chain insights all from one powerful API. Grab a Free API Key
No, the level of security varies between providers. Factors such as authentication methods, documentation, infrastructure security, and support for permission management all affect API safety. Always evaluate each provider individually.
Yes, API keys can be stolen if they are leaked, stored improperly, or targeted via phishing or malware. Proper management—including secret storage and permission limitations—significantly reduces this risk.
Both options can be safe if maintained well. Open-source APIs offer transparency, but require vigilance with updates. Commercial APIs may have dedicated security resources, but users must trust the provider’s disclosures and practices.
Nearly all reputable crypto API providers allow users to revoke (delete/disable) API keys via account settings or developer dashboards. Promptly revoking and rotating compromised keys is essential.
Yes. Many developers build custom APIs to interact with blockchains, but you must implement robust security—including authentication, encryption, and usage controls—to avoid introducing vulnerabilities.
This article is for informational and educational purposes only. It does not constitute investment advice, trading recommendations, financial guidance, or an endorsement of any specific crypto product. Always conduct independent due diligence and consult professional advisors before integrating or relying on technology in sensitive or financial contexts.


 Create Your Free Account
Create Your Free Account9450 SW Gemini Dr
PMB 59348
Beaverton, Oregon 97008-7105 US
.svg)




.png)
Token Metrics Media LLC is a regular publication of information, analysis, and commentary focused especially on blockchain technology and business, cryptocurrency, blockchain-based tokens, market trends, and trading strategies.
Token Metrics Media LLC does not provide individually tailored investment advice and does not take a subscriber’s or anyone’s personal circumstances into consideration when discussing investments; nor is Token Metrics Advisers LLC registered as an investment adviser or broker-dealer in any jurisdiction.
Information contained herein is not an offer or solicitation to buy, hold, or sell any security. The Token Metrics team has advised and invested in many blockchain companies. A complete list of their advisory roles and current holdings can be viewed here: https://tokenmetrics.com/disclosures.html/
Token Metrics Media LLC relies on information from various sources believed to be reliable, including clients and third parties, but cannot guarantee the accuracy and completeness of that information. Additionally, Token Metrics Media LLC does not provide tax advice, and investors are encouraged to consult with their personal tax advisors.
All investing involves risk, including the possible loss of money you invest, and past performance does not guarantee future performance. Ratings and price predictions are provided for informational and illustrative purposes, and may not reflect actual future performance.



