Top Crypto Trading Platforms in 2025







%201.svg)
%201.svg)
Big news: We’re cranking up the heat on AI-driven crypto analytics with the launch of the Token Metrics API and our official SDK (Software Development Kit). This isn’t just an upgrade – it's a quantum leap, giving traders, hedge funds, developers, and institutions direct access to cutting-edge market intelligence, trading signals, and predictive analytics.
Crypto markets move fast, and having real-time, AI-powered insights can be the difference between catching the next big trend or getting left behind. Until now, traders and quants have been wrestling with scattered data, delayed reporting, and a lack of truly predictive analytics. Not anymore.
The Token Metrics API delivers 32+ high-performance endpoints packed with powerful AI-driven insights right into your lap, including:
Getting started with the Token Metrics API is simple:
At Token Metrics, we believe data should be decentralized, predictive, and actionable.
The Token Metrics API & SDK bring next-gen AI-powered crypto intelligence to anyone looking to trade smarter, build better, and stay ahead of the curve. With our official SDK, developers can plug these insights into their own trading bots, dashboards, and research tools – no need to reinvent the wheel.
%201.svg)
%201.svg)
The biggest gains in crypto rarely come from the majors. They come from Moonshots—fast-moving tokens with breakout potential. The Moonshots API surfaces these candidates programmatically so you can rank, alert, and act inside your product. In this guide, you’ll call /v2/moonshots, display a high-signal list with TM Grade and Bullish tags, and wire it into bots, dashboards, or screeners in minutes. Start by grabbing your key at Get API Key, then Run Hello-TM and Clone a Template to ship fast.
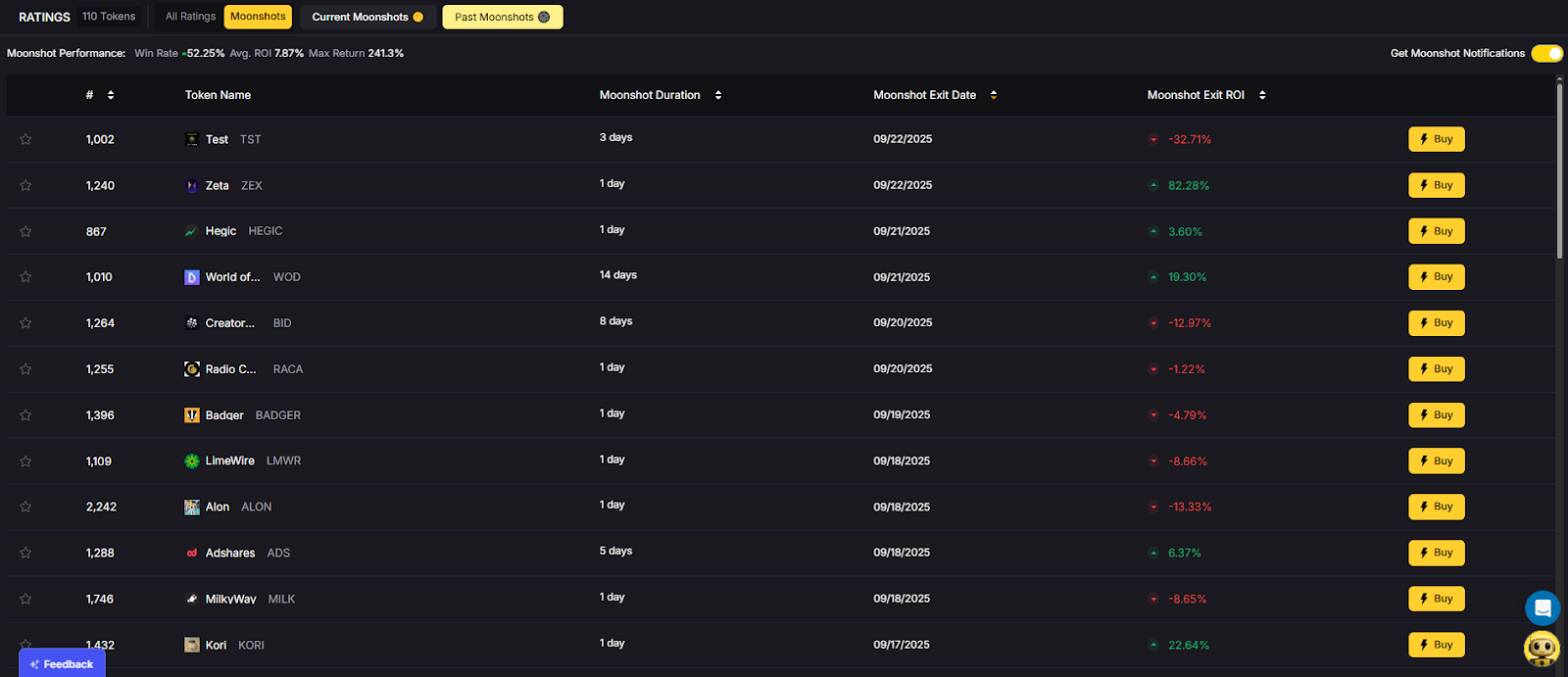
Discovery that converts. Users want more than price tickers—they want a curated, explainable list of high-potential tokens. The moonshots API encapsulates multiple signals into a short list designed for exploration, alerts, and watchlists you can monetize.
Built for builders. The endpoint returns a consistent schema with grade, signal, and context so you can immediately sort, badge, and trigger workflows. With predictable latency and clear filters, you can scale to dashboards, mobile apps, and headless bots without reinventing the discovery pipeline.
The Moonshots API cURL request is right there in the top right of the API Reference. Grab it and start tapping into the potential!
👉 Keep momentum: Get API Key • Run Hello-TM • Clone a Template
Fork a screener or alerting template, plug your key, and deploy. Validate your environment with Hello-TM. When you scale users or need higher limits, compare API plans.
The Moonshots endpoint aggregates a set of evidence—often combining TM Grade, signal state, and momentum/volume context—into a shortlist of breakout candidates. Each row includes a symbol, grade, signal, and timestamp, plus optional reason tags for transparency.
For UX, a common pattern is: headline list → token detail where you render TM Grade (quality), Trading Signals (timing), Support/Resistance (risk placement), Quantmetrics (risk-adjusted performance), and Price Prediction scenarios. This lets users understand why a token was flagged and how to act with risk controls.
Polling vs webhooks. Dashboards typically poll with short-TTL caching. Alerting flows use scheduled jobs or webhooks (where available) to smooth traffic and avoid duplicates. Always make notifications idempotent.
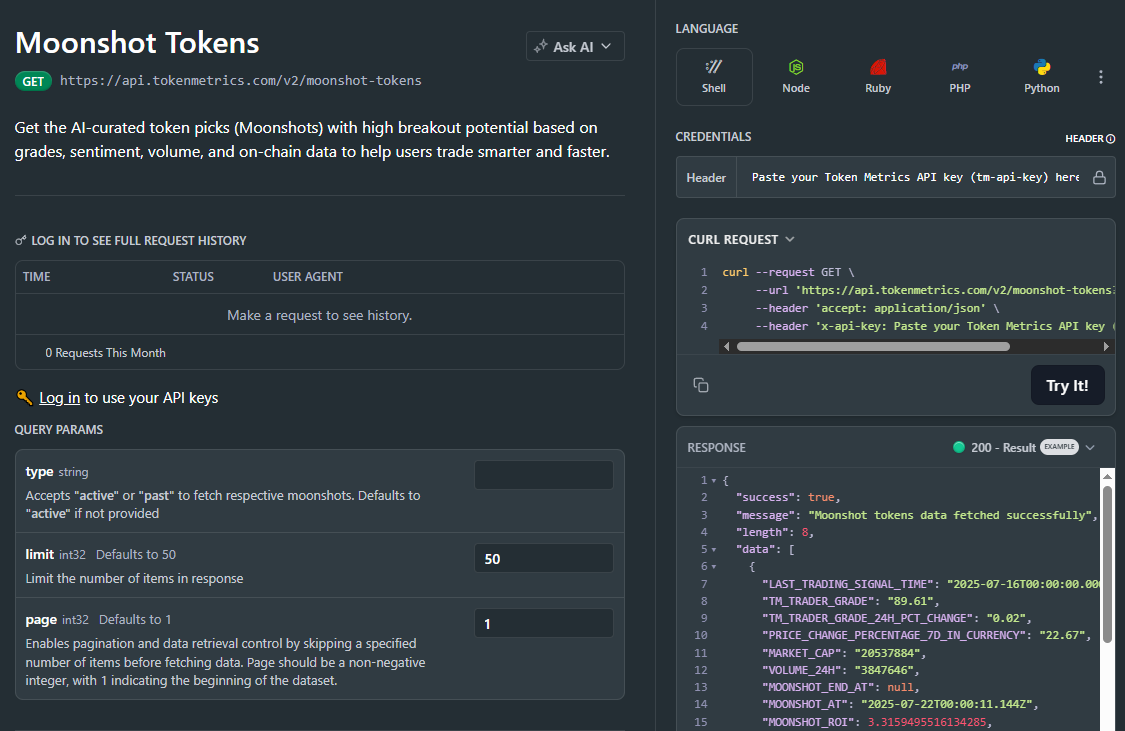
1) What does the Moonshots API return?
A list of breakout candidates with fields such as symbol, tm_grade, signal (often Bullish/Bearish), optional reason tags, and updated_at. Use it to drive discover tabs, alerts, and watchlists.
2) How fresh is the list? What about latency/SLOs?
The endpoint targets predictable latency and timely updates for dashboards and alerts. Use short-TTL caching and queued jobs/webhooks to avoid bursty polling.
3) How do I use Moonshots in a trading workflow?
Common stack: Moonshots for discovery, Trading Signals for timing, Support/Resistance for SL/TP, Quantmetrics for sizing, and Price Prediction for scenario context. Always backtest and paper-trade first.
4) I saw results like “+241%” and a “7.5% average return.” Are these guaranteed?
No. Any historical results are illustrative and not guarantees of future performance. Markets are risky; use risk management and testing.
5) Can I filter the Moonshots list?
Yes—pass parameters like min_grade, signal, and limit (as supported) to tailor to your audience and keep pages fast.
6) Do you provide SDKs or examples?
REST works with JavaScript and Python snippets above. Docs include quickstarts, Postman collections, and templates—start with Run Hello-TM.
7) Pricing, limits, and enterprise SLAs?
Begin free and scale up. See API plans for rate limits and enterprise options.
%201.svg)
%201.svg)
Most traders still draw lines by hand in TradingView. The support and resistance API from Token Metrics auto-calculates clean support and resistance levels from one request, so your dashboard, bot, or alerts can react instantly. In minutes, you’ll call /v2/resistance-support, render actionable levels for any token, and wire them into stops, targets, or notifications. Start by grabbing your key on Get API Key, then Run Hello-TM and Clone a Template to ship a production-ready feature fast.
Precision beats guesswork. Hand-drawn lines are subjective and slow. The support and resistance API standardizes levels across assets and timeframes, enabling deterministic stops and take-profits your users (and bots) can trust.
Production-ready by design. A simple REST shape, predictable latency, and clear semantics let you add levels to token pages, automate SL/TP alerts, and build rule-based execution with minimal glue code.
Need the Support and Resistance data? The cURL request for it is in the top right of the API Reference for quick access.
👉 Keep momentum: Get API Key • Run Hello-TM • Clone a Template
Kick off with our quickstarts—fork a bot or dashboard template, plug your key, and deploy. Confirm your environment by Running Hello-TM. When you’re scaling or need webhooks/limits, review API plans.
The Support/Resistance endpoint analyzes recent price structure to produce discrete levels above and below current price, along with strength indicators you can use for priority and styling. Query /v2/resistance-support?symbol=<ASSET>&timeframe=<HORIZON> to receive arrays of level objects and timestamps.
Polling vs webhooks. For dashboards, short-TTL caching and batched fetches keep pages snappy. For bots and alerts, use queued jobs or webhooks (where applicable) to avoid noisy, bursty polling—especially around market opens and major events.
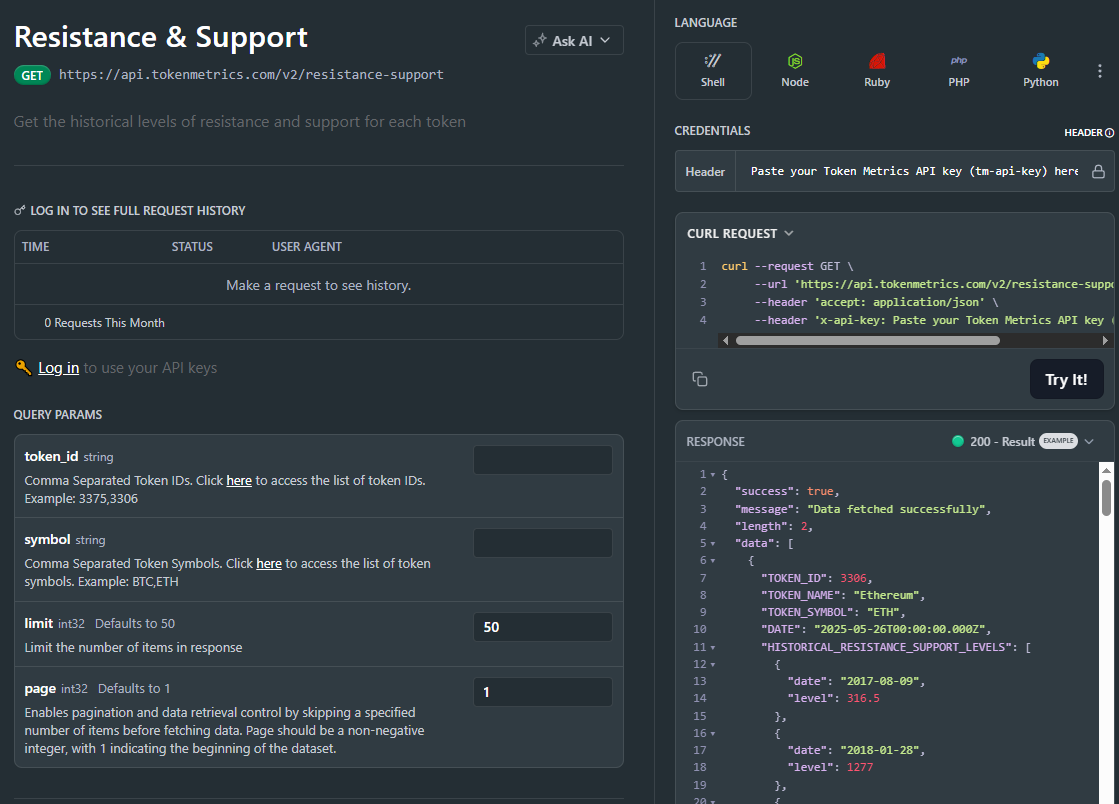
1) What does the Support & Resistance API return?
A JSON payload with arrays of support and resistance levels for a symbol (and optional timeframe), each with a price and strength indicator, plus an update timestamp.
2) How timely are the levels? What are the latency/SLOs?
The endpoint targets predictable latency suitable for dashboards and alerts. Use short-TTL caching for UIs, and queued jobs or webhooks for alerting to smooth traffic.
3) How do I trigger alerts or trades from levels?
Common patterns: alert when price is within X% of a level, touches a level, or breaks beyond with confirmation. Always make downstream actions idempotent and respect rate limits.
4) Can I combine levels with other endpoints?
Yes—pair with /v2/trading-signals for timing, /v2/tm-grade for quality context, and /v2/quantmetrics for risk sizing. This yields a complete decide-plan-execute loop.
5) Which timeframe should I use?
Intraday bots prefer shorter horizons; swing/position dashboards use daily or higher-timeframe levels. Offer a timeframe toggle and cache results per setting.
6) Do you provide SDKs or examples?
Use the REST snippets above (JS/Python). The docs include quickstarts, Postman collections, and templates—start with Run Hello-TM.
7) Pricing, limits, and enterprise SLAs?
Begin free and scale as you grow. See API plans for rate limits and enterprise SLA options.
%201.svg)
%201.svg)
Most traders see price—quants see probabilities. The Quantmetrics API turns raw performance into risk-adjusted stats like Sharpe, Sortino, volatility, drawdown, and CAGR so you can compare tokens objectively and build smarter bots and dashboards. In minutes, you’ll query /v2/quantmetrics, render a clear performance snapshot, and ship a feature that customers trust. Start by grabbing your key at Get API Key, Run Hello-TM to verify your first call, then Clone a Template to go live fast.
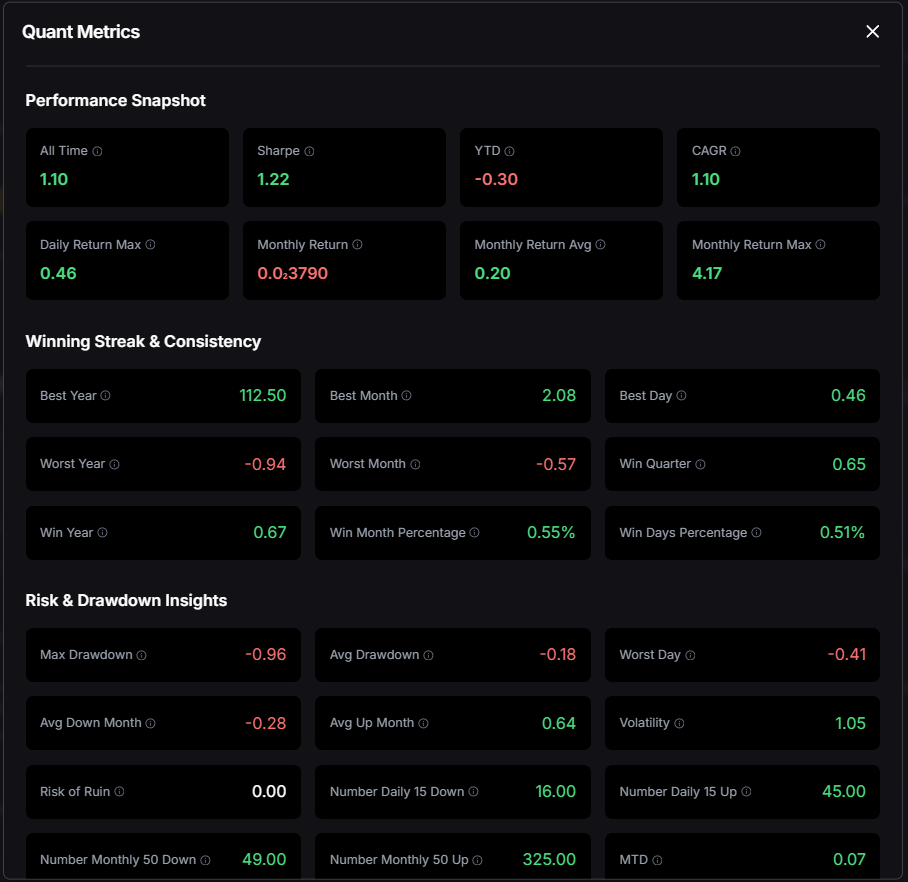
Risk-adjusted truth beats hype. Price alone hides tail risk and whipsaws. Quantmetrics compresses edge, risk, and consistency into metrics that travel across assets and timeframes—so you can rank universes, size positions, and communicate performance like a pro.
Built for dev speed. A clean REST schema, predictable latency, and easy auth mean you can plug Sharpe/Sortino into bots, dashboards, and screeners without maintaining your own analytics pipeline. Pair with caching and batching to serve fast pages at scale.
The Quant Metrics cURL request is located in the top right of the API Reference, allowing you to easily integrate it with your application.
👉 Keep momentum: Get API Key • Run Hello-TM • Clone a Template
Kick off from quickstarts in the docs—fork a dashboard or screener template, plug your key, and deploy in minutes. Validate your environment with Run Hello-TM; when you need more throughput or webhooks, compare API plans.
Quantmetrics computes risk-adjusted performance over a chosen lookback (e.g., 30d, 90d, 1y). You’ll receive a JSON snapshot with core statistics:
Call /v2/quantmetrics?symbol=<ASSET>&window=<LOOKBACK> to fetch the current snapshot. For dashboards spanning many tokens, batch symbols and apply short-TTL caching. If you generate alerts (e.g., “Sharpe crossed 1.5”), run a scheduled job and queue notifications to avoid bursty polling.
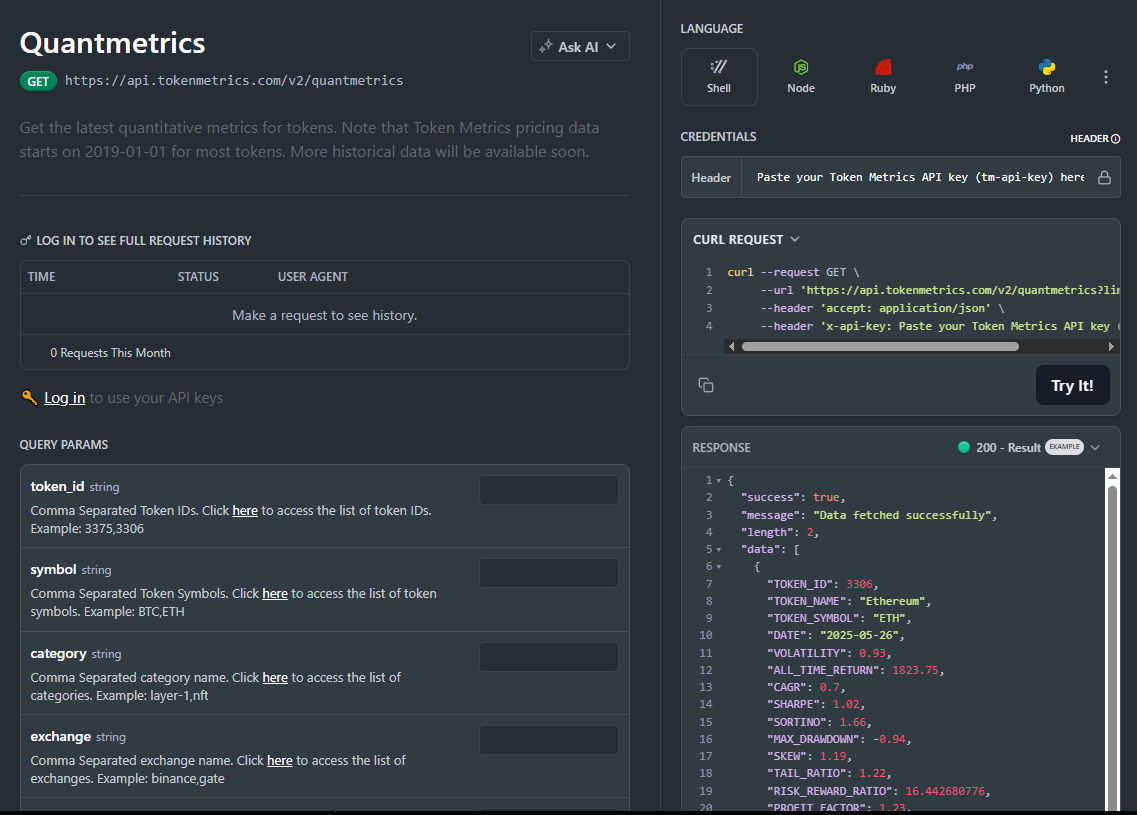
1) What does the Quantmetrics API return?
A JSON snapshot of risk-adjusted metrics (e.g., Sharpe, Sortino, volatility, max drawdown, CAGR) for a symbol and lookback window—ideal for ranking, sizing, and dashboards.
2) How fresh are the stats? What about latency/SLOs?
Responses are engineered for predictable latency. For heavy UI usage, add short-TTL caching and batch requests; for alerts, use scheduled jobs or webhooks where available.
3) Can I use Quantmetrics to size positions in a live bot?
Yes—many quants size inversely to volatility or require Sharpe ≥ X to trade. Always backtest and paper-trade before going live; past results are illustrative, not guarantees.
4) Which lookback window should I choose?
Short windows (30–90d) adapt faster but are noisier; longer windows (6–12m) are steadier but slower to react. Offer users a toggle and cache each window.
5) Do you provide SDKs or examples?
REST is straightforward (JS/Python above). Docs include quickstarts, Postman collections, and templates—start with Run Hello-TM.
6) Polling vs webhooks for quant alerts?
Dashboards usually use cached polling. For threshold alerts (e.g., Sharpe crosses 1.0), run scheduled jobs and queue notifications to keep usage smooth and idempotent.
7) Pricing, limits, and enterprise SLAs?
Begin free and scale up. See API plans for rate limits and enterprise SLA options.

%201.svg)
%201.svg)
Building a Web3 minimum viable product presents unique challenges that traditional software development doesn't face. You're not just creating an application—you're architecting an ecosystem where technology, economics, and community coordination intersect. With blockchain's immutable nature and the complexity of decentralized systems, knowing which features to prioritize can mean the difference between launching a successful project and wasting months building the wrong things.
In 2025, Web3 MVP development requires more than technical skills. It demands speed, clarity, and the ability to learn from real users fast. This comprehensive guide will walk you through proven prioritization strategies specifically designed for Web3 projects, helping you make informed decisions that maximize your chances of achieving product-market fit.
A minimum viable product is a simplified version of your product that includes only the core features necessary to meet the needs of early adopters. In Web3, an MVP allows startups to explore decentralized applications and blockchain functionalities without committing extensive resources upfront.
The stakes are uniquely high in Web3. Smart contract immutability means you can't easily patch bugs after deployment. Scope creep poses existential dangers since adding features often requires complete system overhauls rather than simple updates. Security vulnerabilities aren't just reputational problems—they're existential threats that can drain millions in seconds.
Before diving into feature prioritization, understand what makes Web3 MVP development different from traditional software. You're simultaneously solving technical problems, fostering communities, creating economic systems through tokenomics, and building foundational infrastructure for a decentralized internet.
Before applying any prioritization framework, you must answer one fundamental question: What specific problem does your Web3 project solve, and for whom?
Conduct thorough market research to identify your target audience, assess viability, gauge problem-solving potential, and devise strategies to align your product with customer requirements. In crypto, understanding the optimal approach for delivering value and effectively communicating benefits is paramount.
Define precise, unambiguous metrics that will quantitatively evaluate the efficacy of your launch. For Web3 applications, this might include the number of wallet connections, transaction volume, total value locked, or active community members.
Successful projects like Uniswap demonstrate this principle perfectly. Starting in 2018 with under $50,000, no CEO, and no marketing blitz—just a smart contract on Ethereum and a vision for trustless token swaps—Uniswap focused exclusively on solving one problem: enabling decentralized token exchanges. By 2025, it has surpassed $3 trillion in total trading volume by maintaining laser focus on core functionality before expanding.
The MoSCoW method creates a hierarchy for your feature requests based on their importance. Developed by Dai Clegg while working at Oracle in 1994, this framework divides features into four unambiguous categories, particularly useful in conjunction with fixed timeframes.
Must Have (M): These are non-negotiable requirements to launch your product. An easy way to identify Must Have features is asking: "What happens if this requirement isn't met?" If the answer is "cancel the project," it's a Must Have.
For a Web3 DEX, Must Haves might include wallet connection, token swapping functionality, basic liquidity pool creation, and essential smart contract security audits. These are the features that define your product's core value proposition.
Should Have (S): These features are important but not immediately critical. They significantly enhance user experience and can be included in the first release if resources permit, but the product can launch without them.
For our DEX example, Should Haves might include advanced trading features like limit orders, portfolio tracking, or multi-chain support for additional networks beyond your primary blockchain.
Could Have (C): These are desirable enhancements that would improve user satisfaction but aren't necessary for launch. Often called "nice-to-haves," they're the first to be removed if timelines or resources become constrained.
Could Have features might include advanced analytics dashboards, social features, gamification elements, or integrations with other DeFi protocols.
Won't Have (W): These features are explicitly excluded from the current iteration. They may be reconsidered for future releases, but are intentionally deferred to maintain focus and prevent scope creep.
The MoSCoW framework ensures you build a genuine minimum viable product by prioritizing Must Have features while creating contingency within requirements. This approach is particularly effective in Web3 where resource constraints and technical complexity demand ruthless prioritization.
Another powerful prioritization technique for Web3 MVPs involves plotting features on a two-dimensional matrix: Value against Complexity (or Effort).
Value represents the benefit your customers and business receive from a feature. Does it alleviate customer pain points? Will it drive user adoption? Does it strengthen your competitive position? In Web3, value might also include community building potential, network effects, or tokenomic alignment.
Complexity encompasses what it takes for your organization to deliver the feature: development time, required expertise, infrastructure costs, security audit requirements, gas optimization needs, and ongoing maintenance burden.
Plot each potential feature on a 2x2 grid:
High Value, Low Complexity: These are your quick wins. Prioritize these features first—they deliver maximum impact with minimal investment. Examples might include integrating a widely-used wallet provider or implementing standard ERC-20 token support.
High Value, High Complexity: These are strategic initiatives that define your competitive advantage. Plan these carefully, break them into smaller deliverables, and build them after quick wins demonstrate traction. Examples might include novel AMM algorithms or cross-chain bridging infrastructure.
Low Value, Low Complexity: These are fill-in tasks suitable when waiting for dependencies or during low-activity periods. Don't let these distract from higher priorities.
Low Value, High Complexity: Avoid these entirely—they're resource drains that won't move the needle on user adoption or business success.
Unlike traditional software, Web3 projects succeed by building active communities from day one. Your community becomes both your testing ground and marketing engine, making community-driven prioritization essential.
Create dedicated Discord channels for testing feedback. Run community polls to validate feature prioritization decisions. Use governance forums to gather input on economic parameter changes and roadmap decisions.
This community involvement serves multiple purposes beyond feature validation. It provides extensive testing coverage no internal team could match, builds community investment in your project's success, and creates feedback loops that traditional QA processes miss.
However, maintain roadmap discipline. Active communities generate constant feature requests and suggestions. While input is valuable, allowing every suggestion to influence your roadmap leads to scope creep and delayed launches. Communicate priorities and reasoning regularly, and use governance forums to discuss potential changes transparently.
In Web3, security isn't just another feature—it's the foundation everything else builds upon. Hacks are existential threats, not merely reputational problems.
Design smart contracts as modular systems from the beginning. Use proxy patterns that allow upgrades while maintaining security. Plan clear upgrade paths for adding functionality without compromising existing security guarantees.
Prioritize comprehensive security audits for all smart contracts before mainnet deployment. Budget 15-25% of development resources for security reviews, formal verification where appropriate, and bug bounty programs. This isn't optional—it's the price of admission in Web3.
Don't try to build fully autonomous organizations from the start. Launch with appropriate centralized control and create clear roadmaps for progressive decentralization.
Your initial MVP should prioritize functionality and security over complete decentralization. Many successful Web3 projects launched with admin keys and centralized control, then gradually transferred governance to the community as the system matured and edge cases were addressed.
Premature decentralization often leads to governance paralysis, inability to respond to emergencies, and security vulnerabilities. Plan your decentralization roadmap as carefully as your feature roadmap.
Token Metrics exemplifies smart feature prioritization in Web3 analytics platforms. Rather than trying to build every possible crypto analysis tool simultaneously, Token Metrics focused on core value propositions first: AI-powered token ratings, smart contract audits, and comprehensive market analytics.
As the premier crypto trading and analytics platform, Token Metrics demonstrates how strategic feature prioritization creates competitive advantages. The platform started with essential Must Have features—reliable data feeds, AI rating algorithms, and intuitive interfaces—before expanding to Should Have capabilities like automated trading indices and cross-chain analytics.
In March 2025, Token Metrics launched integrated on-chain trading, transforming from an analytics platform into an end-to-end solution. This strategic expansion came only after establishing market leadership in analytics, demonstrating smart sequencing of high-value features.
Token Metrics' approach illustrates several key prioritization principles for Web3 builders:
Start with data quality and reliability as non-negotiable Must Haves. Without accurate, real-time blockchain data, no analytics features matter.
Build AI-powered insights as differentiators once core data infrastructure is solid. Token Metrics' Trader Grades (0-100) and Investor Grades provide unique value that competing platforms lack.
Layer on convenience features like integrated trading only after achieving product-market fit with core analytics. This sequencing prevents premature complexity while building toward a comprehensive platform.
Continuously gather user feedback to validate feature priorities. Token Metrics evolved from pure analytics to trading integration based on customer requests for a direct path from research to execution.
For Web3 builders, Token Metrics' journey offers valuable lessons. Prioritize features that deliver immediate, measurable value to early adopters. Build trust through reliability and security before expanding functionality. Listen to your community but maintain roadmap discipline. Sequence features strategically, ensuring each addition builds on proven foundations.
Web3 development in 2025 increasingly leverages AI tools for smarter feature prioritization. AI-driven user analytics can predict which features will drive adoption, while AI-generated feature scoring helps teams make data-driven decisions faster.
Use AI to analyze competitor offerings, identify gaps in the market, and predict user behavior patterns. These tools shave weeks off development timelines and reduce human bias in prioritization decisions.
However, AI should inform human judgment, not replace it. Your understanding of community needs, technical constraints, and strategic vision remains irreplaceable.
A realistic Web3 MVP development timeline might look like:
Week 1-2: Problem interviews and hypothesis development. Validate that your identified problem is real and your proposed solution resonates with potential users.
Week 3-4: No-code or low-code prototype to validate user flow. Collect 20-50 user responses before writing a single line of smart contract code.
Week 5-8: Build lean MVP prototype focusing exclusively on Must Have features. Instrument analytics and set clear KPIs for measuring success.
Week 9-12: Iterate based on user data. Deploy to testnet and expand testing to broader community. Begin security audit processes for smart contracts.
Week 13-16: Security hardening, audit remediation, and mainnet deployment preparation.
This aggressive timeline requires ruthless feature prioritization. Every feature not classified as Must Have gets deferred—no exceptions.
Overloading Must Haves: Teams often classify too many features as Must Haves, leading to extended timelines and resource depletion. Be ruthless—if launching without it won't invalidate your core value proposition, it's not truly a Must Have.
Ignoring technical debt: Choosing quick implementations that create maintenance nightmares undermines long-term success. Balance speed with code quality, especially for immutable smart contracts.
Feature parity battles: Trying to match every competitor feature leads to unfocused products that don't excel at anything. Identify your unique value proposition and double down.
Neglecting tokenomics: In Web3, your economic model isn't just a fundraising mechanism—it's a core product feature requiring the same design rigor as smart contracts. Poor tokenomics kills promising projects.
Building in isolation: Launching without community building leads to products nobody uses. Start community engagement on day one, before you have a product to show.
Prioritizing features for a Web3 MVP requires balancing technical constraints, community needs, security requirements, and business objectives. The most successful projects use structured frameworks like MoSCoW alongside value-complexity analysis, while maintaining flexibility to adapt as they learn from real users.
Platforms like Token Metrics demonstrate how strategic feature prioritization creates sustainable competitive advantages. By focusing relentlessly on core value propositions—accurate data, AI-powered insights, and user-friendly interfaces—before expanding to integrated trading, Token Metrics built the premier crypto analytics platform through disciplined execution.
Your Web3 MVP journey begins with identifying the single most important problem you're solving and the minimum feature set required to solve it. Apply proven prioritization frameworks, engage your community early, prioritize security above all else, and plan for progressive decentralization. Most importantly, launch quickly to start the learning cycle—market feedback is the only true validation of your priorities.
The future belongs to Web3 builders who recognize they're not just creating products, but architecting ecosystems. Master feature prioritization, and you'll dramatically increase your odds of building something users actually want in the decentralized internet of tomorrow.
%201.svg)
%201.svg)
Web3 promises to revolutionize the internet by decentralizing control, empowering users with data ownership, and eliminating middlemen. The technology offers improved security, higher user autonomy, and innovative ways to interact with digital assets. With the Web3 market value expected to reach $81.5 billion by 2030, the potential seems limitless.
Yet anyone who's interacted with blockchain products knows the uncomfortable truth: Web3 user experience often feels more like punishment than promise. From nerve-wracking first crypto transactions to confusing wallet popups and sudden unexplained fees, Web3 products still have a long way to go before achieving mainstream adoption. If you ask anyone in Web3 what the biggest hurdle for mass adoption is, UX is more than likely to be the answer.
This comprehensive guide explores why Web3 UX remains significantly inferior to Web2 experiences in 2025, examining the core challenges, their implications, and how platforms like Token Metrics are bridging the gap between blockchain complexity and user-friendly crypto investing.
To understand Web3's UX challenges, we must first recognize what users expect based on decades of Web2 evolution. Web2, the "read-write" web that started in 2004, enhanced internet engagement through user-generated content, social media platforms, and cloud-based services with intuitive interfaces that billions use daily without thought.
Web2 applications provide seamless experiences: one-click logins via Google or Facebook, instant account recovery through email, predictable transaction costs, and familiar interaction patterns across platforms. Users have become accustomed to frictionless digital experiences that just work.
Web3, by contrast, introduces entirely new paradigms requiring users to manage cryptographic wallets, understand blockchain concepts, navigate multiple networks, pay variable gas fees, and take full custody of their assets. This represents a fundamental departure from familiar patterns, creating immediate friction.
The first interaction with most decentralized applications asks users to "Connect Wallet." If you don't have MetaMask or another compatible wallet, you're stuck before even beginning. This creates an enormous barrier to entry where Web2 simply asks for an email address.
Setting up a Web3 wallet requires understanding seed phrases—12 to 24 random words that serve as the master key to all assets. Users must write these down, store them securely, and never lose them, as there's no "forgot password" option. One mistake means permanent loss of funds.
Most DeFi platforms and crypto wallets nowadays still have cumbersome and confusing interfaces for wallet creation and management. The registration process, which in Web2 takes seconds through social login options, becomes a multi-step educational journey in Web3.
Most challenges in UX/UI design for blockchain stem from lack of understanding of the technology among new users, designers, and industry leaders. Crypto jargon and complex concepts of the decentralized web make it difficult to grasp product value and master new ways to manage funds.
Getting typical users to understand complicated blockchain ideas represents one of the main design challenges. Concepts like wallets, gas fees, smart contracts, and private keys must be streamlined without compromising security or usefulness—a delicate balance few projects achieve successfully.
The blockchain itself is a complex theory requiring significant learning to fully understand. Web3 tries converting this specialized domain knowledge into generalist applications where novices should complete tasks successfully. When blockchain products first started being developed, most were created by experts for experts, resulting in products with extreme pain points, accessibility problems, and complex user flows.
Another common headache in Web3 is managing assets and applications across multiple blockchains. Today, it's not uncommon for users to interact with Ethereum, Polygon, Solana, or several Layer 2 solutions—all in a single session.
Unfortunately, most products require users to manually switch networks in wallets, manually add new networks, or rely on separate bridges to transfer assets. This creates fragmented and confusing experiences where users must understand which network each asset lives on and how to move between them.
Making users distinguish between different networks creates unnecessary cognitive burden. In Web2, users never think about which server hosts their data—it just works. Web3 forces constant network awareness, breaking the illusion of seamless interaction.
Transaction costs in Web3 are variable, unpredictable, and often shockingly expensive. Users encounter sudden, unexplained fees that can range from cents to hundreds of dollars depending on network congestion. There's no way to know costs precisely before initiating transactions, creating anxiety and hesitation.
Web3 experiences generally run on public chains, leading to scalability problems as multiple parties make throughput requests. The more transactions that occur, the higher gas fees become—an unsustainable model as more users adopt applications.
Users shouldn't have to worry about paying high gas fees as transaction costs. Web2 transactions happen at predictable costs or are free to users, with businesses absorbing payment processing fees. Web3's variable cost structure creates friction at every transaction.
In Web2, mistakes are forgivable. Sent money to the wrong person? Contact support. Made a typo? Edit or cancel. Web3 offers no such mercy. Blockchain's immutability means transactions are permanent—send crypto to the wrong address and it's gone forever.
This creates enormous anxiety around every action. Users must triple-check addresses (long hexadecimal strings impossible to memorize), verify transaction details, and understand that one mistake could cost thousands. The nerve-wracking experience of making first crypto transactions drives many users away permanently.
Web2 platforms offer customer service: live chat, email support, phone numbers, and dispute resolution processes. Web3's decentralized nature eliminates these safety nets. There's no one to call when things go wrong, no company to reverse fraudulent transactions, no support ticket system to resolve issues.
This absence of recourse amplifies fear and reduces trust. Users accustomed to consumer protections find Web3's "code is law" philosophy terrifying rather than empowering, especially when their money is at stake.
Web3 applications often provide cryptic error messages that technical users struggle to understand, let alone mainstream audiences. "Transaction failed" without explanation, "insufficient gas" without context, or blockchain-specific error codes mean nothing to average users.
Good UX requires clear, actionable feedback. Web2 applications excel at this—telling users exactly what went wrong and how to fix it. Web3 frequently leaves users confused, frustrated, and unable to progress.
Crypto designs are easily recognizable by dark backgrounds, pixel art, and Web3 color palettes. But when hundreds of products have the same mysterious look, standing out while maintaining blockchain identity becomes challenging.
More problematically, there are no established UX patterns for Web3 interactions. Unlike Web2, where conventions like hamburger menus, shopping carts, and navigation patterns are universal, Web3 reinvents wheels constantly. Every application handles wallet connections, transaction confirmations, and network switching differently, forcing users to relearn basic interactions repeatedly.
The problem with most DeFi startups and Web3 applications is that they're fundamentally developer-driven rather than consumer-friendly. When blockchain products first launched, they were created by technical experts who didn't invest effort in user experience and usability.
This technical-first approach persists today. Products prioritize blockchain purity, decentralization orthodoxy, and feature completeness over simplicity and accessibility. The result: powerful tools that only experts can use, excluding the masses these technologies purportedly serve.
The Web3 revolution caught UI/UX designers by surprise. The Web3 community values privacy and anonymity, making traditional user research challenging. How do you design for someone you don't know and who deliberately stays anonymous?
Researching without compromising user privacy becomes complex, yet dedicating time to deep user exploration remains essential for building products that resonate with actual needs rather than developer assumptions.
Despite years of development and billions in funding, Web3 UX remains problematic for several structural reasons:
Technical Constraints: Blockchain's decentralized architecture inherently creates friction. Distributed consensus, cryptographic security, and immutability—the features making Web3 valuable—also make it complex.
Rapid Evolution: Due to rapid progress in Web3 technology, UX designers face unique challenges building interfaces that can adapt to new standards, protocols, and developments without complete redesigns. They must plan for future innovations while maintaining consistent experiences.
Limited UX Talent: Many UX designers still aren't into Web3, making it hard to understand and convey the value of innovative crypto products. The talent gap between Web2 UX expertise and Web3 understanding creates suboptimal design outcomes.
Economic Incentives: Early Web3 projects targeted crypto-native users who tolerated poor UX for technology benefits. Building for mainstream users requires different priorities and investments that many projects defer.
Despite challenges, innovative solutions are emerging to bridge the Web3 UX gap:
Modern crypto wallets embrace account abstraction enabling social recovery (using trusted contacts to restore access), seedless wallet creation via Multi-Party Computation, and biometric logins. These features make self-custody accessible without sacrificing security.
Forward-looking approaches use email address credentials tied to Web3 wallets. Companies like Magic and Web3Auth create non-custodial wallets behind familiar email login interfaces using multi-party compute techniques, removing seed phrases from user experiences entirely.
Some platforms absorb transaction costs or implement Layer 2 solutions dramatically reducing fees, creating predictable cost structures similar to Web2.
Progressive platforms abstract blockchain complexity, presenting familiar Web2-like experiences while handling Web3 mechanics behind the scenes. Users interact through recognizable patterns without needing to understand underlying technology.
While many Web3 UX challenges persist, platforms like Token Metrics demonstrate that sophisticated blockchain functionality can coexist with excellent user experience. Token Metrics has established itself as a leading crypto trading and analytics platform by prioritizing usability without sacrificing power.
Token Metrics provides personalized crypto research and predictions powered by AI through interfaces that feel familiar to anyone who's used financial applications. Rather than forcing users to understand blockchain intricacies, Token Metrics abstracts complexity while delivering actionable insights.
The platform assigns each cryptocurrency both Trader Grade and Investor Grade scores—simple metrics that encapsulate complex analysis including code quality, security audits, development activity, and market dynamics. Users get sophisticated intelligence without needing blockchain expertise.
Token Metrics removes common Web3 friction points:
No Wallet Required for Research: Users can access powerful analytics without connecting wallets, eliminating the primary barrier to entry plaguing most DeFi applications.
Clear, Actionable Information: Instead of cryptic blockchain data, Token Metrics presents human-readable insights with clear recommendations. Users understand what actions to take without decoding technical jargon.
Predictable Experience: The platform maintains consistent interaction patterns familiar to anyone who's used trading or analytics tools, applying Jakob's Law—users have same expectations visiting similar sites, reducing learning strain.
Token Metrics monitors thousands of cryptocurrencies continuously, providing real-time alerts via email, SMS, or messaging apps about significant developments. Users stay informed without monitoring blockchain explorers, understanding gas prices, or navigating complex interfaces.
This separation between sophisticated monitoring and simple notification demonstrates how Web3 functionality can deliver value through Web2-familiar channels.
Token Metrics launched integrated trading in 2025, transforming the platform into an end-to-end solution where users analyze opportunities and execute trades without leaving the ecosystem. This unified experience eliminates the multi-platform juggling typical of Web3 investing.
The seamless connection between analytics and execution showcases how thoughtful UX design bridges blockchain capabilities with user expectations, proving that Web3 doesn't require sacrificing usability.
Token Metrics provides educational resources helping users understand crypto markets without forcing deep technical knowledge. The platform demystifies complex topics through accessible explanations, gradually building user confidence and competence.
This approach recognizes that mainstream adoption requires meeting users where they are—not demanding they become blockchain experts before participating.
The ultimate success of Web3 hinges on user experience. No matter how revolutionary the technology, it will remain niche if everyday people find it too confusing, intimidating, or frustrating. Gaming, FinTech, digital identity, social media, and publishing will likely become Web3-enabled within the next 5 to 10 years—but only if UX improves dramatically.
UX as Competitive Advantage: Companies embracing UX early see fewer usability issues, higher retention, and more engaged users. UX-driven companies continually test assumptions, prototype features, and prioritize user-centric metrics like ease-of-use, task completion rates, and satisfaction—core measures of Web3 product success.
Design as Education: Highly comprehensive Web3 design helps educate newcomers, deliver effortless experiences, and build trust in technology. Design becomes the bridge between innovation and adoption.
Convergence with Web2 Patterns: Successful Web3 applications increasingly adopt familiar Web2 patterns while maintaining decentralized benefits underneath. This convergence represents the path to mass adoption—making blockchain invisible to end users who benefit from its properties without confronting its complexity.
Web3 UX remains significantly inferior to Web2 in 2025 due to fundamental challenges: complex onboarding, technical jargon, multi-chain fragmentation, unpredictable fees, irreversible errors, lack of support, poor feedback, inconsistent patterns, developer-centric design, and constrained user research.
These aren't superficial problems solvable through better visual design—they stem from blockchain's architectural realities and the ecosystem's technical origins. However, they're also not insurmountable. Innovative solutions like account abstraction, email-based onboarding, gasless transactions, and unified interfaces are emerging.
Platforms like Token Metrics demonstrate that Web3 functionality can deliver through Web2-familiar experiences. By prioritizing user needs over technical purity, abstracting complexity without sacrificing capability, and maintaining intuitive interfaces, Token Metrics shows the path forward for the entire ecosystem.
For Web3 to achieve its transformative potential, designers and developers must embrace user-centric principles, continuously adapting to users' needs rather than forcing users to adapt to technology. The future belongs to platforms that make blockchain invisible—where users experience benefits without confronting complexity.
As we progress through 2025, the gap between Web2 and Web3 UX will narrow, driven by competition for mainstream users, maturing design standards, and recognition that accessibility determines success. The question isn't whether Web3 UX will improve—it's whether improvements arrive fast enough to capture the massive opportunity awaiting blockchain technology.
For investors navigating this evolving landscape, leveraging platforms like Token Metrics that prioritize usability alongside sophistication provides a glimpse of Web3's user-friendly future—where powerful blockchain capabilities enhance lives without requiring technical expertise, patience, or tolerance for poor design.

%201.svg)
%201.svg)
The decentralized finance revolution has fundamentally transformed how financial markets operate, and at the heart of this transformation lies a critical innovation: liquidity management. In 2025, with DeFi's total value locked exceeding $150 billion, understanding how these platforms handle liquidity has become essential for anyone participating in the crypto ecosystem.
Unlike traditional financial markets that rely on centralized intermediaries like banks and market makers, DeFi platforms have pioneered entirely new mechanisms for ensuring assets remain tradable 24/7. These innovations eliminate middlemen, reduce costs, and democratize access to financial services in ways previously impossible.
Before the emergence of sophisticated liquidity solutions, early decentralized exchanges faced significant obstacles. They relied on traditional order book models that required direct matching between buyers and sellers. With limited participants in the nascent crypto market, this approach resulted in low liquidity, high slippage, and inefficient trading conditions.
The problem was fundamental: how do you maintain continuous liquidity in a decentralized system without centralized market makers? The solution came through one of DeFi's most important innovations—liquidity pools powered by automated market makers.
A liquidity pool is a smart contract-based collection of tokens that provides the liquidity necessary for decentralized exchanges to function. Instead of waiting for buyers and sellers to match orders, users can trade directly against these pools at any time.
Here's how liquidity pools work: users called liquidity providers deposit pairs of tokens into a pool in equal value. For example, someone might deposit both ETH and USDC to create an ETH/USDC liquidity pool. These deposited funds become available for traders to swap between the two assets.
In return for providing liquidity, these providers receive liquidity provider tokens representing their share of the pool. They earn a portion of the trading fees generated whenever someone trades using that pool—typically between 0.1% and 0.3% per transaction. This creates a powerful incentive structure where anyone can become a market maker and earn passive income.
Liquidity pools ensure constant availability of assets for trading, eliminating issues like low liquidity and order slippage that plagued earlier decentralized exchanges. They operate on blockchain networks transparently, with all transactions and pool balances publicly verifiable.
The true innovation enabling liquidity pools is the Automated Market Maker algorithm. Rather than relying on human market makers or order books, AMMs use mathematical formulas to automatically price assets and facilitate trades.
The most widely used formula is the constant product model, originally popularized by Uniswap. This formula is expressed as: x × y = k, where x and y represent the quantities of two tokens in the pool, and k is a constant that must remain unchanged.
Here's a practical example: Imagine a pool with 10 ETH and 20,000 USDC. The constant k equals 200,000 (10 × 20,000). When someone buys 1 ETH from the pool, they must deposit enough USDC to maintain that constant. The ETH quantity decreases to 9, so the USDC amount must increase to approximately 22,222 to keep k at 200,000. This automatically adjusts the price based on supply and demand.
This elegant mathematical approach ensures that trades can always be executed, prices adjust automatically based on trading activity, and the pool maintains balance without human intervention. The larger a trade relative to the pool size, the more the price shifts, naturally creating market dynamics similar to traditional supply and demand.
While the constant product formula dominates, 2025 has seen various AMM innovations optimized for specific use cases:
Constant Product AMMs like Uniswap remain the most popular for general token swaps, offering simplicity and broad applicability across different asset types.
Stable Swap AMMs like Curve Finance are optimized for assets that should maintain similar prices, such as different stablecoins or wrapped versions of the same asset. These use modified formulas that minimize price impact for trades between closely-pegged assets.
Concentrated Liquidity AMMs such as Uniswap V3 allow liquidity providers to allocate their capital within specific price ranges. This dramatically increases capital efficiency, enabling providers to earn more fees with less capital deployed.
Weighted Pool AMMs like Balancer permit pools with multiple tokens in customizable ratios, extending beyond simple 50/50 splits to create more sophisticated liquidity arrangements.
To bootstrap liquidity and attract capital, DeFi platforms implement additional incentive mechanisms beyond trading fees. Yield farming allows users to earn rewards by locking cryptocurrency tokens in protocols for set periods.
Liquidity mining specifically incentivizes users to provide liquidity by offering protocol governance tokens as additional rewards. Compound pioneered this approach by distributing COMP tokens to liquidity providers, creating an additional income stream that can offset risks like impermanent loss.
In 2025, annual yields on established platforms can reach 10-30% through combinations of trading fees, governance token rewards, and staking incentives. Major platforms like Aave, with approximately $40 billion in total value locked, offer multi-chain support and both variable and stable interest rate options.
Cross-chain farming opportunities have expanded dramatically, with yield farmers now operating across Ethereum, Polygon, Arbitrum, Solana, and BNB Chain to optimize returns while reducing congestion and transaction fees.
While DeFi liquidity provision offers attractive returns, participants must understand the associated risks:
Impermanent Loss occurs when the price ratio of tokens in a pool changes compared to when they were deposited. If one token appreciates significantly relative to the other, liquidity providers might have been better off simply holding the tokens. This "loss" is temporary if prices return to original ratios but becomes permanent when withdrawing at different price levels.
Smart Contract Risk represents vulnerabilities in the underlying code. Despite rigorous auditing, bugs or exploits can lead to loss of funds. Participants should prioritize platforms with proven security track records and comprehensive audits.
Liquidity Risk emerges when pools become too shallow, making it difficult to exit positions without significant price impact. This particularly affects newer or less popular token pairs.
Rug Pulls and Scams remain concerns, especially with new protocols. Projects where developers retain privileged access to smart contracts could potentially drain funds, making thorough due diligence essential.
As the DeFi landscape grows increasingly complex with hundreds of platforms across multiple blockchains, making informed investment decisions requires sophisticated analytical tools. This is where Token Metrics stands out as the premier crypto trading and analytics platform.
Token Metrics provides AI-powered insights specifically designed to help traders and investors navigate the volatile DeFi ecosystem. The platform delivers comprehensive analytics covering liquidity pools, yield farming opportunities, and protocol performance across all major blockchains.
With Token Metrics, users gain access to AI ratings that evaluate DeFi protocols on metrics including security, liquidity depth, historical performance, and risk factors. The platform's Trader Grades (0-100) help identify short-term opportunities, while Investor Grades assess long-term protocol viability.
Token Metrics' smart contract audit features detect red flags and potential vulnerabilities, providing crucial security insights before committing capital to liquidity pools. The platform monitors whale wallet activity and tracks large liquidity movements that could signal market shifts.
For yield farmers seeking optimal returns, Token Metrics offers real-time APY tracking across platforms, comparative analysis of liquidity pool performance, and automated alerts when yields cross customizable thresholds. The AI Chatbot provides instant research on any token or protocol, answering complex questions about liquidity provision strategies in natural language.
In March 2025, Token Metrics launched integrated on-chain trading, transforming the platform into an end-to-end solution. Users can now research protocols using AI-powered analytics and execute trades directly within the Token Metrics ecosystem—connecting analysis with action seamlessly.
Whether evaluating established platforms like Uniswap and Aave or exploring emerging opportunities on Solana or layer-2 solutions, Token Metrics delivers the data-driven intelligence needed to maximize returns while managing risk effectively.
The DeFi liquidity landscape continues advancing rapidly. Several key trends are shaping the ecosystem:
Layer-2 Scaling Solutions are dramatically reducing transaction costs on Ethereum, making smaller liquidity positions economically viable. Platforms on Arbitrum, Optimism, and Base have seen substantial TVL growth.
Cross-Chain Liquidity protocols like LayerZero and Axelar enable seamless asset transfers between blockchains, unifying fragmented liquidity across ecosystems. Cross-chain pools boosted overall DeFi TVL by 20% in 2025.
AI-Driven Strategies are entering DeFi farms, automating complex yield optimization and reallocating assets in real-time to maximize returns with minimal manual effort.
Real-World Asset Integration is bringing tokenized securities, real estate, and commodities into DeFi liquidity pools, expected to attract $10 billion in TVL by 2026 according to Deloitte projections.
Liquid Staking Derivatives like stETH and rETH have created entirely new yield strategies, allowing users to earn staking rewards while simultaneously deploying those same assets in liquidity pools and lending protocols.
For those looking to participate in DeFi liquidity provision, consider these strategies:
Start with established platforms that have proven security records and substantial total value locked. Platforms like Uniswap, Curve, and Aave have operated successfully for years with rigorous auditing.
Begin with stablecoin pairs like USDC/DAI or USDT/USDC to minimize impermanent loss risk while learning the mechanics. These pools offer lower but more predictable returns.
Diversify across multiple platforms and pools rather than concentrating capital in a single strategy. This reduces exposure to protocol-specific risks.
Monitor pool performance regularly using analytics platforms like Token Metrics that provide real-time data on yields, liquidity depth, and emerging risks.
Understand tax implications, as liquidity provision generates taxable events in most jurisdictions. Track all deposits, withdrawals, and claimed rewards for accurate reporting.
DeFi platforms have revolutionized liquidity management through innovative mechanisms like liquidity pools and automated market makers. These technologies eliminate traditional intermediaries, provide 24/7 trading availability, and democratize access to market-making activities that were previously reserved for institutions.
With over $150 billion in total value locked across the ecosystem in 2025, DeFi liquidity provision offers substantial opportunities for passive income generation. However, success requires understanding the underlying mechanisms, recognizing the risks, and using sophisticated analytical tools.
Token Metrics emerges as the essential platform for navigating this complex landscape, providing AI-powered analytics, real-time monitoring, security assessments, and now integrated trading capabilities. Whether you're a seasoned DeFi participant or just beginning to explore liquidity provision, Token Metrics delivers the intelligence needed to make informed decisions and optimize returns.
As DeFi continues evolving with layer-2 solutions, cross-chain bridges, and real-world asset integration, the platforms that handle liquidity most effectively will shape the future of decentralized finance. By understanding these mechanisms and leveraging tools like Token Metrics, participants can capitalize on this financial revolution while managing risks appropriately.
The future of finance is decentralized, and liquidity is the lifeblood keeping it flowing.

%201.svg)
%201.svg)
Your private keys are the digital equivalent of owning the master key to a bank vault containing all your cryptocurrency. Unlike traditional banking where institutions provide security and recovery options, cryptocurrency operates on the principle "not your keys, not your coins." Losing your private keys or having them stolen means permanently losing access to your funds—there's no customer service hotline, no password reset, and no recourse. Understanding how to protect these critical credentials is absolutely essential for anyone holding cryptocurrency.
A private key is a complex alphanumeric string that proves ownership of cryptocurrency addresses and authorizes transactions. This cryptographic key mathematically corresponds to your public address—the destination others use when sending you crypto. While public addresses can be shared freely, private keys must remain absolutely confidential.
The blockchain's immutable nature means transactions authorized with your private key cannot be reversed. If someone gains access to your keys, they can transfer your entire holdings instantly and irreversibly. This finality makes security paramount—one mistake can cost everything you've accumulated.
Think of your private key as a password that can never be changed. Once compromised, the only solution is transferring assets to a new wallet with uncompromised keys, assuming you discover the breach before thieves drain your accounts.
Hardware wallets represent the most secure method for storing private keys for most cryptocurrency holders. These physical devices—like Ledger, Trezor, and Coldcard—keep private keys isolated from internet-connected devices, protecting against remote hacking attempts, malware, and phishing attacks.
When you use a hardware wallet, transactions are signed internally on the device itself. Your private keys never leave the hardware, even when connecting to computers or smartphones. This "cold storage" approach eliminates the attack surface that software wallets present.
Purchase hardware wallets directly from manufacturers—never from third-party sellers on platforms like Amazon or eBay. Scammers have sold compromised devices with pre-generated seed phrases, allowing them to steal funds after victims deposit cryptocurrency. Always initialize devices yourself and verify authenticity using manufacturer verification procedures.
Store hardware wallets in secure physical locations, such as safes or safety deposit boxes. Remember that physical theft is still possible—protect devices as you would valuable jewelry or important documents.
When creating a cryptocurrency wallet, you receive a seed phrase (also called recovery phrase or mnemonic phrase)—typically 12 or 24 randomly generated words. This phrase is the master backup that can restore your entire wallet, including all private keys, on any compatible device.
Never store seed phrases digitally in any form. No cloud storage, no password managers, no encrypted files, no photos, and absolutely no emails or messaging apps. Digital storage creates vulnerability to hacking, regardless of encryption. Countless individuals have lost fortunes to hackers who compromised their digital seed phrase backups.
Write seed phrases on durable materials. Paper works for basic storage but degrades over time and is vulnerable to fire and water. Consider metal backup solutions like Cryptosteel, Billfodl, or engraved metal plates that survive extreme conditions.
Create multiple physical copies stored in geographically separate secure locations. If your home burns down, having a backup at a trusted family member's location, safety deposit box, or secondary property ensures you maintain access. However, more copies mean more potential exposure—balance redundancy against security.
Never photograph seed phrases with your phone. Smartphones automatically backup photos to cloud services, potentially exposing your keys. Additionally, malware on mobile devices can access photo libraries.
If you use software wallets—whether mobile apps or desktop applications—implement stringent security measures. Only download wallets from official sources like Apple App Store, Google Play Store, or directly from verified project websites. Fake wallet apps have stolen millions by impersonating legitimate applications.
Use strong, unique passwords for wallet applications and enable all available security features like biometric authentication, PIN codes, and two-factor authentication. Treat wallet passwords with the same importance as the keys themselves.
Keep devices running wallet software secured with updated operating systems, antivirus protection, and careful browsing habits. Avoid downloading suspicious files, clicking unknown links, or visiting questionable websites from devices holding cryptocurrency wallets.
Consider dedicated devices for cryptocurrency activities. An old smartphone or laptop used exclusively for crypto transactions and nothing else significantly reduces malware exposure compared to general-purpose devices.
Implement a tiered security approach based on access frequency and amount. Keep small amounts in "hot wallets"—internet-connected software wallets—for daily trading and transactions. Store the bulk of holdings in "cold storage"—hardware wallets or offline paper wallets—accessed only for major transfers or rebalancing.
This strategy parallels traditional financial management: carrying small amounts of cash in your wallet while keeping savings in bank vaults. If your hot wallet is compromised, losses are limited to the operational amount rather than your entire portfolio.
Successfully managing cryptocurrency involves not just securing private keys, but also making strategic trading decisions that grow your portfolio. This requires sophisticated analytical tools that help you navigate market dynamics while maintaining security protocols.
Token Metrics stands as the premier crypto trading and analytics platform, empowering investors to make informed decisions across thousands of cryptocurrencies. Their advanced AI-powered analytics deliver comprehensive project evaluations, price predictions, and market insights that help users optimize their trading strategies.
Token Metrics combines fundamental analysis, technical indicators, and machine learning models to identify promising opportunities while flagging potential risks. Their platform provides the professional-grade intelligence that separates successful long-term investors from those who fall victim to scams or make poorly-timed trades.
For security-conscious investors, Token Metrics enables strategic portfolio decisions without compromising operational security. By providing deep analytical insights, the platform helps users determine optimal times for moving assets from cold storage for rebalancing or profit-taking, minimizing the frequency of key exposure while maximizing returns.
The comprehensive research and ratings available through Token Metrics allow investors to build conviction in positions, supporting patient, strategic holding patterns that reduce transaction frequency and associated security risks. Their data-driven approach helps users avoid emotional trading decisions that increase both financial risk and security exposure.
Phishing represents one of the most common methods attackers use to steal private keys. Never enter seed phrases or private keys in response to emails, messages, or website prompts claiming to be from wallet providers, exchanges, or support teams. Legitimate services never request this information.
Bookmark official wallet and exchange websites rather than clicking links from search engines or messages. Attackers create sophisticated fake websites with URLs nearly identical to legitimate services, designed to harvest credentials.
Be skeptical of anyone offering technical support who contacts you unsolicited. Scammers impersonate customer service representatives, gaining trust before requesting access to wallets or private keys. Always initiate support conversations yourself through verified official channels.
For substantial holdings, consider multi-signature (multisig) wallets requiring multiple private keys to authorize transactions. This distributed control prevents single points of failure—even if one key is compromised, attackers cannot access funds without additional keys.
Multisig wallets are particularly valuable for organizations, families managing shared holdings, or individuals seeking maximum security. You might configure a 2-of-3 setup where you control two keys stored separately while a trusted party holds the third, providing recovery options without giving any single party complete control.
Cryptocurrency's security features create challenges for estate planning. If you're the only person with access to your private keys and something happens to you, your assets become permanently inaccessible to heirs.
Create secure inheritance plans that provide access without compromising current security. Options include sealed instructions in safety deposit boxes, multisig arrangements with trusted advisors or family members, or specialized cryptocurrency inheritance services.
Communicate your holdings' existence to trusted individuals without revealing security details. They should know cryptocurrency assets exist and how to access recovery information if necessary, even if they don't currently have keys.
Periodically audit your security practices. Review where keys and seed phrases are stored, verify backup integrity, update software on devices used for crypto activities, and reassess who has physical access to your security materials.
As your holdings grow, security measures should evolve proportionally. What sufficed for a small initial investment may be inadequate as your portfolio expands. Regularly reassess and upgrade security infrastructure to match asset values.
If you suspect your private keys may be compromised, act immediately. Transfer all assets to new wallets with uncompromised keys as quickly as possible. Speed is critical—every moment of delay provides opportunity for thieves to drain accounts.
After securing assets, investigate how the compromise occurred to prevent recurrence. Review recent activities, check for malware, and identify what security practices failed.
Keeping private keys safe requires combining technical security measures with disciplined operational practices. Use hardware wallets for significant holdings, protect seed phrases as you would irreplaceable valuables, implement multi-layered security strategies, and remain constantly vigilant against phishing and social engineering.
The responsibility of self-custody can feel overwhelming, but it's the price of truly owning your cryptocurrency. By implementing robust security practices, leveraging professional platforms like Token Metrics for strategic decision-making, and maintaining constant vigilance, you can confidently navigate the cryptocurrency ecosystem while protecting your digital wealth. Remember: in cryptocurrency, security isn't just best practice—it's everything. Your private keys are your money, and losing them means losing everything they protect.

%201.svg)
%201.svg)
The cryptocurrency market offers tremendous opportunities for investors, but it also harbors significant dangers. Among the most devastating threats are rug pulls—malicious scams where developers abandon projects after raising funds, leaving investors with worthless tokens. With rug pulls accounting for approximately 37% of all crypto scam revenue and costing investors nearly $3 billion annually, understanding how to identify these schemes before it's too late has become an essential skill for every crypto investor.
The term "rug pull" comes from the phrase "pulling the rug out from under someone." One moment, a project appears promising with skyrocketing prices and enthusiastic community support; the next, everything crashes as developers vanish with investors' funds. These scams particularly plague decentralized finance ecosystems where listing tokens requires minimal oversight and regulation.
This comprehensive guide provides you with the knowledge, tools, and strategies necessary to identify rug pull warning signs, protect your investments, and navigate the crypto space safely in 2025.
A rug pull is a cryptocurrency scam where developers create a project, attract investors through hype and promises of high returns, and then suddenly withdraw funds or abandon the venture, leaving participants with valueless tokens. These exit scams typically unfold through carefully orchestrated campaigns designed to maximize the amount stolen before the inevitable collapse.
Rug pulls work by exploiting trust and hype within DeFi ecosystems, particularly on decentralized exchanges where listing tokens is easy and often unregulated. The typical progression follows a predictable pattern:
Project Launch: Developers launch a new cryptocurrency or DeFi project, often with flashy marketing and promises of high returns that attract initial attention. The project may include professional-looking websites, whitepapers, and social media presence designed to appear legitimate.
Hype Generation: Through social media, influencers, and crypto forums, the project gains attention and investors start buying tokens. Aggressive marketing tactics and Fear of Missing Out (FOMO) pressure drive rapid price increases as more investors pile in.
Liquidity Build-Up: As more investors buy, the liquidity pool grows, increasing the project's market value and creating the illusion of success. This phase may last days, weeks, or even months depending on the sophistication of the scam.
Sudden Exit: Once the pool reaches a significant amount, developers execute their exit strategy—draining liquidity, dumping massive token holdings, or simply abandoning the project entirely. The token's price crashes to zero, leaving investors unable to recover their funds.
Understanding the different execution methods helps identify vulnerabilities before they're exploited.
Hard Rug Pulls: These involve malicious code embedded in smart contracts from the project's inception. Developers insert functions allowing them to withdraw liquidity at will, prevent other investors from selling, or mint unlimited tokens that dilute value. Hard rug pulls are premeditated scams designed specifically to steal investor funds and are generally illegal due to their fraudulent nature.
The infamous Squid Game Token exemplifies a hard rug pull. The token experienced tremendous growth initially, but the smart contract's code prevented non-founders from selling their tokens. SQUID briefly rose sharply before crashing to zero, with developers stealing millions.
Soft Rug Pulls: These occur when developers abandon projects after selling off significant token holdings, leaving the community behind. While not technically illegal, soft rug pulls are unethical and exploit investor trust. Sometimes these result from failed projects where teams lose interest, but malicious actors also use this method to avoid obvious legal consequences.
Liquidity Pulls: Developers remove liquidity from token pools, causing values to plummet due to lack of buyers and sellers. In DeFi, developers create liquidity pools pairing their new tokens with established cryptocurrencies like Ethereum or BNB. After attracting sufficient investment, they withdraw all liquidity, making it impossible for investors to sell holdings.
Dumping Schemes: Fraudsters rapidly sell off their cryptocurrency holdings, drastically reducing the value of other investors' tokens. This pump-and-dump manipulation deliberately inflates prices before coordinated selling crashes the market, generating profits for insiders while causing losses for everyone else.
Limited Sell Orders: Scammers restrict token sales for everyone except specific addresses, allowing themselves to sell at will while regular token holders cannot exit positions. This traps investors' funds, rendering their assets completely worthless.
Identifying rug pulls before losing money requires recognizing common warning signs that distinguish legitimate projects from scams.
If the project team lacks transparency or operates under pseudonyms, it represents a major warning sign. Legitimate projects typically have known founders with verifiable backgrounds, LinkedIn profiles, and established industry credentials. Anonymous teams eliminate accountability and make it impossible to pursue legal action after scams.
Look for team members with track records in the cryptocurrency space. Verify their involvement through independent sources rather than trusting project-provided information alone. Check LinkedIn profiles for employment history, connections, and endorsements from reputable industry figures.
Be wary of fake social media identities and accounts. Scammers create elaborate personas with purchased followers and engagement that appear legitimate superficially but lack genuine substance upon deeper investigation.
Reputable cryptocurrency projects undergo third-party security audits by firms like CertiK, Quantstamp, or Trail of Bits. These audits examine smart contract code for vulnerabilities, malicious functions, and potential exploits. Projects lacking audits or refusing to share audit reports raise immediate red flags.
When audits exist, verify their authenticity. Visit the auditing firm's website directly rather than trusting links provided by projects. Read audit reports carefully—legitimate audits detail findings, vulnerabilities discovered, and whether issues were resolved before deployment.
Some scammers create fake audit reports or claim audits that never occurred. Always independently verify audit claims through the auditing company's official channels.
Liquidity locking is a security measure where project liquidity pool tokens are locked in smart contracts for set periods, preventing developers from withdrawing funds prematurely. This builds investor trust by reducing rug pull risk since creators cannot drain liquidity and collapse token values.
Unlocked liquidity allows project owners to withdraw assets at will, creating enormous theft opportunities. To check whether pools have locked liquidity, use tools like GeckoTerminal, which displays liquidity lock status for pools. Every pool on GeckoTerminal shows a GT Score panel indicating whether liquidity is locked—under "Liquidity Lock" for Solana pools and "Rugpull Risk" for Ethereum pools.
If liquidity remains unlocked or locks expire soon, developers maintain complete control over funds and can execute rug pulls at any moment.
Checking token allocation on blockchain explorers like Etherscan or BscScan reveals who holds the most significant token amounts and how coins are allocated. If large percentages are held by small numbers of wallets, the token is more susceptible to price manipulation and dumping.
Healthy token distributions spread holdings across many addresses, preventing any single entity from controlling market dynamics. Projects where developers or early insiders hold 50% or more of supply create enormous risks—these holders can crash prices through coordinated selling.
Use block explorers to determine total token holder counts. If limited users hold a cryptocurrency, it indicates high centralization and manipulation vulnerability. Large, early transactions to unknown wallets also signal potential fund siphoning.
If projects promise unusually high yields or guaranteed returns with little risk, they're likely Ponzi schemes or rug pulls. While DeFi can offer attractive returns, promises of triple-digit annual percentage yields (APYs) typically come with extreme risk or represent outright fraud.
Scammers lure victims with promises of 10% or higher daily returns, often through fake investment platforms. These astronomical figures defy economic reality—legitimate projects cannot sustain such yields long-term without underlying revenue or value creation.
If it sounds too good to be true, it almost certainly is. Approach extraordinary return promises with extreme skepticism and demand clear explanations of how yields are generated.
Whitepapers explain project goals, technology, tokenomics, and roadmaps. Legitimate projects provide detailed whitepapers with concrete technical information, clear use cases, and realistic timelines. Missing, vague, or plagiarized whitepapers indicate lack of substance and potentially fraudulent intent.
Read whitepapers critically. Look for specific technical details, not just marketing buzzwords. Verify claims about technology, partnerships, and team credentials through independent sources. Use plagiarism checkers to ensure whitepapers aren't copied from other projects.
Projects with unclear purposes or existing solely for speculation rather than solving real problems represent major red flags.
While marketing is essential for legitimate projects, excessive hype—especially from unofficial channels or unaffiliated influencers—can indicate scams. Aggressive marketing tactics creating artificial urgency and Fear of Missing Out pressure investors into decisions without proper research.
Scammers often leverage social media, paid influencers, and coordinated campaigns to generate buzz. They create false impressions of organic community growth through bot accounts, purchased engagement, and fake testimonials.
Legitimate projects build communities through value delivery and genuine interest, not manufactured hype. Be especially cautious of projects promising guaranteed returns, emphasizing "limited time offers," or discouraging due diligence.
Be careful about abrupt price movements in new coins, particularly those without liquidity locks. Fraudulent cryptocurrencies tend to see significant price surges before inevitable declines. These artificial pumps result from coordinated buying by scammers using initial funds to inflate values before dumping holdings.
Rapid price increases without clear fundamentals often indicate pump-and-dump schemes linked to potential rug pulls. Monitor price action relative to news, developments, and broader market trends. Spikes occurring without corresponding positive catalysts suggest manipulation.
Poorly written smart contracts indicate inexperienced developers or intentional obfuscation designed to hide malicious functions. Review contract code on blockchain explorers for obvious issues like uncapped minting functions, hidden transfer restrictions, or excessive administrative privileges.
Tools like Token Sniffer automatically analyze smart contracts for common vulnerabilities and malicious patterns. These platforms provide safety scores helping identify dangerous projects before investment.
Healthy projects maintain active trading with substantial volume across multiple exchanges. Low liquidity or irregular trading patterns signal unsustainable projects or potential rug pulls. Projects with minimal trading activity face enormous slippage risks and enable easy price manipulation.
Monitor trading volume trends. Declining volume despite ongoing development activity suggests loss of community interest or insider knowledge of impending problems.
Modern technology provides numerous tools helping identify rug pulls before they execute.
GeckoTerminal includes an inbuilt rug pull checker examining liquidity locks, token distribution, and other critical metrics. Every pool displays a GT Score indicating overall safety based on multiple factors. Use this tool to quickly assess new projects before investing.
DEX scanners like DexTools and DexScreener provide real-time trading data, holder analytics, and liquidity information helping spot suspicious patterns.
Etherscan, BscScan, and similar explorers allow deep investigation of smart contracts, token holders, and transaction histories. Review contract code for malicious functions, examine top holder addresses, and trace fund movements to identify red flags.
Large transfers to exchanges from developer wallets often precede dumps. Monitor these movements to anticipate potential rug pulls.
Token Sniffer provides AI-driven smart contract analysis across multiple blockchains, identifying scams through code examination, liquidity status evaluation, and holder distribution analysis. The platform generates safety scores from 0 to 100, with scores above 80 indicating high reliability and below 50 flagging potential risks.
Additional platforms like GoPlus Security detect malicious addresses and dApp vulnerabilities, providing comprehensive security assessments.
While automated tools provide valuable technical analysis, platforms like Token Metrics offer comprehensive, AI-powered intelligence that goes far beyond surface-level checks. Token Metrics has established itself as a leading crypto trading and analytics platform, providing sophisticated tools essential for protecting against rug pulls and identifying legitimate investment opportunities.
Comprehensive Project Evaluation: Token Metrics assigns each token both a Trader Grade for short-term potential and an Investor Grade for long-term viability. The Investor Grade specifically incorporates security factors including audit status, code quality, team credibility, and liquidity metrics—critical indicators for distinguishing legitimate projects from potential rug pulls.
This dual-rating system enables investors to quickly identify projects with robust foundations versus those exhibiting rug pull characteristics. By analyzing thousands of tokens continuously, Token Metrics identifies patterns and anomalies that individual investors might miss.
Real-Time Risk Monitoring: Token Metrics leverages machine learning and data-driven models to deliver powerful insights across the digital asset ecosystem. The platform monitors code changes, liquidity movements, trading patterns, and social sentiment in real-time, alerting users to suspicious activities that might precede rug pulls.
Customizable alerts via email, SMS, or messaging apps notify investors immediately when projects exhibit warning signs like liquidity removals, unusual whale activity, or sudden team changes. This proactive monitoring proves invaluable for protecting investments from emerging threats.
Team and Development Analysis: Token Metrics evaluates project teams through comprehensive background checks, GitHub activity monitoring, and historical performance analysis. The platform identifies anonymous teams, tracks development progress against roadmap promises, and flags projects with suspicious team behaviors.
By analyzing commit frequency, code quality, and developer engagement, Token Metrics distinguishes projects with genuine development activity from those creating illusions of progress while planning exits.
Social Sentiment and Community Analysis: Token Metrics uses natural language processing to interpret social media trends, community sentiment, and engagement patterns. The platform distinguishes organic community growth from artificial hype campaigns typical of rug pull schemes.
By monitoring discussion quality across Twitter, Reddit, Telegram, and Discord, Token Metrics identifies manufactured enthusiasm, bot activity, and coordinated shilling that often accompany scams.
Liquidity and Market Intelligence: Token Metrics analyzes liquidity depth, distribution, and lock status across exchanges and DeFi protocols. The platform tracks liquidity movements in real-time, alerting users when pools are drained or unlocked—immediate rug pull indicators.
The AI-driven analytics identify suspicious trading patterns including pump-and-dump schemes, wash trading, and coordinated manipulation that frequently precede or accompany rug pulls.
Historical Pattern Recognition: Token Metrics' machine learning models analyze historical rug pull data, identifying patterns and characteristics common across scams. This enables predictive analysis warning investors about projects exhibiting similar profiles before schemes execute.
By learning from past scams, Token Metrics continuously improves its detection capabilities, staying ahead of evolving tactics scammers employ.
Combining technological tools with disciplined investment practices provides optimal protection against rug pulls.
Do Your Own Research remains the golden rule. Investigate project backgrounds, teams, technology, and communities before investing. Don't rely solely on marketing materials or influencer endorsements—verify all claims independently.
Read whitepapers critically, check team credentials on LinkedIn, examine smart contract code (or hire auditors), and engage with communities to assess legitimacy. Look for red flags systematically rather than accepting projects at face value.
When exploring new projects, invest only small amounts initially. This limits potential losses if projects prove fraudulent while allowing participation if they're legitimate. As projects demonstrate sustained legitimacy through delivered milestones and transparent operations, consider increasing positions gradually.
Never invest money you cannot afford to lose entirely. The crypto space remains highly volatile and experimental, with even legitimate projects sometimes failing.
Always confirm liquidity is locked for reasonable periods through independent verification—never trust project claims alone. Use tools like GeckoTerminal to check lock status directly on-chain.
Similarly, verify audit reports through auditing firms' official websites. Read reports carefully to understand issues discovered and whether they were resolved. Multiple audits from reputable firms provide stronger assurance than single audits or audits from unknown companies.
Engage with project communities on Telegram, Discord, and Reddit. Observe whether teams answer questions honestly and address concerns transparently, or whether they censor criticism and avoid difficult topics.
Legitimate projects foster open dialogue and welcome scrutiny. Scammers typically create echo chambers filled with uncritical supporters while silencing dissenting voices.
Stick to well-established exchanges that vet projects before listing. While centralized exchanges aren't immune to listing scams, they generally perform more due diligence than decentralized platforms allowing anyone to list tokens.
Platforms like Token Metrics help identify which projects listed on various exchanges exhibit legitimate characteristics versus rug pull warning signs.
Never concentrate holdings in single projects, especially new or unproven ones. Diversification across multiple assets, sectors, and risk levels protects portfolios from individual project failures including rug pulls.
Allocate larger percentages to established projects with proven track records while limiting exposure to higher-risk newer projects.
Follow trusted crypto news sources, security researchers, and platforms like Token Metrics that provide ongoing project monitoring. Scam alerts and community warnings often emerge before rug pulls execute, giving vigilant investors opportunities to exit positions.
Join crypto security communities on Twitter and Telegram where researchers share findings about suspicious projects in real-time.
Despite best efforts, some investors still fall victim to rug pulls. Taking immediate action minimizes damage and potentially helps others avoid similar fates.
Report fraudulent projects to community-driven platforms like Chainabuse that track scams. In the United States, file reports with the Securities and Exchange Commission (SEC) or Federal Trade Commission (FTC). International investors should contact equivalent financial authorities in their jurisdictions.
While recovering funds remains rare, every report adds to intelligence databases potentially preventing future victims and supporting regulatory actions against perpetrators.
Post detailed warnings on social media platforms like Twitter, relevant Reddit threads (r/CryptoCurrency), and Telegram/Discord channels. Be concise, factual, and transparent. Include token contract addresses, timelines of suspicious activity, and exactly what occurred.
Your warning could prevent others from losing money to the same scam.
If you've realized losses from rug pulls, document transactions thoroughly for potential tax deductions. Many jurisdictions allow capital loss claims for crypto scams, potentially offsetting other investment gains.
Consult tax professionals familiar with cryptocurrency to understand available options for recovering some losses through tax benefits.
Analyze what warning signs you missed and how you could have better protected yourself. Use the experience to strengthen your due diligence processes and avoid repeating mistakes.
Every investor makes errors—the key is learning from them to become more discerning over time.
Rug pulls represent one of cryptocurrency's most persistent threats, costing investors billions annually through increasingly sophisticated schemes. However, armed with knowledge of warning signs, access to analytical tools, and disciplined investment practices, you can dramatically reduce your exposure to these scams.
Critical red flags including anonymous teams, missing audits, unlocked liquidity, irregular token distribution, unrealistic returns, and excessive marketing should immediately trigger additional scrutiny. When multiple red flags appear together, avoid projects entirely regardless of how promising they seem.
Leverage sophisticated analytics platforms like Token Metrics that provide AI-powered project evaluation, real-time risk monitoring, team analysis, and comprehensive market intelligence. These tools identify patterns and anomalies individual investors might miss, offering crucial protection against evolving scam tactics.
Remember that if something sounds too good to be true, it almost certainly is. The most effective defense against rug pulls combines technological tools with common sense, healthy skepticism, and disciplined research practices. Never let FOMO override rational analysis, and always invest only what you can afford to lose.
The cryptocurrency space offers tremendous opportunities for those who navigate it carefully. By understanding rug pull mechanics, recognizing warning signs early, using advanced analytical tools, and maintaining disciplined investment practices, you can participate in crypto's upside while minimizing exposure to its most devastating scams.
Stay vigilant, stay informed, and leverage platforms like Token Metrics to make data-driven decisions. Your financial security in the crypto space depends on your ability to distinguish legitimate innovations from sophisticated frauds—a skill that becomes increasingly valuable as the industry continues evolving in 2025 and beyond.

%201.svg)
%201.svg)
Choosing the right cryptocurrency exchange is one of the most critical decisions for anyone entering the digital asset market. With over 254 exchanges tracked globally and a staggering $1.52 trillion in 24-hour trading volume, the landscape offers tremendous opportunities alongside significant risks. The wrong platform choice can expose you to security breaches, regulatory issues, or inadequate customer support that could cost you your investment.
In 2025, the cryptocurrency exchange industry has matured significantly, with clearer regulatory frameworks, enhanced security standards, and more sophisticated trading tools. However, recent data shows that nearly $1.93 billion was stolen in crypto-related crimes in the first half of 2025 alone, surpassing the total for 2024 and making it crucial to select exchanges with proven track records and robust security measures.
This comprehensive guide examines the most trusted cryptocurrency exchanges in 2025, exploring what makes them reliable, the key factors to consider when choosing a platform, and how to maximize your trading security and success.
Cryptocurrency exchanges are platforms that allow traders to buy, sell, and trade cryptocurrencies, derivatives, and other crypto-related assets. These digital marketplaces have evolved dramatically since Bitcoin's release in 2008, transforming from rudimentary peer-to-peer platforms into sophisticated financial institutions offering comprehensive services.
Centralized Exchanges (CEX): Platforms like Binance, Coinbase, and Kraken hold your funds and execute trades on your behalf, acting as intermediaries similar to traditional banks. These exchanges offer high liquidity, fast transaction speeds, user-friendly interfaces, and customer support but require trusting the platform with custody of your assets.
Decentralized Exchanges (DEX): Platforms enabling direct peer-to-peer trading without intermediaries, offering greater privacy and self-custody but typically with lower liquidity and more complex user experiences.
Hybrid Exchanges: In 2025, some platforms seek to offer the best of both worlds, providing the speed of centralized exchanges with the self-custodial nature of decentralized platforms. Notable examples include dYdX v4, Coinbase Wallet with Base integration, and ZK-powered DEXs.
Brokers: Platforms like eToro and Robinhood that allow crypto purchases at set prices without orderbook access, prioritizing simplicity over advanced trading features.
Selecting a trustworthy exchange requires evaluating multiple dimensions beyond just trading fees and available cryptocurrencies. The following factors distinguish truly reliable platforms from potentially risky alternatives.
Security remains the paramount concern, with exchanges now required to implement rigorous know-your-customer and anti-money laundering protocols in addition to meeting new licensing and reporting requirements. The most trusted exchanges maintain industry-leading security protocols including two-factor authentication, cold storage for the majority of assets, regular security audits, and comprehensive insurance funds.
Regulatory compliance has become increasingly important as governments worldwide develop frameworks for digital assets. Licensed exchanges that comply with regulations are more trustworthy and less likely to face sudden shutdowns or regulatory actions. In 2025, anti-money laundering and countering terrorism financing requirements continue as core elements of the regulatory framework for cryptocurrency businesses.
Markets in Crypto-Assets Regulation (MiCA): The European Union's comprehensive framework entered full application in late 2024, establishing uniform market rules for crypto-assets across member states. Exchanges operating under MiCA provide additional assurance of regulatory compliance and consumer protection.
U.S. Regulatory Evolution: Early 2025 marked a turning point in U.S. crypto regulation, with the SEC's Crypto Task Force working to provide clarity on securities laws application to crypto assets. The CLARITY Act, advancing through Congress, aims to distinguish digital commodities from securities, creating clearer regulatory boundaries.
High liquidity ensures easier entry and exit points, enhancing investor confidence and enabling traders to execute large orders without significant price impact. The best exchanges support large numbers of coins and trading pairs, offering spot trading, margin trading, futures, options, staking, and various earning programs.
According to current market data, the three largest cryptocurrency exchanges by trading volume are Binance, Bybit, and MEXC, with total tracked crypto exchange reserves currently standing at $327 billion. These platforms dominate due to their deep liquidity, extensive asset support, and comprehensive feature sets.
Trading fees can significantly erode profits over time, making fee comparison essential. Most exchanges employ maker-taker fee models, where makers who add liquidity to orderbooks pay lower fees than takers who remove liquidity. Fee structures typically range from 0.02% to 0.6%, with volume-based discounts rewarding high-frequency traders.
Beyond trading fees, consider deposit and withdrawal charges, staking fees, and any hidden costs associated with different transaction types. Some exchanges offer zero-fee trading pairs or native token discounts to reduce costs further.
Responsive customer support proves invaluable when issues arise. The best exchanges offer 24/7 multilingual support through multiple channels including live chat, email, and comprehensive help documentation. User experience encompasses both desktop and mobile platforms, with over 72% of users now trading via mobile apps according to recent data.
Educational resources, including learning centers, tutorials, and market analysis, help users make informed decisions and maximize platform features. Exchanges prioritizing education demonstrate commitment to user success beyond just facilitating transactions.
Based on security track records, regulatory compliance, user reviews, and feature sets, these exchanges have earned recognition as the most trustworthy platforms in the current market.
Kraken stands out as one of the few major platforms that has never experienced a hack resulting in loss of customer funds. Founded in 2011, Kraken has gained popularity thanks to its transparent team and strong focus on security, with CEO Jesse Powell often echoing the principle "Not your keys, not your crypto" while actively encouraging self-custody.
The platform offers more than 350 cryptocurrencies to buy, sell, and trade, making it one of the top exchanges for variety. Kraken maintains licenses across the United States, Canada, Australia, the United Kingdom, the European Union, and several other regions worldwide. This focus on compliance, security, and transparency has earned trust from both clients and regulators.
Kraken provides two primary interfaces: a standard version for beginners and Kraken Pro—a customizable platform for advanced traders featuring enhanced technical analysis tools, powerful margin trading, and access to sophisticated order types. All features are supported by responsive 24/7 multilingual support and educational resources.
Key Strengths:
Reputable independent industry reviewers like Kaiko and CoinGecko consistently rank Kraken among the best crypto exchanges worldwide.
Coinbase is one of the most widely known crypto exchanges in the United States and globally, often serving as the starting point for those just entering the digital assets space. Founded in 2012 by Brian Armstrong and Fred Ehrsam, Coinbase now serves customers in more than 190 countries and has approximately 36 million users as of September 2025.
The platform supports around 250 cryptocurrencies, with asset availability depending on region and account type. Coinbase offers both a standard version for beginners and Coinbase Advanced for more sophisticated trading tools and reduced fees. The exchange excels in its commitment to security, using advanced features including two-factor authentication and cold storage for the majority of assets.
Coinbase is one of the few exchanges that is publicly traded, enhancing its credibility and transparency. Users can feel confident knowing Coinbase operates under stringent regulatory guidelines, adding extra layers of trust. The platform maintains strong regulatory presence in the U.S. and is widely available in most U.S. states.
Key Strengths:
Coinbase and Kraken are considered the most secure exchanges due to their strong regulatory compliance and robust security measures.
Binance, founded in 2017, quickly reached the number one spot by trade volumes, registering more than $36 billion in trades by early 2021 and maintaining its position as the world's largest exchange. The platform serves approximately 250 million users as of January 2025, offering one of the most comprehensive cryptocurrency ecosystems in the industry.
Binance supports hundreds of cryptocurrencies and provides extensive trading options including spot, margin, futures, staking, launchpool, and various earning programs. The exchange has one of the lowest trading fees among major platforms, ranging around 0.1%, with further reductions available through native BNB token usage.
The platform maintains a clean interface with over 72% of users trading via the mobile app. Binance stores 10% of user funds in its Secure Asset Fund for Users (SAFU), providing an additional safety net against potential security incidents. The exchange offers both a standard platform and Binance Pro for advanced traders.
Key Strengths:
Note that regulatory status varies by region, with Binance.US operating separately under U.S. regulations with different features and fee structures.
Founded in 2014 by Cameron and Tyler Winklevoss, Gemini has solidified its position in the cryptocurrency exchange sphere with over $175 million in trading volume. The platform is recognized for taking additional security measures and providing high-end service suitable for both beginners and advanced users.
Gemini maintains comprehensive insurance for digital assets stored on the platform and operates as a New York trust company, subjecting it to banking compliance standards. The exchange is fully available across all U.S. states with no geographic restrictions, maintaining strong regulatory relationships nationwide.
The platform offers both simple interfaces for beginners and ActiveTrader for more sophisticated users. Gemini provides various earning options including staking and interest-bearing accounts. The exchange has launched innovative products including the Gemini Dollar stablecoin, demonstrating ongoing commitment to crypto ecosystem development.
Key Strengths:
OKX has emerged as a major global exchange offering extensive trading options across spot, futures, and derivatives markets. The platform serves users in over 180 countries and supports hundreds of digital assets with deep liquidity across major trading pairs.
The exchange provides advanced trading tools, comprehensive charting, and sophisticated order types suitable for professional traders. OKX maintains competitive fee structures and offers various earning opportunities through staking, savings, and liquidity provision programs.
Key Strengths:
Bitstamp, founded in 2011, stands as one of the oldest continuously operating cryptocurrency exchanges. The platform was among the first to be registered by BitLicense in New York, demonstrating early commitment to regulatory compliance.
The exchange adopted a tiered fee structure based on 30-day trading volumes, with fees ranging from 0% for high-volume traders to 0.5% for smaller transactions. Bitstamp maintains strong security practices and banking relationships, particularly in Europe where it serves as a primary fiat on-ramp for many investors.
Key Strengths:
While choosing a trusted exchange provides the foundation for secure crypto trading, maximizing returns requires sophisticated analytics and market intelligence. This is where Token Metrics, a leading AI-powered crypto trading and analytics platform, becomes invaluable for serious investors.
Token Metrics provides personalized crypto research and predictions powered by AI, helping users identify the best trading opportunities across all major exchanges. The platform monitors thousands of tokens continuously, providing real-time insights that enable informed decision-making regardless of which exchange you use.
Token Metrics assigns each token both a Trader Grade for short-term potential and an Investor Grade for long-term viability. These dual ratings help traders determine not just what to buy, but when to enter and exit positions across different exchanges for optimal returns.
The platform offers AI-generated buy and sell signals that help traders time their entries and exits across multiple exchanges. Token Metrics analyzes market conditions, technical indicators, sentiment data, and on-chain metrics to provide actionable trading recommendations.
Customizable alerts via email, SMS, or messaging apps ensure you never miss important opportunities or risk signals, regardless of which exchange hosts your assets. This real-time monitoring proves particularly valuable when managing portfolios across multiple platforms.
Token Metrics leverages machine learning and data-driven models to deliver powerful insights across the digital asset ecosystem. The platform's AI-managed indices dynamically rebalance based on market conditions, providing diversified exposure optimized for current trends.
For traders using multiple exchanges, Token Metrics provides unified portfolio tracking and performance analysis, enabling holistic views of holdings regardless of where assets are stored. This comprehensive approach ensures optimal allocation across platforms based on liquidity, fees, and available trading pairs.
Token Metrics helps users identify which exchanges offer the best liquidity, lowest fees, and optimal trading conditions for specific assets. The platform's analytics reveal where institutional money flows, helping traders follow smart money to exchanges with the deepest liquidity for particular tokens.
By analyzing order book depth, trading volumes, and price spreads across exchanges, Token Metrics identifies arbitrage opportunities and optimal execution venues for large trades. This intelligence enables traders to minimize slippage and maximize returns.
Beyond trading analytics, Token Metrics evaluates the security posture of projects listed on various exchanges, helping users avoid scams and high-risk tokens. The platform's Investor Grade incorporates security audit status, code quality, and team credibility—factors critical for distinguishing legitimate projects from potential frauds.
Token Metrics provides alerts about security incidents, exchange issues, or regulatory actions that might affect asset accessibility or value. This proactive risk monitoring protects users from unexpected losses related to platform failures or project compromises.
Token Metrics launched its integrated trading feature in 2025, transforming the platform into an end-to-end solution where users can analyze opportunities, compare exchange options, and execute trades seamlessly. This integration enables traders to act on insights immediately without navigating between multiple platforms.
The seamless connection between analytics and execution ensures security-conscious investors can capitalize on opportunities while maintaining rigorous risk management across all their exchange accounts.
Even when using trusted exchanges, implementing proper security practices remains essential for protecting your assets.
Two-factor authentication (2FA) provides critical additional security beyond passwords. Use authenticator apps like Google Authenticator or Authy rather than SMS-based 2FA, which remains vulnerable to SIM swap attacks. Enable 2FA for all account actions including logins, withdrawals, and API access.
While trusted exchanges maintain strong security, self-custody eliminates counterparty risk entirely. Hardware wallets like Ledger or Trezor provide optimal security for long-term holdings, keeping private keys completely offline and safe from exchange hacks.
Follow the principle "not your keys, not your crypto" for significant amounts. Keep only actively traded assets on exchanges, transferring long-term holdings to personal cold storage.
Many exchanges offer withdrawal address whitelisting, restricting withdrawals to pre-approved addresses. Enable this feature and require extended waiting periods for adding new addresses, preventing attackers from quickly draining accounts even if they gain access.
Regularly review login history, active sessions, and transaction records. Enable email and SMS notifications for all account activity including logins, trades, and withdrawals. Immediate awareness of unauthorized activity enables faster response to security incidents.
Never share account credentials, avoid accessing exchanges on public Wi-Fi networks, keep software and operating systems updated, and use unique strong passwords for each exchange account. Consider using a dedicated email address for crypto activities separate from other online accounts.
Crypto regulations and exchange availability vary significantly by region, requiring consideration of local factors when selecting platforms.
Coinbase has the strongest regulatory presence and widest state availability. Kraken offers comprehensive services with strong compliance. Binance.US operates separately with more limited features than the international platform. Regulatory clarity improved in 2025 with the CLARITY Act and enhanced SEC guidance.
The MiCA regulation provides comprehensive framework ensuring consumer protection and regulatory clarity. Kraken, Bitstamp, and Binance all maintain strong European presence with full MiCA compliance. SEPA integration provides efficient fiat on-ramps for EU users.
FCA-registered exchanges including Kraken, eToro, and Bitstamp offer strong security measures and regulatory compliance. Brexit created distinct regulatory regime requiring specific licensing for UK operations.
Bybit and OKX provide extensive services across the region. Regulatory approaches vary dramatically by country, from crypto-friendly jurisdictions like Singapore to more restrictive environments requiring careful platform selection.
The cryptocurrency exchange landscape continues evolving rapidly with several key trends shaping the industry's future.
Major financial institutions are increasingly offering crypto services, with traditional banks now providing custody following the SEC's replacement of SAB 121 with SAB 122 in early 2025. This institutional embrace drives higher security standards and regulatory clarity across the industry.
Centralized exchanges are integrating decentralized finance protocols, offering users access to yield farming, liquidity provision, and lending directly through exchange interfaces. This convergence provides best-of-both-worlds functionality combining CEX convenience with DeFi opportunities.
Exchanges face tighter compliance requirements including enhanced KYC/AML protocols, regular audits, and transparent reserve reporting. These measures increase user protection while creating barriers to entry for less-established platforms.
AI-powered trading assistance, sophisticated algorithmic trading tools, and professional-grade analytics are becoming standard offerings. Platforms like Token Metrics demonstrate how artificial intelligence revolutionizes crypto trading by providing insights previously available only to institutional investors.
Selecting trusted crypto exchanges requires balancing multiple factors including security track records, regulatory compliance, available features, fee structures, and regional accessibility. In 2025, exchanges like Kraken, Coinbase, Binance, Gemini, and Bitstamp have earned recognition as the most reliable platforms through consistent performance and strong security practices.
The most successful crypto traders don't rely on exchanges alone—they leverage sophisticated analytics platforms like Token Metrics to maximize returns across all their exchange accounts. By combining trusted exchange infrastructure with AI-powered market intelligence, traders gain significant advantages in identifying opportunities, managing risks, and optimizing portfolio performance.
Remember that no exchange is completely risk-free. Implement proper security practices including two-factor authentication, cold storage for significant holdings, and continuous monitoring of account activity. Diversify holdings across multiple trusted platforms to reduce concentration risk.
As the crypto industry matures, exchanges with strong regulatory compliance, proven security records, and commitment to transparency will continue dominating the market. Choose platforms aligned with your specific needs—whether prioritizing low fees, extensive coin selection, advanced trading tools, or regulatory certainty—and always conduct thorough research before committing significant capital.
With the right combination of trusted exchanges, robust security practices, and sophisticated analytics from platforms like Token Metrics, you can navigate the crypto market with confidence, maximizing opportunities while minimizing risks in this exciting and rapidly evolving financial landscape.

%201.svg)
%201.svg)
The cryptocurrency market has evolved from a niche digital experiment into a multi-trillion-dollar asset class. With thousands of tokens and coins available across hundreds of exchanges, the question isn't whether you should research before buying—it's how to conduct that research effectively. Smart investors know that thorough due diligence is the difference between identifying the next promising project and falling victim to a costly mistake.
Before diving into specific research methods, successful crypto investors start by understanding the fundamental difference between various digital assets. Bitcoin operates as digital gold and a store of value, while Ethereum functions as a programmable blockchain platform. Other tokens serve specific purposes within their ecosystems—governance rights, utility functions, or revenue-sharing mechanisms.
The first step in any research process involves reading the project's whitepaper. This technical document outlines the problem the project aims to solve, its proposed solution, tokenomics, and roadmap. While whitepapers can be dense, they reveal whether a project has substance or merely hype. Pay attention to whether the team clearly articulates a real-world problem and presents a viable solution.
A cryptocurrency project is only as strong as the team behind it. Investors scrutinize founder backgrounds, checking their LinkedIn profiles, previous projects, and industry reputation. Have they built successful companies before? Do they have relevant technical expertise? Anonymous teams aren't automatically red flags, but they require extra scrutiny and compelling reasons for their anonymity.
Development activity serves as a crucial health indicator for any blockchain project. GitHub repositories reveal whether developers are actively working on the project or if it's effectively abandoned. Regular commits, open issues being addressed, and community contributions all signal a vibrant, evolving project. Conversely, repositories with no activity for months suggest a project that may be dying or was never serious to begin with.
Understanding a token's economic model is essential for predicting its long-term value potential. Investors examine total supply, circulating supply, and emission schedules. Is the token inflationary or deflationary? How many tokens do the team and early investors hold, and when do those tokens unlock? Large unlock events can trigger significant price drops as insiders sell.
The token's utility within its ecosystem matters tremendously. Does holding the token provide governance rights, staking rewards, or access to platform features? Tokens without clear utility often struggle to maintain value over time. Smart researchers also investigate how value accrues to token holders—whether through buybacks, burning mechanisms, or revenue sharing.
Price action tells only part of the story, but market metrics provide valuable context. Trading volume indicates liquidity—can you buy or sell significant amounts without drastically moving the price? Market capitalization helps determine a token's relative size and potential growth runway. A small-cap project has more room to grow but carries higher risk.
On-chain metrics offer deeper insights into token health. Active addresses, transaction volume, and network usage reveal actual adoption versus speculation. High trading volume on exchanges with minimal on-chain activity might indicate wash trading or manipulation. Token distribution matters too—if a small number of wallets hold most of the supply, the token faces centralization risks and potential price manipulation.
Professional crypto investors increasingly rely on sophisticated analytics platforms that aggregate multiple data sources and provide actionable insights. Token Metrics has emerged as a leading crypto trading and analytics platform, offering comprehensive research tools that save investors countless hours of manual analysis.
Token Metrics combines artificial intelligence with expert analysis to provide ratings and predictions across thousands of cryptocurrencies. The platform evaluates projects across multiple dimensions—technology, team, market metrics, and risk factors—delivering clear scores that help investors quickly identify promising opportunities. Rather than manually tracking dozens of metrics across multiple websites, users access consolidated dashboards that present the information that matters most.
The platform's AI-driven approach analyzes historical patterns and current trends to generate price predictions and trading signals. For investors overwhelmed by the complexity of crypto research, Token Metrics serves as an invaluable decision-support system, translating raw data into understandable recommendations. The platform covers everything from established cryptocurrencies to emerging DeFi tokens and NFT projects, making it a one-stop solution for comprehensive market research.
Cryptocurrency projects thrive or die based on their communities. Active, engaged communities signal genuine interest and adoption, while astroturfed communities relying on bots and paid shillers raise red flags. Investors monitor project Discord servers, Telegram channels, and Twitter activity to gauge community health.
Social sentiment analysis has become increasingly sophisticated, with tools tracking mentions, sentiment polarity, and influencer engagement across platforms. Sudden spikes in social volume might indicate organic excitement about a partnership or product launch—or orchestrated pump-and-dump schemes. Experienced researchers distinguish between authentic enthusiasm and manufactured hype.
The regulatory landscape significantly impacts cryptocurrency projects. Researchers investigate whether projects have faced regulatory scrutiny, registered as securities, or implemented compliance measures. Geographic restrictions, potential legal challenges, and regulatory clarity all affect long-term viability.
Security audits from reputable firms like CertiK, Trail of Bits, or ConsenSys Diligence provide crucial assurance about smart contract safety. Unaudited contracts carry significant risk of exploits and bugs. Researchers also examine a project's history—has it been hacked before? How did the team respond to security incidents?
Experienced investors develop instincts for spotting problematic projects. Guaranteed returns and promises of unrealistic gains are immediate red flags. Legitimate projects acknowledge risk and market volatility rather than making impossible promises. Copied whitepapers, stolen team photos, or vague technical descriptions suggest scams.
Pressure tactics like "limited time offers" or artificial scarcity designed to force quick decisions without research are classic manipulation techniques. Projects with more focus on marketing than product development, especially those heavily promoted by influencers being paid to shill, warrant extreme skepticism.
Cryptocurrency research isn't a one-time activity but an ongoing process. Markets evolve rapidly, projects pivot, teams change, and new competitors emerge. Successful investors establish systems for monitoring their holdings and staying updated on developments. Setting up Google Alerts, following project social channels, and regularly reviewing analytics help maintain awareness of changing conditions.
Whether you're evaluating established cryptocurrencies or exploring emerging altcoins, thorough research remains your best defense against losses and your greatest tool for identifying opportunities. The time invested in understanding what you're buying pays dividends through better decision-making and improved portfolio performance in this dynamic, high-stakes market.

%201.svg)
%201.svg)
The cryptocurrency industry has revolutionized finance and created incredible wealth-building opportunities, but it has also become a breeding ground for sophisticated scams that target unsuspecting investors. As the crypto market matures in 2025, scammers have evolved their tactics, making it more challenging than ever to distinguish legitimate opportunities from fraudulent schemes. Understanding how to protect yourself in crypto communities isn't just recommended—it's essential for survival in this space.
Cryptocurrency scams have cost investors billions of dollars globally, with losses continuing to mount each year. From fake investment platforms and phishing attacks to rug pulls and Ponzi schemes, the variety and sophistication of crypto scams can be overwhelming. The decentralized and largely unregulated nature of cryptocurrency makes it particularly attractive to criminals, as transactions are irreversible and often difficult to trace.
What makes crypto scams especially insidious is that they frequently target the very communities designed to help investors—social media groups, Discord servers, Telegram channels, and Reddit forums where enthusiasts gather to share information and strategies. Scammers infiltrate these spaces, build trust, and then exploit that trust for financial gain.
Understanding the landscape of crypto scams is your first line of defense. Phishing scams remain among the most prevalent, with criminals creating fake websites that mimic legitimate exchanges or wallet services to steal login credentials and private keys. These scams often circulate through community channels disguised as official announcements or helpful resources.
Pump-and-dump schemes proliferate in Telegram groups and Discord servers where coordinated groups artificially inflate the price of low-cap cryptocurrencies before selling their holdings, leaving other investors with worthless tokens. These schemes often promise "guaranteed returns" or insider information about the "next 100x coin."
Impersonation scams have become increasingly sophisticated, with fraudsters creating fake profiles that mimic influencers, project founders, or platform administrators. They reach out to community members via direct messages offering investment opportunities, giveaways, or technical support—all designed to steal funds or private information.
Fake ICOs and token launches represent another major threat, with scammers creating professional-looking websites and marketing materials for non-existent projects. They collect investor funds and then disappear completely—a practice known as a "rug pull."
Giveaway scams frequently appear across social media platforms, claiming that celebrities or major crypto figures are giving away cryptocurrency. The catch? You need to send crypto first to "verify your address" or "unlock your reward." These are always scams—legitimate giveaways never require upfront payment.
Developing a keen eye for warning signs can save you from devastating losses. Any investment opportunity promising guaranteed returns or extraordinarily high yields with zero risk should immediately raise suspicions. In legitimate financial markets, higher returns always come with higher risk—there are no exceptions.
Unsolicited direct messages offering investment advice or opportunities are almost always scams. Legitimate projects and platforms don't cold-message potential investors through social media. Similarly, excessive pressure to invest immediately or claims about "limited-time opportunities" are classic manipulation tactics designed to prevent you from conducting proper due diligence.
Poor grammar, spelling errors, and unprofessional communication often indicate scams, though sophisticated fraudsters have improved in this area. More reliable indicators include anonymous teams, lack of verifiable credentials, and absence of working products or prototypes. Always be wary of projects that can't clearly explain their technology, use case, or business model.
Requests for private keys, seed phrases, or wallet passwords are absolute deal-breakers. No legitimate service ever needs this information. Your private keys are like the keys to your house—you never give them to anyone, regardless of the reason they provide.
Protecting yourself requires implementing multiple layers of security. Start by enabling two-factor authentication (2FA) on all your crypto accounts using authenticator apps rather than SMS, which can be vulnerable to SIM-swapping attacks. Use hardware wallets for storing significant amounts of cryptocurrency, keeping the majority of your holdings offline and away from potential hackers.
Create unique, complex passwords for each crypto-related account using a reputable password manager. Never reuse passwords across platforms, as a breach on one site could compromise all your accounts. Be especially cautious about which browser extensions you install, as malicious extensions can steal wallet information and transaction data.
Before joining any crypto community or platform, verify its legitimacy through multiple independent sources. Check official websites, read reviews from established crypto news sites, and look for red flags in community discussions. Platforms like Token Metrics—a leading crypto trading and analytics platform—provide comprehensive project ratings and analysis that help investors separate legitimate opportunities from potential scams through data-driven research and AI-powered risk assessment.
Due diligence is your most powerful weapon against scams. When evaluating any cryptocurrency project, start by researching the team behind it. Legitimate projects have doxxed team members with verifiable LinkedIn profiles, previous work experience, and professional reputations. Be extremely cautious of anonymous teams, especially for projects seeking significant investment.
Examine the project's whitepaper carefully. While technical complexity doesn't guarantee legitimacy, vague or plagiarized whitepapers are major red flags. Search for phrases from the whitepaper online to check for plagiarism. Legitimate projects invest significant resources into creating original, detailed technical documentation.
Check the project's smart contract code if it's been deployed. Many scams include malicious code that prevents investors from selling tokens or allows developers to drain liquidity pools. Use blockchain explorers to verify contract addresses and examine transaction histories. Look for third-party smart contract audits from reputable firms—though remember that even audited projects can be scams if audits are faked.
Token Metrics excels in this area by providing comprehensive fundamental analysis, on-chain metrics, and risk assessments that help investors evaluate projects objectively. The platform's AI-driven approach analyzes thousands of data points to identify potential red flags and assess project viability, making it an invaluable tool for avoiding scams while identifying genuine opportunities.
Different crypto communities require different approaches to safety. In Discord and Telegram groups, be aware that scammers often create bot accounts or compromise existing accounts to spread malicious links. Never click on links from users you don't know, and always verify URLs carefully before entering any credentials.
On Twitter and other social media platforms, verify accounts by checking for official verification badges and cross-referencing with information from official project websites. Be aware that scammers create look-alike accounts with similar handles and profile pictures to impersonate legitimate figures.
In Reddit communities, check user history and karma scores before trusting financial advice. Scammers often use new accounts or purchased accounts with minimal activity. Participate in established communities like r/CryptoCurrency where moderation teams actively combat scams and misinformation.
When participating in crypto communities, maintain operational security by never discussing specific investment amounts, wallet addresses, or holdings publicly. This information makes you a target for sophisticated social engineering attacks.
Leverage technology to enhance your security posture. Use VPNs when accessing crypto accounts from public networks, install reputable antivirus and anti-malware software, and regularly update all your devices and applications to patch security vulnerabilities.
Blockchain analytics tools can help you verify transaction histories and identify suspicious activity. Platforms like Token Metrics integrate advanced analytics with trading signals and portfolio management tools, providing institutional-grade security insights previously available only to professional investors. The platform's comprehensive approach combines technical analysis, fundamental research, and AI-powered predictions to help users make informed decisions while avoiding fraudulent projects.
Set up alerts for unusual account activity and regularly monitor your exchange accounts and wallets for unauthorized transactions. The faster you detect potential compromises, the better your chances of minimizing damage.
If you identify a potential scam, report it immediately to the platform where you encountered it and warn other community members. Most crypto platforms have dedicated channels for reporting suspicious activity. Document everything, including screenshots, wallet addresses, and communication records—this information may be valuable for investigations or recovery efforts.
If you've been scammed, act quickly. Contact your exchange immediately if funds are still in transit, report the incident to relevant authorities, and share your experience in community forums to prevent others from falling victim. While recovery is often difficult, rapid action sometimes enables partial fund recovery.
Avoiding scams in crypto communities requires ongoing vigilance rather than one-time actions. Stay educated about emerging scam tactics by following reputable crypto security experts and news sources. Regularly review and update your security practices as new threats emerge.
Maintain a healthy skepticism about opportunities that seem too good to be true—because they usually are. Trust but verify should be your mantra in crypto communities. Before investing in any project, regardless of how enthusiastic the community appears, conduct thorough independent research.
Consider using professional-grade analytics and research platforms like Token Metrics to supplement your due diligence. The platform's comprehensive ratings, AI-driven insights, and risk assessment tools provide objective analysis that helps cut through hype and identify legitimate opportunities while flagging potential scams.
Navigating crypto communities safely in 2025 requires awareness, vigilance, and the right tools. While scams continue to evolve in sophistication, informed investors who implement robust security practices, conduct thorough due diligence, and leverage professional analytics platforms significantly reduce their risk exposure.
Remember that in cryptocurrency, you are your own bank—which means you're also responsible for your own security. No legitimate investment requires you to share private keys, send funds upfront, or make rushed decisions under pressure. By combining community wisdom with professional tools like Token Metrics, maintaining healthy skepticism, and following the security practices outlined in this guide, you can participate confidently in crypto communities while protecting your investments from fraudulent schemes.
The crypto industry offers tremendous opportunities for those who approach it intelligently and cautiously. Stay informed, stay skeptical, and always prioritize security over potential gains. Your future self will thank you for the diligence you exercise today.

%201.svg)
%201.svg)
The cryptocurrency market continues to expand at a breakneck pace, with new tokens launching daily across multiple blockchain networks. While this innovation presents exciting opportunities for early investors to capture significant gains, it also introduces substantial risks. In 2024 alone, scams like rug pulls and honeypots cost investors $1.2 billion, demonstrating the critical importance of thorough project vetting.
As the crypto market surpasses $3 trillion in valuation, distinguishing legitimate projects from sophisticated scams has become both more challenging and more essential. Communities have developed robust frameworks for evaluating new cryptocurrencies, combining technical analysis, social intelligence, and specialized tools to identify promising opportunities while avoiding catastrophic losses.
This comprehensive guide explores how experienced crypto communities vet new projects in 2025, providing you with the knowledge and tools necessary to make informed investment decisions in this volatile landscape.
Crypto due diligence is a multifaceted research process that goes beyond simply analyzing historical price charts. It involves comprehensive assessment of a cryptocurrency project, encompassing technological underpinnings, financial health, regulatory compliance, security measures, and team competence.
Despite significant growth, crypto remains a volatile and under-regulated environment where project life cycles are short, scams are frequent, and technical vulnerabilities can be catastrophic. Traditional investing relies on established vetting frameworks, but many crypto decisions still happen informally over Telegram, Discord, or X, making formalized due diligence more critical than ever.
The notorious case of influencer Hailey Welch's HAWK token exemplifies these risks. In early 2025, the token quickly reached a market value of $490 million following her promotion, but lost over 90 percent of its value shortly after launch when blockchain records revealed that just ten wallets controlled 96 percent of the supply.
Similarly, Argentina's President Javier Milei publicly supported a cryptocurrency called LIBRA in 2025, describing it as an initiative to boost private sector growth. Investors rushed to buy, causing prices to skyrocket before eventual collapse—highlighting the danger of trusting celebrity endorsements without thorough verification.
Communities employ systematic frameworks addressing key risk areas that separate legitimate projects from potential scams. Understanding these components is fundamental to protecting your investment.
Financial transparency provides clarity around token allocation, treasury management, and fundraising history. A well-designed token economy incentivizes network participation and long-term sustainability, while poorly structured tokenomics often signal underlying problems.
Critical Elements to Examine:
Analyze the project's token distribution, vesting schedules, and overall economic model. Beware of projects with overly concentrated token ownership or inflationary mechanisms that dilute value over time. Check if liquidity is locked using services like UNCX and verify the lock duration—unlocked liquidity enables rug pulls where developers drain funds.
Examine token allocation across founders, team members, early investors, and community. Projects allocating excessive percentages to insiders create selling pressure and manipulation risks. Healthy distributions typically reserve substantial portions for community growth, ecosystem development, and long-term incentives.
Assess token utility beyond speculation. Does the token serve a genuine purpose within the ecosystem? Tokens without clear use cases are generally speculative and prone to drastic price swings, making them vulnerable to pump-and-dump schemes.
Technical security encompasses comprehensive audits of smart contracts and blockchain architecture. Smart contract vulnerabilities can lead to significant financial losses, making security verification paramount.
Smart Contract Audits:
Ensure smart contracts have been audited by reputable third-party security firms like CertiK, OpenZeppelin, or Trail of Bits. Review audit reports for critical vulnerabilities, and verify that identified issues have been resolved before deployment. Projects lacking audits or refusing to publish audit results raise major red flags.
Verified contracts ensure code is publicly viewable on block explorers like Etherscan or BscScan, allowing community members to inspect the code. Check for honeypot mechanisms—malicious code restricting token sales, trapping investors who can buy but never sell.
Blockchain Analysis:
Understand the underlying blockchain technology and consensus mechanism. Assess scalability, security, and transaction speed. Research the network's history of hacks or vulnerabilities that might compromise project security.
A token project is only as credible as its team. Investigation of identities, credentials, and track records of founders, developers, and advisors is essential for assessing project legitimacy.
Founder and Team Research:
Verify claims such as education and employment history through LinkedIn profiles, industry reports, and professional networks. Look for any past business failures, fraud, or involvement in failed projects. Independent background checks can confirm team members are who they claim to be and flag past criminal convictions, lawsuits, or financial troubles.
An anonymous or inexperienced team—while not uncommon in crypto—carries higher risk than teams led by reputable, known professionals. In the wake of recent scandals, investors should prioritize thorough background checks rather than trusting endorsements from other investors.
Check if team members have participated in industry conferences, contributed to open-source projects, or received recognition from established blockchain organizations. A team actively engaged with the broader crypto community demonstrates commitment and expertise.
Regulatory compliance has become increasingly important as governments worldwide develop frameworks for digital assets. Determine the project's legal jurisdiction and applicable regulations, as crypto regulations vary significantly across countries.
Compliance Verification:
Ensure the project adheres to KYC (Know Your Customer) and AML (Anti-Money Laundering) requirements. Projects operating in regulated environments provide more security and lower risks of sudden regulatory shutdowns. Verify registration with relevant financial authorities and confirm necessary permits.
Assess whether the token might be classified as a security under applicable laws. Securities classification imposes additional regulatory burdens and restrictions on trading. Projects ignoring securities laws face regulatory enforcement that can destroy token value overnight.
Modern crypto communities leverage sophisticated tools designed to analyze smart contracts and identify risky projects by evaluating code, liquidity, and holder distribution.
Token Sniffer is a powerful AI-driven platform that scans smart contracts across 15 blockchains, including Ethereum, BNB Chain, and Polygon, to detect potential scams like rug pulls, honeypots, or malicious code. It provides safety scores from 0 to 100 based on contract analysis, liquidity status, and holder distribution.
Using Token Sniffer Effectively:
Always use contract addresses rather than token names to avoid fake tokens with similar names. Find the contract address on platforms like CoinMarketCap, CoinGecko, or the project's official website, then paste it into Token Sniffer's search bar.
Token Sniffer generates detailed reports with safety scores where scores above 80 indicate high reliability, 50-80 suggests caution, and below 50 flags potential risks. The platform checks for verified contracts, honeypot mechanisms, similar contracts copied from known scams, and liquidity analysis.
Complementary Tools:
Token Sniffer has limitations, such as incomplete data for new tokens or lack of Solana support. Complement it with DexTools for analyzing buy/sell activity and liquidity pools, Soul Sniffer for Solana-based tokens, Etherscan/BscScan for verifying contract code, and GoPlus Security for detecting malicious addresses and dApp vulnerabilities.
While automated tools provide valuable technical analysis, platforms like Token Metrics offer comprehensive, AI-powered insights that go beyond surface-level checks. Token Metrics has emerged as a leading crypto analytics platform, providing the sophisticated analysis necessary for identifying legitimate projects with long-term potential.
AI-Driven Project Evaluation:
Token Metrics leverages machine learning and data-driven models to deliver powerful, actionable insights across the digital asset ecosystem. The platform assigns each token both a Trader Grade for short-term potential and an Investor Grade for long-term viability, helping users prioritize opportunities efficiently.
The Investor Grade specifically considers technical factors including code quality, development activity, security audit status, and team credibility—critical indicators of project robustness that distinguish legitimate ventures from scams. This dual-rating system helps investors distinguish between assets suitable for quick trading gains versus those appropriate for long-term holdings.
Real-Time Monitoring and Alerts:
Token Metrics monitors thousands of projects continuously, tracking code updates, audit reports, and security incidents that might indicate smart contract vulnerabilities. By analyzing development patterns, commit frequency, and team responsiveness to identified issues, Token Metrics helps investors avoid projects with poor security practices.
The platform's real-time alerts notify users about significant code changes, audit failures, or security incidents that could affect their holdings. Customizable alerts via email, SMS, or messaging apps ensure you never miss important opportunities or risk signals.
Community Sentiment and Social Analysis:
Token Metrics uses natural language processing to interpret social media trends and sentiment, helping traders anticipate market movements before they materialize. The platform aggregates data from Twitter, Reddit, Telegram, and other social channels to gauge community engagement and identify projects gaining genuine traction versus those driven by artificial hype.
Comprehensive Research Resources:
Token Metrics provides personalized crypto research and predictions powered by AI, including detailed project analysis that highlights security considerations, team backgrounds, partnership verification, and competitive positioning. The platform's research team publishes regular updates on emerging threats, best practices, and security trends.
Through Token Metrics' comprehensive dashboard, users can access information about project audits, known vulnerabilities, and historical security incidents. This transparency helps investors make risk-aware decisions rather than relying solely on marketing promises.
Integration with Trading Infrastructure:
Token Metrics launched its integrated trading feature in 2025, transforming the platform into an end-to-end solution where users can review ratings, analyze token details, and execute trades without leaving the ecosystem. This seamless integration ensures security-conscious investors can act on insights immediately.
Experienced communities have identified common patterns that indicate potential scams or high-risk projects. Being alert to these warning signs can prevent catastrophic losses.
Anonymous or Pseudonymous Teams: Projects with anonymous teams are riskier due to lack of accountability. While some legitimate projects maintain anonymity, it significantly increases risk, especially when combined with other warning signs.
Unrealistic Yield Promises: Scammers lure victims with promises of 10 percent or higher daily returns, often through fake investment platforms. The 2025 cases in Australia and Cyprus saw victims lose tens of thousands after depositing crypto into these schemes. If returns sound too good to be true, they probably are.
High Concentration of Holdings: A few wallets holding large shares of tokens increases risk of price manipulation and coordinated dumps. Analyze holder distribution on block explorers—healthy projects show diverse, distributed ownership rather than concentration among a handful of addresses.
Lack of Clear Token Utility: Tokens without genuine use cases beyond speculation are prone to boom-and-bust cycles. Projects should articulate clear utility that drives organic demand rather than relying purely on speculative trading.
Vague or Copied Whitepapers: Projects with vague, overly ambitious, or plagiarized whitepapers lack the substance needed for long-term success. Whitepapers should provide concrete technical details, realistic roadmaps, and clear problem-solution frameworks.
Pressure Tactics and FOMO: Legitimate projects don't need artificial urgency. Excessive marketing emphasizing "limited time offers," "guaranteed returns," or "once in a lifetime opportunity" often signal scams designed to prevent thorough due diligence.
Unusual Transaction Patterns: Frequent transfers, large round-number values, and transactions just below reporting thresholds may indicate structuring or layering activity associated with money laundering.
Anonymity-Enhancing Tools: Excessive use of crypto mixers, privacy coins, or unverifiable peer-to-peer platforms raises red flags, as these tools obscure transaction trails and often signal money laundering or fraud.
High-Risk Jurisdictions: Projects or exchanges operating in countries with lax AML regulations are hotspots for illicit activity, often evading regulatory scrutiny and exposing investors to additional risks.
Crypto communities have developed structured approaches to collective due diligence, combining individual research with collaborative intelligence.
Active, engaged user bases can amplify visibility, drive usage, and create momentum during both bull and bear cycles. From meme coins to major altcoins, history shows that the most successful tokens are backed by strong communities.
Analyzing Community Sentiment:
Join project Telegram channels, Discord servers, and subreddits to gauge community engagement. Healthy communities feature substantive discussions about technology, use cases, and development progress rather than exclusively focusing on price speculation.
Look for red flags in community behavior: excessive moderation that deletes critical questions, bot-like responses praising the project without substance, or coordinated shilling across multiple platforms. A sudden influx of hype or aggressive marketing may signal pump-and-dump schemes.
Follow Token Sniffer's updates on X or its newsletter for new scam patterns, as scammers evolve tactics continuously. Community-reported issues provide valuable early warnings about emerging problems.
A project's whitepaper is its foundational document. Analyze it critically, evaluating clarity of vision, feasibility of the proposed solution, and technical soundness of its architecture. Look for concrete details and avoid projects with vague or overly ambitious claims.
Key Documentation Elements:
Technical specifications should explain how the blockchain or protocol works, what consensus mechanism is used, and how the project differs from competitors. Business logic should clearly articulate the problem being solved, target market, and revenue model.
Roadmap assessment requires evaluating milestone feasibility and timeline realism. Overly ambitious roadmaps promising revolutionary features in unrealistic timeframes often indicate inexperienced teams or intentional deception.
Similar to presales, launchpads are ideal for finding new crypto tokens where third-party platforms host fundraising campaigns, meaning the provider facilitates due diligence and pre-vetting. Major exchanges including Binance and MEXC offer launchpads with established vetting procedures.
ICOBench and ICO Drops provide information on latest presales, including existing and upcoming campaigns. These platforms aggregate project details, making comparative research more efficient. However, listing on these platforms doesn't guarantee legitimacy—always conduct independent verification.
Understanding market dynamics and competitive landscape provides crucial context for evaluating project viability.
Evaluate cryptocurrency market capitalization, trading volume, and liquidity. Assess price history, volatility, and correlation with other assets. Understanding the project's competitive landscape and potential for future growth requires analyzing both absolute metrics and relative positioning.
Liquidity Analysis:
When liquidity is high, it fosters easier entry and exit points, enhancing investor confidence. Low liquidity makes tokens vulnerable to manipulation and prevents investors from exiting positions without significant slippage. Track liquidity across multiple exchanges to assess true market depth.
Trading Volume Patterns:
Tracking trends in capital inflows from institutional investors helps spot heightened interest in specific sectors or technologies. Observing fluctuations in trading volumes, especially during periods of volatility, reveals whether price movements reflect genuine interest or manipulation.
Successful projects typically solve real problems—whether in finance, infrastructure, or data—and maintain active developer communities that drive progress. These are hallmarks of high-potential cryptocurrencies that can maintain competitive advantages.
Assess how the project differentiates from competitors. Does it offer superior technology, better user experience, lower costs, or access to underserved markets? Projects without clear competitive advantages struggle to gain traction in crowded markets.
Crypto regulations vary significantly across countries, making compliance verification essential for risk mitigation. The regulatory landscape continues evolving, with enforcement becoming more stringent globally.
Determine the project's legal jurisdiction and applicable regulations. Projects operating in jurisdictions with clear regulatory frameworks provide more certainty and lower risks of unexpected shutdowns or enforcement actions.
Many regulatory bodies are increasingly aligning around standards like FATF and MiCA. Understanding these frameworks helps assess whether projects are positioned for long-term viability or face regulatory headwinds.
Assess whether the token might be classified as a security under applicable laws like the Howey Test in the United States. Securities classification imposes additional regulatory burdens and restrictions that affect liquidity, trading venues, and investor eligibility.
Projects ignoring securities laws face potential enforcement actions from regulators like the SEC, which can result in trading suspensions, delisting from exchanges, and significant financial penalties that destroy token value.
Combining community wisdom with personal due diligence provides the most robust protection against scams and poor investments.
Create a standardized checklist covering all essential vetting areas: team verification, tokenomics analysis, security audits, regulatory compliance, community assessment, and competitive positioning. Systematically work through this checklist for every project under consideration.
Document your research findings, including sources, dates, and key observations. This creates accountability and enables pattern recognition across multiple projects. Maintain skepticism throughout the process—many scams are sophisticated and designed to pass superficial scrutiny.
Never invest more than you can afford to lose in new crypto projects. Even thoroughly vetted projects can fail due to market conditions, technical issues, or unforeseen circumstances. Diversification across multiple projects, sectors, and risk levels provides essential protection.
Start with small positions in new projects, increasing exposure only after projects demonstrate sustained development progress, growing adoption, and community strength. This approach limits downside while maintaining upside participation.
Due diligence doesn't end at investment. Ongoing monitoring ensures you identify emerging risks or opportunities early. Subscribe to project newsletters, follow official channels, and track development activity through GitHub or similar repositories.
Set up price and volume alerts to identify unusual activity. Use portfolio tracking tools like CoinStats or Delta to monitor holdings across exchanges and wallets, flagging suspicious activity such as unexpected withdrawals.
As the cryptocurrency ecosystem matures, vetting processes continue evolving with more sophisticated tools and methodologies emerging regularly.
Advanced AI systems like those powering Token Metrics represent the future of crypto due diligence. These platforms analyze vast datasets of blockchain transactions, code repositories, social media sentiment, and security incidents to identify patterns that human analysts might miss.
Machine learning models can predict project success probabilities based on historical data, development activity, and community growth patterns. As these systems improve, they'll provide increasingly accurate risk assessments and opportunity identification.
Increased regulatory clarity across jurisdictions will make vetting more straightforward by establishing clear compliance standards. Projects meeting these standards will be easier to identify and validate, while non-compliant projects will face greater scrutiny and restrictions.
However, regulation also creates barriers to entry that may limit innovation. Balancing security with innovation remains an ongoing challenge for the crypto community.
Decentralized reputation systems and collaborative due diligence platforms enable community members to share research, flag scams, and verify project claims collectively. These systems leverage blockchain transparency to create verifiable track records of project behavior and community assessments.
As these collaborative systems mature, they'll create powerful network effects where collective intelligence outperforms individual research, making scams harder to execute and legitimate projects easier to identify.
Vetting new crypto projects requires combining technical analysis, social intelligence, and sophisticated tools to navigate an environment where opportunities and risks exist in equal measure. Communities have developed robust frameworks addressing team legitimacy, tokenomics, security, regulatory compliance, and competitive positioning.
By carefully analyzing project transparency, tokenomics, utility, and community engagement, you can identify trustworthy ventures with long-term potential, make informed decisions, and avoid impulsive investments influenced by hype alone. Platforms like Token Metrics provide the AI-powered analytics and comprehensive research necessary for effective due diligence in 2025's complex landscape.
The most successful crypto investors combine thorough individual research with community wisdom, leveraging advanced tools while maintaining healthy skepticism. They understand that no vetting process guarantees success, but systematic due diligence dramatically improves odds of identifying legitimate projects while avoiding catastrophic scams.
As new tokens launch daily across multiple blockchain networks, the ability to quickly and effectively vet projects becomes increasingly valuable. Those who master this skill position themselves to capitalize on early-stage opportunities while protecting capital from the numerous scams and failures that plague the crypto space.
Whether you're an experienced trader or new to cryptocurrency, following structured vetting processes, using sophisticated analytics platforms, and maintaining disciplined risk management will serve you well in navigating the exciting but treacherous world of crypto investing in 2025 and beyond.


 Create Your Free Account
Create Your Free Account9450 SW Gemini Dr
PMB 59348
Beaverton, Oregon 97008-7105 US
.svg)




.png)
Token Metrics Media LLC is a regular publication of information, analysis, and commentary focused especially on blockchain technology and business, cryptocurrency, blockchain-based tokens, market trends, and trading strategies.
Token Metrics Media LLC does not provide individually tailored investment advice and does not take a subscriber’s or anyone’s personal circumstances into consideration when discussing investments; nor is Token Metrics Advisers LLC registered as an investment adviser or broker-dealer in any jurisdiction.
Information contained herein is not an offer or solicitation to buy, hold, or sell any security. The Token Metrics team has advised and invested in many blockchain companies. A complete list of their advisory roles and current holdings can be viewed here: https://tokenmetrics.com/disclosures.html/
Token Metrics Media LLC relies on information from various sources believed to be reliable, including clients and third parties, but cannot guarantee the accuracy and completeness of that information. Additionally, Token Metrics Media LLC does not provide tax advice, and investors are encouraged to consult with their personal tax advisors.
All investing involves risk, including the possible loss of money you invest, and past performance does not guarantee future performance. Ratings and price predictions are provided for informational and illustrative purposes, and may not reflect actual future performance.



